| SELinux is a software product that includes several mechanisms that protect against attacks exploiting software vulnerabilities, including attacks on 0-day vulnerabilities. In particular, SELinux implements role-based access control and sandboxing . SELinux also provides a logging and audit facility that records attempts to exceed specified permissions. By monitoring the system log, the administrator of an SELinux system can often discover attempts to escalate privileges and take action to prevent an intruder or insider from interfering with operation of the system. SELinux is designed to protect against misuse and unauthorized use such as: -
Unauthorized reading of data and programs -
Unauthorized modification of data and programs -
Bypassing application security mechanisms -
Interfering with other processes -
Privilege escalation -
Information security breaches 1.2.1 How SELinux Works Figure 1-1 depicts the operation of SELinux in a highly simplified fashion. SELinux works by associating each program or process with a sandbox known as a domain. Each domain is assigned a set of permissions sufficient to enable it to function properly but do nothing else. For instance, a domain is limited in the files it can access and the types of operations it can perform on those files. To enable specification of such permissions, each file is labeled with information called a security context . The definition of a domain spells out what operations it can perform on files having specific security contexts. A domain cannot access files having security contexts other than those for which it is explicitly granted access. Figure 1-1. The operation of SELinux 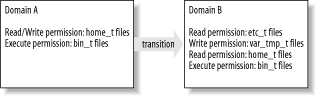
Under specified conditions, a process that executes a program leaves its current domain and transitions to a new domain. Typically, transitions occur upon executing a program designated as an entry point to the new domain. The new domain may have more or fewer privileges than the original domain. Thus, programs can initiate other programs having more or fewer privileges than themselves . An SELinux facility known as type enforcement (TE) ensures that the rules governing domains are always observed . SELinux also has a secondary facility known as role-based access control (RBAC). RBAC limits user access to domains. For instance, some domains are defined to be accessible only to the system administrator, whereas other domains are defined to be publicly available to any user . An exciting aspect of SELinux is that the definitions of domains, security contexts, and transitions appear in files called policy files that can be modified by the SELinux system administrator. Thus, SELinux security policies are extremely flexible and can support a wide range of security needs. For instance, suppose that you want to install a program that neither you nor anyone you know has previously run under SELinux. Therefore, no policy specifying the operations that the program should and should not be allowed to perform exists. Nevertheless, you can create such a policy and enjoy the benefits of running the program in a manner consistent with the principle of least privilege. 1.2.2 SELinux Components and Linux Security Modules (LSM) SELinux was originally implemented as a set of Linux kernel modules that worked with the Linux 2.2 kernel. SELinux has since been updated to work with Linux 2.4. SELinux can also work with the Linux Security Modules (LSM) feature of the Linux 2.6 kernel. LSM consists of a set of hooks inserted into the Linux kernel. These hooks provide the means to notify a software unit, such as SELinux, whenever a process attempts to perform an operation on an object, such as opening a file for read access or deleting a file. LSM also provides a means whereby the software unit can prohibit the attempted access, making it straightforward for software developers to implement a security engine that oversees access to files and other objects, such as that used in SELinux. In addition to kernel modules, SELinux includes a set of system administration programs that have been modified to be aware of the SELinux environment, and a set of programs used to administer SELinux itself. SELinux also includes a policy, implemented as a set of files, that defines users and roles and their permissions. SELinux and User-Mode Linux (UML) User-Mode Linux is an open source product that enables a single host to run multiple, sandboxed instances of the Linux kernel, referred to as virtual machines . UML's function is roughly comparable to that of commercial virtualization products, such as VMware and Microsoft's Virtual PC. However, UML supports only Linux, whereas VMware and Virtual PC support a variety of operating systems. Each virtual machine running under UML can run programs and applications, maintain a distinct filesystem separate from that of other virtual machines, and access the network. So if a program or an entire instance of a running kernel is compromised, the other programs and kernel instances may not be affected. SELinux includes a set of policies that are intended to strengthen the UML sandbox and thereby improve system security and integrity. Using SELinux, you can make it less likely that a wayward application or a successful attack compromising one virtual machine will lead to the subversion or failure of other virtual machines. You can learn more about User-Mode Linux at http://user-mode-linux. sourceforge .net. |
Alternatives to SELinux An alternative product providing functions generally similar to those of SELinux is GRSecurity, described at http://grsecurity.org. Like SELinux, GR Security is supported only for Linux 2. x . Developers of open source operating systems other than Linux are implementing products similar to SELinux. For example, the BSD community is creating TrustedBSD. To learn more about TrustedBSD, see its web site, http://www.trustedbsd.org. |
|