6.3 Identifying Subsystems and Components
| Increasing numbers of exposures and vulnerabilities are identified in web-service subsystems and components used in complex environments. Here are some examples of popular subsystems that can be exploited to gain access to a target web server:
Through ascertaining the core web-service version and clear details of subsystems and enabled components, security analysts can properly investigate and qualify vulnerabilities and catalog exploit scripts to test later. What follows are examples and details of what to look for when identifying these subsystems. 6.3.1 ASP.NETMicrosoft IIS 5.0 and 6.0 servers can often be found running .NET framework components. If ASP.NET pages are in use (commonly with .aspx file extensions as opposed to .asp), H D Moore of Digital Defense, Inc., wrote the dnascan.pl utility to enumerate details of the ASP.NET subsystem and its configuration (http://www.digitaloffense.net/dnascan.pl.gz). Example 6-10 shows the tool identifying the version of ASP.NET running on http://www.patchadvisor.com as 1.1.4322.573). Example 6-10. Performing ASP.NET enumeration# ./dnascan.pl http://www.patchadvisor.com [*] Sending initial probe request... [*] Recieved a redirect response to /Home/Default.aspx... [*] Testing the View State... [*] Sending path discovery request... [*] Sending application trace request... [ .NET Configuration Analysis ] Server -> Microsoft-IIS/5.0 ADNVersion -> 1.1.4322.573 CustomErrors -> Off VSPageID -> 617829138 AppTrace -> LocalOnly ViewStateMac -> True ViewState -> 2 Application -> / If various ASP.NET debugging and tracing options are enabled, the tool can work out the local path of the ASPX scripts, as shown in Example 6-11. Example 6-11. Extracting sensitive information through ASP.NET# ./dnascan.pl http://www.example.org [*] Sending initial probe request... [*] Sending path discovery request... [*] Sending application trace request... [*] Sending null remoter service request... [ .NET Configuration Analysis ] Server -> Microsoft-IIS/6.0 Application -> /home.aspx FilePath -> D:\example-web\asproot\ ADNVersion -> 1.0.3705.288 6.3.2 WebDAVWeb Distributed Authoring and Versioning (WebDAV) is supported by default in IIS 5.0 and above running on Windows 2000 and 2003 Server platforms. Servers such as Apache can support the DAV protocol, depending on configuration. Microsoft IIS WebDAV components can be identified on servers that support the SEARCH and PROPFIND HTTP methods, found by issuing an OPTIONS / HTTP/1.0 request: Server: Microsoft-IIS/5.0 Date: Tue, 15 Jul 2003 17:23:26 GMT MS-Author-Via: DAV Content-Length: 0 Accept-Ranges: none DASL: <DAV:sql> DAV: 1, 2 Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH Allow: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK Cache-Control: private 6.3.3 Microsoft FrontPageFrontPage extensions are found on both Windows and Unix-based web servers. Many hosting companies running virtual hosts or dedicated web servers provide FrontPage extensions so that users can manage their web sites through Microsoft FrontPage (which doesn't use separate channels such as FTP to upload and manage web content). In particular, existence of the following files and directories disclose the presence of FrontPage server extensions running on a web server:
Requesting the _vti_inf.html file from a server running FrontPage extensions often results in a response as shown in Figure 6-3. Figure 6-3. FrontPage server extensions are present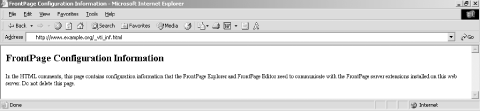 6.3.4 Microsoft Outlook Web AccessMicrosoft Exchange mail servers are often found running an IIS component known as Outlook Web Access (OWA) to facilitate remote HTTP and HTTPS access to user email. Many medium-sized companies favor this approach for remote access because of its simplicity and effectiveness over deployment of VPN and secure remote access solutions. Figure 6-4 shows OWA running from an Exchange 5.5 SP4 server. Figure 6-4. Outlook web access logon screen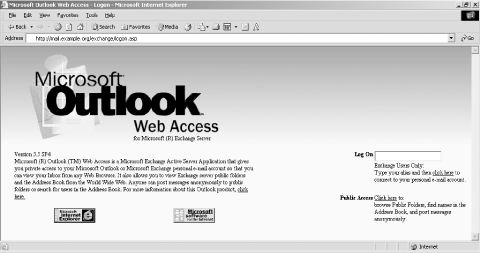 By checking for /owa, /exchange, and /mail directories under the web root through both HTTP and HTTPS, you can usually identify OWA services. Access to OWA is normally tied into Windows NT domain authentication, so brute-force attacks can be launched using tools such as Brutus (http://www.hoobie.net/brutus/). These tools can compromise valid user passwords that can be used by an attacker to gain access to more than just email. 6.3.4.1 Exchange 5.5 OWA public folders information leakExchange 5.5 with OWA has a public folders vulnerability that allows an attacker to search and list all the mailboxes and users registered on the target server, detailed in Microsoft security bulletins MS01-047 and CVE-2001-0660. Example 6-12 shows how to use a simple Perl script (http://examples.oreilly.com/networksa/tools/owa.pl) to enumerate valid users on webmail.example.org. Example 6-12. Enumerating valid user mailboxes on webmail.example.org# wget http://examples.oreilly.com/networksa/tools/owa.pl # perl owa.pl webmail.example.org output.txt Getting.. HTTP/1.1 200 OK Server: Microsoft-IIS/5.0 Date: Sun, 05 Oct 2003 19:52:27 GMT Content-Length: 76 Content-Type: text/html Set-Cookie: ASPSESSIONIDAQDBCRBA=DFDDOMFCFLBKCGDLNKENNBKC; path=/ Cache-control: private The owa.pl script searches through each letter of the alphabet to enumerate users. An extract from the output.txt file shows the format of the user details returned: <th ALIGN="left"><font color=000000 size=2>Phone</font></th> <th ALIGN="left"><font color=000000 size=2>Alias</font></th> <th ALIGN="left"><font color=000000 size=2>Department</font></th> <th ALIGN="left"><font color=000000 size=2>Office</font></th> </tr><tr><td><A HREF="JavaScript:openNewWindow('details.asp?obj=8700000031F9BE99D2B 73E479CC83E739F1BC9300100000006000000C9030000','detailsWindow', 640, 350)">Bosch, Elina</A></td> <td>0208 693 8714</td> <td>EBosch</td> <td>Finance</td> <td>London</td> </tr><tr><td><A HREF="JavaScript:openNewWindow('details.asp?obj=8700000031F9BE99D2B 73E479CC83E739F1BC9300100000000000000CB150000','detailsWindow', 640, 350)">Pablo, Juan</A></td> <td></td> <td>JPablo</td> <td>CAD Studio</td> <td>Reading</td> 6.3.5 Default IIS ISAPI ExtensionsOver the last four years, various buffer overflow vulnerabilities have been identified in Microsoft IIS 4.0 and 5.0 web servers through weird and wonderful file ISAPI mappings (such as .printer, .ida, and .htr). A breakdown of file extensions and their associated components within IIS is listed in Table 6-1.
It is possible to enumerate the enabled file extensions and ISAPI filters present on a target IIS server simply by issuing the following HTTP requests: GET /test.ida HTTP/1.0 GET /test.idc HTTP/1.0 GET /test.idq HTTP/1.0 GET /test.htr HTTP/1.0 GET /test.htw HTTP/1.0 GET /test.shtml HTTP/1.0 GET /test.printer HTTP/1.0 200 OK or 500 Internet Server Error responses from the target web server indicate the presence of the ISAPI mapping, as shown in Figure 6-5. Figure 6-5. The IDQ ISAPI mapping is present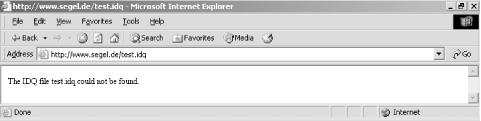 If a 404 File Not Found HTTP response is returned when requesting test.htr, test.htw, or test.printer files, the ISAPI mapping isn't present (as shown in Figure 6-6). Figure 6-6. The PRINTER ISAPI mapping has been removed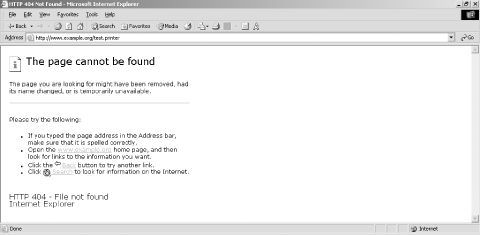 6.3.6 PHPThe PHP subsystem is straightforward to identify on web servers that process HEAD or OPTIONS requests because the Server: response string often lists PHP and other subsystems, especially in the case of Apache servers: # telnet www.trustmatta.com 80 Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'. OPTIONS / HTTP/1.0 HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:29:55 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close If PHP processor information isn't available from responses to HEAD or OPTIONS queries, an attacker may find accessible files on the web server with .php extensions. Most public PHP exploit scripts require that the user define an accessible file so that a malformed argument can be processed. 6.3.7 OpenSSLMany Linux and BSD web servers run OpenSSL to facilitate secure connections (through Apache web servers in particular). You can easily identify the presence of OpenSSL services by checking for TCP port 443 (HTTPS), and analyzing HTTP HEAD and OPTIONS responses. A typical Linux Apache web server running OpenSSL will respond in the following way to a HEAD request: # telnet www.rackshack.com 80 Trying 66.139.76.203... Connected to www.rackshack.com. Escape character is '^]'. HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Tue, 15 Jul 2003 18:06:05 GMT Server: Apache/1.3.27 (Unix) (Red-Hat/Linux) Frontpage/5.0.2.2623 mod_ssl/2.8.12 OpenSSL/0.9.6b DAV/1.0.3 PHP/4.1.2 mod_perl/1.26 Connection: close Content-Type: text/html; charset=iso-8859-1 It is apparent from the Server: string that OpenSSL 0.9.6b is present on this Red Hat Linux server. You can identify additional subsystems and components through this request, as follows:
To exploit most OpenSSL vulnerabilities requires access to TCP port 443 on the target server (either directly or through a proxy). Even if a vulnerable version of OpenSSL is present, filtered access to the port may prevent exploitation. |
EAN: 2147483647
Pages: 166