14.6 Recommendations
| Upon performing the assessment exercise, and qualifying the vulnerabilities at hand, a plan should be put forward to improve security. Recommendations fall into two categories: quick wins and long-term recommendations. 14.6.1 Quick Win RecommendationsThe quick win recommendations for the immediate improvement of security in this case are as follows, broken down by target host. 14.6.1.1 Cisco IOS routerA router Access Control List (ACL) should be implemented to prevent public access, particularly to the Telnet and SNMP services. NTP doesn't pose a security issue within Cisco IOS at the time of writing, although it would be diligent to filter access to this service also. 14.6.1.2 Solaris mail serverPublic access to the OpenSSH service should be filtered, allowing only trusted hosts to connect. OpenSSH should also be upgraded to the latest stable release (3.7.1p2 at the time of writing, available from http://www.openssh.com), to negate the risks posed by the four remote memory manipulation attacks, and the one user enumeration bug. The Sendmail service should be upgraded to the latest stable release (8.12.10 at the time of writing, available from http://www.sendmail.org) to negate the risks posed by the recent prescan( ) vulnerabilities that can permit a remote compromise. A catch-all email account should also be implemented so that RCPT TO: local user enumeration attacks are no longer effective. 14.6.1.3 Windows 2000 web serverBasic hardening of the IIS 5.0 web service ensures that bugs in components and subsystems that are rarely used aren't remotely exploitable. In particular, the following should be undertaken in this case:
14.6.1.3.1 Disable unnecessary ISAPI extensionsYou can disable unnecessary ISAPI extensions by clicking through the following Internet Services Manager (ISM) menus and options:
Figure 14-2. Removing ISAPI extensions through the ISM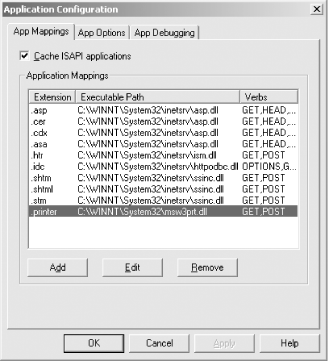 14.6.1.3.2 Install URLScan to block HTTP methods and filter requestsYou can disable support for unnecessary HTTP methods (also known as HTTP verbs), and provide ongoing filtering and protection of the IIS web service, by using the Microsoft URLScan tool, available from http://www.microsoft.com/technet/security/tools/URLScan.asp. By default, URLScan allows only the GET, HEAD, and POST methods to be used and rejects requests for .printer, .ida, .idq, .htr, .htw, and many other unnecessary files. The configuration file can be modified to provide more or less protection, accessible at %windir%\system32\inetsrv\urlscan\urlscan.ini. 14.6.2 Long-Term RecommendationsLong-term recommendations often relate to the entire network, its topology, and more importantly, the nature of the environment and organization. In this case, due to the simplicity of the target network and its small number of hosts, I have no long-term strategic recommendations. However, in large and more complex environments, the following are my long-term recommendations.
|
EAN: 2147483647
Pages: 166