URL Structure
URL Structure
Broadly speaking, a URL is the mechanism for identifying resources on a Web, an SSL, or an ftp server, including the application layer protocol, which makes requests to the Web server. That is, the generic structure of a URL is:
protocol://server/path/to/resource?parameters
Each component is described in Table 5-1.
Figure 5-1 shows three types of URLs.
Figure 5-1. URL examples
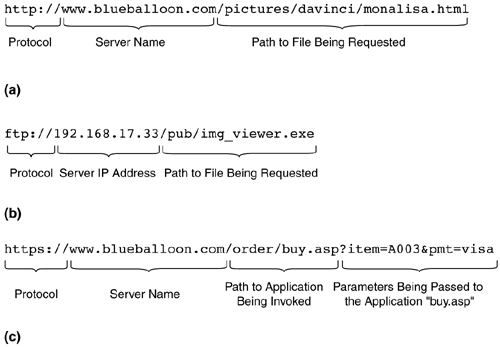
The URL shown in Figure 5-1(a) is self-explanatory. The file monalisa.html is being requested by the HTTP protocol from a server named www.blueballoon.com. The location of monalisa.html in the Web site space on www.blueballoon.com is the /pictures/davinci directory. The URL shown in Figure 5-1(b) is an example of a different protocol being used in place of HTTP. This protocol causes the browser to open an anonymous FTP connection with www.blueballoon.com and download the file img_viewer.exe lying in the /pub/ directory. Because we are focusing almost exclusively on Web applications and protocols, we don't discuss URLs other than HTTP URLs. Hence, for the remainder of this book, the term URL implies that the protocol used is HTTP. The URL shown in Figure 5-1(c) is that of an application being invoked. The application is buy.asp and is located in the /order/ directory. Two parameters are passed to the application namely, "item," with the value of "A003" and "pmt," with the value of "visa." Note that the protocol is not "http:," but rather "https:," which is HTTP used over Secure Sockets Layer (SSL), as discussed in Chapter 2.
Table 5-1. URL Components | |
| Component | Description |
| Protocol | Application layer protocol. The most common use of URLs is to request resources from Web servers (HTTP servers). Therefore the most common protocol is http:. Other protocols may be https:, ftp:, ldap:, telnet:, pop3:, and so on, depending on what the browser and server supports. |
| Server | DNS name, Netbios name, or the IP address of a host on the network, which hosts the resource being requested. |
| Path/to/resource | Directory path, including the resource name of the resource being requested. The resource can be a static file or an application that dynamically generates output. |
| Parameters | Optionally, parameters may be passed to the resource if it is an application or a program that dynamically generates output. Sometimes the part of the URL specifying the parameters is also called the Query String. |
Web Hacker PsychologyLet's try to put ourselves in a hacker's shoes. What makes a hacker? In a nutshell, a hacker has the ability to extrapolate information and think outside the box. Reading between the lines, inferring what is unstated, and piecing together the inner mechanics of an unknown entity is what makes a hacker. Let's take a look at the URL shown in Figure 5-1(c) as a hacker would. https://www.blueballoon.com/order/buy.asp?item=A003&pmt=visa This URL is from an application or a program that dynamically generates output by passing some parameters. What else can we figure out from it? A lot more, actually. The first inference can be made from the name of the resource, buy.asp. The extension .asp suggests that this file is actually a Microsoft Active Server Pages (ASP) file. ASP files run almost exclusively on Microsoft IIS Web servers; hence www.blueballoon.com is most probably a Windows NT/2000/XP server running on IIS. Looking at the parameters, we uncover some more clues. The first parameter, item=A003, suggests that the item being bought is assigned an item code and that the item details must be stored in a database. The most popular choice of a database platform for Windows NT is usually some form of Microsoft SQL Server (a full-blown SQL Server, SQL Desktop Engine) or Microsoft Access database. If it is a small site, it might be Microsoft Access. Thus buy.asp most likely makes an SQL query to a back-end database server to look up the item's details by its item code. The second parameter, pmt=visa, suggests that the payment for the purchase is being made by a credit card in this case, a Visa card. Thus the file buy.asp also may have code that interfaces with a credit card payment gateway system. Perhaps that is why SSL is used. We present more details on mapping the back-end technologies from the Web site structure and URLs in Chapter 6. |
Now let's look at how parameters are passed to Web application programs, as shown in the URL in Figure 5-1(c).
EAN: 2147483647
Pages: 156
- Chapter II Information Search on the Internet: A Causal Model
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XII Web Design and E-Commerce
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment