Cisco Hierarchical Approach
Cisco uses the hierarchical model to design and troubleshoot a network. This model is an efficient design topology that allows you to divide the network into three distinct layers: core, access, and distributed. These layers are a logical and not physical segmentation of the network. The Cisco hierarchical model divides the network into three layers, which reduces the complexity of internetworks that consist of multiple networks, communication subnets, and routers. This makes it possible to maintain each part of the network without disturbing the entire network.
Using the hierarchical model, you can design, maintain, and troubleshoot a network with respect to the following factors:
-
Number of network users
-
Number of running applications
-
Number of subnetworks involved in making the complex network
-
Number of servers in the network and the estimated load that each server can effectively handle
Figure 1.3 displays the Cisco hierarchical model.
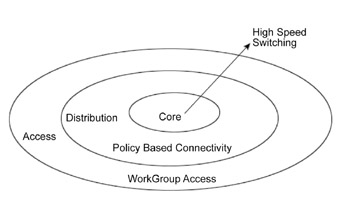
Figure 1.3: The Cisco hierarchical model.
The Access Layer
The access layer enables user interaction with the network. It is also called the desktop layer. End user workstations and local resources such as the printer are placed at this layer. Routers serve as gatekeepers at the entry and exit of this layer, and ensure that local server traffic is not forwarded to the wider network. The access layer controls user and workgroup access to internetwork resources. Other functions performed on this layer include sharing and switching of bandwidth, MAC-layer filtering, and micro segmentation.
Therefore, troubleshooting the access layer would require identifying problems of the local servers or network resources. In addition, problems at the access layer can include switch malfunction. This can be corrected by using backup switches for the main switches.
The Distribution Layer
Next in the Cisco hierarchical model is the distribution layer. This layer enables routing of data to the destination nodes and establishes WAN links between subnetworks. In addition, this layer performs data filtering functions to ensure security of data and the network. It is also called the workgroup layer.
The distribution layer serves as a bridge between the access layer and the core services of the network because it determines which data packets and user requests should be allowed access to core services of the network with respect to the associated user request. The distribution layer also routes data packets through the fastest route to access the required core service of the network or the required destination node.
This layer implements network policies and controls network traffic and data movement. In addition, it performs complex CPU-intensive calculations pertaining to routing, filtering, inter-VLAN routing, Access Control Lists (ACLs), address or area aggregation, security, and it identifies alternate paths to access the core.
To prevent network congestion, the distribution layer segregates the network into domains to distribute the load effectively over the entire network. In addition, the distribution layer ensures compatibility among different types of networks, such as Ethernet and Token Ring. The distribution layer ensures that the data transfer between different types of networks is not hampered because of compatibility issues between the networks.
Problems at the distribution layer are related to network congestion and the nonfunctioning WAN links between the subnetworks. Troubleshooting the problems of the distribution layer involves restoring the WAN link and using appropriate filtering mechanisms or an appropriate security mechanism.
The Core Layer
The core layer is a high-speed switching backbone that transports large volumes of traffic reliably and quickly. The traffic transported across the core is between end users and enterprise services, such as e-mail, video-conferencing, and dial-up access to the network. The links in the core layer are point-to-point.
| Note | The services provided by the network are common to all the users of the network and are called enterprise services. |
The core layer is responsible for providing high-speed transport. As a result, there is no room for latency and complex routing decisions pertaining to filters and access lists. Therefore, protocols such as OSPF and BGP, which have fast convergence time, are implemented at this layer. Quality of Service (QoS) may be implemented at this layer to ensure higher priority to traffic that may be lost or delayed in congestion. The core layer should have a high degree of redundancy.
This is the most important layer of a complex network and needs to be equipped with extensive troubleshooting support. This is because, if there is a malfunction in the backbone, the entire network is rendered nonfunctional.
EAN: 2147483647
Pages: 130
- Structures, Processes and Relational Mechanisms for IT Governance
- An Emerging Strategy for E-Business IT Governance
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governance in IT Outsourcing Partnerships