Filtering on TCP Flags
TCP headers contain a series of flags that define the purpose of the TCP function in the packet. These flags are listed below:
| Flag | Purpose |
|---|---|
| URG | Urgent - see Urgent Pointer field |
| ACK | Acknowledgment |
| PSH | Push through TCP buffer - do not wait |
| RST | Disconnects or refuses connection |
| SYN | Synchronize sequence numbers |
| FIN | Finish (does not disconnect) |
The flags field is at a strange offset because there are two reserved bits that precede it. Figure 31 shows the decode of the flags portion of a SYN packet (used in the TCP handshake process).
As you can see, the Sniffer shows some bit values set at 0. These flags are set to off. The SYN bit, however, is set to 1 indicating that this is a SYN (synchronize) packet.
The first two bit positions are not marked at all - they are the reserved bits; they are always set to 0.
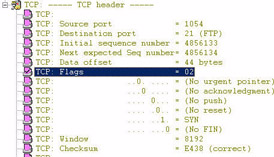
Figure 31: The flags field is 6 bits long. It is preceded by two reserved bits (set to 0).
So, how to do you convert the individual bit values to a decimal number for the entire byte? How did this SYN bit setting equal a flags field setting of 02?
Well, let’s look at the values of the individual bit positions. Figure 32 shows the values of each of the bits in the flags field.
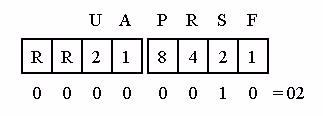
Figure 32: Based on the bit setting, the flag field value for a SYN packet is 02.
Let’s look at a couple of other flag settings. Figures 33 and 34 show the settings defined for the SYN/ACK packet (the second packet of the three-way TCP handshake) and a packet with the Urgent bit set to 1.
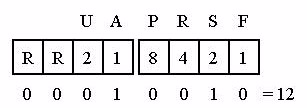
Figure 33: When both the ACK and SYN bits are set to 1, the flags field value is 12.
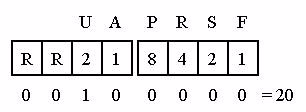
Figure 34: When just the Urgent bit is set, the flags field value is 20.
Figure 35 shows the setting when a TCP reset is sent. This one is particularly interesting because you’ll want to build a filter for all TCP resets to identify potential port scans and connection problems.
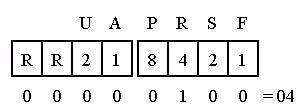
Figure 35: When just the Reset bit is set, the flags field value is 4.
Now let’s put this knowledge together to catch a specific attack called the WinNuke attack. This attack was used to push Windows 95 systems to the BSOD (blue screen of death). The attacker simply sent out NetBIOS packets with the Urgent bit set to 1.[8] NetBIOS traffic is sent out on ports 137, 138, or 139. To build a filter for these packets you must use the AND operand and look for two patterns:
-
a pattern with the Urgent bit set to 1
-
a pattern with the destination port 137, 138 or 139
Figures 36, 37, and 38 show each pattern filter along with the summary indicating that the patterns are combined with the AND operand.
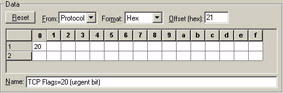
Figure 36: The Urgent bit pattern.
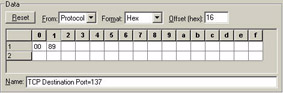
Figure 37: The NetBIOS filter is based on traffic to port 137 (0x0089).
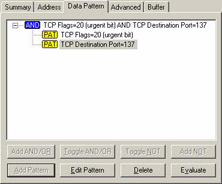
Figure 38: The two patterns are combined with the AND operand to ensure we only capture NetBIOS packets with the Urgent bit set to 1.
What would have happened if you had used the OR operand in this filter?
___________________________________
___________________________________
___________________________________
___________________________________
[8]Microsoft labeled this attack, the “Out of Bounds” attack.
EAN: 2147483647
Pages: 65