Lesson 3: Understanding Wireless Standards and Protocols
Lesson 3: Understanding Wireless Standards and Protocols
Wireless networking provides the opportunity for greater freedom of movement in the home or workplace. For home users, wireless networking can provide a solution to the complex job of stringing new Ethernet Category 5 cabling to multiple rooms. For corporate users, the ability to move throughout the workplace and continue to have access to networked resources is important. With the convenience of wireless access, however, comes the need to secure it.
Imagine yourself as the security manager for your company's network. You have just helped with the installation of wireless technology. You notice someone working with a notebook computer in the parking lot outside your building, but think nothing of it. You imagine it is probably just someone waiting to pick up a spouse or friend. Later you walk by and the same person is still there, so you ask that person what he or she is doing and find that the person is connected to your wireless network and accessing your network resources.
There is a technique very similar to war dialing that is known as war driving. War driving is when a person drives around businesses and neighborhoods attempting to locate a wireless access point (AP) by using a portable device running a utility that sniffs out and catalogs wireless APs.
To help secure your company's wireless access capability, you must understand the terminology, standards, and protocols that govern wireless technology development and implementation.
After this lesson, you will be able to
-
Explain how a wireless network operates in ad hoc or infrastructure mode
-
Understand the 802.11x standards and specifications
-
Understand the Wireless Access Protocol suite of protocols
-
Understand the security provided by the 802.1x standard
Estimated lesson time: 20 minutes
How Wireless Networking Works
Wireless networking is not unlike networking on cable. Computers can form a peer-to-peer network, or can be connected to form a client/server network. Hubs and switches can be used to connect network segments and allow communications over a broader area. Standards and protocols are employed so that the devices on the network operate in a common manner. If the computers that form the wireless network are running in ad hoc mode, however, they can communicate directly with one another without the need for an access point, as shown in Figure 5-6.
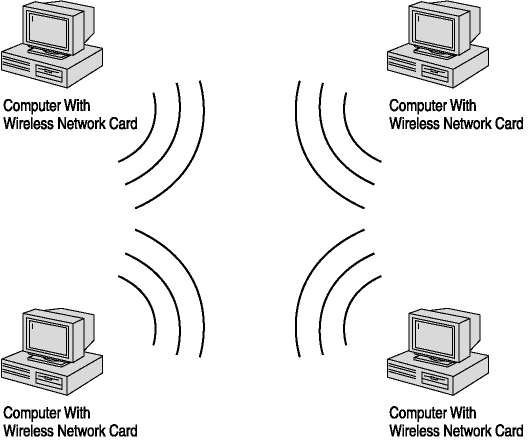
Figure 5-6. Wireless ad hoc networking
Ad hoc networking is not very scalable and offers little control over communications, but does provide the ability to form a peer-to-peer network with other wireless-enabled computers near you. To scale and provide some control over the communications, an access point (AP) can be introduced. This is a device that controls the communications flow between the wireless computers accessing it, and can forward communications to wired networks or other APs. This type of wireless networking is said to be running in infrastructure mode, as shown in Figure 5-7.
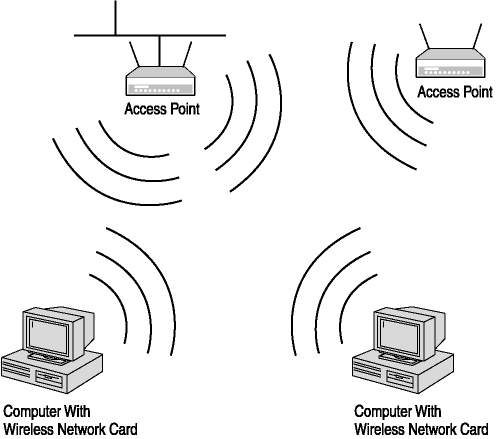
Figure 5-7. Wireless networking with an AP
Wireless Standards
Standards that govern the speeds and operation of wireless technology are governed by International Electrical and Electronics Engineers (IEEE) standards. The IEEE 802.11 standards cover wireless networking. Since being introduced, wireless speeds have increased dramatically. The following list provides some of the standards and their speeds:
- 802.11a.
Maximum speed 54 Mbps
- 802.11b.
Maximum speed 11 Mbps; fallback speeds 5, 2, and 1 Mbps
- 802.11g.
Maximum speed 22 Mbps; fallback speeds 11, 5, 2, and 1 Mbps
IEEE 802.11b devices are commonly used today and can transmit in the 2.4 GHz range at speeds of up to 11 Mbps and a range of up to 1500 feet outdoors. The standard requires the use of Direct Sequence Spread Spectrum (DSSS), which means that devices must synchronize with one another to use a pattern of frequency switching.
IEEE 802.11b networks, like their wired Ethernet counterparts, must also have some mechanism for data flow control to ensure that data does not get lost as a result of many computers trying to communicate with one another simultaneously. To this end, IEEE 802.11b uses Carrier Sense Multiple Access (CSMA) like typical Ethernet networks; however, it uses collision avoidance (CA), rather than collision detection. With CSMA/CA networks, devices wait until the channel is clear before sending the data. The receiving station sends an acknowledgment back to the sending system when it receives the frame. If the sending device does not receive an acknowledgment within a particular time, it retransmits the frame.
Communicating Across Multiple APs
Wireless networking allows a user to travel from room to room or building to building and stay connected to the network at all times. There are two different modes of communications that can be configured with wireless APs: basic service sets (BSS) and extended service sets (ESS).
BSS
When an AP exists, the wireless devices (notebooks and handhelds) no longer communicate in ad hoc mode. Instead, all traffic from one device destined for another device is relayed through the AP. Even though it seems like this would double the amount of traffic on the wireless local area network (WLAN), this also provides for traffic buffering on the AP when a device is operating in a low-power mode. With this model, the computers can only communicate through the AP they are close to and have selected.
ESS
The compelling force behind a WLAN deployment is the fact that with IEEE 802.11, users are free to move about without switching network connections manually. With a single infrastructure BSS, this moving about would be limited to the signal range of one AP. Through the ESS, the IEEE 802.11 architecture allows users to move among multiple infrastructure BSSs. In an ESS, the APs talk among themselves, forwarding traffic from one BSS to another, as well as switching the roaming devices from one BSS to another. They do this using a medium called the distribution system (DS). The DS forms the spine of the WLAN, making the decisions whether to forward traffic from one BSS to the wired network or back out to another AP or BSS.
Wireless Application Protocol
Wireless Application Protocol (WAP) provides a suite of protocols used for securing communications in layers 3 through 7 of the OSI model. The WAP communications model can be compared to the seven-layer OSI model; communication is broken into logical layers, and protocols are written to operate at those layers, as shown in Table 5-2. Understanding how some of these protocols provide support and security for your network will help you better secure your wireless network solution.
More information on WAP can be found at the Open Mobile Alliance Web site at http://www.wapforum.org.
| Layer | Protocol | Description |
| Application | Wireless Application Environment (WAE) | Wireless Markup Language (WML) protocol operates at this layer. |
| Session | Wireless Session Protocol (WSP) | Uses a token-based version of Hypertext Transfer Protocol (HTTP) to support operations over limited bandwidth. |
| Transaction | Wireless Transaction Protocol (WTP) | Supports multiple message types and limits the overhead of packaging sequencing. |
| Transport | Wireless Transport Layer Security (WTLS) | Security layer, based on standard Transport Layer Security (TLS) |
| Bearer | Wireless Datagram Protocol (WDP) | Provides a consistent interface between over-the-air protocols. |
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is the mechanism created in the IEEE 802.11b standard that utilizes a cryptographic security countermeasure to provide confidentiality, and has the added benefit of becoming an authentication mechanism. This benefit is realized through a shared key authentication that allows the encryption and decryption of the wireless transmissions. When high security is needed, other mechanisms, such as IEEE 802.1x, should be employed.
Most APs advertise that they support WEP in at least 40-bit encryption, but often the 128-bit option is also supported. For corporate networks, 128-bit encryption-capable devices should be considered as a minimum. With data security enabled in a closed network, the settings on the client for the Service Set Identifier (SSID) and the encryption keys have to match the AP when attempting to associate with the network, or it will fail.
WEP uses the RC4 encryption algorithm, where both the sender and receiver use the stream cipher to create identical pseudo-random strings from a known shared key. The sender logically performs the binary exclusive OR operation (XOR) on the plaintext transmission with the stream cipher to produce the ciphertext. The receiver takes the shared key and identical stream and reverses the process to gain the plaintext transmission.
For this process, a 24-bit initialization vector (IV) is used to create the identical cipher streams. The IV is a nonsecret binary vector used as the initializing input algorithm for the encryption of plaintext. The IV is produced by the sender, and is included in the transmission of each frame. A new IV is used for each frame to prevent the reuse of the key, weakening the encryption. This means that for each string generated, a different value for the RC4 key is used. Although a secure policy, consideration of the components of WEP bear out one of the flaws in WEP. Because the 24-bit space is so small with respect to the potential set of IVs, in a short period of time, all keys are eventually reused. This weakness exists for both the 40- and 128-bit encryption levels.
To protect against some rudimentary attacks that insert known text into the stream to attempt to reveal the key stream, WEP incorporates a checksum in each frame. Any frame not found to be valid through the checksum is discarded. This sounds secure, but WEP has well-documented flaws, which are covered in later sections.
The WEP Authentication Process
Shared key authentication is a four-step process that begins when the AP receives the validated request for association. After the AP receives the request, a series of management frames are transmitted between the stations to produce the authentication. This includes the use of the cryptographic mechanisms employed by WEP as a validation. Strictly with respect to WEP, in the authorization phase, the four steps break down in the following manner:
-
The requestor (the client) sends a request for association.
-
The authenticator (the AP) receives the request, and responds by producing a random challenge text and transmitting it back to the requestor.
-
The requestor receives the transmission, ciphers the challenge with the shared key stream, and returns it.
-
The authenticator decrypts the challenge text and compares the values against the original. If they match, the requestor is authenticated.
WEP Advantages and Disadvantages
WEP provides some security and privacy in transmissions to prevent curious or casual browsers from viewing the contents of the transmissions held between the AP and the clients. To gain access, the degree of sophistication of the intruder has to improve, and specific intent to gain access is required. Additional benefits of implementing WEP include the following:
-
All messages are encrypted using a checksum to provide some degree of tamper resistance.
-
Privacy is maintained through the encryption. If you do not have the key, you cannot decrypt the message.
-
WEP is easy to implement. Set the encryption key on the AP and repeat the process on each client.
-
WEP provides a very basic level of security for WLAN applications.
-
WEP keys are user definable and unlimited. You do not have to use predefined keys, and you can and should change them often.
As with any standard or protocol, WEP has some inherent disadvantages. The focus of security is to allow a balance of access and control while juggling the advantages and disadvantages of each implemented countermeasure for security gaps. The following are some of the disadvantages of WEP:
-
The RC4 encryption algorithm is a known stream cipher. This means it takes a finite key and attempts to make an infinite pseudo-random key stream to generate the encryption.
-
Once you alter the key you have to tell everyone so they can adjust their settings. The more people you tell, the more public the information becomes.
-
Used on its own, WEP does not provide adequate WLAN security.
-
WEP must be implemented on every client as well as every AP to be effective.
Security Implications of Using WEP
From a security perspective, WEP can be used to deter curious hackers, but used alone, it will not stop determined hackers. Because WEP relies on a known stream cipher, it is vulnerable to certain attacks. By no means is it the final authority, and it should not be the only security countermeasure in place to protect your network. Some of the security challenges faced with wireless networks include the following:
-
With wireless communication, it would be a relatively easy matter to put together the hardware to allow an eavesdropper to pick up signals in open, unsecured areas without having physical access to the interior of a building. Therefore, physical security is more challenging.
-
Users might have the need to move between wireless zones without having to reconfigure components. In situations in which the wireless zone is in a different administrative domain, users should be able to contact the appropriate domain controller, even if that zone is, for example, located in an airport or another office that provides wireless connectivity.
Security of 64-Bit versus 128-Bit Keys
It might seem obvious to a nontechnical person that something protected with a 128-bit encryption scheme would be more secure than something protected with a 64-bit encryption scheme. This, however, is not the case with WEP. Because the same vulnerability exists with both encryption levels, they can be equally broken within similar time limits.
With 64-bit WEP, the network administrator specifies a 40-bit key, typically 10 hexadecimal digits (0 9, a f, or A F). A 24-bit IV is appended to this 40-bit key, and the RC4 key scheme is built from these 64 bits of data. This same process is followed in the 128-bit scheme. The administrator specifies a 104-bit key this time 26 hexadecimal digits (0 9, a f, or A F). The 24-bit IV is added to the beginning of the key, and the RC4 key schedule is built.
Acquiring a WEP Key
As mentioned previously, programs exist that allow an authenticated or unassociated device within the listening area of the AP to capture and recover the WEP key. Depending on the speed of the machine listening to the wireless conversations, the number of wireless hosts transmitting on the WLAN, and the number of IV retransmissions due to 802.11 frame collisions, the WEP key could be cracked within a couple of hours. If an attacker attempts to listen to a WEP-protected network when there is very little network traffic, it would take much longer to obtain the data necessary to crack WEP.
Armed with a valid WEP key, an intruder can successfully negotiate association with an AP and gain entry onto the target network. Unless other mechanisms such as media access control (MAC) filtering are in place, this intruder is now able to roam across the network and potentially break into servers or other network machines. If MAC filtering is occurring, another procedure must be attempted to get around this.
Wireless Transaction Layer Security
WTLS is the security layer of the WAP, providing privacy, data integrity, and authentication for WAP services. WTLS, designed specifically for the wireless environment, is required because the client and the server must be authenticated for wireless transactions to remain secure and because the connection needs to be encrypted. For example, a user making a bank transaction over a wireless device needs to know that the connection is secure and private and not subject to a security breach during transfer (sometimes referred to as a man-in-the-middle attack). WTLS is necessary because mobile networks do not provide complete end-to-end security.
WTLS is based on the widely used TLS v1.0 security layer used in Internet communication. Because of the nature of wireless transmissions, modifications were made to TLS v1.0 to accommodate for the low bandwidth, datagram connection, limited processing power and memory capacity, and cryptography exporting restrictions of wireless transmissions. The WTLS classes of security are as follows:
-
Class 1: Anonymous authentication
-
Class 2: Server authentication
-
Class 3: Two-way client and server authentication
Security in the WLAN
Data security is one of the biggest concerns facing network administrators when implementing a WLAN. In a wired environment, the lack of access to the physical wire can prevent someone from wandering into your building and connecting to your internal network. In a WLAN scenario, it is impossible for the AP to know if the person operating the wireless device is sitting inside your building, passing time in your lobby, or sitting in a parked car just outside your office. Acknowledging that passing data across an unreliable radio link could lead to possible snooping, the IEEE 802.11 standard provides three ways to ensure a greater amount of security for the data that travels over the WLAN. Adopting any (or all three) of these mechanisms decreases the likelihood of an accidental security exposure.
The first method makes use of the 802.11 SSID. This SSID can be associated with one or more APs to create multiple WLAN segments within the infrastructure BSS. These segments can be related to floors of a building, business units, or other data-definition sets. Because the SSID is presented during the authentication process, it acts as a crude password. Because most end users set up their wireless devices, these SSIDs could be shared among users, thus limiting their effectiveness. Another disadvantage to using SSIDs as a sole form of authentication is that if an SSID were to be changed (due to an employee termination or other event, for example), all wireless devices and APs would have to reflect this change. On a medium-sized WLAN, rotating SSIDs on even a biannual basis could prove to be a daunting and time- consuming task.
As mentioned earlier, the AP also can authenticate a wireless device against a list of MAC addresses. This list could reside locally on the AP, or the authentication could be checked against a database of allowed MACs located on the wired network. This typically provides a good level of security, and is best used with small WLAN networks. With larger WLAN networks, administering the list of allowable MAC addresses requires some back-end services to reduce the amount of time needed to make an addition or subtraction from the list.
The third mechanism IEEE 802.11 offers to protect data traversing the WLAN was also mentioned earlier. The privacy service uses an RC4 based encryption scheme, or WEP, to encapsulate the payload of the 802.11 data frames. WEP specifies a 40-bit encryption key, although some vendors have implemented a 104-bit key. As mentioned previously, WEP is not meant to be an end-to-end encryption solution. WEP keys on the APs and wireless devices can be rotated, but because the 802.11 standard does not specify a key-management protocol, all key rotation must be done manually. Like the SSID, rotating the WEP key would affect all APs and wireless users and take significant effort from the network administrator.
Understanding 802.1x
IEEE 802.1x is a standard for port-based network access control that provides authenticated network access to 802.11 wireless networks and wired Ethernet networks. That is, these standards allow for additional authentication methods. Port-based network access control uses the physical characteristics of a switched LAN infrastructure to authenticate devices that are attached to a LAN port and to prevent access to that port when the authentication process fails.
During a port-based network access control interaction, as shown in Figure 5-8, a LAN port adopts one of two roles: authenticator or supplicant. In the role of authenticator, a LAN port enforces authentication before it allows user access to the services that can be accessed through that port. In the role of supplicant, a LAN port requests access to the services that can be accessed through the authenticator's port. An authentication server, which can either be a separate entity or colocated with the authenticator, checks the supplicant's credentials on behalf of the authenticator. The authentication server then responds to the authenticator, indicating whether the supplicant is authorized to access the authenticator's services.
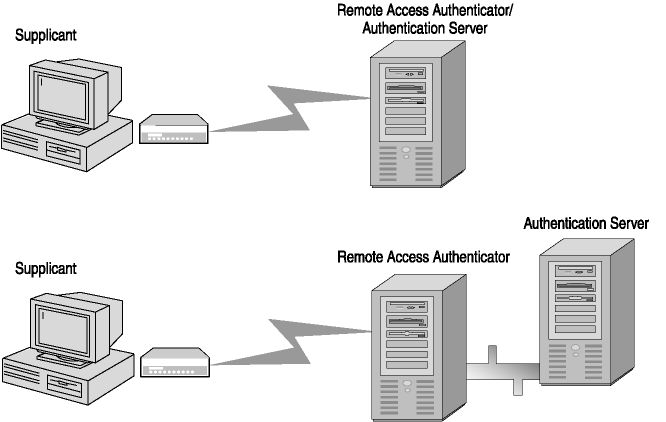
Figure 5-8. Remote access authentication roles
The authenticator's port-based network access control defines two logical access points to the LAN through one physical LAN port. The first logical access point, the uncontrolled port, allows data exchange between the authenticator and other computers on the LAN, regardless of the computer's authorization state. The second logical access point, the controlled port, allows data exchange between an authenticated LAN user and the authenticator.
IEEE 802.1x uses standard security protocols, such as RADIUS, to provide centralized user identification, authentication, dynamic key management, and accounting. When a client device connects to a port on an 802.1x switch and AP, the switch port can determine the authenticity of the devices. Due to this, and according to the protocol specified by 802.1x, the services offered by the switch can be made available on that port. Only Extensible Authentication Protocol over LAN (EAPOL) frames can be sent and received on that port until the authentication is complete. When the device is properly authenticated, the port switches traffic as though it were a regular port. Some terminology for the 802.1x standard that you should familiarize yourself with includes the following:
- Port.
A port is a single point of connection to the network.
- Port Access Entity (PAE).
The PAE controls the algorithms and protocols that are associated with the authentication mechanisms for a port.
- Authenticator PAE.
The authenticator PAE enforces authentication before it allows access resources located off that port.
- Supplicant PAE.
The supplicant PAE tries to access the services that are allowed by the authenticator.
- Authentication Server.
The Authentication Server is used to verify the supplicant PAE. It decides whether the supplicant is authorized to access the authenticator.
- Extensible Authentication Protocol over LAN (EAPOL).
The 802.1x standard defines a standard for encapsulating EAP messages so that they can be handled directly by a LAN MAC service. 802.1x tries to make authentication more encompassing, rather than enforcing specific mechanisms on the devices. Because of this, 802.1x uses EAP to receive authentication information.
- Extensible Authentication Protocol over Wireless (EAPOW).
When EAPOL messages are encapsulated over 802.11 wireless frames, they are known as EAPOW.
With the addition of the 802.1x standard, clients are identified by user names, not the MAC address of the devices. This facet was designed not only to enhance security, but also to streamline the process for authentication, authorization, and accountability for your network. 802.1x was designed so that it could support extended forms of authentication, using password (that is, one-time password or Kerberos) and nonpassword (that is, biometrics, IKE, smart card) methods.

In this exercise, you match the wireless standard with the maximum speed it supports.
|
|

Match the term in the left column with the most appropriate statement in the right column.
|
|

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
What is the maximum transport speed supported by the 802.11b standard?
-
2.4 GHz
-
2 Mbps
-
11 Mbps
-
10 Mbps
-
-
What is the encryption method employed by WEP? What is the maximum bit encryption supported?
-
RC4
-
RC5
-
64-bit encryption
-
128-bit encryption
-
Lesson Summary
-
IEEE 802.11b devices can transmit in the 2.4 GHz range at speeds of up to 11 Mbps and a range of up to 1500 feet outdoors.
-
The IEEE 802.11 standard provides three ways to provide a greater amount of security for the data that travels over the WLAN: using SSIDs, providing a mechanism to authenticate wireless users, and employing encryption capabilities.
-
WEP utilizes the RC4 encryption algorithm to provide up to 128-bit encryption and also provides the added benefit of becoming an authentication mechanism.
-
WAP is a transport protocol used with wireless networking, and most application development for wireless applications uses WML.
-
WTLS is the security layer of the WAP, providing privacy, data integrity, and authentication for WAP services.
-
IEEE 802.1x is a standard for port-based network access control that provides authenticated network access to 802.11 wireless networks and wired Ethernet networks.
-
During a port-based network access control interaction, a LAN port adopts one of two roles: authenticator or supplicant. In the role of authenticator, a LAN port enforces authentication before it allows user access to the services that can be accessed through that port. In the role of supplicant, a LAN port requests access to the services that can be accessed through the authenticator's port.
EAN: 2147483647
Pages: 55