HTTP and Session Tracking
HTTP and Session Tracking
To see how session tracking is achieved over HTTP, let's take as an example Alice using eWebMail to send an e-mail message to Charles. Figure 13-12 shows how Alice used eWebMail, in terms of a state diagram and a session.
Figure 13-12. Alice's session with eWebMail
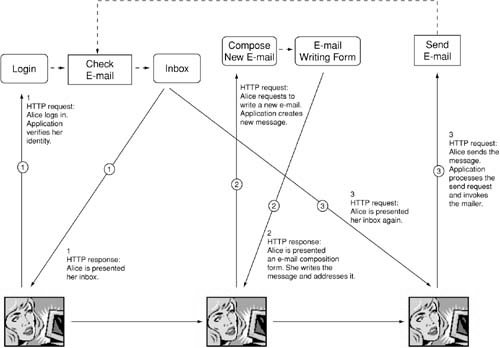
Alice starts at the Login state. She enters her username and password and successfully transits out of the Login state. In turn, the application creates a "uid" for her and sends it as a browser cookie to Alice's browser. The application sets an expiration time stamp of one hour from the time the cookie was issued. Thus, every time the browser sends a request to http://ewebmail.example.com/, the "uid" cookie is sent along with the HTTP request, until the cookie expires. Once Alice has cleared the Login state, the application takes her to the Inbox state. The application now sends a response to the HTTP request it received while in the Login state. The response consists of the Inbox view that appears in Alice's browser, completing the HTTP transaction. The browser and the Web server have no ongoing network connection between them, they are only logically connected at this point.
At the Inbox state Alice decides to compose a new e-mail message by clicking on the Compose link on the left-hand side bar. The browser sends the HTTP request, along with the cookie, to http://ewebmail.example.com/. When the application receives the request, it first decrypts the cookie string with the XOR mechanism and learns that the request has come from Alice. This is how the application creates a logical binding of the user's identity to the HTTP request. How does the application know that Alice was in the Inbox state? That's where the ":1" at the end of the cookie string comes in. Unbeknownst to Bob, the ":1" corresponds to the state number. In the case of eWebMail, each state was given a state number, which is passed back and forth between the browser and the server. The 1 corresponds to the Inbox state, the 2 corresponds to the Read e-mail state, the 3 corresponds to the Compose e-mail state, and so on. Encountering the trailing ":1," the application knows that Alice was at state 1, or the Inbox state, before she requested transition to state 3, or the Compose e-mail state. Internally, the application now sets her state number as 3, and transitions her session to the Compose e-mail state. The HTTP reply contains an e-mail composition form, as shown earlier in Figure 13-2. The cookie string returned now contains ":3" at the end. The browser replaces the old cookie with the new one and the new expiration date. The browser and the Web server once again are disconnected from a network connections point of view.
Once Alice finished composing the e-mail, she clicks on the Send button. Another HTTP request is sent to eWebMail. The incoming cookie is inspected, and Alice is transitioned from the e-mail composing form to the Send e-mail process. The Send e-mail process is a temporary state that provides its own transition. Once the e-mail is handed to the mailer program, the application transitions Alice to the Inbox state. Upon reaching the Inbox state, the cookie sent along with the response now ends with ":1." When Alice clicks on Logoff, the application sends an empty cookie string, which clears the cookie from Alice's browser. Alice's session with eWebMail is now over.
EAN: 2147483647
Pages: 156