Lesson 4: User Rights
Although access to Windows 2000 objects such as files, folders, and printers is controlled by permissions, user rights grant other privileges and logon rights to users and groups in your computing environment.
After this lesson, you will be able to
- Explain the purpose of user rights
- Explain the purpose of privileges and logon rights
- Assign user rights to users and groups
Estimated lesson time: 10 minutes
User Rights
Administrators can assign specific rights to group accounts or to individual user accounts. These rights authorize users to perform specific actions, such as logging on to a system interactively or backing up files and directories. User rights are different from permissions because user rights apply to user accounts, and permissions are attached to objects. Additionally, because user rights are part of a GPO, user rights can be overridden depending on the GPO affecting the user.
User rights define capabilities at the local level. Although user rights can apply to individual user accounts, user rights are best administered on a group account basis. This ensures that a user logging on as a member of a group automatically inherits the rights associated with that group. By assigning user rights to groups rather than individual users, you simplify the task of user account administration. When users in a group all require the same user rights, you can assign the set of user rights once to the group rather than repeatedly assigning the same set of user rights to each individual user account.
User rights that are assigned to a group are applied to all members of the group while they remain members. If a user is a member of multiple groups, the user's rights are cumulative, which means that the user has more than one set of rights. The only time that rights assigned to one group might conflict with those assigned to another is in the case of certain logon rights. In general, however, user rights assigned to one group do not conflict with the rights assigned to another group. To remove rights from a user, the administrator simply removes the user from the group. In this case, the user no longer has the rights assigned to that group.
There are two types of user rights: privileges and logon rights.
Privileges
Privileges specify allowable user actions on the network. Table 21.13 describes the privileges that can be assigned to a user.
Table 21.13 Privileges
| Privilege | Description |
|---|---|
| Act As Part Of The Operating System | Allows a process to authenticate as any user and therefore gain access to the same resources as any user. Only low-level authentication services should require this privilege. The potential access is not limited to what is associated with the user by default, because the calling process may request that arbitrary additional accesses be put in the access token. Of even more concern is that the calling process can build an anonymous token that can provide any and all accesses. Additionally, this token does not provide a primary identity for tracking events in the audit log. Processes that require this privilege should use the LocalSystem account, which already includes this privilege, rather than using a separate user account with this privilege specially assigned. |
| Add Workstations To Domain | Allows the user to add a computer to a specific domain. The user specifies the domain through an administrative user interface on the computer being added, creating an object in the Computer container of Active Directory. The behavior of this privilege is duplicated in Windows 2000 by another access control mechanism (permissions attached to the Computer container or OU). |
| Back Up Files And Directories | Allows the user to circumvent file and directory permissions to back up the system. Specifically, the privilege is similar to granting the following permissions on all files and folders on the local computer: Traverse Folder/Execute File, List Folder/Read Data, Read Attributes, Read Extended Attributes, and Read Permissions. See also the Restore Files And Directories privilege. |
| Bypass Traverse Checking | Allows the user to pass through directories to which the user otherwise has no access, while navigating an object path in any Windows file system or in the registry. This privilege does not allow the user to list the contents of a directory, only to traverse directories. |
| Change The System Time | Allows the user to set the time for the internal clock of the computer. |
| Create A Pagefile | Allows the user to create and change the size of a pagefile by specifying a paging file size for a given drive in the System Properties Performance Options. |
| Create A Token Object | Allows a process to create a token that it can then use to get access to any local resources when the process uses NtCreate-Token() or other token-creation application programming interfaces (APIs). It is recommended that processes requiring this privilege use the LocalSystem account, which already includes this privilege, rather than using a separate user account with this privilege specially assigned. |
| Create Permanent Shared Objects | Allows a process to create a directory object in the Windows 2000 object manager. This privilege is useful to Kernel-mode components that plan to extend the Windows 2000 object namespace. Because components running in Kernel mode already have this privilege assigned to them, it is not necessary to specifically assign this privilege. |
| Debug Programs | Allows the user to attach a debugger to any process, providing powerful access to sensitive and critical system operating components. |
| Enable Computer And User Accounts To Be Trusted For Delegation | Allows the user to set the Trusted For Delegation setting on a user or computer object. The user or object that is granted this privilege must have write access to the account control flags on the user or computer object. A server process either running on a computer that is trusted for delegation or run by a user that is trusted for delegation can access resources on another computer. This uses a client's delegated credentials, as long as the client account does not have the Account Cannot Be Delegated account control flag set. Misuse of this privilege or of the Trusted For Delegation settings could make the network vulnerable to sophisticated attacks using Trojan horse programs that impersonate incoming clients and use their credentials to gain access to network resources. |
| Force Shutdown From A Remote System | Allows a user to shut down a computer from a remote location on the network. See also the Shut Down The System privilege. |
| Generate Security Audits | Allows a process to make entries in the security log for object access auditing. The process can also generate other security audits. The security log is used to trace unauthorized system access. See also the Manage Auditing And Security Log privilege. |
| Increase Quotas | Allows a process with write property access to another process to increase the processor quota assigned to that other process. This privilege is useful for system tuning, but can be abused, as in a denial-of-service attack. |
| Increase Scheduling Priority | Allows a process with write property access to another process to increase the execution priority of that other process. A user with this privilege can change the scheduling priority of a process through the Task Manager user interface. |
| Load and Unload Device Drivers | Allows a user to install and uninstall Plug and Play device drivers. Device drivers that are not Plug and Play are not affected by this privilege and can only be installed by administrators. Because device drivers run as trusted (highly privileged) programs, this privilege could be misused to install hostile programs and give these programs destructive access to resources. |
| Lock Pages In Memory | Allows a process to keep data in physical memory, preventing the system from paging the data to virtual memory on disk. Exercising this privilege could significantly affect system performance. This privilege is obsolete and is therefore never checked. |
| Manage Auditing And Security Log | Allows a user to specify object access auditing options for individual resources such as files, Active Directory objects, and registry keys. Object access auditing is not actually performed unless you have enabled it in the computer-wide audit policy settings under group policy or under group policy defined in Active Directory; this privilege does not grant access to the computer-wide audit policy. A user with this privilege can also view and clear the security log from the Event Viewer. |
| Modify Firmware Environment Values | Allows modification of the system environment variables, either by a user through the System Properties or by a process. |
| Profile Single Process | Allows a user to use Windows NT and Windows 2000 performance-monitoring tools to monitor the performance of nonsystem processes. |
| Profile System Performance | Allows a user to use Windows NT and Windows 2000 performance-monitoring tools to monitor the performance of system processes. |
| Remove Computer From Docking Station | Allows a user to undock a computer using the Windows 2000 user interface. |
| Replace A Process Level Token | Allows a process to replace the default token associated with a subprocess that has been started. |
| Restore Files And Directories | Allows a user to circumvent file and directory permissions when restoring backed up files and directories, and to set any valid security principal as the owner of an object. See also the Back Up Files And Directories privilege. |
| Shut Down The System | Allows a user to shut down the local computer. |
| Synchronize Directory Service Data | Allows a process to provide directory synchronization services; relevant only on domain controllers. By default, this privilege is assigned to the Administrator and LocalSystem accounts on domain controllers. |
| Take Ownership Of Files Or Other Objects | Allows a user to take ownership of any securable object in the system, including Active Directory objects, files and folders, printers, registry keys, processes, and threads. |
Some of these privileges can override permissions set on an object. For example, a user logged on to a domain account as a member of the Backup Operators group has the right to perform backup operations for all domain servers. However, this requires that users have the ability to read all files on those servers, even files on which their owners have set permissions that explicitly deny access to all users, including members of the Backup Operators group. A user right, in this case the right to perform a backup, takes precedence over all file and directory permissions.
Logon Rights
Logon rights specify the ways in which a user can log on to a system. Table 21.14 describes the logon rights that can be assigned to a user.
Table 21.14 Logon Rights
| Logon Right | Description |
|---|---|
| Access This Computer From The Network | Allows a user to connect to the computer over the network. By default, this privilege is granted to Administrators, Everyone, and Power Users. |
| Deny Access To This Computer From The Network | Prohibits a user or group from connecting to the computer from the network. By default, no one is denied this right. |
| Deny Logon As A Batch Job | Prohibits a user or group from logging on through a batch-queue facility. By default, no one is denied this right. |
| Deny Logon As A Service | Prohibits a user or group from logging on as a service. By default, no one is denied this right. |
| Deny Logon Locally | Prohibits a user or group from logging on locally. By default, no one is denied this right. |
| Log On As A Batch Job | Allows a user to log on using a batch-queue facility. By default, this privilege is granted to Administrators. |
| Log On As A Service | Allows a security principal to log on as a service, as a way of establishing a security context. The LocalSystem account always retains the right to log on as a service. Any service that runs under a separate account must be granted this right. By default, this right is not granted to anyone. |
| Log On Locally | Allows a user to log on at the computer's keyboard. By default, this right is granted to Administrators, Account Operators, Backup Operators, Print Operators, and Server Operators. |
The special user account LocalSystem has almost all privileges and logon rights assigned to it because all processes that are running as part of the operating system are associated with this account, and these processes require a complete set of user rights.
Assigning User Rights
To ease the task of user account administration, you should assign user rights primarily to group accounts rather than to individual user accounts. When you assign privileges to a group account, users are automatically assigned those privileges when they become members of that group.
Follow these steps to assign user rights:
- Access the Group Policy snap-in for a GPO.
- In the Group Policy snap-in, click Computer Configuration, double-click Windows Settings, double-click Security Settings, double-click Local Policies, and then double-click User Rights Assignment.
- In the details pane, right-click the user right that you want to set, and then click Security.
- In the Templates Security Policy Setting dialog box (see Figure 21.12), click the Define These Policy Settings check box, and then click Add.
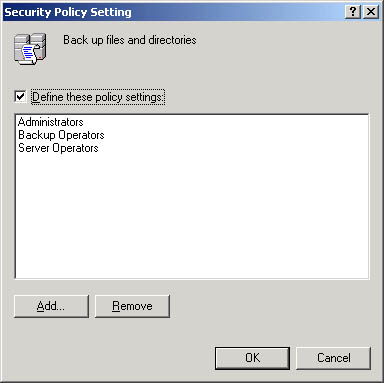
Figure 21.12 The Template Security Policy Setting dialog box
- In the Add User Or Group dialog box, add the users and/or groups you want to be affected by this user right, and then click OK.
- Click OK twice when you have finished adding users and/or groups.
A list of users and/or groups appears in the Computer Setting column in the details pane.
Lesson Summary
In this lesson you learned how user rights grant specific privileges and logon rights to users and groups in your computing environment. Privileges specify allowable user actions on the network. Logon rights specify the ways in which a user can log on to a system. To ease the task of user account administration, you should assign user rights primarily to group accounts, rather than to individual user accounts. User rights are assigned using the Group Policy snap-in.
EAN: N/A
Pages: 244