Administrative Delegation
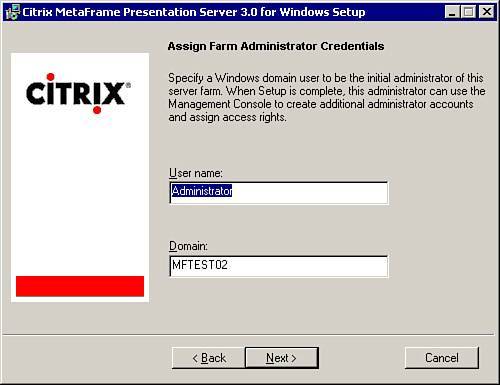
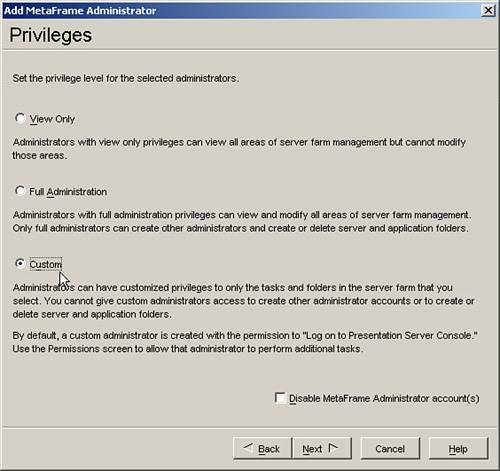
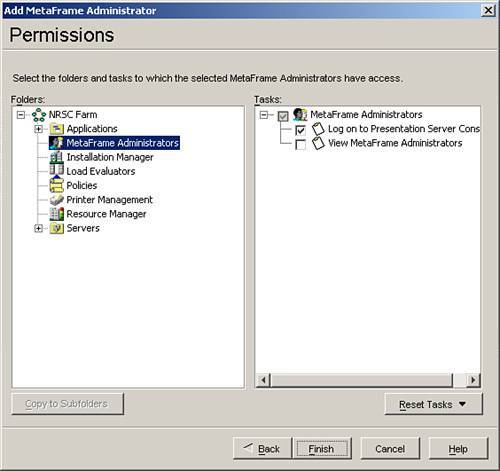
| Securing an MPS environment begins when you install MetaFrame onto the first server in the farm. You should remember that during the creation of the new data store for the server farm, you are prompted to provide the username and domain that will be assigned as the first administrator for the farm (see Figure 9.1). Any member of a Windows or a Novell Directory Services (NDS) domain can be granted access to administer a MetaFrame server farm. Figure 9.1. Full access is delegated for the first time during the installation of the first server in a new farm. This user is automatically granted full administrative authority over the farm and is the account that must be used when logging in to the Management Console for the first time. When you are logged in to the Management Console, you then can delegate varying levels of administrative authority to specific users and/or user groups. Delegation ExamplesAlthough the existence of only a few administrators with full authority to the server farm is usually sufficient in small MetaFrame implementations (one server farm zone and a single geographic location), in larger farm deployments, it may be desirable to delegate a subset of the administrative features to different "classes" of administrators. One common example involves granting help desk staff access to open the Management Console, view published applications, and manage user sessions connected to those applications. This staff can also manage sessions ( logoff , shadow, and so on) through the Servers folder. No other Management Console features are available to the user. Delegating this limited access to manage the environment allows help desk representatives to troubleshoot and resolve typical first-level support issues without an administrator having to worry that they may modify other configuration settings on the server. Figure 9.2 illustrates the limited view within the Management Console that would be available to a help desk representative in this example. This help desk representative does not even see the nodes to which he or she has not been granted access. Figure 9.2. Through delegation, you can limit what portions of the Management Console are available to the user.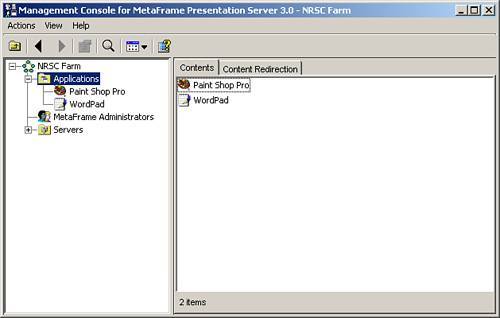 Through the creation of subfolders under Applications or Servers, you can further subdivide the delegation of authority. In the example given here, you may have certain applications that contain sensitive information (accounting or payroll, for example) that you do not want the help desk directly supporting. Instead, you may have a special subset of administrators who are authorized to manage only the accounting applications or maybe an accounting-specific server. By creating subfolders and placing the appropriate applications/servers into those folders, you can then delegate access to the folder just as you would the root Applications or Servers folder. Figure 9.3 shows an example of a subfolder called Accounting defined under Applications. When this subfolder is first created, you have the option of automatically copying the permissions from the parent folder. If users are not assigned permissions to view this folder, they will not even see it appear when they query the contents of the Applications folder. Figure 9.3. Subfolders are used to assign more granular control to applications or servers when necessary.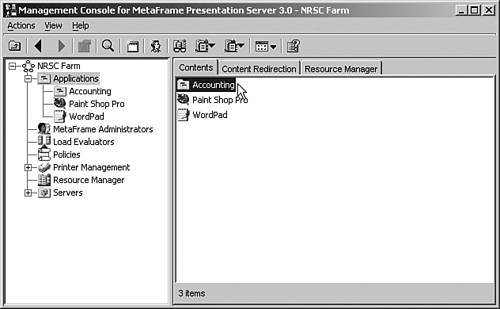 Note Access delegated to a management node (MetaFrame Administrators, Installation Manager, Load Evaluators, Policies, Printer Management, Resource Manager) applies farm-wide, while permissions set on either the Applications or Servers folder (and all subfolders) apply only to the corresponding objects within the folder. The following "Creating and Delegating Administrators" section provides examples on how this is done. Creating and Delegating MetaFrame AdministratorsAll MetaFrame administrative delegation is done through the Management Console. After you have logged in to the Management Console as an administrator with full authority, you can add and configure additional users who will be able to access and manage the server farm. Administrators are easily added to the system either by right-clicking the MetaFrame Administrators node or selecting the Action menu and choosing Add MetaFrame Administrator. Alert Only those administrators granted full administrative authority are able to add, modify, or delete other administrator accounts in the farm. You cannot delegate these privileges as a subset of full authority. You are then presented with the Add MetaFrame Administrator Wizard, which guides you through the steps of configuring the new administrator accounts. The basic steps for delegating administrative privileges in the farm are as follows :
MetaFrame Administrative PrivilegesTable 9.1 summarizes the privileges that can currently be configured when the Custom privilege configuration is chosen. In preparation for the exam, you should be able to identify the privileges that exist and understand how they affect the portions of the Management Console that are accessible to the administrator. Many of the permissions are self-explanatory from the description, so we don't go into too much detail here on stating exactly what they manage unless you should be aware of something of particular importance. Table 9.1. Privileges Available in the Custom Privilege Configuration Option
Note If you want to assign permissions to subfolders of the Applications or Servers nodes, you need to create the desired folders before you assign permissions. Folders cannot be created while creating new (or modifying existing) administrative delegations. You create subfolders by highlighting Applications or Servers and then choosing New Folder from the Actions menu or right-clicking and choosing New Folder from the context menu. Zone-Based Administrative DelegationWe mentioned earlier that administrative privileges could also be delegated based on the location or zone breakdown of the MetaFrame servers in the farm. The actual mechanism for doing this is not automatically controlled by the existing zones in your farm, but is managed by creating corresponding server groups and allocating servers in such a way that it mirrors the zone (or geographical) layout of the farm. Figure 9.6 demonstrates this by showing three subfolders under the Servers node labeled New York, Los Angeles, and London. Within these subfolders are the MetaFrame servers that are physically divided into these locations. Figure 9.6. Leveraging the support of subfolders for the Servers node, you can mirror your zone layout in the server farm and delegate access to different groups of administrators for each zone.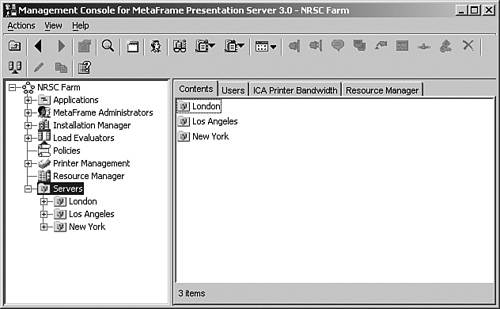 From this, you can then assign different administrative privileges based on the requirements of the servers in each location. As you can see, this manual process must be undertaken to correspond to the layout of the servers. Currently, this support is not automatically kept in sync with the zone breakdown in the server farm. If you move servers or create a new zone, you have to manually update the subfolders to reflect these changes. Modifying Existing DelegationsExisting MetaFrame administrators can have their privileges modified at any time. You do so simply by modifying the properties for the administrator in the MetaFrame Administrators node. The three dialog boxes that appeared when the administrator was first created are all accessible and can be modified from within the properties of an administrator. If the administrator currently has the Management Console open, he or she is presented with a message stating that permissions have been modified and that he or she must log in again to the Management Console. The administrator is immediately logged out of his or her current Management Console session. The option to disable the administrator account can be quickly enabled or disabled by right-clicking the name and choosing the one that is currently active. If the account is currently enabled, the disable option is available and vice versa. If an existing administrator is deleted, the settings are lost. If the administrator to be deleted is the last one in the farm with full authority, MetaFrame does not allow you to delete the account. Note You can also modify the permissions for a node or folder at any time from within the Management Console simply by right-clicking the item and selecting Permissions from the context menu. Managing Access to External Citrix MetaFrame ToolsOne important note is that the delegation of permissions within the Management Console affects management of the farm through the console only. It does not enable or disable access or execution of other external Citrix MetaFrame tools such as the Citrix Connection Configuration tool or the command-line tools used for managing MetaFrame sessions. For example, even though an administrator may have been granted access to disconnect user sessions through the Management Console, unless that administrator has similar access at the connection level, he or she cannot use the command-line tool TSDISCON to disconnect active sessions. Attempting to do so results in an access- denied message. The same error would be generated if the user attempted to disconnect sessions using the Terminal Services Management GUI ( TSADMIN.EXE ). Understanding the scope of delegated permissions is an important part of effectively managing the environment. Security best practices recommend that access to external tools be controlled through local or domain security groups and that permissions defined at the connection level be restricted. This ensures that external tools cannot be used to modify or manage the environment outside the Management Console. Configuration and administrative techniques were discussed in Chapter 6, "Configuring and Administering MetaFrame Presentation Servers." |
EAN: N/A
Pages: 199