Lesson 1: The Big Picture
Lesson 1: The Big Picture
A network is two or more machines interconnected for communications. This is a very simple view of a network, but it does help lay the groundwork for the big picture, which is today's networking and business environment.
Companies connect computers to share information and resources, providing better efficiency and productivity at a lower cost. Servers are computers that are built with a lot of computing power and data storage capacity so that they can answer requests from client computers on the network. Printers are an example of resources that can be added to the network and managed from the servers.
Client computers can connect to the servers so a company's employees can store and retrieve data, and print information to the network printers. The servers are backed up, and in the event of data loss, the information can be restored from the backup media. This provides the employees with the tools needed to do their job and provides an efficient, cost-effective, reliable work environment where the information the company generates is stored securely and is somewhat safe from equipment failure or user mishap.
To help employees be more productive, Internet access is configured. This allows a company's employees to communicate with people at other companies using instant messaging, e-mail, and many other methods. The other companies are connected to the Internet and sensitive data is transferred back and forth. The Internet provides a fast, inexpensive way to conduct business, so the company tries to conduct as much business as possible using the Internet.
When business is conducted, sensitive data is stored and transferred, and sensitive communications occur. Some opportunistic people might attempt to disrupt that business, steal or destroy the data, or exploit the communications.
As the "computer person" in a small company, a member of the Information Systems (IS) group at a larger company, or even just a regular user who enjoys surfing the Internet and e-mailing family and friends, you need to be aware of some information security basics. Even if you are not filling a high tech job, if you connect to the Internet, sensitive data you store on your system can be compromised. Your system can be used to attack or bring down other systems and your system can be infected with a virus that could harm operations.
If you are currently in or want to get a job in a high tech field, you must understand how to protect your company's assets (including the information stored on the computers), provide employees with the tools needed to perform their jobs, and provide a communications link with other companies and data sources. One of your first steps is to understand information security, its terms, and its concepts.
After this lesson, you will be able to
-
Understand what is at stake
-
Understand how to value your assets
-
Understand the goal of information security
-
Understand how to manage risk
Estimated lesson time: 20 minutes
What's at Stake
You might think that attacks are unlikely and that they do not cause too much damage. According to an article published on Newsfactor.com in February of 2001, Frank Bernhard of the University of California at Davis conducted a study of 3,000 U.S. businesses, and found that computer hackers and other security breaches cost businesses nearly 6 cents for every dollar of revenue. That is a lot of damage.
Valuing Your Assets
For every company, information has value. If every soft drink maker had the formula for Coca-Cola, everyone could make it and the Coca-Cola Company would have a harder time selling its product. For an airplane manufacturer, it might be the plans to a new jet that will revolutionize the airplane industry. Whatever the company and whatever the industry, there is information that needs to be protected and secure.
Just how important and valuable is your company's information? The following are some of the questions to ask that might help you understand the value:
-
What is the loss to my company's assets if the company's data is compromised?
-
What is the loss of intellectual property worth to my company?
-
What is the loss in revenue or market share?
-
What is the loss of privacy worth?
-
What is the damage to my company's reputation worth?
For every company, the value of information is different. For most companies, information is one of the top assets, if not the top asset they have. If a piece of hardware fails or the building the company is in gets damaged, the losses can be costly, but the equipment can be replaced or the damages repaired in most cases. However, if the information is destroyed, it is gone forever and cannot be replaced. This could cause irreparable damage. You must also realize that the value of information changes over its lifetime. Also, the value might be real or perceived.
- Real value.
Imagine you work for a company that makes tea. If your company has a formula for a special blend of tea and the yearly sales of that tea is $5 million, then you could say that formula has a value of $5 million. Five years from now, coffee might be more popular so the yearly sales of the tea might drop to $2 million. The value of the formula would have dropped from $5 million to $2 million. The information did not change, but the value of the information changed.
- Perceived value.
The tea company you work for has a very smart management and marketing group. The management team has a plan for collaborating with a distribution company to increase the availability of the tea across the world. The marketing team has an idea for a marketing campaign that will make the tea more popular and could slow the rise in popularity of coffee.
Having access to the management and marketing team's information would have value, but the value is not tangible, it is perceived. Regardless of whether information has a tangible or perceived value, it is your responsibility to protect the information. The higher the real or perceived value, the larger the target for theft.
Understanding the Goal of Security
The C-I-A triad, shown in Figure 1-1, is a common term used when talking about information security. C-I-A stands for
- Confidentiality.
Ensures that information is accessed only by authorized personnel.
- Integrity.
Ensures that information is modified only by authorized personnel.
- Availability.
Ensures that information and systems can be accessed when needed by authorized personnel.
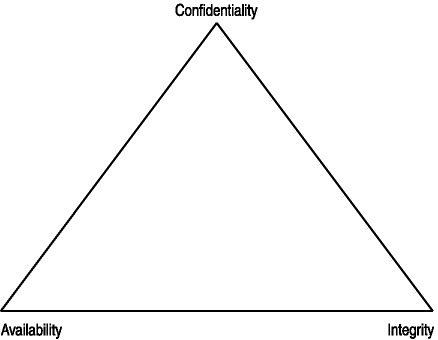
Figure 1-1. The C-I-A triad
When you combine efforts to provide data confidentiality, data integrity, and data availability with physical security you can provide a very effective security solution.
Throughout the rest of this book, the defenses presented protect against the threats described. The job of the IS specialist, especially the security specialist, is to provide highly available, reliable data to only those who should have access when they need access.
Managing Risk
Your company's information has value and must be available where and when needed, for use by authorized personnel. As a security expert, your job is to minimize the chance that the C-I-A triad will collapse.
Risk management, shown in Figure 1-2, is the complete process used to identify, control, and mitigate the impact of uncertain events. Because it is impossible to eliminate risk completely, the goal of risk management is to reduce risk and maintain the C-I-A triad. You do this by determining what the risks are, identifying threats and vulnerabilities, and then reducing them.
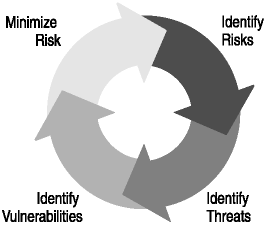
Figure 1-2. Risk management
You minimize risk by identifying the risks and creating a mitigation plan for those risks. Mitigation is defined as making something less harmful or less painful; therefore, you are planning to lessen your risks. For the tea company, the mitigation plan might be to limit the number of copies of the formula and number of locations in which it is stored. It might also include limiting the number of people that have access to the formula and how they can access it.
To minimize risk, you first identify the potential risks, threats, and vulnerabilities that your company faces.
-
Risk is the exposure to loss or possible injury. With information security, the risk is that your company's information will fall prey to outside forces and cause your company losses in time, money, and reputation.
With the tea company, the risk is that if the formula is compromised through exposure, other companies might start making a very similar tea. This would cause a loss in market share for the tea company. If the tea formula were commonly known and the value was in creating the tea inexpensively, then the risk due to loss of the formula would not be that great. The value would then be in the production process.
-
A threat, for information security, is any activity that represents possible danger to your information. Threats can take many forms, but any threat poses a danger to the C-I-A triad. In the example of the tea company, another company could steal the formula for the tea, or an employee could sell the formula to another company.
-
A vulnerability is a weakness in your information security that could be exploited by a threat; that is, a weakness in your systems and network security, processes, and procedures. With the tea company, the formula for the tea is the valued information. People have to have access to the formula to make the tea and the formula has to be stored somewhere.
Some of the vulnerabilities could include the location the formula is stored in, the number of people that need to have access to the formula, and where the formula is accessed.
Putting It All Together
For information security, you must protect the C-I-A triad, but you cannot protect it at any cost, and there is not always a need to protect information. For instance, if your company sells bottled water purified using the process of reverse osmosis, the process is well known, and therefore it does not make good business sense for you to protect that information. However, if your company has a revolutionary process that cuts the cost and time for water purification in half, it would make sense to secure that information. There is a limit to the value of implementing protection so you must combine your knowledge of value, threats, vulnerabilities, and risks to put together a feasible plan. To do this, follow this plan:
-
Place a value on the information.
-
Identify as many risks as possible and their associated threats and vulnerabilities.
-
Mitigate the identified risks.
-
Be aware that there are always things that you overlooked.
There is a limit to your ability to mitigate risk, and sometimes the cost or difficulty of reducing the risk is greater than the risk itself. For instance, if you work at a tea company and have a data file that contains all of the ingredients used to produce your entire line of tea products, it might not be worth the time, money, and effort to protect that information, because it is simply a laundry list of ingredients. However, if you have a recipe for your best-selling tea and your company is the only maker of that tea, it could be worth considerable time, effort, and money to protect that information. Every risk plan is different because every company has a different set of circumstances, budget, and workforce to use in minimizing risk. Some of the questions you can ask to help better identify the constraints that your company is working under include the following:
-
What information needs to be secured?
-
What is the value of the information?
-
What are the chances that the information can be compromised?
-
What is the cost to the company if the information is compromised?
-
In what manner is the information accessed?
-
How many people access the information?
-
Is the information easily secured?
Regardless of whether you decide to mitigate a risk, you should identify as many potential risks as possible and develop a mitigation plan that encompasses each of them. Once you identify the risks and assign a cost (in time and money) to secure the information, you can compare that with the information's value to determine what security measures are reasonable. For every situation, the risk management and trade-offs will be different. Using the tea company as an example, you might identify the following:
-
The value of the tea formula is $5 million because sales of the tea are $5 million.
-
The risk is that competitors might obtain the tea formula.
-
The threats are that someone from outside will locate and gain access to the tea formula, or an employee will gain access to the formula and sell it or give it to competitors.
-
The vulnerabilities are that the formula is stored in five different locations and that a large number of people have access to the formula.
-
To mitigate the risks, the formula could be stored in one location and made accessible, no one, but this is impractical. A better mitigation plan might be to reduce the number of locations to three and limit access to 25 people.
-
Things you might not have thought of would be to limit access to the area where the formula is used to produce the tea, post a list of the people who have access, and use a method to authenticate the people accessing the formula.
There are probably several additional threats, vulnerabilities, risks, and mitigations that you can identify. Identifying as many of these as possible is required of a good security specialist.

You are the security specialist for a small company that makes and sells scented candles. Your company sells these candles to retail stores, but also sell the candles over the Internet. The supplies that you use to make the candles are purchased over the Internet from four different suppliers. Your company has a remote sales force that works worldwide and accesses your internal network across the Internet. You also have employees who are allowed to work from home and access the company's network through a remote access solution.
The company does $12 million each year in sales, with $3 million in sales of everyday candles to retail stores, $2 million in sales of specialty scented candles that are only available on the Internet, and $7 million in sales of candle-making supplies.
In this exercise you need to:
-
Identify the value of the various parts of the business.
-
Identify as many threats as you can.
-
Identify as many vulnerabilities as you can.
-
Identify as many risks as you can.
-
Develop a risk management plan.
There are no definitive answers to this exercise. It was designed to encourage you to think about possible risks and how you might mitigate them. Throughout the book you will gain valuable information that you can use to provide a better, more detailed answer to this exercise. Record your answer now, and after completing this training kit, return to this exercise to realize the knowledge and expertise you have gained.

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
Although there is a need for information security, and there is a small chance of getting hacked, there is not normally any damage done and the cost to the company that is hacked is relatively minor. (True or False?)
-
You work for a company that sells tea and tea supplies. The total annual sales for the company are $5 million. The sales of tea total $2 million and the sales of tea supplies total $3 million. The tea has a very interesting taste that cannot be duplicated. Which of the following should be considered when placing a value on the tea formula, and why?
-
How the tea is produced
-
What the total annual sales of the tea is
-
Where the tea formula is stored
-
How many people in the company have access to the tea formula
-
-
You work for a company that sells tea and tea supplies. The total annual sales for the company are $5 million. The sales of tea total $2 million and the sales of tea supplies total $3 million. The tea has a very interesting taste that cannot be duplicated. The marketing group for your company has a marketing plan that is expected to double the sales of the tea from $2 million to $4 million. What is the real value of the tea formula? What is the perceived value of the marketing plan?
-
When talking about information security, what are the three cornerstones of the C-I-A triad?
-
List the sequence in which you perform the following steps when creating a risk management plan.
-
Identify the vulnerabilities to your C-I-A triad
-
Identify the value of your C-I-A triad
-
Identify the threats to your C-I-A triad
-
Identify how you can mitigate the risks
-
Lesson Summary
In this lesson, you learned that information security revolves around ensuring that your company's information security plan provides data confidentiality, data integrity, and data availability. The key points to remember are the following:
-
Confidentiality is assuring information is secure, with access limited to appropriate persons.
-
Integrity is ensuring information is not accidentally or maliciously altered or destroyed.
-
Availability is assuring information and communication services will be ready for use when expected.
-
To assure that your information plan maintains confidentiality, integrity, and availability, security is necessary. You must identify the possible threat and intrusion points, your vulnerabilities, the risk if your security plan fails, and ways to mitigate those risks by mounting a defense. To mitigate risks, you must determine a value for the information you are protecting and what the potential liability would be if that information were in the wrong hands. In doing this, you must understand the legal ramifications of what you do and ensure that the string of evidence remains intact to allow legal authorities to gather the necessary data and prosecute those responsible.
-
The C-I-A triad is a way to remember that the confidentiality, integrity, and availability of information is the concern of every IS specialist, and especially the security specialist.
EAN: 2147483647
Pages: 55