Lesson 6: Security Configuration and Analysis
Security Configuration and Analysis is a tool that enables you to configure security, analyze security, view results, and resolve any discrepancies revealed by analysis. This tool is located on the Security Configuration and Analysis console. This lesson shows you how to use the Security Configuration and Analysis console.
After this lesson, you will be able to
- Explain how the Security Configuration and Analysis console works
- Use the Security Configuration and Analysis console to perform security configuration and analysis tasks
Estimated lesson time: 25 minutes
How the Security Configuration and Analysis Console Works
The Security Configuration and Analysis console uses a database to perform configuration and analysis functions. The security configuration and analysis database is a computer-specific data store. The database architecture allows the use of personal databases, security template import and export, and the combination of multiple security templates into one composite security template that can be used for analysis or configuration. New security templates can be incrementally added to the database to create a composite security template; overwriting a template is also an option. You can also create personal databases for storing your own customized security templates.
Security Configuration
The Security Configuration and Analysis console can be used to configure local system security. By using personal databases, you can import security templates created with the Security Templates console and apply these templates to the GPO for the local computer. This immediately configures the system security with the levels specified in the template.
Security Analysis
The state of the operating system and applications on a computer is dynamic. For example, security levels may occasionally be required to change temporarily in order to enable immediate resolution of an administration or network issue. After this security requirement is finished, the temporary change may not be reversed. This means that a computer may no longer meet the requirements for enterprise security.
The Security Configuration and Analysis console allows administrators to perform a quick security analysis. In the analysis, recommendations are presented alongside current system settings, and icons or remarks are used to highlight any areas where the current settings do not match the proposed level of security. Security Configuration and Analysis also offers the ability to resolve any discrepancies revealed by analysis.
Regular analysis enables an administrator to track and ensure an adequate level of security on each computer as part of an enterprise risk management program. Analysis is highly specified and information about all system aspects related to security is provided in the results. This enables an administrator to tune the security levels, and most important, to detect any security flaws that may occur in the system over time.
Using Security Configuration and Analysis
The following is the sequence of tasks required to use Security Configuration and Analysis:
- Accessing the Security Configuration and Analysis console
- Setting a working security database
- Importing a security template into a security database
- Analyzing system security
- Viewing security analysis results
- Configuring system security
- Exporting security database settings to a security template
Accessing the Security Configuration and Analysis Console
The Security Configuration and Analysis console is the main tool for using the security configuration and analysis tool.
Follow these steps to access the Security Configuration and Analysis console:
- Do one of the following:
- To add the Security Configuration and Analysis console to a new console, click Start, click Run, type mmc and then click OK.
- To add the Security Configuration and Analysis console to an existing console, go directly to Step 2.
- On the Console menu, click Add/Remove Snap-In, and then click Add.
- In the Add Standalone Snap-In dialog box, select Security Configuration And Analysis and click Add.
- Click Close, and then click OK.
- On the Console menu, click Save.
- Enter the name to assign to this console and click Save.
The console appears on the Administrative Tools menu.
Setting a Working Security Database
The Security Configuration and Analysis console uses a database to perform configuration and analysis functions. Before you can configure or analyze security you must determine the working security database to use.
Follow these steps to set a working security database:
- In the Security Configuration and Analysis console (see Figure 21.16), right-click Security Configuration And Analysis.
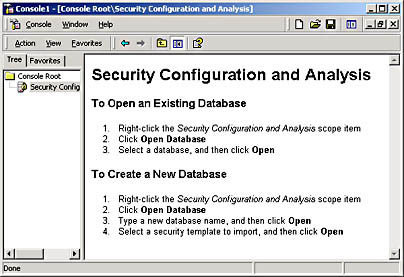
Figure 21.16 The Security Configuration and Analysis console
- Click Open Database.
- In the Open Database dialog box, choose an existing personal database or type a filename to create a new personal database, and then click Open.
- If you chose an existing personal database, this database is now the working security database.
- If you created a new personal database, the Import Template dialog box appears.
- Select the security template to load into the security database, and then click Open.
This database is now the working security database.
Importing a Security Template into a Security Database
In Lesson 5, "Using Security Templates," you learned to import a security template directly into a GPO. In this lesson you import a security template into the security database used in the Security Configuration and Analysis console.
You can merge several different templates into one composite template, which can then can be used for analysis or configuration of a system, by importing each template into a working database. The database merges the various templates to create one composite template, resolving conflicts in order of import; the last one imported takes precedence when there is contention. Only if you chose to overwrite will they not be merged into a composite template (stored configuration). Once the templates are imported to the selected database, you can analyze or configure the system.
Follow these steps to import a security template into a security database:
- In the Security Configuration and Analysis console, right-click Security Configuration And Analysis.
- Open or create a working security database.
- Select Import Template.
- Select a security template file, and then click Open.
- Repeat the previous step for each template you want to merge with previous templates into the database.
NOTE
If you want to replace the template rather than merge it into the stored template, click the Clear This Database Before Importing check box in the Import Template dialog box.
Analyzing System Security
Security Configuration and Analysis performs security analysis by comparing the current state of system security against a security template that you have imported to a personal database. This template is the database configuration, and it is the template that contains your preferred or recommended security settings for that system.
Security Configuration and Analysis queries the system's security settings for all security areas in the database configuration. Values found are compared to the database configuration. If the current system settings match the database configuration settings, they are assumed to be correct. If not, the policies in question are displayed as potential problems that need investigation.
Follow these steps to analyze system security:
- In the Security Configuration and Analysis console, set a working database (if one is not currently set).
- Right-click Security Configuration And Analysis, and then click Analyze Computer Now.
- In the Perform Analysis dialog box, verify the path for the log file location, and then click OK.
The different security areas are displayed as they are analyzed. Once this is complete, you can check the log file or review the results.
NOTE
To check the log file, right-click Security Configuration And Analysis, and then click View Log File.
Viewing Security Analysis Results
The Security Configuration and Analysis console displays the analysis results organized by security area with visual flags to indicate problems. For each security policy in the security area, the current database and computer configuration settings are displayed.
Follow these steps to view security analysis results:
- In the Security Configuration and Analysis console, click Security Configuration And Analysis.
- Double-click a security policies node (such as Account Policies), and then click the security area (such as Password Policy) for which you want to view results.
- In the details pane (see Figure 21.17), the Policy column indicates the policy name for the analysis results, the Database Setting column indicates the security value in your template, and the Computer Setting column indicates the current security level in the system.
- A red X indicates a difference from the database configuration.
- A green check mark indicates consistency with the database configuration.
- No icon indicates that the security policy was not included in your template and therefore not analyzed.
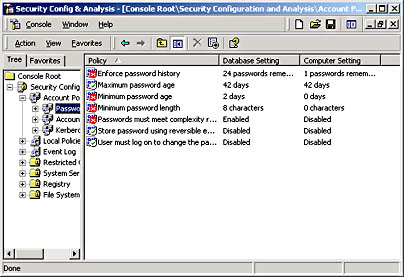
Figure 21.17 Analysis results for Password Policy
Configuring System Security
Security Configuration and Analysis enables you to resolve any discrepancies revealed by analysis, including the following:
- Accepting or changing some or all of the values flagged or not included in the configuration if you determine the local system security levels are valid due to the context (role) of a particular computer
- Configuring the system to the original database configuration values if you determine the system is not in compliance with valid security levels
- Importing a more appropriate template, for the role of a particular computer, into the database as the new database configuration and applying it to the system
You can repeat the import process and load multiple templates. The database merges the various templates to create one composite template, resolving conflicts in order of import; the last one imported takes precedence when there is contention. Once the templates are imported to the database, you can choose Configure System Now to apply the stored template (database configuration) to the system.
IMPORTANT
These changes are made to the stored template in the database, not to the security template file. The security template file only modified if you either return to Security Templates and edit that template or export the stored configuration to the same template file.
Using the Security Configuration and Analysis console is not recommended when you are analyzing security for domain-based clients, as you would have to go to each client individually. In this case, you should return to the Security Templates console, modify the template, and reapply it to the appropriate GPO.
Follow these steps to configure system security:
- In the Security Configuration and Analysis console, set a working database (if one is not currently set).
- Right-click Security Configuration And Analysis, and then click Configure Computer Now.
- In the Configure System dialog box, click OK to use the default analysis log or enter a filename and valid path.
The different security areas are displayed as they are configured. Once this is complete, you can check the log file or analyze system security and view the results.
Follow these steps to edit the database security configuration:
- In the Security Configuration and Analysis console, click Security Configuration And Analysis.
- Double-click a security policies node (such as Account Policies), and then click a security area (such as Password Policy).
- In the details pane, double-click the security attribute you want to edit.
- Click the Define This Policy In The Database check box to allow editing.
- Enter a new value for the security policy, and then click OK.
- Repeat the previous four steps for each security policy you want to edit.
Follow these steps to view security configuration results:
- In the console from which you manage group policy, double-click the GPO.
- In the console tree, click Security Settings.
- Double-click a security policy node (such as Account Policies), and then click a security area (such as Password Policy).
- Double-click the security attribute you want to view (such as Minimum Password Length).
Exporting Security Templates
The export feature provides the ability to save a security database configuration as a new template file that can be imported into other databases, used as is to analyze or configure a system, or even redefined with the Security Templates console.
To export security database settings to a security template
- In the Security Configuration and Analysis console, right-click Security Configuration and Analysis.
- If you have created a composite security template by importing multiple templates into one database and you want to save the composite template as a separate template file, click Export Template.
- In the Export Template To dialog box, type a valid filename in the File Name box, type a path to where your template should be saved in the Save In list, and select the type of file you want to save in the Save As Type list, and then click Save.

Practice: Using Security Configuration and Analysis
In this practice you access the Security Configuration and Analysis console, set a working security database, analyze system security, and then view the results.
Exercise 1: Accessing the Security Configuration and Analysis Console
In this exercise you access the Security Configuration and Analysis console, the main tool for using the Security Configuration and Analysis tool.
To access the Security Configuration and Analysis console
- Click Run, type mmc and then click OK.
- On the Console menu, click Add/Remove Snap-In, and then click Add.
- In the Add Standalone Snap-In dialog box, select Security Configuration And Analysis, and then click Add.
- Click Close, and then click OK.
- On the Console menu, click Save.
- In the File Name box, type security config & analysis to name this console and click Save.
The console appears on the Administrative Tools menu.
Exercise 2: Setting a Working Security Database
In this exercise you determine the working security database to use.
To set a working security database
- In the Security Configuration and Analysis console, right-click Security Configuration And Analysis.
- Click Open Database.
- In the Open Database dialog box, in the File Name box, type new for the new personal database file name, and then click Open.
- In the Import Template dialog box, select the securedc security template to load into the security database, and then click Open.
The new database is now the working security database, and it contains the securedc security template.
Exercise 3: Analyzing System Security
In this exercise you analyze system security, comparing the settings in the security template securedc with the security settings currently running on your system.
To analyze system security
- Right-click Security Configuration And Analysis, and then click Analyze Computer Now.
- In the Perform Analysis dialog box, verify the path for the log file location, and then click OK.
The different security areas are displayed as they are analyzed.
Exercise 4: Viewing Security Analysis Results
In this exercise you view the security analysis results.
To view security analysis results
- In the Security Configuration and Analysis console, click Security Configuration And Analysis.
- Double-click the Account Policies node, and then click the Password Policy security area.
In the details pane, what is indicated in the Policy column? In the Database Setting column? In the Computer Setting column?
In the Policy column, what does the red X indicate? What does the green check mark indicate?
Answer
Lesson Summary
In this lesson you learned how the Security Configuration and Analysis console uses a database to perform configuration and analysis functions.
You learned that when you configure system security using the Security Configuration and Analysis console, changes are made to the stored template in the database, not to the security template file. The security template file is only modified if you either return to Security Templates and edit that template or export the stored configuration to the same template file.
You also learned that Security Configuration and Analysis performs security analysis by comparing the current state of system security against a security template that you have imported to a personal database. This template is the database configuration, and it is the template that contains your preferred or recommended security settings for that system.
In the practice portion of this lesson you accessed the Security Configuration and Analysis console, set a working security database, analyzed system security, and then viewed the results.
EAN: N/A
Pages: 244