Lab 9-1: Planning Security for Network Services

Lab Objectives
This lab prepares you to design security for common Windows 2000 network services by meeting the following objectives:
- Design security for the DNS Service
- Design security for the DHCP Service
- Design security for RIS
- Design security for the SNMP Service
- Design security for Terminal Services
About This Lab
This lab looks at the design of the DNS, DHCP, RIS, SNMP, and Terminal Services for Contoso Ltd. to ensure that security is maintained for the deployment of these services.
Before You Begin
Make sure that you've read the chapter material before starting the lab. Pay close attention to the sections where the design decisions were applied throughout the chapter for information on building your administrative structure.
Scenario: Contoso Ltd.
Contoso Ltd., an international magazine sales company, wants to ensure that network services deployed on the corporate network don't compromise the security of the network. Specifically, Contoso wishes to design security for the following services:
- DNS
- DHCP
- RIS
- SNMP
- Terminal Services
The Planned DNS Environment for Contoso Ltd.
Contoso has deployed DNS to support Active Directory. The DNS deployment provides name resolution for both internal and external clients. This name resolution is accomplished in the following manner:
- The DNS servers at the London office host the contoso.tld DNS domain and are made available to both internal and external network users. The contoso.tld domain is configured as an Active Directory–integrated zone with the properties shown in Figure 9.15.
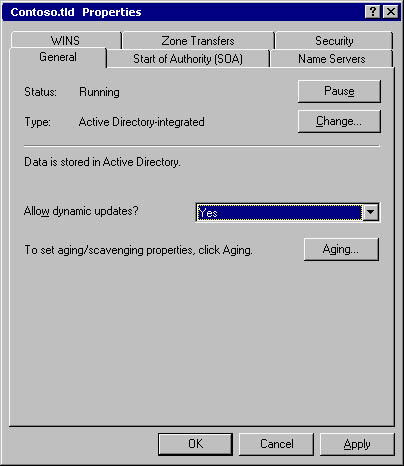
Figure 9.15 DNS configuration for the contoso.tld domain
- The subdomains london.contoso.tld, seattle.contoso.tld, and lima.contoso.tld are delegated to DCs located at the London, Seattle, and Lima offices. The subdomains are configured as Active Directory–integrated zones.
- Contoso uses the 172.28.0.0/16 network for their internal IP addressing scheme.
- During the design phase of the Contoso network, the network engineers developed the following security requirements for the DNS deployment:
- Only authenticated clients will be allowed to register DNS resource records using dynamic update.
- Only the following DNS resource records should be available to external clients connecting to contoso.tld Internet resources:
- mail.contoso.tld. A host record that refers to the external mail address of the Internet gateway mail servers
- www.contoso.tld. A host record that references the external Web server Network Load Balancing Service (NLBS) cluster address
- contoso.tld. A host record that references the external Web server in case someone doesn't type the prefix www
- vpn.contoso.tld. A host record that references the virtual private network (VPN) server used by the remote sales force to connect to the network
- An MX record that indicates that mail.contoso.tld is the mail exchanger for contoso.tld
- Standard Name Server (NS) and Start of Authority (SOA) resource records for the contoso.tld domain
- Only approved DNS servers can host DNS zone information for contoso.tld, london.contoso.tld, seattle.contoso.tld, and lima.contoso.tld.
The following table shows the UP addresses of all approved DNS servers. By default, the DNS servers host only Active Directory–integrated zones for the domain that they are a member of.
DNS Server IP Address Ns1.contoso.tld 172.28.1.2 Ns2.contoso.tld 172.28.1.3 Ns3.london.contoso.tld 172.28.5.2 Ns4.london.contoso.tld 172.28.5.3 Ns4.seattle.contoso.tld 172.28.9.2 Ns5.seattle.contoso.tld 172.28.9.3 Ns6.london.contoso.tld 172.28.13.2 Ns7.london.contoso.tld 172.28.13.3
DHCP Usage at Contoso Ltd.
Contoso uses a centralized deployment for DHCP IP address assignment. DHCP services are installed on member servers in the london.contoso.tld andseattle.contoso.tld domains. The Lima office has the DHCP Service installed on a DC.
Only client computers in the london.contoso.tld, seattle.contoso.tld, and lima.contoso.tld domains are configured to be DHCP clients. The DHCP server is configured to update DNS clients that don't perform dynamic updates. The plan is to replace all legacy client computers with Windows 2000 Professional–based computers. Therefore, DHCP servers are configured as members of the DNSUpdateProxy group to prevent the DHCP server from taking ownership of any DNS resource records it registers on behalf of down-level clients.
Contoso has several distribution plants where magazine shipments originate. These sites are Barcelona, Yokohama, and Perth. The remote office routers are configured as DHCP Relay agents, and the DHCP requests are forwarded to the nearest central office.
Last month the Barcelona office was unable to communicate with other offices when a new employee studying for his Microsoft Certified Professional designation installed the DHCP Service on a Windows NT 4.0 server. The DHCP server issued incorrect IP addressing information to the Barcelona clients. To avoid such problems in the future, Contoso plans to prevent unauthorized DHCP servers from assigning incorrect IP address information.
Remote Installation Services Deployment
Contoso plans to use RIS to deploy updated client computers and reduce the time the Information Technology (IT) department spends installing the new computers. The new client computers all have PXE-enabled network adapters installed to facilitate the deployment of RIS images.
Separate RIS images will be created for the Sales, Marketing, IT, and Accounting departments. For offices where users choose the RIS image, only the image for their department should be presented when the user runs the RIS client installation.
Due to the large number of client computers (300) requiring upgrades to Windows 2000 at the London office, Contoso wants users to install the RIS images themselves. When the RIS image is installed, the computer account that is created should be placed into the correct OU structure, as shown in Figure 9.16.

Figure 9.16 Proposed OU structure for RIS clients in the Seattle domain
The Seattle and Lima offices will use prestaged computer accounts and ensure that the computer accounts are precreated in the correct OU structure.
Network Management Plans for Contoso Ltd.
Contoso has purchased HP OpenView to enable SNMP network management on their network. Contoso will use SNMP to manage all servers, client workstations, and network devices on the network.
Contoso will deploy SNMP management using a hybrid model. The WAN management team at the London office must be able to query all network devices and reconfigure network devices on the network from the London office. All WAN management will take place from the HP OpenView UNIX console located at IP address 172.28.2.254. The London Windows 2000 deployment team also needs to be able to query information from all Windows 2000–based computers at all three office locations. The Windows 2000 deployment team requires only Read access to the Windows 2000–based computers. All management of the Windows 2000–based computers will take place from an HP OpenView console installed on a DC at IP address 172.16.3.254.
NOTE
The routers currently used on Contoso's network don't support IPSec encryption.
Each of the three offices have network administrators who need to query all servers, clients, and network devices located at their offices. These network administrators require only Read access to all SNMP agents in their local network. The following table outlines the IP address for each of the HP OpenView consoles:
| Office | Management Station |
|---|---|
| London | 172.28.6.254 |
| Seattle | 172.16.10.254 |
| Lima | 172.16.14.254 |
If any unauthorized SNMP management stations attempt to manage SNMP agents, an SNMP trap should be sent to any configured SNMP management stations for the community in which the SNMP request is sent.
As part of the initial design, Contoso has developed four SNMP communities to meet the SNMP design requirements. The SNMP community design is shown in Figure 9.17.
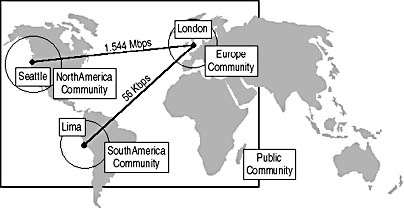
Figure 9.17 Proposed SNMP community names for Contoso Ltd.
Using Terminal Services
Terminal Services has been deployed at each of the three offices to allow both application access and remote network management.
At the London and Seattle offices, remote administration of the network is accomplished by using Terminal Services. No users require access to Terminal Services for running applications.
The Lima office requires both remote administration of the network and application support for clients. The clients who require access to Terminal Services in the Lima office include the 20 Wyse Winterm (hardware-based Terminal Services) clients on the shop floor and the 10 Windows for Workgroups 3.11 clients who require immediate use of Windows 2000–approved software.
The Winterm clients require only access to the Time Billing application. As the magazines are printed, the Time Billing application records how long it takes to produce each production run of a magazine and how many magazines are printed in the run. The Winterm clients won't require access to any other applications.
The Windows for Workgroups clients need to connect to the terminal server by using their Web browser. The 10 users who access the terminal server require distinct permission assignments because they're editing sensitive legal documents. Each user will be able to access only specific documents. The Windows for Workgroup clients must have access to the standard Windows 2000 Professional screen so that they can run Office 2000 in the Terminal Services session.
Figure 9.18 shows the initial Terminal Services environment proposed for the Lima office. All Terminal Services clients will connect to the Terminal Services member server at the Lima office.
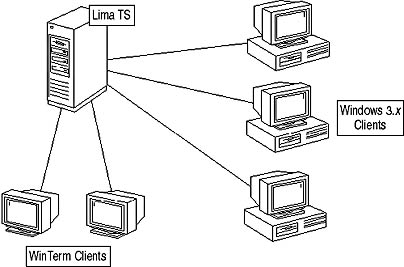
Figure 9.18 Proposed Terminal Services environment for the Lima office
Exercise 1: Designing DNS Security
In this exercise you will review the security of Contoso's DNS design. The answers to these questions can be found in the appendix.
- Are there any security issues with the configuration of the contoso.tld Active Directory–integrated zone? If so, what change must you make to the DNS zone properties?
- What security risks for exposure of resource records on the Internet does the current DNS configuration for contoso.tld have?
- What modification is required to increase security for external DNS requests?
- To ensure that the contoso.tld DNS domain is available at all locations even if a WAN link is unavailable, Contoso has decided to make the contoso.tld DNS zone available at all corporate DNS servers. What form of DNS zone must you configure in the London, Seattle, and Lima domains?
- What must you do to secure the zone transfers of the contoso.tld DNS zone to the child domains?
- What must you do to prevent unauthorized zone transfers from the DNS servers located in the London, Seattle, and Lima domains?
Answers
Exercise 2: Designing DHCP Security
In this exercise you will review Contoso's DHCP design and identify security weaknesses. You will complete the exercise by proposing alternatives that will increase security of the DHCP server. The answers to these questions can be found in the appendix.
- What risks are there with the DHCP Service in Lima being installed on a DC?
- How does membership in the DNSUpdateProxy group affect the SRV resource records registered by the DC hosting the DHCP Service?
- What would you recommend to Contoso to improve the DHCP security at the Lima office?
- Why was the DHCP server at the Barcelona office allowed to reply to DHCP requests even though the DHCP server wasn't authorized in Active Directory?
- What could be done to prevent unauthorized DHCP servers on the Contoso network?
Answers
Exercise 3: Designing RIS Security
In this exercise you will review the RIS deployment plan for Contoso to determine whether any security configurations are missing. The answers to these questions can be found in the appendix.
- During the pilot project, many users installed the incorrect image when they performed the RIS client setup. How can Contoso ensure that users in the London office install the correct image based on their departmental membership?
- What security assignments must take place to limit users so that they can install only the RIS image associated with their department?
- Can a single RIS server meet the security requirement to create the necessary computer accounts in the correct OU based on department?
- What security configuration is required at the RIS servers at the Lima and Seattle offices to prevent unauthorized RIS client installations?
- What permissions on computer objects will the user accounts require to install the RIS images at the Seattle and Lima offices?
Answers
Exercise 4: Designing SNMP Security
In this exercise you will review the proposed SNMP design for Contoso and modify it to meet the company's security requirements. The answers to these questions can be found in the appendix.
- Do the four proposed communities, Public, NorthAmerica, SouthAmerica, and Europe, meet the SNMP security requirements?
- What risks are involved with using the default community name Public? What permissions can you assign to this community to limit risk?
- Complete the following table to show the required community names and permissions that must be assigned to each community name.
Community Permissions - What SNMP configuration must you perform to restrict SNMP management tasks only to approved SNMP management stations?
- Which communities and SNMP management station IP addresses should you configure Windows 2000 clients at the London office to send SNMP authentication traps to?
- Could you use IPSec to protect SNMP status messages and SNMP trap messages for any of the communities? What must you configure in the IPSec rule?
Answers
Exercise 5: Designing Terminal Services
In this exercise you will review the proposed Terminal Services design for Contoso and modify the design to meet security requirements. The answers to these questions can be found in the appendix.
- What mode must Terminal Services use on DCs in the London and Seattle domain to make sure that only administrators can use Terminal Services?
- If you wanted to enforce that the shell is replaced with the Time Billing ap-plication for the Winterm clients at the terminal server, does the proposed Terminal Services deployment support both the Winterm and Windows for Workgroups Terminal Services clients?
- What risks are there in configuring the shell replacement for the Winterm clients at the clients?
- How would you ensure that the Windows for Workgroups clients are allowed access only to resources based on their individual and group membership permissions?
- What minimum level of encryption is required for the Windows for Workgroups clients when connecting to the terminal server?
Answers
EAN: 2147483647
Pages: 172