9.6 Security and Privacy Mechanisms
9.6 Security and Privacy Mechanisms
Several security mechanisms are available today, and many more are on the horizon. However, not all mechanisms are appropriate for every environment. Each security mechanism should be evaluated for the network that it is being applied to based on the degree of protection it provides; its impact on users' ability to do work; the amount of expertise required for installation and configuration; the cost of purchasing, implementing, and operating it; and the amounts of administration and maintenance required.
In this section, we will cover physical security and awareness, protocol and application security, encryption/decryption, network perimeter security, and remote access security.
9.6.1 Physical Security and Awareness
Physical security is the protection of devices from physical access, damage, and theft. Devices are usually network and system hardware, such as network devices (e.g., routers, switches, hubs), servers, and specialized devices, but can also be software CDs, tapes, or peripheral devices. Physical security is the most basic form of security and the one that is most intuitive to users. Nevertheless, it is often overlooked when developing a security plan. Physical security should be addressed as part of the network architecture even when the campus or building has access restrictions or security guards.
Ways to implement physical security include the following (Figure 9.4):
-
Access-controlled rooms (e.g., via card keys) for shared devices (servers) and specialized devices
-
Backup power sources and power conditioning
-
Off-site storage and archival
-
Alarm systems (e.g., fire and illegal entry alarms)
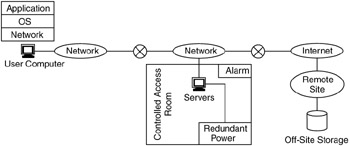
Figure 9.4: Areas of physical security.
Physical security also applies to other types of physical threats, such as natural disasters (e.g., fires, earthquakes, storms). Security from natural disasters includes protection from fire (using alarm systems and fire-abatement equipment), water (with pumping and other water-removal/protection mechanisms), and structural degradation (e.g., through having devices in racks attached to floors, walls). Addressing physical security lays the foundation for your entire network security and privacy plan.
Security awareness is getting users educated and involved with the day-to-day aspects of security in their network and helping them understand the potential risks of violating security policies and procedures. Security awareness can be promoted through providing sessions on security, where users have a chance to discuss issues with security and voice their opinions and problems with security mechanisms, policies, and procedures and potentially offer options for security and privacy; by providing users with bulletins or newsletters (or adding information to the organization's newsletter) on network security and what they can do to help; and by providing users with information on the latest security attacks.
9.6.2 Protocol and Application Security
In this section, we will consider some common protocol and application security mechanisms: IPSec, SNMP, and packet filtering.
IPSec is a protocol for providing authentication and encryption/decryption between devices at the network layer. IPSec mechanisms consist of authentication header (AH) and encapsulating security payload (ESP). There are two modes in which IPSec operates: transport and tunneling. In transport mode, the IP payload is encrypted using ESP and the IP header is left in the clear, as shown in Figure 9.5.
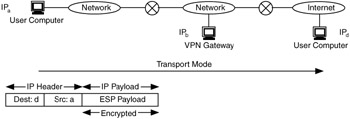
Figure 9.5: Transport mode of IPSec.
In tunnel mode, IPSec can be used to encapsulate packets between two virtual private network (VPN) gateways (IPb and IPc in Figure 9.6).
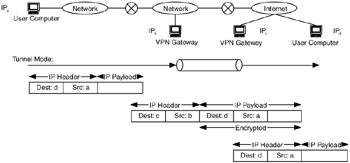
Figure 9.6: Tunnel mode of IPSec.
The tunneling process consists of the following:
-
IPSec tunnels are created between VPN gateways IPb and IPc in Figure 9.6.
-
IP packets are encrypted using ESP.
-
These packets are then encapsulated within another IP packet, addressed with the ends of the IPSec tunnel (IPb and IPc).
-
At the end of the tunnel (the VPN gateway serving IPd), the original packet is unencapsulated and decrypted and sent to its destination (IPd).
This is an example of tunneling, or encapsulating information within protocol headers for the purpose of isolating and protecting that information. Note that this is different from traditional protocol encapsulation, which is used to support varying functions at each protocol layer. VPNs apply this tunneling concept to create multiple isolated networks across a common infrastructure.
Tunneling and VPNs are common methods for building an isolated network across a common infrastructure such as the Internet.
Security for the SNMP version 3 (SNMPv3) is described in the user-based security model (USM), protecting against modification of information, masquerades, disclosure (eavesdropping), and message stream modification. SNMP security provides the following security capabilities:
-
SNMP message verification (data integrity), user identity verification (data origin authentication), and data confidentiality (via authProtocol, authKey, privProtocol, privKey)
-
Detects SNMP messages that have exceeded time thresholds (message timeliness/limited replay) (via snmpEngineID, snmpEngineBoots, snmpEngineTime)
SNMP security also includes authentication mechanisms (authProtocol) and encryption/decryption mechanisms (privProtocol):
-
HMAC-MD5-96 (128-bit message digest algorithm [MD5] cryptographic hash function, message-authentication codes [HMAC] mode, truncated to 96 bits)
-
HMAC-SHA-96 (secure hash algorithm)
-
CBC-data-encryption standard (DES) Cipher Block Chaining Mode Symmetric Encryption/Decryption Protocol
SNMP security also provides for modifying management information base (MIB) views and access modes. For example, it is possible to have different MIB views definable for different groups, and access modes (RO, RW) are also definable for different groups and are tied to MIB views.
Packet filtering is a mechanism in network devices to explicitly deny or pass packets at strategic points within the network. They are often used to deny packets to or from particular IP addresses or ports (services), as in Figure 9.7.
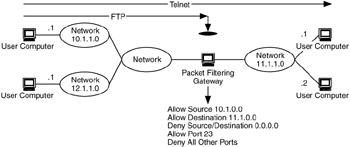
Figure 9.7: Example of packet filtering.
9.6.3 Encryption/Decryption
Although other security mechanisms provide protection against unauthorized access and destruction of resources and information, encryption/decryption protects the information from being usable by the attacker. Encryption/decryption is a security mechanism in which cipher algorithms are applied together with a secret key to encrypt data so that they are unreadable if they are intercepted. Data are then decrypted at or near the destination. This is shown in Figure 9.8.
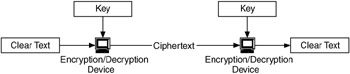
Figure 9.8: Encryption/decryption of network traffic.
As such, encryption/decryption enhances other forms of security by protecting information in case other mechanisms fail to keep unauthorized users from that information. There are two common types of encryption/decryption: public key and private key. Software implementations of public key encryption/decryption are commonly available. Examples include DES private key encryption, triple DES private key encryption, and Rivest-Shamir-Adleman (RSA) public key encryption.
Public key infrastructure (PKI) is an example of a security infrastructure that uses both public and private keys. Public key infrastructure is a security infrastructure that combines security mechanisms, policies, and directives into a system that is targeted for use across unsecured public networks (e.g., the Internet), where information is encrypted through the use of a public and a private cryptographic key pair that is obtained and shared through a trusted authority. PKI is targeted toward legal, commercial, official, and confidential transactions and includes cryptographic keys and a certificate management system. Following are components of this system:
-
Managing generation/distribution of public/private keys
-
Publishing public keys with user IDs (UIDs) as certificates in open directories
-
Ensuring that specific public keys are truly linked to specific private keys
-
Authenticating the holder of a public/private key pair
PKI uses one or more trusted systems known as certification authorities (CAs), which serve as trusted third parties for PKI. The PKI infrastructure is hierarchical, with issuing authorities, registration authorities, authentication authorities, and local registration authorities.
Another example is the secure sockets library (SSL). SSL is a security mechanism that uses RSA-based authentication to recognize a party's digital identity and RC4 to encrypt and decrypt the accompanying transaction or communication. SSL has grown to become one of the leading security protocols on the Internet.
One trade-off with encryption/decryption is a reduction in network performance. Depending on the type of encryption/decryption and where it is implemented in the network, network performance (in terms of capacity and delay) can be degraded from 15% to 85% or more. Encryption/decryption usually also requires administration and maintenance, and some encryption/decryption equipment can be expensive. Although this mechanism is very compatible with other security mechanisms, trade-offs such as these should be considered when evaluating encryption/ decryption.
9.6.4 Network Perimeter Security
For network perimeter security, or protecting the external interfaces between your network and external networks, we will consider the use of address translation mechanisms and firewalls.
Network address translation (NAT) is the mapping of IP addresses from one realm to another. Typically this is between public and private IP address space. Private IP address space is the set of Internet Engineering Task Force-defined private address spaces (RFC 1918):
| Class A | 10.x.x.x | 10/8 prefix |
| Class B | 172.16.x.x | 172.16/12 prefix |
| Class C | 192.168.x.x | 192.168/16 prefix |
NAT is used to create bindings between addresses, such as one-to-one address binding (static NAT), one-to-many address binding (dynamic NAT), and address and port bindings (network address port translation [NAPT]).
Although NAT was developed to address the issues of address space exhaustion, it was quickly adopted as a mechanism to enhance security at external interfaces. Routes to private IP address spaces are not propagated within the Internet, so the use of private IP addresses hides the internal addressing structure of a network from the outside.
The security architecture should consider a combination of static and dynamic NAT and NAPT, based on the devices that are being protected. For example, static NAT is often used for bindings to multiple-user devices such as servers or high-end computing devices, and dynamic NAT is used with generic computing devices.
Firewalls are combinations of one or more security mechanisms, implemented in network devices (routers), that are placed at strategic locations within a network. Firewalls can be filtering gateways, an application proxy with filtering gateways, or a device running specialized "firewall" software.
9.6.5 Remote Access Security
Remote access consists of traditional dial-in, point-to-point sessions, and VPN connections, as shown in Figure 9.9.
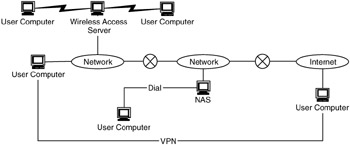
Figure 9.9: Remote access mechanisms.
Security for remote access includes what is commonly known as AAAA: authentication of users, authorization of resources to authenticated users, accounting of resources and service delivery, and allocation of configuration information (e.g., addresses or default route). AAAA is usually supported by a network device such as a network access server (NAS) or subscriber management system (SMS).
Remote access security is common in service-provider networks (see also the service-provider architectural model in Chapter 5), but it is evolving into enterprise networks as enterprises recognize the need to support a remote access model for their networks.
Considerations when providing remote access include the following (Figure 9.10):
-
Method(s) of AAAA
-
Server types and placement (e.g., demilitarized zone [DMZ])
-
Interactions with DNS, address pools, other services
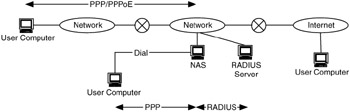
Figure 9.10: Remote access considerations.
Figure 9.11 shows the protocol interaction of the Point-to-Point Protocol (PPP), PPP over Ethernet (PPPoE) and remote access dial-in user service (RADIUS) in a remote access network.
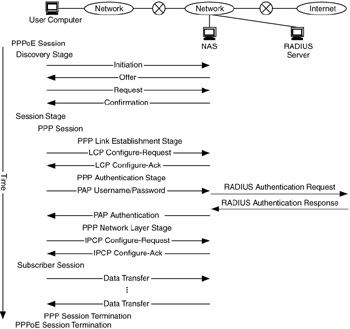
Figure 9.11: Process for PPP/PPPoE session establishment.
Figure 9.11 shows the process of establishing a PPPoE session, upon which a PPP session is started. PPPoE provides a shim between Ethernet and PPP, supporting the point-to-point nature of PPP sessions over a broadcast Ethernet network.
Thus, a PPPoE session starts with a broadcast packet, the PPPoE active discovery initiation (PADI). This packet begins a handshake between the user's computer and the NAS, consisting of PADI, PPPoE active discovery offer (PADO), PPPoE active discovery request (PADR), and PPPoE active discovery session (PADS) packets. The PPP session can begin at the completion of this part of the process.
A PPP session has three stages: link establishment, authentication, and network layer. Each stage builds on the previous one to establish the PPP session. Once PPPoE and PPP sessions have been established, the user can begin using the network.
Authentication in a remote access network is typically accomplished via a combination of PPP, PPPoE, PAP, CHAP, and RADIUS protocols.
Other authentication mechanisms at the remote access network include tokens, smart cards, digital certificates, and callback. VPNs and tunnels can also be considered part of the remote access network.
VPNs are an example of what can be considered a subarchitecture. VPNs, by themselves, can require their own set of architectural considerations. This is particularly true when they make an extranet, which is an intranet extended to include access to or from selected external organizations (e.g., customers, suppliers), but not to the general public. Such considerations include equipment types, tunneling protocols and security, VPN locations, policies on VPN provisioning and support, and the use of routing protocols such as the Border Gateway Protocol (BGP) or multiprotocol label switching (MPLS).
Finally, remote access security should also consider wireless communications and portable computing devices using standards such as 802.11 and homephoneline networking alliance (homePNA). Wireless can target a number of environments, such as mobility, portability, and nomadic computing.
EAN: 2147483647
Pages: 161