Additional Configuration Parameters
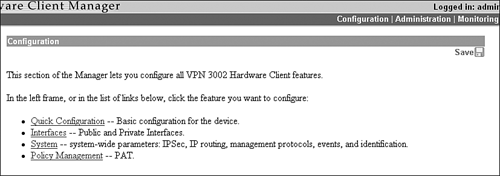
| The majority of the configuration parameters are managed by the Quick Configuration Setup dialog. However, you can still navigate through the configuration pages of the Client Manager's navigation frame (Figure 9.8) to make additional configurations or change Quick Configuration parameters. In fact, the top of the navigation frame contains a link to the Quick Configuration setup utility. Unlike the VPN 3000 Concentrator, the VPN 3002 Hardware Client enables you to jump back to the Quick configuration whenever you wish. Figure 9.8. 3002 Hardware Client Manager Configuration division.
One notable configuration screen is the Configuration | Tunneling Protocols | IPSec page. This configuration screen has similar fields to the Quick Configuration | IPSec screen; however, it additionally contains a backup server field. In this option, you can specify up to 10 backup concentrators for tunnel connectivity to the network. These devices can be defined on the VPN 3002 Hardware Client; however, it is also a policy that can be enforced or disabled from the central location's concentrator. When a policy push occurs, the list pushed from the concentrator overwrites the hardware client's list.
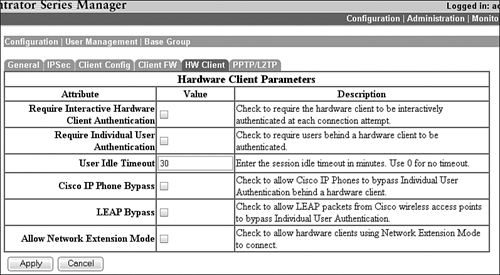
VPN 3000 Concentrator Hardware Client ParametersRemarkably enough, some of the most pertinent configurations are not done on the VPN 3002 Hardware Client. For several policies and parameters, the central VPN 3000 Concentrator is responsible for pushing configuration attributes down to hardware and software clients. What's more, the HW Client tab in the concentrator's Configuration | User Management page is devoted to parameters that are pushed to the VPN 3002 Hardware Client. Illustrated in Figure 9.9, the HW Client tab on the VPN 3000 Concentrator enables you to configure options that will be pushed down to the hardware client. The top of the tab pertains to the authentication features discussed in the beginning of this chapter. If you want to enforce interactive and/or individual authentication, check the appropriate boxes on this page. By default, both these options are disabled for all groups. Figure 9.9. 3002 Hardware Client Manager Configuration screen.
Following the authentication features, the next field presented defines a peer idle timeout for the tunnel. This field enables you to define how many minutes of inactivity (default is 30) are allowed before the tunnel is terminated. In instances where you are operating in Network Extension mode and you want to use Cisco IP phones across the tunnel, you can enable the "Cisco IP Phone Bypass" option that allows Cisco phones to circumvent individual authentication because they lack the capability to perform this function. Similarly, when utilizing Cisco Aironet wireless devices that employ LEAP (Lightweight Extensible Authentication Protocol) for wireless network authentication to a RADIUS server, you can check the LEAP Bypass option so these LEAP packets can bypass the individual authentication. After the wireless user authenticates to the RADIUS server, the user is still required to perform the individual authentication. Finally, Network Extension mode must be enabled at the head-end concentrator if the hardware client in this group is requesting it. If this option is not selected, no VPN 3002 Hardware Clients in the group can establish a site-to-site connection to the concentrator. Interactive and Individual LoginBecause the interactive and individual authentication features are so prominent throughout this chapter, it's important to look at the steps involved for the users to initiate the tunnel and authenticate to the head-end concentrator. Recall that these options are not enabled by default in the group configurations on the concentrator. Thus, as long as you have the IPSec attributes configured correctly in the Quick Config | IPSec or the Configuration | Tunneling Protocols | IPSec configuration pages, the tunnel will initiate and allow all users whenever the traffic warrants it.
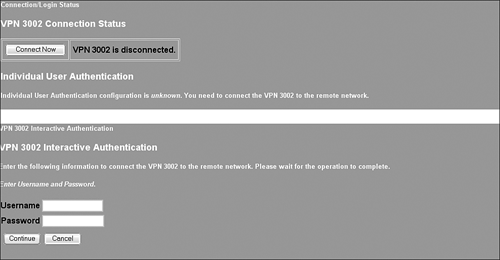
Interactive Tunnel Connection ExampleWhen Interactive tunnel authentication is enabled from the central-site concentrator, any saved passwords on the hardware client are erased from the configuration. The tunnel must be manually established by a user on the private network. To perform this action, users navigate their browser to the client's private interface. The 3002 Hardware Client Manager login page (refer to Figure 9.3) contains a Connection/Login Status hyperlink, which produces an output similar to that shown at the top of Figure 9.10. When the user clicks on the Connect Now button, a new page is presented with a screen comparable to that shown at the bottom of Figure 9.10. At this point, the user must input a valid username and password for the VPN 3002 Hardware Client that is to be sent to the head-end concentrator. If approved, the tunnel is established and remains up until the inactivity timer expires or an administrator disconnects it. Mind you, after this tunnel is established, all users on the private interface network can utilize it. Figure 9.10. Interactive Login display screens.
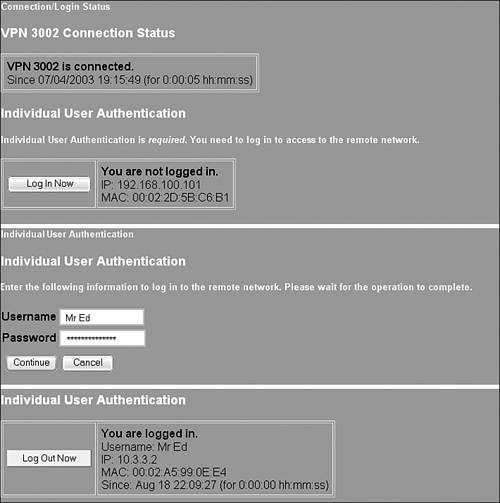
Individual Login ExampleRegardless how the tunnel is initiated, you can enforce individual users to authenticate themselves to the concentrators before they can use the tunnel. After this policy is pushed from the concentrator, users need to authenticate themselves in one of two ways:
In either instance, you are presented with the screens depicted in Figure 9.11. The hardware client will recognize your IP and MAC address and determine that you need to log in. After clicking on the Log In Now button, enter the username and password values matching the concentrator's user parameters. After you are authenticated, you are presented with a screen similar to the bottom of Figure 9.11, and you are able to use any service that you require across the tunnel. Figure 9.11. Individual User Authentication Screens
|
EAN: 2147483647
Pages: 185
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XV Customer Trust in Online Commerce
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability