Application State Diagrams
Application State Diagrams
We can best describe what went wrong by preparing a state diagram of the eWebMail application, as shown in Figure 13-11. State diagrams are part of a branch of discrete mathematics called finite state automata or finite state machine theory. A thorough discussion of finite state automata is beyond the scope of this book.
Figure 13-11. State diagram of eWebMail
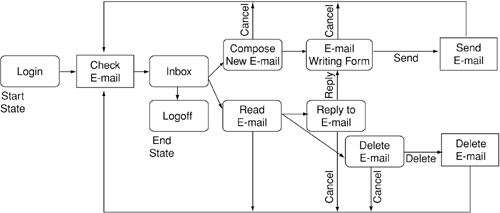
Each application has at least two states: a starting state and a terminating, or an ending, state. Whenever engaged with an application, a user is said to be in one or another of the various states of the application. In Figure 13-11, boxes with rounded corners denote states. Boxes with square corners denote processes that are internal to the application. States are interconnected by transition paths, taking the user from one state to another. Transitioning between two states shouldn't be possible if a transition path doesn't exist between them. This last statement is very important. In essence, a session hijacking attack makes use of a flaw that allows such illegal transitioning.
In the case of eWebMail, let's look at the state labeled Read E-mail. The user can reach this state only if she is already at the Inbox state. The user indicates to the application that she wants to transition from the Inbox state to the Read E-mail state by clicking on the Inbox hyperlink. Internally, the application processes the user's request and brings up the list of e-mails currently in the Inbox. This action causes the user to transition to the Read E-mail state. From the Read E-mail state, she has three possibilities namely, to go back to the Inbox state, to go to the Reply to e-mail state, or to go to the Delete E-mail state.
Entry into the application is governed by the Start state. In this case, it is the Login state, which can be cleared only if the proper user credentials are supplied. When presented with the proper user credentials, the application creates a logical session. The session binds the user to the application and is responsible for keeping track of the user's state within the application. The session lasts until the End state is reached or an error occurs. In this case, the Logoff state terminates the user session. It is responsible for clearing any values stored for keeping track of the session. At this point, the user is no longer engaged with or connected to the application.
EAN: 2147483647
Pages: 156