Everyday Security Basics
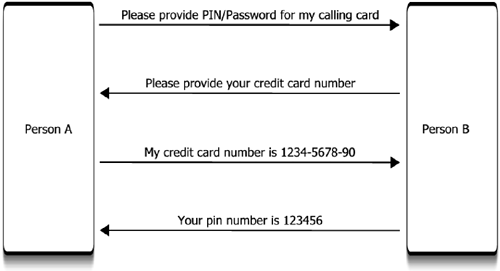
| The issues underlying security on the Internet are not that different from security issues we face when making everyday transactions. These issues are not just about monetary transactions that involve the exchange of money during purchases, but any transaction where there is dissemination of critical information such as social security or other uniquely identifying numbers, or of limited resources, such as money. Transactions rely on a level of trust between the parties involved in the transaction. The person disseminating information must prove to the person receiving information that she is who she claims to be. The person receiving the information must also prove to the person disseminating the information that he will hold the information in confidence and use it responsibly and appropriately. In many situations, the second person may also have information to disseminate based on the received information. In this case, both parties must prove their identities to the other. As an example, imagine that Person A is trying to get a Personal Identification Number (PIN) and password for using a calling card from Person B. Before issuing the PIN and password, Person B requests Person A's credit card number to which it will charge the cost of the calls. Before giving out the credit card number, Person A must be sure that Person B is who he says he is, e.g., a legitimate representative of the phone company. Person A must also prove to Person B that she is who she says she is and the legitimate owner of the credit card. Otherwise, if Person A is not the legitimate owner of the credit card, the credit card company may not release funds to the phone company even though Person A has used the calling card to make calls. Figure 8-1 illustrates this conversation between the two people and shows the importance of trust in the transaction. Figure 8-1. The importance of trust between transacting parties.
Every transaction involves risks, whether the transaction is an online Internet-based transaction or a standard face-to-face interaction-based transaction. These risks can be classified into four broad categories:
These categories of risks are all around us throughout our everyday lives. As some of the examples described, even if one were to completely avoid computers and the Internet, the potential for risk in doing transactions is very much present. But, the increasing use of computers for electronic transactions increases the potential for security breaches. At the same time, electronic transactions provide more opportunities to identify, document, and trap security breaches. In the next section, we discuss the importance of looking at security from an end-to-end perspective, and not just a point-to-point one. |
EAN: 2147483647
Pages: 141