8.15 A View of Fraud
8.15 A View of Fraud
We start with an initial exploratory look at the data by using a link analysis component that allows us to view the associations between various products, clickstream behaviors, and demographics as they relate to criminal activity. For example, after importing the data into a data mining tool, its link analysis component quickly finds strong associations between two main product lines and fraudulent transactions. The tool displays the strength of the associations by the boldness of the links. The bolder the line, the stronger the association between the variables in the graph, and vice versa. The weaker relationships are displayed as broken lines, such as those between wireless and PDA units as they relate to fraud (see Figure 8.1).
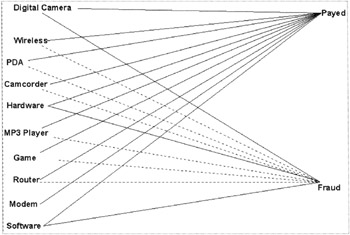
Figure 8.1: Associations between products and fraud. Note the bold line between hardware/software and fraud.
This initial link analysis can display the associations between specific products lines and fraud for this e-business, which it is probably already aware of. However, using this same technique, other variables can be viewed and compared to see how fraudulent transactions relate to the time of day of the purchase, a visitor's operating system, median income, zip code demographics, and scores of other clickstream behaviors and demographic attributes. The objective of this first analysis is to begin the construction of a fraud profile prior to moving to deter the on-line criminal activity.
EAN: 2147483647
Pages: 232