The Nature of Security Breaches
When you're dealing with security, it's very easy to focus on the obvious sources and types of attacks—that is to say, external attacks with malicious intent. Don't assume, as others have, that this is the most common or most dangerous source of attack. The diagram in Figure 12.1 illustrates the three primary sources of security breaches, as well as some of the types of damage that an attacker can inflict on your organization.
As you can see in Figure 12.1, the three primary sources of attacks are:
- External attacks over a network, such as the Internet
- External attacks made by compromising dial-up access
- Internal attacks by using authenticated logons inside the organization
A survey conducted by Michael G. Kessler and Associates, a New York-based security firm, examined attacks from the perspective of the parties responsible for attacks—for example, hackers, business competitors, and so on. Table 12.1 summarizes the results of this survey.
NOTE
These survey results show how important it is to ensure that the back-end network for your cluster is secure. Remember, the back-end network adapter on every cluster member carries all the administrative traffic for an Application Center cluster.
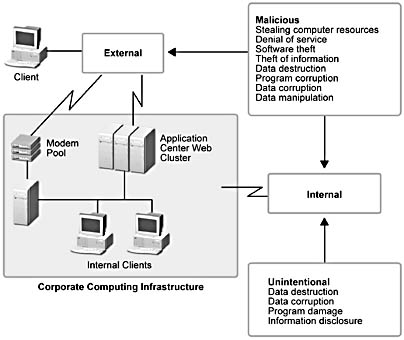
Figure 12.1 Sources of security attacks and types of damage
Table 12.1 Summary of Michael G. Kessler and Associates Security Survey
| Party responsible for attack | Percent |
|---|---|
| Employees | 35 |
| Outside hackers | 28 |
| Other U.S. companies | 18 |
| Foreign corporations | 11 |
| Foreign governments | 8 |
External Attacks—Network Access
The Internet provides an environment where a few individuals can create major security concerns for administrators whose systems are exposed to the public. External attacks from the Internet take many forms, such as disseminating viruses, defacing sites, and denial of service (DoS). The latter has become the attack of choice for hackers because this type of attack requires the least skill, is the hardest to defend against, and is very difficult to trace back to its source. The hacker doesn't have to penetrate deeply into a security perimeter; he simply has to overload a server to the point that it becomes unavailable to legitimate users. (See the sidebar below.)
Denial of Service (DoS)
Distributed Denial-of-Service (DDoS) attacksIn response to the growth in DDoS attacks this year, the SANS Institute published the following two documents, which can be obtained from their Web site:
- "Consensus Roadmap for Defeating Distributed Denial of Service Attacks"
- "Help Defeat Denial of Service Attacks: Step-by-Step"
Denial-of-service threat gets IETF's attention—July 24, 2000
In response to the seriousness of DoS attacks, the Internet Engineering Task Force (IETF) launched a working group to develop Internet Control Message Protocol (ICMP) trace-back messages, which would let network managers discover the path that packets take through the Internet. Nicknamed "itrace," this new tool will be based on a forthcoming IETF standard for trace-back messages.
Although itrace can't prevent DoS attacks, it will be an important tool for network managers who are trying to isolate and stop these attacks.
"Itrace is a pretty important initiative," says John Pescatore, research director for network security at Gartner Group. "What we need are standard mechanisms that can be built into the Internet switching infrastructure. That's the only place it will work to stop distributed denial-of-service attacks."
Deconstructing DoS attacks
Related to DoS, Bradley F. Shimmin of Bug Net (http://www.bugnet.com) published an article called "Deconstructing Denial of Service Attacks". This article, published on ZDNet (http://www.zdnet.com) in February 2000, uses the attack on Yahoo! to illustrate how you can analyze a DoS attack and implement preventive measures.
External Attacks—Remote Access
Remote access by using remote access and a dial-up or DSL/cable connection provides the second avenue for an external attack on corporate systems.
The general principle for remote access by employees is to ensure that everyone accessing your network has a connection that is properly authenticated and secured.
NOTE
Staff members who are engaged in remote system administration require stronger levels of authentication and encryption than the default levels for typical users.
Internal Attacks
When assessing the security of your computing environment, it's important to remember that not all attacks come from the outside, as clearly indicated by the Kessler and Associates survey (Table 12.1). In fact, security consultants from Network Associates Inc. (NAI) state that recent statistics indicate that internal attacks are on a dramatic upswing.
It's also important to note that not all internal attacks are intentional or necessarily malicious. The most valued and trusted employee can cause tremendous damage or significant downtime on a vulnerable system. You need to ensure that files, services, and applications are only accessible by users that should have access and that can provide the appropriate authentication information.
EAN: N/A
Pages: 183