Filtering on FTP Commands
If you’ve attended one of the hands-on courses that I’ve taught recently, then you already learned how to build filters based on the application command set.
Command filters are really great! You can catch almost any command being sent across the wire as long as you know the offset and the value. Go to www.ietf.org and download the specification you are most interested in. Read through it to get the command sequences that cross the wire for various operations. In this example, we’ll focus on the FTP command sequences. This filter set will catch anyone sending FTP traffic across the wire regardless of the port number they use for the commands. If someone’s trying to slip through our network perimeter using a non-standard FTP port number, we can easily catch them.
If you refer to the FTP specifications defined in RFC 959 (Section 4.1), you’ll see the list of FTP commands that follow immediately after the TCP header (offset 0x28 from the protocol start). A few of the common FTP commands are listed below:
| USER: | Precedes the username during the FTP login. |
| PASS: | Precedes the user’s password during login. |
| RETR: | Indicates the file that is to be retrieved. |
| PORT: | Used to set up a port for a second connection. |
| NLST: | Used to list the directory contents. |
| STOR: | Used to put files on the FTP server. |
| CWD: | Used to change the directory. |
You can make a separate pattern for each one of these commands and catch any of them crossing the wire or you can simply build one filter that looks at just one pattern (such as the RETR command). In Figure 42, I’ve made a series of patterns using a standard offset of 0x28 (protocol).
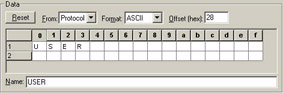
Figure 42: Three patterns to catch FTP USER, PASS and NLST commands regardless of the port used.
Finally, we’ll put all this together with another set of patterns that cancel out any FTP commands to or from the standard port number 21. This way we can be sure we are catching someone doing something unusual on the network.
First, we must make a filter for all traffic to port 21 and another filter for all traffic from port 21 (follow the same methods we used earlier to catch traffic to and from port 1214).
Next, we need to use the NOT operand to ensure that we are looking for traffic that uses the USER, PASS or NLST command and NOT port 21 in the source or destination port field, as shown in Figure 43.
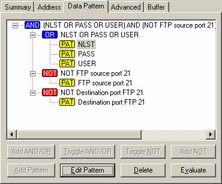
Figure 43: The filter looks pretty cool when you put it all together.
This filter isn’t very difficult to build and it can be very useful in testing your firewall to see if it is catching traffic based on packet content as opposed to just looking at the port numbers used in the packet.
If you are interested in testing our your filter, download the “isit-ftp.cap” or “is-it-ftp.pkt” trace file that is located in the Trace File library online at www.packet-level.com. See if you can spot what’s happening in this trace file set.
EAN: 2147483647
Pages: 65