Investigating Wi-Fi Protected Access (WPA)
In reaction to the problems that researchers discovered about the WEP encryption protocol, the Wi-Fi Alliance began work on the next generation wireless encryption standard. Called Wireless Protected Access (WPA), this standard corrects many of the problems associated with WEP and actually provides a degree of protection to wireless networks.
The Wi-Fi Alliance based WPA on an early, unpublished subset of the IEEE 802.11i security standard. Since then, the IEEE has published the final version of the 802.11i standard, and subsequent versions of WPA will incorporate more of 802.11i’s features.
Most new Wi-Fi gear supports WPA rather than WEP encryption. Some older devices are upgradeable to WPA simply by downloading a firmware update from the manufacturer. If WPA is available as an option on your Wi-Fi device, use it. It’s far more secure than WEP and will go a long way toward securing your home WLAN.
That said, WPA isn’t invulnerable to attack. To protect access points from attack, WPA authenticates users. If WPA detects two packets of unauthorized data within a one-second period, it assumes that it’s under attack and shuts down. Although this feature is meant to thwart an attack, it’s easily exploitable as a means to a denial-of- service (DoS) attack.
All an attacker has to do is send two bad packets every minute, and the access point will continue to shut down and reboot (see Figure 10-10). In fact, there are already attack tools available on the Web that automate this and make it easy to launch a WPA DoS attack.
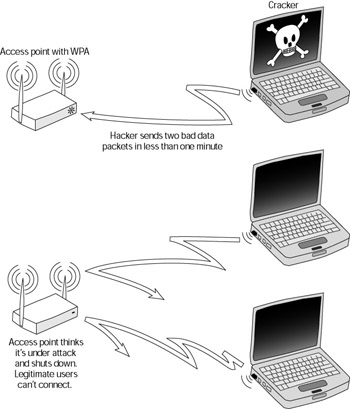
Figure 10-10: WPA DoS attack
In addition to DoS attack vulnerability, crackers can also attack WPA encryption. However, unlike WEP, the weaknesses in WPA encryption aren’t inherent in the WPA standard, but in the manner that some manufacturers have implemented the interface.
Some devices have an interface that limits the length of the password or passphrase a user can use to 20 characters or less. If you type words found in a dictionary or use a short passphrase, a cracker can use any one of a number of password-cracking programs to recover the password and discover the WPA key.
Once again, this isn’t a problem with WPA, but an interface problem. For maximum security, use long passwords or phrases with random letters and numbers. Ideally, you should enter hexadecimal numbers if your software allows you to.
EAN: 2147483647
Pages: 145