Lesson 3: NTLM Authentication
Only Windows 2000 clients and UNIX clients can use Kerberos authentication in a Windows 2000 domain. To provide access to Windows NT 4.0 clients and Windows 95 and Windows 98 clients running the Directory Service client, Windows 2000 continues to support the use of the Windows NT LAN Manager (NTLM) authentication protocol.
After this lesson, you will be able to
- Design NTLM authentication for Windows 2000–based clients and down-level clients in a Windows 2000 network
Estimated lesson time: 30 minutes
Designing NTLM Authentication
In addition to providing NTLM authentication for down-level clients, NTLM is also used to authenticate logons to Windows 2000 computers that aren't participating in a domain or when authentication against the local account database of a member server or Windows 2000 Professional computer takes place.
In the last few years, security weaknesses were found with the NTLM protocol. Password crackers were developed that were able to decrypt NTLM-protected authentication. To counteract this, NTLM version 2 was developed for Windows NT 4.0 Service Pack 4. NTLMv2 introduces additional security features, including
- Unique session keys per connection. Each time a new connection is established, a unique session key is generated for that session. This way a captured session key will serve no useful purpose after the connection is completed.
- Session keys protected with a key exchange. The session key can't be intercepted and used unless the key pair used to protect the session key is obtained.
- Unique keys generated for the encryption and integrity of session data. The key that's used for the encryption of data from the client to the server will be different from the one that's used for the encryption of data from the server to the client.
Figure 3.10 shows how NTLMv2 authentication takes place.
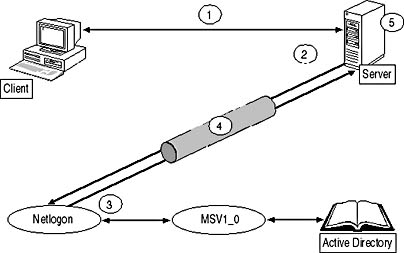
Figure 3.10 NTLM authentication
In this environment the client is connecting to a server. Active Directory uses the MSV1_0 sub-authentication filter to perform the authentication.
- The NTLM challenge response is sent from the client computer to the server that the client is connecting to.
- The application server uses the local security authority (LSA) to log on to the domain using the Netlogon service.
- The Netlogon service queries Active Directory using the MSV1_0 sub-authentication filter to validate the user.
- If the user is validated, the Netlogon service returns the user and group SIDs from the authenticating DC back to the server.
- For the logon process, NTLMv2 introduces a secure channel to protect the authentication process.
Making the Decision
Because Kerberos authentication is available only to Windows 2000 client computers, your network design must ensure that the next strongest form of authentication is available to non-Windows 2000 client computers and Windows 2000 client computers.
Clients use NTLMv2 authentication in the circumstances shown in Table 3.4.
Table 3.4 Determining when NTLMv2 Authentication is Used
| Client | Use NTLMv2 when |
|---|---|
| Windows 2000 | Authenticating to the local SAM database of a stand-alone Windows 2000–based computer Authenticating with a Windows NT 4.0 computer with SP4 or higher installed |
| Windows NT 4.0 | Authenticating with Windows 2000 and Windows NT 4.0 servers and the client has Service Pack 4 or higher applied Authenticating with Windows 2000 and Windows NT 4.0 servers and the client has the Directory Services Client installed |
| Windows 95/Windows 98 | Authenticating with Windows 2000 and Windows NT 4.0 servers and the client has the Directory Services Client installed |
Applying the Decision
The Market Florist network has a combination of Windows NT 4.0 Workstation and Windows 95 clients that are unable to use Kerberos when authenticating with the network.
Based on the scenario, Market Florist must include the deployment of the Directory Services Client only to the Windows 95 clients to ensure that all non–Windows 2000 clients on the network use NTLMv2 authentication. The Windows NT 4.0 Workstation clients won't require the Directory Service Client software to enable NTLMv2 authentication because the clients had the latest service pack applied for Year 2000 compliance. This doesn't mean that there isn't a business case to distribute the Directory Service Client software to Windows NT 4.0 workstations. It only means that the Windows NT 4.0 clients don't require the Directory Service Client software to ensure that NTLMv2 is used for authentication.
Lesson Summary
NTLM authentication is still used in a Windows 2000 network. Be sure that you know when NTLM authentication is used and plan the deployment of the Directory Services Client software to ensure that Windows 95, Windows 98, and Windows NT 4.0 clients can use the added security of NTLMv2 authentication. When Kerberos can't be used, NTLMv2 provides strong authentication security.
EAN: 2147483647
Pages: 172
- Structures, Processes and Relational Mechanisms for IT Governance
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT
- Governance Structures for IT in the Health Care Industry