| An important preventive maintenance task is to protect your Mac from other people who use it or from those who access its files from a network. You can also use the security pane of the System Preferences application, the secure delete trash function, and keychains to help you protect your Mac's security. Securing Your Mac with User Accounts You should create user accounts for everyone who uses your Mac. In addition to the features user accounts provide, such as a website and well-organized file storage, user accounts prevent unauthorized users from changing the system configuration of your machine.  To learn how to create and configure user accounts, p. 26. To learn how to create and configure user accounts, p. 26.
Securing Your Mac with Privileges For those who access your Mac over a network and for those who share your machine, you can control the access to specific items by setting privileges for those items. You can control access in several levels of privilege from not being able to even see the item to being able to read and write to it.  To learn how to configure privileges, p. 935. To learn how to configure privileges, p. 935.
Securing Your Mac with the Security Pane The Security pane of the System Preferences application enables you to protect your Mac in a couple of ways. One is by using the FileVault feature that encrypts all the files in your Home folder; these files can't be used unless you input your login password or the master password for your Mac. The other way is by configuring various security settings for your Mac. Securing Your Mac with FileVault Mac OS X's FileVault feature encrypts all the files in your Home folder with 128-bit encryption. Such files can't be opened unless one of two passwords is entered. One password is the one you use to log in to your account. The other is a master password you set for your Mac; with this password, you can decrypt any encrypted files on your Mac, regardless of the user account with which those files are associated. Once configured, FileVault works in the background and you won't notice it doing its job. CAUTION According to Apple, FileVault can interfere with backups because it makes your Home folder appear as a single file to the backup system. This can make the individual files impossible to restore. When using FileVault, be sure you test your backup system to ensure that you can still recover files if you need to.
The following steps demonstrate how to configure FileVault: 1. | Open the System Preferences application and click the Security icon. The Security pane will appear (see Figure 35.6).
Figure 35.6. Use the FileVault feature if you want to encrypt the files in your Home folder so they can't be used without a valid password. 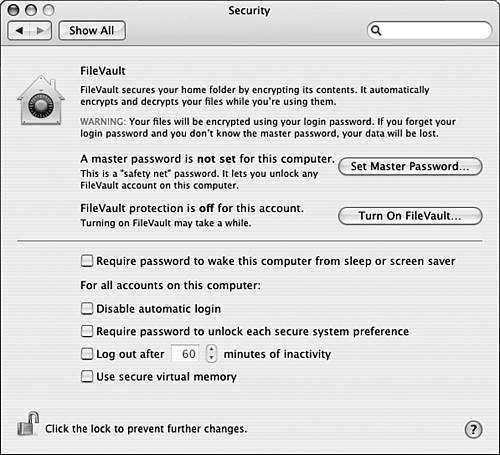
| 2. | Click the Set Master Password button. The master password sheet will open. Generally, you should use this feature if there is some chance that any user of your Mac will forget his password; the master password enables you to decrypt encrypted files for all users. You must create a master password before you can activate FileVault.
| 3. | Enter the master password in the Master Password field and enter it again in the Verify field.
TIP Click the ? next to the Master Password box to open the Password Assistant. You can use this tool to generate passwords based on specific criteria, such as type and length. When you have configured a password, it will be placed in the box for you. You then have to type it in the Verify box. | 4. | Enter a hint for the master password in the Hint field.
| 5. | Click Continue to set the master password.
NOTE To use FileVault, a user account must have a password. If you didn't configure a password for your user account, or for any other user account, you will need to do so before you can activate FileVault. | 6. | Click the Turn On FileVault button. If there currently isn't a password for the user account, you can use the Password sheet to create one. The warning sheet will appear. If the user account already has a password, the service starts up and you are prompted to enter your password.
| 7. | Enter your user account's login password and click OK. You will see a warning sheet that explains what you are doing and that activating this service can take a while (you can't log out of your account until the service has been turned on).
NOTE If you also want Secure Erase (which overwrites deleted data so that it can't be recovered as easily), check the "Use secure erase" check box. | 8. | Click the Turn On FileVault button. The FileVault window appears; you can't do anything else on your Mac until FileVault has started up. This window shows you the progress of the encryption process. If you have a lot of data in your Home folder, this process can take quite some time. When the process is complete, you see the Login window.
NOTE If you want this feature to be active for multiple user accounts, you must log in under each account and turn on FileVault. | 9. | Log back in to your account. You shouldn't notice any difference, but all your Home folder files will be encrypted and won't be accessible unless a valid encryption password has been entered.
|
CAUTION FileVault applies only to each user account in which it is activated. And it works only on the files in each user's Home folder. Files stored outside the Home folders for which it is activated are not protected.
When you log in to your account (or any other user whose account is protected by FileVault), the files in your Home folder are decrypted automatically so you won't need to do anything else to access them. The value of FileVault is for those times when you aren't logged in to your account and someone else has access to your machine. For example, suppose someone steals your PowerBook. Although she can't access your user account without your login password, she could connect the machine to a FireWire drive with Mac OS X installed and start up from that volume. Because the files on your PowerBook's startup volume are not protected anymore (the OS on the FireWire drive is active), they are accessible. If FileVault is not on, these files are not encrypted and can be used, but if FileVault is on, these files are encrypted and are useless. You can turn off FileVault again by clicking the Turn Off FileVault button and entering your login password. If another user on your Mac turns on FileVault and subsequently forgets her password, you can use your Mac's master password (assuming you set one) to decrypt the files in that user's Home folder. You can provide the master password to the other user so they can decrypt their files. Then, change the master password to make sure only the "right" people have it. NOTE When a user account is protected by FileVault, its Home folder icon looks like a cross between the normal Home folder icon and a safe.
Securing Your Mac with Security Settings Several other security settings are available on the Security pane (refer to Figure 35.6). These features are described in the following list: Require password to wake this computer from sleep or screen saver If you enable this feature, a user account's login password is required to stop the screensaver or wake up the Mac from sleep. This setting impacts only the account currently active; if you want this to be required for each user account, you need to log in to each one and set it for that account. Disable automatic login Check this box and the automatic login feature is turned off. This means that someone will have to log in into your Mac manually to be able to use it. Require password to unlock each secure system preference When you check this box, a login password must be entered to make any changes that affect system security. Log out after _ minutes of activity This feature logs out the current user account after the specified amount of inactivity has occurred. To use it, check the box and set the amount of time using the box. When the amount of inactive time passes, the current user is logged out automatically. Use secure virtual memory When this feature is active, data written to disk when virtual memory is required is also stored securely.
Securing Your Mac by Removing Trash Securely Normally, when you delete files they are deleted from the system, but the data for those files might or might not be overwritten by other data. If not, files can sometimes be recovered by software restoration tools. If you want the files you delete to be overwritten with system-generated data so they can't be recovered, use the Secure Empty Trash command on the Finder's File menu instead of the normal Empty Trash command. This causes the files you delete to be overwritten so they can't be recovered. Securing Your Mac with Keychains For security and other reasons (such as making online shopping more convenient), you need usernames and passwords to access network resources, whether those resources are on a local network or the Internet. After using even a few of these, you will have a large collection of usernames and passwords. Remembering these can be a challenge. Fortunately, your Mac lets you store all your usernames and passwords in a keychain. You can then apply your keychain to whatever resource you want, to use and the appropriate information is provided so you can access what you need. All you need to remember is the password that unlocks your keychain. By default, this is the same as your login password so that your keychain is used automatically. After you have added a password to your keychain, you can access the related resources without entering your keychain's password (because it is entered when you log in). NOTE Safari can also remember usernames and passwords for sites you visit so you don't have to enter this information each time you log in. This saves a lot of time and keystrokes (assuming you can even remember all your usernames and passwords, of course). What actually happens is that Safari creates an item within the Passwords category in which all your web username and passwords are stored. When you return to a page for which you have had Safari remember your login information, it uses the data stored in the keychain to input the appropriate information for you.
 For more information about Safari and keychains, p. 460. For more information about Safari and keychains, p. 460.
You can configure other keychains so that you can gain automatic access to secured resources during each working session. To secure those resources again, you can lock your keychain, which means the password must be entered for that keychain to be applied. Before you can use a keychain, one has to be created. A keychain is created automatically for each user account you create. However, you can create additional keychains for specific purposes if you need to. To use a keychain, it must be unlocked. To unlock a keychain, you enter its password when you are prompted to do so. When you log in to your user account, the default keychain for that account is unlocked automatically. NOTE You can store information that you want to secure using notes. For example, if you want to store your credit card information so it can't be accessed unless you are logged in to your user account, you can add it to your keychain. When you need that information, you can open the secured note containing your credit card information in your keychain.
Many types of resources can be added to your keychain to enable you to access them, including the following: AirPort network password When you add an Airport network password to your keychain, you can join the network by selecting it via the AirPort controls. The network's password will be added to your keychain automatically. Application password Some applications require passwords to perform specific tasks. One notable example is the iTunes Music Store function. When you have your iTunes Music Store password added to your keychain, you can purchase songs with a single click of the mouse button (which can be a dangerous thing!). AppleShare password Any passwords you use to access network volumes can also be added to your keychain. Internet password When you need to enter passwords for Internet services, such as email accounts, adding them to your keychain makes accessing those services much more convenient because you never have to enter the password manually. .Mac password When you enter your .Mac password in the .Mac pane of the System Preferences application, it is added to your keychain so you can work with your iDisk from the desktop without having to log in to your .Mac account each time. Secure note These enable you to store information securely. Web form password When you access your account on secure websites, you can add your usernames and passwords to your keychain. When you visit those sites again (via Safari), you can log in just by clicking the Login button because your username and password are entered automatically.
Viewing and Configuring Your Keychains and Keychain Items You access your keychains through the Keychain Access application by doing the following: 1. | Open the Keychain Access application (Applications/Utilities folder). When the application opens, two panes appear (see Figure 35.7). In the left pane (the drawer) is a list of categories for all the keychains that are installed under your user account. These categories include All Items, which contains all keychain items you can access; Passwords, which contains passwords for network and other resources; and so on. Select a category and the keychain items it contains will appear in the right pane of the window. You will see information related to each keychain item, such as its name, its kind, the date it was last modified, and the keychain in which it is stored.
Figure 35.7. This user can access several items stored in the selected keychain, including a network password and a secured note. 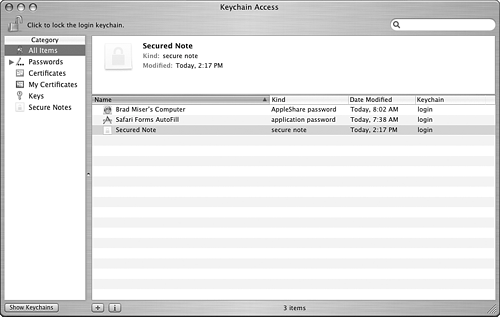
TIP The Passwords category contains several subcategories. To view them, expand that category by clicking its expansion triangle. | 2. | To view all the keychains your user account can access, click the Show Keychains button at the bottom of the Keychain Access window (see Figure 35.8).
Figure 35.8. Here, you can see that this user has several keychains available; only the Login keychain is currently unlocked. 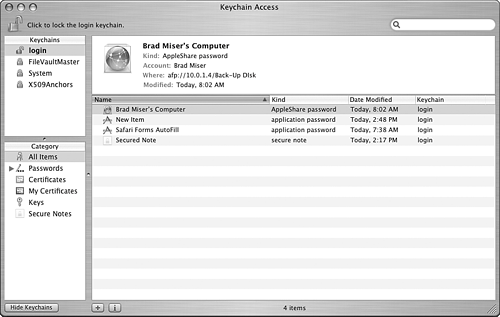
| 3. | To get detailed information about a keychain item, select it. A summary of the item will appear at the top of the window and will list the kind of item it is, the user account with which it is associated, where the location to which it relates is, and the modification data.
| 4. | With the item still selected, click the Information button (the i located at the bottom of the Keychain Access window). The Information window will appear. This window has two tabs: Attributes and Access Control (see Figure 35.9). The Attributes tab presents various information about the item, such as its name, its kind, the account, the location of the resource with which it is associated, comments you have entered, and the password (which is hidden when you first view an item). The Access Control tab enables you to configure how the item is used.
Figure 35.9. The Information window provides detailed information about a keychain item. 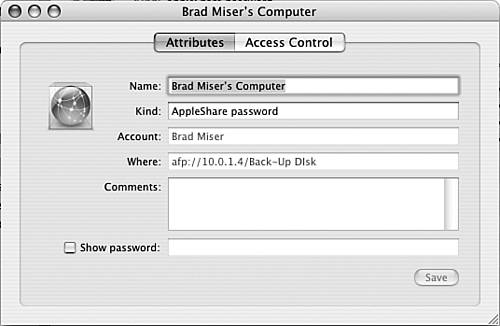
| 5. | To see the item's password, check the "Show password" check box. You are then prompted to confirm the keychain's password (you'll learn more about this in the next section).
| 6. | Confirm the password by entering it at the prompt and choosing to allow access to the item (the options you see are explained in the next section). When you return to the Attributes tab, you will see the item's password.
| 7. | Click the Access Control tab. You will see a list of the applications that have access to the keychain item. Use the access controls in the window to control which applications can access this item and how they can access it.
| 8. | To allow access to the item by all applications, check the "Allow all applications to access this item" radio button. You will see a warning that access to the item is not restricted. This means that all applications will be able to use the item. With this option, you can't configure the other options because they don't apply. If you want to configure access for specific applications, continue with the rest of these steps.
| 9. | To allow access by specific applications but require confirmation, click the "Confirm before allowing access" radio button, and check the "Ask for Keychain password" check box if you want to be prompted for your keychain's password before access is allowed (if you don't select this option, the item will be accessed automatically).
| 10. | To enable an application not currently on the list to access the keychain item, click the Add button (the + located at the bottom of the application list) and select the application to which you want to provide access.
| 11. | To remove an application's access to the item, select the application and click Remove (the - located at the bottom of the application list).
| 12. | Click Save to save the changes to the keychain and its items.
|
Adding Items to a Keychain You can add items to a keychain in several ways, including the following: When you access a resource that can provide access to a keychain, such as a file server, look for the "Add to Keychain" check box. When you check this, an item for that resource is added to your keychain. This is the most common and easiest way to add items to a keychain. NOTE Sometimes you have to click the Options button to be able to add an item to your keychain. For example, when you mount a network volume, click Options to reveal the Add Password to Keychain check box.
Drag a network server onto the Keychain Access window. Drag the Internet Resource Locator file for a web page onto the Keychain Access window. Manually create an item.
CAUTION Not all applications support keychain access. If a particular application or resource doesn't support keychains, you won't be able to access that resource automatically. However, you can still use Keychain Access to store such an item's username and password for you, thus enabling you to recall that information easily. This also stores it more securely than writing it down on a piece of paper.
To manually add a password item to your keychain, perform the following steps: 1. | Open Keychain Access (Applications/Utilities).
| 2. | View the keychains installed for your user account and select the keychain to which you want to add the item (your default keychain, which is the login keychain unless you have changed it, is selected automatically).
| 3. | Select File, New Password Item or press  -N to see the New Password Item sheet. -N to see the New Password Item sheet.
| 4. | Enter the name of the item in the Keychain Item Name box. If you are adding an Internet resource, such as a web page, enter its URL.
| 5. | Enter the account name or username for the item in the Account box. This is the name of the user account with which the keychain item will be associated.
| 6. | Enter the password for the item in the Password box. If you want to see the password as you type it, check the Show Typing check box. This helps you confirm you are entering the correct password. Otherwise, you see only bullets as you type.
TIP Click the Key button to open the Password Assistant to help you configure a password for the item. | 7. | Click Add to return to the keychain's window and see the new item you added. You will be able to access that item using your keychain. You can view and configure the new item using the steps in the previous section.
|
TIP You can set the default keychain for your user account by selecting the keychain you want to make the default one and choosing File, Make Keychain keychainname Default, where keychainname is the name of the keychain you have selected.
To add a secure note to a keychain, use the following steps: 1. | Open Keychain Access.
| 2. | Select the keychain to which you want to add the note (your default keychain is selected automatically).
NOTE If you select a keychain that is currently locked, you will have to unlock it before you can add items to it. | 3. | Select File, New Secure Note Item or press Shift-[cmd]-N. The New Secured Note sheet will appear.
| 4. | Enter the name of the note in the Keychain Item Name box.
| 5. | Enter the information you want to store in the Note box. This a freeform text field so you can enter anything you want.
| 7. | Click Add to return to the Keychain Access window where you will see the new note you added.
| 8. | To view the note, double-click it and click the "Show note" check box. You will see the note in the window.
|
Adding a Keychain You might want to add a keychain to your current account, which you can do using the following steps: NOTE You might want to move a keychain between user accounts so you don't have to re-create the items it contains.
1. | Open Keychain Access (Applications/Utilities).
| 2. | To add a keychain, select File, New Keychain or press Option- -N. You will see the New Keychain dialog box. -N. You will see the New Keychain dialog box.
| 3. | Move to the location in which you want to save the keychain, name it, and click Create. (By default, keychains are stored in the Keychains folder in the Library folder in your Home folder. In most cases, you should store new keychains in this folder.) You are prompted to create the password for the keychain.
TIP An exception to where you keep your keychains might be when you want to enable others to import your new keychain into their accounts, in which case you should store it in a location accessible to others, such as your Public folder. For example, you might want to create a keychain with website items on it. You could provide this to other users who would then be able to access the items contained in the keychains you install. | 4. | Enter the password for the keychain in the Password and Verify fields; then click OK. The new keychain is added to the list of available keychains, and you can work with it just like those already on the list.
|
TIP Click the Key button to open the Password Assistant to use it to create a password for the keychain you are creating.
Using Keychains When you have a keychain configured for an account and it is unlocked, you can access the items it contains without entering your username or password. For example, when you open a server, it opens for you immediately. NOTE By the way, this is how Mac OS X can access your .Mac account without you having to log in each time. When you create a .Mac account, it is added to the keychain for the Mac OS X user account related to it. Mac OS X can use this keychain to access the .Mac account without requiring that you log in manually.
To prevent a keychain from being accessed, lock it. Do so by opening the Keychain Access application, selecting the keychain, and selecting File, Lock Keychain keychainname, where keychainname is the name of the keychain. You can also do so by pressing  -L or clicking the Lock button (the padlock) on the toolbar. -L or clicking the Lock button (the padlock) on the toolbar. To unlock a keychain again, select it, click the Unlock button or press  -L, enter the password for that keychain, and click OK. -L, enter the password for that keychain, and click OK. When an application needs to access a keychain item and it is not configured to always allow access, you will see the Confirm Access to Keychain dialog box that prompts you to enter a keychain's password and choose an access option. When prompted, you have the following three options: Deny If you click this, access to the item is prevented. Allow Once A single access to the item is allowed. The next time you attempt to access it, you see the prompt again. Always Allow Access to the item is always allowed.
NOTE The first time you access keychain items after the OS has been updated, such as through the Software Update application, you see the Confirm Access to Keychain prompt, even for those items for which you have selected the "always allow access" option (such as the first time you check your email after upgrading the OS). This is normal behavior. Just select the Always Allow option to reenable that behavior.
Going Further with Keychains Keychain Access is actually a fairly complex application that can do more than just what I have room to show you in this section. Following are some pointers in case you are interested in exploring on your own: Your keychains are stored in the Library/Keychains folder in your Home directory. You can add a keychain from one account to another account by exporting the keychain file (use the File, Export command) to a location that can be accessed by the second account. (For example, you can copy your keychain into the Public folder of your Home directory to enable other users to add that keychain to their own accounts.) To add a keychain to a user account, open Keychain Access under that account and use the File, Import command. This is useful if you want to use the same keychain from several accounts. You can't export all keychains, so you have to try one to see whether you can export it. Delete a keychain either by selecting it and selecting File, Delete Keychain keychainname, where keychainname is the name of the keychain. If you select Edit, Change Settings for Keychain keychainname, where keychainname is the name of the keychain, you can set a keychain to lock after a specified period of time or lock when the Mac is asleep. You can synchronize keychains on different computers by using .Mac. If you select Edit, Change Password for Keychain keychainname, where keychainname is the name of the keychain, you can change a keychain's password. Choose Keychain Access, Preferences. On the General tab, check "Show Status in Menu Bar." This will add the Keychain Access menu to the Mac's menu bar. From this menu, you can lock or unlock keychains and access security preferences and the Keychain Access application. If you select Edit, Keychain List or press Option- -L, you see the Configure Keychain sheet. You can use this to configure keychains for a user account or the system. For example, you can check the Shared check box to share a keychain between user accounts. -L, you see the Configure Keychain sheet. You can use this to configure keychains for a user account or the system. For example, you can check the Shared check box to share a keychain between user accounts. If you select Keychain Access, Keychain First Aid or press Option- -A, you see the Keychain First Aid dialog box. You can use this to verify keychains or repair a damaged keychain. -A, you see the Keychain First Aid dialog box. You can use this to verify keychains or repair a damaged keychain. In the keychain access prompt, you can click the Show Details button to expose the details of the keychain access being requested.
|
 To learn how to create and configure user accounts,
To learn how to create and configure user accounts, 


