Lesson 1: Introduction to Protocols
This lesson offers an introduction to protocols and their function in a networking environment. It explains the roles of protocols in network communications and describes how different protocols work at different OSI levels.
After this lesson, you will be able to:
- Identify the functions of protocols and protocol stacks.
- Describe the network processes that use protocols and how they utilize them.
- Map specific protocols to the appropriate OSI level.
Estimated lesson time: 45 minutes
The Function of Protocols
Protocols are rules and procedures for communicating. The term "protocol" is used in a variety of contexts. For example, diplomats from one country adhere to rules of protocol designed to help them interact smoothly with diplomats from other countries. Rules of protocol apply in the same way in the computer environment. When several computers are networked, the rules and technical procedures governing their communication and interaction are called protocols.
Keep three points in mind when you think about protocols in a network environment:
- There are many protocols. While each protocol facilitates basic communications, each has different purposes and accomplishes different tasks. Each protocol has its own advantages and restrictions.
- Some protocols work only at particular OSI layers. The layer at which a protocol works describes its function. For example, a protocol that works at the physical layer ensures that the data packet passes through the network interface card (NIC) and out onto the network cable.
- Protocols can also work together in a protocol stack, or suite. Just as a network incorporates functions at every layer of the OSI reference model, different protocols also work together at different levels in a single protocol stack. The levels in the protocol stack "map," or correspond, to the layers of the OSI reference model. For instance, the TCP/IP protocol's application layer maps to the OSI reference model's presentation layer. Taken together, the protocols describe the entire stack's functions and capabilities.
How Protocols Work
The entire technical operation by which data is transmitted over the network has to be broken down into discrete, systematic steps. At each step, certain actions take place that cannot take place at any other step. Each step includes its own rules and procedures, or protocol.
The protocol steps must be carried out in a consistent order that is the same on every computer in the network. In the sending computer, these steps must be executed from the top down. In the receiving computer, these steps must be carried out from the bottom up.
The Sending Computer
Protocols at the sending computer:
- Break the data into smaller sections, called packets, that the protocol can handle.
- Add addressing information to the packets so that the destination computer on the network can determine that the data belongs to it.
- Prepare the data for transmission through the NIC and out onto the network cable.
The Receiving Computer
Protocols at the receiving computer carry out the same series of steps in reverse order. They:
- Take the data packets off the cable.
- Bring the data packets into the computer through the NIC.
- Strip the data packets of all the transmitting information that was added by the sending computer.
- Copy the data from the packets to a buffer for reassembly.
- Pass the reassembled data to the application in a usable form.
Both sending and receiving computers need to perform each step in the same way so that the data will have the same structure when it is received as it did when it was sent.
For example, two different protocols might each break data into packets and add on various sequencing, timing, and error-checking information, but each will do it differently. Therefore, a computer using one of these protocols will not be able to communicate successfully with a computer that is using the other protocol.
Routable Protocols
Until the mid-1980s, most local area networks (LANs) were isolated. A LAN served a single department or company and was rarely connected to any larger environments. As LAN technology matured, however, and the data communication needs of businesses expanded, LANs evolved, becoming components in larger data communication networks in which LANs talked to each other.
Data that is sent from one LAN to another along any of several available paths is said to be routed. The protocols that support multipath LAN-to-LAN communications are known as routable protocols. Because routable protocols can be used to tie several LANs together and create new wide-area environments, they are becoming increasingly important.
Protocols in a Layered Architecture
In a network, several protocols have to work together. By working together, they ensure that the data is properly prepared, transferred to the right destination, received, and acted upon.
The work of the various protocols must be coordinated so that no conflicts or incomplete operations take place. The results of this coordination effort are known as layering.
Protocol Stacks
A protocol stack is a combination of protocols. Each layer of the stack specifies a different protocol for handling a function or subsystem of the communication process. Each layer has its own set of rules. In Chapter 5, "Introducing Network Standards," we discussed the OSI reference model. Figure 6.1 shows the OSI reference model and the rules associated with each layer. The protocols define the rules for each layer in the OSI reference model.

Figure 6.1 The OSI reference model showing the layers of protocols
The lower layers in the OSI reference model specify how manufacturers can make their equipment connect to equipment from other manufacturers, for example, by using NICs from several manufacturers on the same LAN. As long as they operate with the same protocols, they are able to send and receive data from each other. The upper layers specify rules for conducting communications sessions (the time during which two computers maintain a connection) and the interpretation of applications. The higher they are in the stack, the more sophisticated the tasks and their associated protocols become.
The Binding Process
The binding process—the process by which protocols become connected to each other and the NIC—allows a great deal of flexibility in setting up a network. Protocols and NICs can be mixed and matched on an as-needed basis. For example, two protocol stacks, such as Internetwork Packet Exchange and Sequenced Packet Exchange (IPX/SPX), discussed in Lesson 3: NetWare Protocols, and Transmission Control Protocol/Internet Protocol (TCP/IP), discussed in Lesson 2: TCP/IP, can be bound to one NIC. If there is more than one NIC in the computer, one protocol stack can be bound to either or both NICs.
The binding order determines the sequence in which the operating system runs the protocol. When multiple protocols are bound to a single NIC, the binding order is the sequence in which the protocols will be utilized to attempt a successful connection. Typically, the binding process is initiated when either the operating system or the protocol is installed or initialized. For example, if TCP/IP is the first protocol to be bound, the network operating system will attempt a network connection via TCP/IP before attempting to use another protocol. If this network connection fails, the computer will attempt to make a connection by using the next protocol in the binding order.
The binding process consists of more than just binding the protocol stack to the NIC. Protocol stacks need to be bound or associated with the components above and below them so that data can proceed smoothly through the stack during execution. For example, TCP/IP may be bound to the Network Basic Input/Output System (NetBIOS) session layer above as well as to the NIC driver below it. The NIC driver is also bound to the NIC.
Standard Stacks
The computer industry has designated several kinds of stacks as standard protocol models. Hardware and software manufacturers can develop their products to meet any one or a combination of these protocols. The most important models include:
- The ISO/OSI protocol suite.
- The IBM Systems Network Architecture (SNA).
- Digital DECnet.
- Novell NetWare.
- Apple's AppleTalk.
- The Internet protocol suite, TCP/IP.
Protocols exist at each layer of these stacks, performing the tasks specified by that layer. However, the communication tasks that networks need to perform are grouped into one of three protocol types. Each type is comprised of one or more layers of the OSI. As shown in Figure 6.2, these three protocol types map roughly to layers of the OSI reference model (application, transport, and network).
NOTE
Many protocols were written long before the OSI reference model came into common use. Thus, it is not uncommon to find protocol stacks that do not map directly to the OSI model.
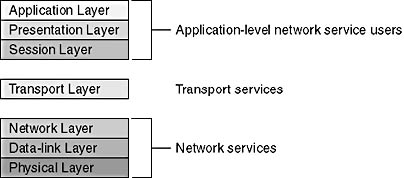
Figure 6.2 Communication tasks within the OSI reference model
Application Protocols
Application protocols work at the uppermost layer of the OSI reference model. They provide application-to-application interaction and data exchange. Popular application protocols are shown in Table 6.1.
Table 6.1 Popular Application Protocols
| Protocol | Description |
|---|---|
| APPC (Advanced Program-to-Program Communication) | IBM's peer-to-peer SNA protocol, mostly used on AS/400 computers. APPC is defined as an applica- tion protocol, because it works in the presentation layer of the OSI reference model. However, it is also considered a transport protocol because APPC uses the LU 6.2 protocol that works in both the transport and session layers of the OSI reference model. |
| FTAM (File Transfer Access and Management) | An OSI file access protocol. |
| X.400 | A CCITT protocol for international e-mail transmissions. |
| X.500 | A CCITT protocol for file and directory services across several systems. |
| SMTP (Simple Mail Transfer Protocol) | An Internet protocol for transferring e-mail. |
| FTP (File Transfer Protocol) | An Internet file transfer protocol. |
| SNMP (Simple Network Management Protocol) | An Internet protocol for monitoring networks and network components. |
| Telnet | An Internet protocol for logging on to remote hosts and processing data locally. |
| Microsoft SMBs (Server Message Blocks) and client shells or redirectors | A client/server, request response protocol. |
| NCP (Novell NetWare Core Protocol) and Novell client shells or redirectors | A set of service protocols. |
| AppleTalk and AppleShare | Apple's networking protocol suite. |
| AFP (AppleTalk filing Protocol) | Apple's protocol for remote file access. |
| DAP (Data Access Protocol) | A DECnet file access protocol. |
Transport Protocols
Transport protocols facilitate communication sessions between computers and ensure that data is able to move reliably between computers. Popular transport protocols are shown in Table 6.2.
Table 6.2 Popular Transport Protocols
| Protocol | Description |
|---|---|
| TCP | The TCP/IP protocol for guaranteed delivery of sequenced data. |
| SPX | Part of Novell's IPX/SPX protocol suite for sequenced data. |
| NWLink | The Microsoft implementation of the IPX/SPX protocol. |
| NetBEUI (NetBIOS extended user interface) | Establishes communication sessions between computers (NetBIOS) and provides the underlying data transport services (NetBEUI). |
| ATP (AppleTalk Transaction Protocol) and NBP (Name Binding Protocol) | Apple's communication-session and data-transport protocols. |
Network Protocols
Network protocols provide what are called "link services." These protocols handle addressing and routing information, error checking, and retransmission requests. Network protocols also define rules for communicating in a particular networking environment such as Ethernet or Token Ring. Popular network protocols are shown in Table 6.3.
Table 6.3 Popular Network Protocols
| Protocol | Description |
|---|---|
| IP | The TCP/IP protocol for packet-forwarding routing. |
| IPX | NetWare's protocol for packet forwarding and routing. |
| NWLink | The Microsoft implementation of the IPX/SPX protocol. |
| NetBEUI | A transport protocol that provides data-transport services for NetBIOS sessions and applications. |
| DDP (Datagram Delivery Protocol) | An AppleTalk data-transport protocol. |
Protocol Standards
The OSI reference model is used to define which protocols should be used at each layer. Figure 6.3 shows the OSI reference model and how several popular network manufacturers apply their protocols. Products from different manufacturers that subscribe to this model can communicate with each other.
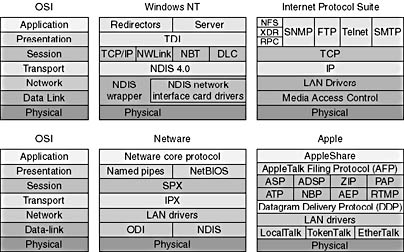
Figure 6.3 Manufacturer compatibility
The ISO, the Institute of Electrical and Electronic Engineers (IEEE), ANSI (American National Standards Institute), CCITT (Comité Consultatif Internationale de Télégraphie et Téléphonie), now called the ITU (International Telecommunications Union), and other standards bodies have developed protocols that map to some of the layers in the OSI reference model.
The IEEE protocols at the physical layer are:
- 802.3 (Ethernet) This is a logical bus network that can transmit data at 10 Mbps. Data is transmitted on the network to every computer. Only computers meant to receive the data acknowledge the transmission. The carrier-sense multiple access with collision detection (CSMA/CD) protocol regulates network traffic by allowing a transmission only when the network is clear and no other computer is transmitting.
- 802.4 (token passing) This is a bus layout that uses a token-passing scheme. Each computer receives all the data, but only the computers that are addressed respond. A token that travels the network determines which computer is able to broadcast.
- 802.5 (Token Ring) This is a logical ring network that transmits at either 4 Mbps or 16 Mbps. Although this is called a ring, it more resembles a star with each computer branching off a hub. The ring is actually inside the hub. A token traveling around the ring determines which computer can send data.
As described in Chapter 5, Lesson 1: Open Systems Interconnection (OSI) Reference Model, the data-link layer is divided into two sublayers (see Figure 6.4).
The IEEE has further defined these protocols to facilitate communications activity at the Media Access Control (MAC) sublayer.
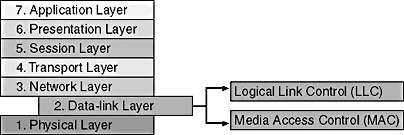
Figure 6.4 MAC driver or NIC driver
A MAC driver is located at the Media Access Control sublayer; this device driver is also known as the NIC driver. It provides low-level access to network adapters by providing data-transmission support and some basic adapter management functions.
A MAC protocol determines which computer can use the network cable when several computers try to use it simultaneously. CSMA/CD, the 802.3 protocol, allows computers to transmit data when no other computer is transmitting. If two hosts transmit simultaneously, a collision occurs. The protocol detects the collision and halts all transmission until the wire is clear. Then, each computer can begin to transmit again after waiting a random period of time.
Implementing and Removing Protocols
Protocols are implemented and removed in much the same way that drivers are added and removed. Essential protocols are installed automatically at the same time the initial operating system is installed on the computer. To install protocols such as NWLink after the initial installation, the network operating system usually includes a utility that leads the administrator through the process. For example, a network operating system setup program might provide a series of graphical windows that lead the administrator through the process of:
- Installing a new protocol.
- Changing the order in which the installed protocols have been linked.
- Removing a protocol.

Exercise 6.1 (a): Matching the OSI Model Rules to Layers
This exercise is designed to help you reinforce your understanding of network protocol stacks. The following table contains two columns. In the left column are listed the seven layers of the OSI reference model. In the right column, enter the rule that applies to the layer on the left.
OSI Reference Model Rules
| OSI Layers | Rules |
|---|---|
| Application layer | |
| Presentation layer | |
| Session layer | |
| Transport layer | |
| Network layer | |
| Data-link layer | |
| Physical layer |
Answers
Exercise 6.1 (b): Matching the OSI Model Layers with Communication Tasks
Because many protocols were written before the OSI reference model was developed, some protocol stacks developed earlier don't match the OSI reference model; in those stacks, tasks are often grouped together.
Communication tasks can be classified into three groups. In this part of the exercise, the seven layers of the OSI reference model are again listed in the left column. In the right column, write in the name of one of the three groups in the following list. Your task is to identify which of these three groups maps to each of the OSI layers in the left column.
The three groups are:
- Transport services.
- Network services.
- Application-level network service users.
Matching OSI Reference Model with Communication Tasks
| OSI Layers | Communication Task |
|---|---|
| Application layer | |
| Presentation layer | |
| Session layer | |
| Transport layer | |
| Network layer | |
| Data-link layer | |
| Physical layer |
Answers
Lesson Summary
The following points summarize the main elements of this lesson:
- Protocols in a networking environment define the rules and procedures for transmitting data.
- To send data over a network successfully requires a series of separate steps that must be carried out in a prescribed order.
- The sending and receiving computers use protocols to:
- Break data into packets.
- Add addressing information to the packets.
- Prepare the packets for transmission.
- Take the packets off the cable.
- Copy the data from the packets for reassembly.
- Pass the reassembled data to the computer.
- Several stacks are used as standard protocols; the most prominent standard protocols are based on the OSI reference model layers.
- Protocols are implemented and removed in the same manner as drivers.
EAN: 2147483647
Pages: 106