The Security Design Process
There are several valid methodologies for conducting a security analysis and designing a solution that implements the appropriate security policies and technologies for your organization.
NOTE
The information in this section is extracted from Chapter 2 , "A Process for Building Secure Web Applications" of Michael Howard's book, Designing Secure Web-Based Applications for Microsoft Windows 2000 (Microsoft Press, 2000).
As Michael notes in his book, the security design process is iterative—as well as cyclical—because threats change rapidly and continuously. Figure 12.2 illustrates his security design process.
The purpose of the security design process is to develop the appropriate security solution for meeting your company's overall business and information requirements. As noted, different types of businesses will have different security goals and objectives, and their implementation of security services reflects those goals. (See the sidebar below.)
Another significant step in the security design process is conducting a risk assessment (see Figure 12.2). This assessment provides the basis for developing a security policy and selecting security technologies to support your organization's security services.
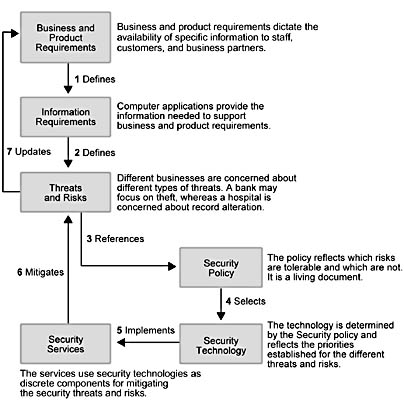
Figure 12.2 The process for determining security requirements and technologies
General security objectives and controls
Security objectives are the information requirements that a company implements in order to meet its business objectives. Here are the goals that most IT groups strive toward when dealing with business objectives and computer security:
- Integrity—Any data or information created and stored is complete and accurate. Integrity is required to support proper processing as well as to meet financial and reporting requirements.
- Availability—The system(s) must provide information on demand to the business process.
- Confidentiality—Sensitive information must be protected to prevent unauthorized access to the system and its data.
- Efficiency—Resources must be used in the most effective and efficient manner when providing information.
- Compliance—Information, and the processes used to create it, must comply with contracts and laws imposed by external business requirements.
Security controls provide the means by which you can meet your security objectives. There are three primary types of controls: preventing, detecting, and correcting.
- Preventing—The purpose of this control is to ensure that security vulnerabilities are not exposed.
- Detecting—This involves discovering when a security breach takes place.
- Correcting—These are measures that you take when a security hole or issue is detected.
Risk Assessment
In a nutshell, risk assessment is the process of analyzing your system(s) to determine:
- Whether or not your site is an attractive target—what is the likelihood that your site will be penetrated?
- The cost and consequences of a successful attack—what damages (tangible and intangible) are you likely to incur?
- The cost of security against probable attacks—what will it cost in terms of effort and dollars?
- Which threats should you defend against—since you likely can't address all of them, what are your priorities?
In order to conduct a sound risk assessment that reflects your company's business requirements and enables you to deploy secure applications, you need to understand the threats. You can use a basic taxonomy of attacks—threats that have been carried out—to provide the foundation for understanding and prioritizing threats. We recommend STRIDE, which is a more granular taxonomy that Microsoft uses. The STRIDE model includes:
- Spoofing user identity. The hacker impersonates a valid system user or resource to gain access to the system.
NOTE
Chapter 5, "Load Balancing," provides detailed information about custom header vulnerability to spoofing attacks when request forwarding is enabled. - Tampering with data (integrity). The attacker modifies system or user data with/without detection.
- Repudiability. A user can deny performing an action without administrators having a way to prove otherwise.
- Information disclosure (disclosure). A user has the ability to read a file that he was not granted access to, or an intruder can read data in transit between two computers.
- Denial of service. The attacker uses techniques that deny service to valid users by making a system temporarily unavailable or unuseable.
- Elevation of privilege. A user with low access privileges is able to gain undetected, privileged access to a system.
The following tables, taken from Chapter 2, "A Process for Building Secure Web Applications," of Michael Howard's book, Designing Secure Web-Based Applications for Microsoft Windows 2000, summarizes the countermeasures that can be applied to each threat in the STRIDE model (Table 12.2) and the Windows 2000 technologies that can be used to implement countermeasures (Table 12.3).
Table 12.2 Countermeasures Mapped to Each Threat in the STRIDE Model
| Threat | Countermeasures |
|---|---|
| Spoofing user identity | Strong authentication. Don't store secrets (such as passwords) in configuration files. If you must store secrets, use secure mechanisms. |
| Tampering with data | Strong access control mechanisms. Hashes/digital signatures on resources. End-to-end tamper-resistant data transfer protocols. |
| Repudiability | Secure logging. Digital signatures and time stamping. |
| Information disclosure | Strong access control mechanisms. Perform correct file canonical resolution. Limit specific file operations. End-to-end encrypted data transfer protocols. Don't store secrets (such as passwords) in configuration files. If you must store secrets, use secure mechanisms. |
| Denial of service | Bandwidth throttling. Resource throttling. Quality of service. Packet filtering. |
| Elevation of privilege | Run process in low privileged account. Safe buffer management. |
Table 12.3 Windows 2000 Technologies Mapped to the Countermeasures in Table 12.2
| Countermeasure | Technologies and best practices |
|---|---|
| Strong authentication | Don't design your own authentication scheme; most of the time such schemes are very weak and flawed. Use digest, certificates, or Kerberos authentication, if possible. |
| Storing secrets | Use the data protection APIs: CryptProtectData and CryptUnprotectData. |
| Access control | Use access control lists (ACLs) on resources, such as files and registry settings. |
| Hashes and digital signatures | CryptoAPI 2.0 provides functions such as signatures CryptHashData and CryptSignHash for creating hashes from data. |
| Secure end-to-end protocols | Secure Sockets Layer/Transport Layer Security protocol (SSL/TLS), which is built into most Web servers and browsers such as Microsoft Internet Explorer and IIS. Internet Protocol Security (IPSec), which is the industry-standard IP security protocol built into Windows 2000. |
| File access | Use the Windows 2000 functions to open files rather than writing your own. If you perform your own work, you may make incorrect assumptions about file names. |
| Limiting specific file operations | Consider whether '..' (parent operations directory) is allowed in a file name. Allowing this might enable an attacker to access files otherwise not accessible. |
| Bandwidth throttling | Windows 2000 thread pools. IIS bandwidth throttling. HTTP compression, built-in to IIS, conserves bandwidth and provides faster data transmission between the Web server and compression-enabled clients.1 |
| Resource throttling | IIS CPU throttling. IIS uses Windows 2000 job objects to perform this task. The Microsoft Developer Network (MSDN) describes a job object like so: "A job object allows groups of processes to be managed as a unit. Job objects are namable, securable, sharable objects that control attributes of the processes associated with them. Operations performed on the job object affect all processes associated with the job object." You can set CPU, time, user interface restrictions, and memory limits on a job object. |
| Quality of service (QoS) | Windows QoS controls how network bandwidth is allotted to applications; time-critical applications can be given more bandwidth, and less important applications can be given less bandwidth. |
| Packet filtering | Packet filtering is used to specify what type of traffic is allowed into and out of the computer. For example, you can limit a computer to accept only Web traffic (which uses TCP port 80) and ping traffic (which uses IMCP). |
| Buffer management | Windows 2000 structured exception handling and good programming practices, such as:
|
| Low privilege context | Run the application under a non-administrator and non-local-system account. Use restricted tokens, such as CreateRestrictedToken, to remove privileges and security identifiers (SIDs) from the user's token. Use Windows 2000 secondary logon. |
1. On Web sites that use a lot of dynamic content, the overhead for compressing/decompressing files may drastically affect your server's performance. Before you implement HTTP compression, you should read "Using HTTP Compression on Your IIS 5.0 Web Site" (Microsoft TechNet).
Threat Trees
One of the foremost techniques for risk assessment is the construction of a Threat Tree, which is formal methodology for analyzing systems and subsystems. The tree construct is used to represent the object that you're trying to protect and the potential threats to the object. This technique, presented by Ed Amoroso in his book, Fundamentals of Computer Security Technology (Prentice-Hall, 1994), steps you through the process of modeling security threats so you can develop a realistic view of your system's risk level. You can then use the tree to play "what if" games with potential countermeasures and select the appropriate countermeasure for a specific threat.
EAN: N/A
Pages: 183