Lab 15-1: Designing Secure Internet Access

This lab requires you to develop a design for providing secure Internet Access to the private network users of the Contoso Ltd. network.
Lab Objectives
This lab prepares you to develop a security design that provides secure Internet access to private network users by meeting the following objectives:
- Develop a security plan to restrict access to Internet resources based on an Internet acceptable use policy
- Limit access to the Internet to only authorized users
- Limit access to the Internet to only authorized protocols
- Restrict the types of content that can be downloaded to private network computers
- Design an auditing strategy for Internet access
About This Lab
This lab examines the process of securing Internet access for Contoso Ltd. private network users. In this lab you will develop an Internet acceptable use policy that matches the risk levels that Contoso deems appropriate. You will then develop a network design that enforces the Internet acceptable use policies.
Before You Begin
Make sure that you've completed reading the chapter material before starting the lab. Pay close attention to the sections where the decisions are applied throughout the chapter for information on designing your administrative structure.
Scenario: Contoso Ltd.
Contoso Ltd., an international magazine sales company, wants to provide Internet access for their private network users. Figure 15.17 shows the network infrastructure that's been approved for the Contoso network.
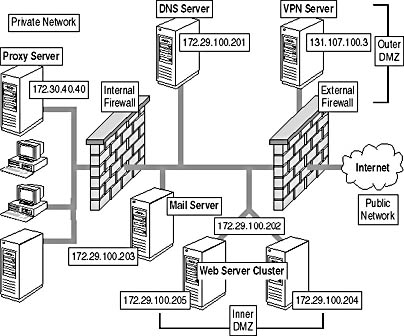
Figure 15.17 The Contoso Ltd. private network and DMZ configuration
The Proxy Server is located on the private network so that the internal firewall can limit which protocols are allowed to exit the private network.
Firewall Configuration
You must configure the firewalls for Contoso to meet the following business objectives:
- The internal firewall must only allow private network users to connect to the mail server and the Web server cluster in the DMZ. They should be restricted from connecting to any other servers in the DMZ or the Internet.
- The internal firewall must restrict connections to the Web server cluster from the private network to use only HTTP or HTTPS protocols.
- The internal firewall must allow the private network client computers to connect to the mail server in the DMZ by using any protocol.
- The firewalls must allow the Proxy Server to access the Internet by using any protocol.
- The Proxy Server must be configured to use the DNS server located in the DMZ as its primary DNS service.
- The DNS server in the DMZ must be allowed to forward DNS requests to any DNS server on the Internet.
- The mail server must be allowed to send e-mail messages to any mail server on the Internet.
Concerns About Providing Internet Access
The decision to allow Internet access has been a hard one for Contoso's CEO, Brian H. Valentine. Valentine is worried that access to the Internet will result in the employees using the Internet for nonbusiness purposes, which could lead to decreased productivity.
The original cause for concern occurred during a pilot project at the Seattle office. After a long series of all-day meetings, some pornographic Web content was viewed and left on a computer screen for all to see the next morning. A complaint was filed with the Human Resources department, but no action could be taken since Contoso hadn't clearly defined how the users of its private network should and should not use the Internet.
Valentine has developed the following preliminary set of guidelines that he wants to enforce through the secure Internet access solution developed by Contoso's IT department.
- All access to the Web site that led to the complaint to the Human Resources department, ww.southridgevideo.tld/, must be blocked. Any attempts to connect to the Web site must be logged and reported to Valentine within 24 hours.
- All access to Web sites that contain pornography must be blocked.
- Any employees who access unauthorized Web sites will be terminated if a committee composed of management and staff finds that the employee knowingly performed the prohibited action.
- The IT department will determine authorized protocols in discussions with each department's technology specialist. The technology specialist will propose a list of required protocols to be approved or denied by the IT department.
- All personnel who access the Internet must sign a document that defines the Internet acceptable use policy. The signature ensures that Contoso has a record that the employee has accepted all the conditions of the agreement.
- The Internet acceptable use policy must clearly outline what is authorized and what is unauthorized when an employee connects to the Internet.
Proposed Restrictions for Internet Access
The IT department has spent several months investigating policy restrictions on which protocols, departments, and content can be accessed on the Internet. The following are the results of their research:
- In investigating preliminary logs, the IT department found that the Web site ww.adatum.tld/ downloads an unauthorized ActiveX control that reports disk and port information to an attacker on the Internet. In response to this incident, the IT department wants to prevent all access to this site and any sites associated with adatum.tld/.
- As a result of the ww.adatum.tld/ incident, ActiveX downloads
- Must be limited to the Web server cluster in the DMZ and to trusted Web sites defined by the IT department
- Should not display any prompts to the user when ActiveX controls are downloaded from the trusted sites.
- Table 15.10 outlines which protocols each department will be allowed to use when accessing the Internet.
Table 15.10 Protocols Allowed by Each Department
Protocol Marketing HR Accounting IT Training HTTP X X X X X HTTPS X X X X X Telnet X NNTP X X X POP3 X SMTP X NetMeeting X X - You must configure Internet Explorer to prevent access to Web sites that contain pornography.
- Updates and configuration changes to Internet Explorer must be managed centrally from the London office. The changes must be pulled by the clients as soon as they're available.
Exercise 1: Evaluating the Internet Acceptable Use Policy
This exercise evaluates the proposed Internet acceptable use policy developed by Valentine. Answers to these questions can be found in the appendix.
- Do the guidelines proposed by Valentine define what is authorized and unauthorized for Internet access?
- Do the guidelines include provisions for disciplinary actions?
- Is anything missing from the guidelines?
Answers
Exercise 2: Designing Firewall Packet Filters for Secure Internet Access
This exercise examines the packet filters required by the internal and external firewalls to allow private network users and computers to connect securely to the Internet. Answers to these questions can be found in the appendix.
- What packet filters are required at the internal firewall to implement the following restrictions at the internal firewall?
- Allow internal computers to connect to the mail server when using any protocol
- Allow internal computers to connect to the Web server cluster address to use only HTTP or HTTPS
- Require the internal computers to access the Internet only by using the Proxy Server
- Have the internal client computers bypass the Proxy Server for services on the private network and in the DMZ
- Allow the Proxy Server to use the DNS server in the DMZ as its primary DNS server
- Allow the Proxy Server to access any resources on the Internet
Protocol Source IP Source Port Target IP Target Port Transport Protocol Action Any HTTP HTTPS Any Any - What configuration is required on the client computers to bypass the firewall for services on the private network and in the DMZ?
- How can you protect this configuration from being changed by users at the computers?
- What packet filters are required at the external firewall to allow the following outgoing data transmissions?
- The Proxy Server must be able to forward Internet requests to any server on the Internet
- The mail server must be able to send e-mail messages to any mail server on the Internet
- The DNS server must be able to send DNS requests to any DNS server on the Internet
Protocol Source IP Source Port Target IP Target Port Transport Protocol Action Any SMTP DNS DNS
Answers
Exercise 3: Restricting Access to Content
This exercise examines the configuration required to prevent Contoso employees from accessing unauthorized Internet content. Answers to these questions can be found in the appendix.
- What must you do to prevent access to any resources in the adatum.tld domain?
- How would you allow signed ActiveX controls only from sites in the DMZ and from sites deemed trustworthy by the IT department?
- What permission assignments are required for the Web Proxy service?
- What groups are required for this?
- What protocols require the use of the WinSock Proxy service? What group strategy could you use to secure use of these protocols?
- What additional configuration is required at the client computers for the WinSock Proxy service?
- How would you prevent access to Web sites that contain pornography? What measures must you take to prevent access if the Web site doesn't include RSACi metadata in their HTML source files?
- How would you enforce any settings required in the Internet Explorer configuration for Windows 2000–based clients?
- How would you enforce any settings required in the Internet Explorer configuration for non-Windows 2000–based clients?
Answers
EAN: 2147483647
Pages: 172