Global Properties
|
While the brunt of your security policy will reside in the rule base, there are other places you have to pay attention to. In order to fully secure your enterprise, you will need to at least be familiar with the Global Properties, and most likely you will need to alter them. You do this by accessing the Global Properties from the Policy menu. We'll spend the next few sections discussing these properties. Figure 13.32 displays the initial panel of the Global Properties.
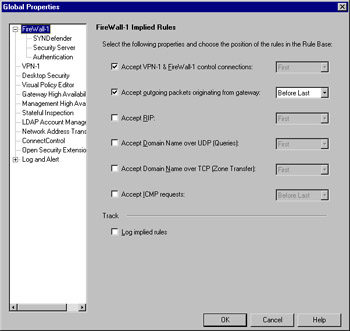
Figure 13.32: Global Properties
FW-1 Implied Rules
FW-1 has a feature that many find mysterious at first blush. That feature is the implied rule base. This rule base is made up of settings in the Global Properties, as opposed to the one explicitly created by you, the firewall administrator. Once you understand this, the mystery is removed, and you'll see that they are actually pretty simple. They are shown, by the way, in Figure 13.32. What you select is up to your security policy, but we highly recommend that you enable the logging of these rules.
One important thing to understand is the implication of the option values. If you select a rule to be included within the implied rule base, you'll need to decide where to place that rule. You have three choices here.
-
First
-
Last
-
Before Last
You'll need to select the location in the rule base where the selected rule will be placed. This is a critical decision, and you should understand how a packet passes through the rule base in order to assist your decision. Furthermore, not all implied rules are as simple as they may seem. The first implied rule, Accept VPN-1 and FW-1 control connections, for example, enables a service group containing 17 services. You probably don't need to worry about this too much, but it is a good thing to be aware of.
Viewing Implied Rules
There are two methods of viewing implied rules. Certainly, you can view them within the Global Properties window, but this is often cumbersome and difficult to do in a cohesive flow. When you want access to these rules while editing the rest of your rule base, the easiest way is to select the View menu and then select Implied Rules. You'll see something like what is displayed in Figure 13.33. Note that the implied rules are unnumbered and are highlighted by their different color.
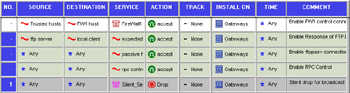
Figure 13.33: Implied Rules
SYNDefender
SYNDefender is a feature used to guard your network from the dreaded SYN flood. Note that this isn't really designed to prevent such an attack against your firewall, but for what it is intended to do it is very handy. It has two modes of operation: SYNGateway and passive SYNGateway. In SYNGateway mode, the firewall actively intercepts SYN packets, completes the three-way handshake, and only then forwards the connection to the true destination. In passive mode, the firewall monitors the connection. If the timeout period is reached, a RST (reset) packet is sent to both the originator and the destination.
Configuring SYNDefender is simple. Simply navigate to the proper sub-menu and select the method, timeout, and maximum connections.
Using SYNDefender to Defend the SYN Attack
The SYN attack is one of the simplest Denial of Service (DoS) attacks to initiate. Unfortunately, it is also one of the most difficult to defend against. The reasons for these truths are identical. The basic operation of a SYN flood is to send hundreds of thousands of connection requests (SYN, or synchronize, packets) to the target server. The target server will send an acknowledgment of that SYN packet, allocate a bit of memory in a pending connection queue, and then wait, for a predefined timeout period, for the final part of the connection process to complete. Herein lies the rub.
There are two problems here. The first is that the sending of a SYN packet is completely normal. A high-volume server might see thousands of SYN packets in any given time period. The second problem is that the server tends to be too generous in its timeout period, giving the client plenty of time to complete the connection. For example, default configuration of Microsoft Windows 2000 will wait 189 seconds. That's over three minutes per connection of resource consumption. While the memory allocated is small, the cumulative impact can be severe enough to gobble up all the resources on the target server.
While firewall tools like SYNDefender can help you keep the bogus SYN packets from reaching the server, you need (and have available) a better method. Since most SYN attacks use spoofed IP addresses, ingress and egress filtering by large ISPs could go a long way to mitigate the dangers of SYN attacks.
Security Server
The Security Server panel allows the entry of welcome messages for many of the most common Internet services. This is accomplished by pointing to the appropriate file containing the message. You can also configure the HTTP Next Proxy, although this is better done in the workstation object, assuming a version of FireWall-1 of NG. Earlier versions still require entry in this field.
Authentication
The Authentication panel enables you to specify the tolerance for failed login attempts. There are parameters for rlogin, telnet, client authentication and session authentication. There is also a section for configuring session timeout, wait mode and logging/alerting for back level modules.
VPN-1
The VPN panel controls the configuration of items like security association (SA) renegotiation, as well as CRL and SecuRemote grace periods.
Desktop Security
The Desktop Security panel contains a lot of information regarding the behavior of your firewall with regard to SecuRemote client requests. The settings you select here are highly dependant on your own security policy, but again, WE strongly recommend that you log violation notifications and not respond to unauthenticated topology requests.
Visual Policy Editor
The Visual Policy Editor (VPE) provides a very slick interface to view your objects and their interrelations, as mentioned in the beginning of this chapter. This panel enables you to display the VPE or conceal it from view. Note that if you disable the VPE, no topology calculations will take place within the firewall inner workings.
Gateway High Availability
Gateway High Availability is the process in which multiple modules can act as one for the sake of redundancy. This panel lets you enable or disable the feature.
Management High Availability
Management High Availability is similar to that for gateways, except that it allows the management modules to exhibit some redundancy. This panel allows for you to select the synchronization time of the management servers participating in the HA configuration.
Stateful Inspection
Stateful Inspection is the heart of FW-1. This panel does not allow you to change that, but instead enables you to specify some timeout settings for the TCP sessions and to configure stateful UDP and ICMP behavior.
LDAP Account Management
The LDAP account management panel allows the enabling of LDAP for account management. Here you can also set some session timeouts and password rules.
Network Address Translation
The NAT panel configures some general NAT behavior such for the Automatic NAT rules and NAT pools for SecuRemote connections.
ConnectControl
The ConnectControl panel allows the configuration of this very handy feature. On this panel, we can set the interval that VPN-1/FW-1 will wait between server checks (commonly known as heartbeat checks) and the number of retries before a server is considered unreachable. We can also set the persistency timeout. This is the time within which all connections from the same source IP will be forwarded to the same server. Finally, you configure the listening address of the server agent used to measure server load and the pooling interval for that.
Open Security Extension
The Open Security Extension (OSE) panel allows configuration for implied rules that are applied only to OSE compliant routers.
Log and Alert
The Log and Alert panel enables you to configure the responses taken when a packet matches a rule.
|
EAN: 2147483647
Pages: 240