Approaches to WLANs, WWANs, WPANs, and PALs
|
|
The major types of data-oriented wireless systems that are currently getting the most attention include the following (see also Figure 1-7):[19]
-
WLANs
-
IEEE 802.11b, which is sometimes called wireless Ethernet or Wi-Fi
-
IEEE 802.11a, high-performance radio local area network type 2 (HIPERLAN/2),[20] IEEE 802.11g, and Home Radio Frequency (HomeRF) (alternatives to 802.11b)[21]
-
-
WPANs (for example, IEEE 802.15 and Bluetooth)
-
WWANs, also known as mobile wireless (voice/telephony with increasing integration of data and video)
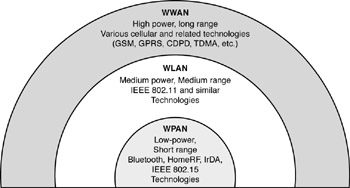
Figure 1-7: Continuum of wireless technologies
Figure 1-8 depicts wireless technologies by locus. Table 1-3 captures some of the design goals of wireless solutions (particularly in a 3G context).
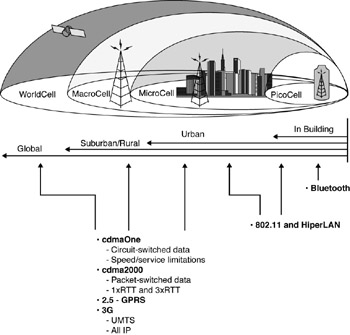
Figure 1-8: Wireless technologies by Locus
| Feature | Goals |
|---|---|
| Services | Stationary users or pedestrian applications with speeds of 0 to 10 km/h Vehicular applications with speeds up to 100 km/h High-speed rail applications with speeds up to 500 km/h Aeronautical applications with speeds up to 1,500 km/h Satellites applications with speeds up to 27,000km/h |
| Data rates | Up to 144 Kbps (more in the future) in vehicular applications At least 384 Kbps for pedestrian (nonhotspot) applications 2.048 Mbps for indoor or low-range outdoor hotspot applications for WWAN solutions and 55 Mbps for WLAN solutions |
| Connection mode | Circuit and packet mode |
| Cell sizes | Regional megacells/worldcell greater than 35 km in radius Macrocells of radius 1 to 35 km Indoor or outdoor microcells of radius up to 1 km for WWAN solutions and 5 km for WLAN solutions Indoor or outdoor picocells of radius less than 50 m |
Forward-looking carriers and companies plan to use Bluetooth, IEEE 802.1a, 802.11b, and IEEE 802.15 to enable top-of-the-line locals and public spaces to achieve global reach over an intranet, extranet, or the Internet. This matches a hotspot service concept. Top-of-the-line buildings, hotels, airports, shopping malls, universities, hospitals, marinas, and other locales can avail themselves of wireless data technology and achieve global reach. Some of these companies support the planning, engineering, deployment, and operations of in-building networks (building PALs) as well as the metro-access, metro-core, long-haul, and Internet connectivity required for end-to-end services. Unlike the Building Local Exchange Carrier (BLEC) concept of the late 1990s, forward-looking companies intend to spend only a relatively small amount of money in each building (not to exceed $5,000 at most and often as little as $1,000) and in the network (for example, by using virtual LAN [VLAN] technology), thereby making the undertaking financially cost effective with a relatively small number of subscribers.
Unlike the technologies used in 3G, where European telecom firms have recently had to invest more than $100 billion to secure spectrum, leaving such companies cash strapped, the kinds of technologies used by hotspot service companies do not need licensing (whether the service is WPAN or WLAN based). However, in fairness, these technologies are short range and do not allow the multiple-mile links of the 2.5G/3G alternatives (at least for omnidirectional applications); however, the hotspot service is achieved with short-range radios in selected buildings or spaces connected to the network at large over terrestrial links such as a T1, Synchronous Optical Network (SONET), and/or fiber.
Nearly all hotspot applications to date are based on IEEE 802.11b technology. Some, however, also advance Bluetooth technology in this context. The Bluetooth Local Infotainment Point (BLIP) is a free-standing communications platform that uses Bluetooth technology to receive and transmit information. It is locally targeted, giving users access to situation- and location-specific services, thereby acting as a filter in the media clutter, according to proponents. Accessed by users’ mobile phones or PDAs, it lets users download images, music, and video files. The first version of BLIP had a range of general functions and is now commercially available, and more specialized versions are expected to be developed in the future. In recent trials in Japan, visitors equipped with Bluetooth-ready handheld computers or PCs and passengers in trains were able to gain location-based useful information with the push technology. Users gained access to contents such as streaming video and the Internet via the Bluetooth network.
Bluetooth proponents see the vast implications for the hotspot and believe that it represents a potential solution for service providers and location partners who want to communicate with the end users more cost effectively and attractively. IEEE-802.11b- and IEEE-802.15-enabled services are also contemplated for hotspots with 802.11b currently having a lead. However, compared to Bluetooth wireless technology, WLANs based on the IEEE 802.11 are more expensive and power consuming, and the hardware requires more physical space; the counterpoint is that the former supports distances of 1,500 feet (or even several miles in narrow beams), while the latter only supports 10 meters. Bluetooth is therefore more suitable for small mobile devices. Bluetooth technology is discussed in more detail in Chapter 3. Figure 1-9 shows connectivity ranges for various technologies.
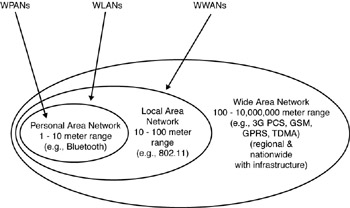
Figure 1-9: Ranges of various technologies
The convenience of wireless access, however, comes with security concerns that must be properly addressed.[22] When data is broadcast over radio waves, it can be intercepted and compromised. Thus, it is imperative to utilize robust security mechanisms to protect wireless communications. Security for IEEE 802.11 networks can be boiled down into three components: the authentication mechanism (or framework), the authentication algorithm, and data frame encryption. Authentication is the act of verifying a claimed identity in the form of a preexisting label from a mutually known name space as the originator of a message (message authentication) or the endpoint of a channel (entity authentication).[23] Encryption is the process of rendering the data impervious to scrutiny, except to those that possess the decryption key. In addition to security and privacy, other issues regarding wireless include input/output mechanisms, invisibility and social acceptance, battery power, and usability.
[19]Fixed broadband wireless multiservice WANs are also receiving some attention. Multichannel Multipoint Distribution Service (MMDS) and Local Multipoint Distribution Service (LMDS) and small dish satellite technologies can be used in this context.
[20]HIPERLAN/1 is an ETSI standard offering 20 Mbps LANs over 50 meters that operates at 5.12 to 5.30 GHz and 17.1 to 17.3 GHz. HIPERLAN/2 operates at 5.2 GHz with a 100 MHz spectrum. It supports 54 Mbps using orthogonal frequency division multiplexing (OFDM). It has quality of service (QoS) capabilities.
[21]New areas to track include 802.11a, 802.11e, and 802.11i.
[22]National security government installations (such as Lawrence Livermore National Laboratory, Aeronautical Radio [which provides communication services to airlines], and the U.S. Department of Transportation) were reassessing their use of Wi-Fi (USA Today, January 29, 2002, B1) at the time of this writing. Fortunately, there are military-grade encryption technologies that can be put in place where needed. IEEE 802.11b provides a data link layer and physical layer service; many people see encryption services as presentation layer services, which can be placed onto the network as needed.
[23]S. Glass, T. Hiller, S. Jacobs, and C. Perkins, “Mobile IP Authentication, Authorization, and Accounting Requirements,” RFC 2977, October 2000.
|
|
EAN: N/A
Pages: 88