Lesson 1: Windows 2000 Overview
This lesson introduces you to the Windows 2000 family of products, including their features and benefits. It explains the key administrative differences between these products and the environment for which each product is designed.
After this lesson, you will be able to
- Describe Windows 2000
- Explain the key differences between Microsoft Windows 2000 Professional and Windows 2000 Server
- Describe the features and benefits of Windows 2000
- Describe the difference between a workgroup model and a domain model in a network environment
Estimated lesson time: 15 minutes
Overview of Windows 2000
Windows 2000 is a multipurpose operating system with integrated support for client/server and peer-to-peer networks. It incorporates technologies that reduce the total cost of ownership and provides for scalability from a small network to a large enterprise network. Total cost of ownership (TCO) is the total amount of money and time associated with purchasing computer hardware and software and deploying, configuring, and maintaining the hardware and software. TCO includes hardware and software updates, training, maintenance and administration, and technical support. One other major factor in TCO is lost productivity. Lost productivity can occur because of user errors, hardware problems, or software upgrades and retraining.
This training kit focuses on the following two versions of the Windows 2000 operating system:
- Windows 2000 Professional. This product is a high-performance, secure network client computer and corporate desktop operating system that includes the best features of Microsoft Windows 98 and significantly extends the manageability, reliability, security, and performance of Microsoft Windows NT Workstation 4.0. Windows 2000 Professional can be used alone as a desktop operating system, networked in a peer-to-peer workgroup environment, or used as a workstation in a Windows 2000 Server or Windows NT domain environment. Windows 2000 Professional can be used with the Microsoft BackOffice family of products to access resources from all the BackOffice products. This product is the main Microsoft desktop operating system for businesses of all sizes.
- Windows 2000 Server. This product is a file, print, terminal, and applications server, as well as a Web-server platform that contains all of the features of Windows 2000 Professional plus many new server-specific functions. This product is ideal for small- to medium-sized enterprise application deployments, Web servers, workgroups, and branch offices.
The Windows 2000 family also includes the following two products:
- Windows 2000 Advanced Server. This product is a powerful departmental and application server and provides rich network operations system (NOS) and Internet services. Advanced Server supports large physical memories, clustering, and load balancing. This product is beyond the scope of this training kit; features unique to Advanced Server will not be covered in this kit.
- Windows 2000 Datacenter Server. This product is the most powerful and functional server operating system in the Windows 2000 family. It is optimized for large data warehouses, econometric analysis, large-scale simulations in science and engineering, and server consolidation projects. This product is beyond the scope of this training kit; features unique to Datacenter Server will not be covered in this kit.
The following table describes the new features included in Windows 2000.
New Features Included in Windows 2000
| Feature | Description |
|---|---|
| Active Directory directory service | Active Directory directory service is an enterprise-class directory service that is scalable, built from the ground up using Internet-standard technologies, and fully integrated at the operating-system level. Active Directory simplifies administration and makes it easier for users to find resources. Active Directory provides a wide range of features and capabilities, including group policy, scalability without complexity, support for multiple authentication protocols, and the use of Internet standards. |
| Active Directory Service Interfaces (ADSI) | ADSI is a directory service model and a set of Component Object Model (COM) interfaces. It enables Windows 95, Windows 98, Windows NT, and Windows 2000 applications to access several network directory services, including Active Directory. It is supplied as a Software Development Kit (SDK). |
| Asynchronous Transfer Mode (ATM) | ATM is a high-speed, connection-oriented protocol designed to transport multiple types of traffic across a network. It is applicable to both local area networks (LANs) and wide area networks (WANs). Using ATM, your network can simultaneously transport a wide variety of network traffic: voice, data, image, and video. |
| Certificate Services | Using Certificate Services and the certificate management tools in Windows 2000, you can deploy your own public key infrastructure. With a public key infrastructure, you can implement standards-based technologies such as smart card logon capabilities, client authentication (through Secure Sockets Layer and Transport Layer Security), secure e-mail, digital signatures, and secure connectivity (using Internet Protocol Security). |
| Component Services | Component is a set of services based on extensions Services of the COM and on Microsoft Transaction Server (an earlier release of a component-based transaction processing system). Component Services provides improved threading and security, transaction management, object pooling, queued components, and application administration and packaging. |
| Disk quota support | You can use disk quotas on volumes formatted with the NTFS file system to monitor and limit the amount of disk space available to individual users. You can define the responses that result when users exceed your specified thresholds |
| Dynamic Host Configuration Protocol with Domain Name System (DNS) and Active Directory | DHCP works with DNS and Active Directory on Internet (IP) networks, freeing you from assigning and Protocol (DHCP) tracking static IP addresses. DHCP dynamically assigns IP addresses to computers or other resources connected to an IP network. |
| Encrypting File System (EFS) | The EFS in Windows 2000 complements existing access controls and adds a new level of protection for your data. The Encrypting File System runs as an integrated system service, making it easy to manage, difficult to attack, and transparent to the user. |
| Graphical Disk Management | Disk Management is a graphical tool for managing disk storage that includes many new features, such as support for new dynamic volumes, online disk management, local and remote drive management, and Volume Mount Points. |
| Group Policy (part of Active Directory) | Policies can define the allowed actions and the settings for users and computers. In contrast with local policy, you can use group policy to set policies that apply across a given site, domain, or organizational unit in Active Directory. Policy-based management simplifies such tasks as operating system updates, application installation, user profiles, and desktop-system lock down. |
| Indexing Service | Indexing Service provides a fast, easy, and secure way for users to search for information locally or on the network. Users can use powerful queries to search in files in different formats and languages, either through the Start menu Search command or through Hypertext Markup Language (HTML) pages that they view in a browser. |
| IntelliMirror | IntelliMirror provides high levels of control on client systems running Windows 2000 Professional. You can use IntelliMirror to define policies based on the respective user's business roles, group memberships, and locations. Using these policies, Windows 2000 Professional desktops are automatically reconfigured to meet a specific user's requirements each time that user logs on to the network, no matter where the user logs on. |
| Internet Authentication Service (IAS) | IAS provides you with a central point for managing authentication, authorization, accounting, and auditing of dial-up or Virtual Private Network users. IAS uses the Internet Engineering Task Force (IETF) protocol called Remote Authentication Dial-In User Service (RADIUS). |
| Internet Connection Sharing | With the Internet connection sharing feature of Network and Dial-Up Connections, you can use Windows 2000 to connect your home network or small office network to the Internet. For example, you might have a home network that connects to the Internet by using a dial-up connection. By enabling Internet connection sharing on the computer that uses the dial-up connection, you are providing network address translation, addressing, and name resolution services for all computers on your network. |
| Internet Information Services (IIS) | The powerful features in Internet Information Services (IIS), a part of Microsoft Windows 2000 Server, make it easy to 5.0 share documents and information across a company intranet or the Internet. Using IIS, you can deploy scalable and reliable Web-based applications, and you can bring existing data and applications to the Web. IIS includes Active Server Pages and other features. |
| Internet Security (IPSec) | Use IPSec to secure communications within an intranet and support to create secure Virtual Private Network solutions across the Internet. IPSec was designed by the IETF and is an industry standard for encrypting Transmission Control Protocol/ Internet Protocol (TCP/IP) traffic. |
| Kerberos v5 Protocol support | Kerberos v5 is a mature, industry-standard network authentication protocol. With Kerberos v5 support, a fast, single logon process gives users the access they need to Windows 2000 Server-based enterprise resources, as well as to other environments that support this protocol. Support for Kerberos v5 includes additional benefits such as mutual authentication (client and server must both provide authenti- cation) and delegated authentication (the user's credential is tracked end-to-end). |
| Layer 2 Tunneling Protocol (L2TP) support | L2TP is a more secure version of Point-to-Point Tunneling Protocol (PPTP) and is used for tunneling, address assign ment, and authentication. |
| Lightweight Directory Access Protocol (LDAP) support | LDAP, an industry standard, is the primary access protocol for Active Directory. LDAP version 3 was defined by the IETF. |
| Message queuing | Integrated message-queuing functionality in Windows 2000 helps developers build and deploy applications that run more reliably over networks, including the Internet. These applications can interoperate with applications running on different platforms such as mainframes and UNIX-based systems. |
| Microsoft Management Console (MMC) | Use MMC to arrange the administrative tools and processes you need within a single interface. You can also delegate tasks to specific users by creating preconfigured MMC consoles for them. The console will provide the user with the tools you select. |
| Network Address Translation (NAT) | Network Address NAT hides internally managed IP addresses from external networks by translating private internal addresses to public external addresses. This reduces IP address registration costs by letting you use unregistered IP addresses internally, with translation to a small number of registered IP addresses externally. It also hides the internal network structure, reducing the risk of attacks against internal systems. |
| Operating system migration, support,and integration | Windows 2000 integrates seamlessly with existing systems and contains support for earlier Windows operating systems, as well as new features for supporting other popular operating systems. Windows 2000 offers: Interoperability with Windows NT Server 3.51 and 4.0; support for clients running a variety of operating systems including Windows 3.x, Windows 95, Windows 98, and Windows NT Workstation 4.0; mainframe and midrange connectivity, using S/390 and AS/ 400 transaction and queuing gateways through Systems Network Architecture (SNA) Server; File Server for Macintosh, allowing Macintosh clients to use the TCP/IP protocol (AppleTalk File Protocol (AFP) over IP) to share files and to access shares on a Windows 2000 server. |
| Plug and Play | With Plug and Play, a combination of hardware and software support, the server can recognize and adapt to hardware configuration changes automatically, without your intervention and without restarting. |
| Public key infrastructure (PKI) and smart card infrastructure | Using Certificate Services and the certificate management tools in Windows 2000, you can deploy your own public key infrastructure. With a public key infrastructure, you can implement standards-based technologies such as smart card logon capabilities, client authentication (through Secure Sockets Layer and Transport Layer Security), secure e-mail, digital signatures, and secure connectivity (using Internet Protocol Security). Using Certificate Services, you can setup and manage certification authorities that issue and revoke X.509 v3 certificates. This means that you don't have to depend on commercial client authentication services, although you can integrate commercial client authentication into your public key infrastructure if you choose. |
| Quality of Service (QoS) | Using QoS, you can control how applications are allotted network bandwidth. You can give important applications more bandwidth and less important applications less bandwidth. QoS-based services and protocols provide a guaranteed, end-to-end, express delivery system for information across the network. |
| Remote Installation Services (RIS) | With Remote Installation Services, you can install Windows 2000 Professional remotely, without the need to visit each client. The target clients must either support remote booting with the Pre-Boot eXecution Environment (PXE) ROM, or else must be started with a remote-startup floppy disk. Installation of multiple clients becomes much simpler. |
| Removable Storage and Remote Storage | Removable Storage makes it easy to track your removable storage media (tapes and optical discs) and to manage the hardware libraries, such as changers and jukeboxes, that contain them. Remote Storage uses criteria you specify to automatically copy little-used files to removable media. If hard-disk space drops below specified levels, Remote Storage removes the (cached) file content from the disk. If the file is needed later, the content is automatically recalled from storage. Since removable optical discs and tapes are less expensive per mega-byte (MB) than hard disks, Removable Storage and Remote Storage can decrease your costs. |
| Routing and Remote Access service | Routing and Remote Access service is a single integrated that terminates connections from either dial-up or service Virtual Private Network (VPN) clients, or provides routing (IP, IPX, and AppleTalk), or both. With Routing and Remote Access, your Windows 2000 server can function as a remote access server, a VPN server, a gateway, or a branch-office router. |
| Safe mode startup | With safe mode, you can start Windows 2000 with a minimal set of drivers and services, and then view a log showing the sequence of events at startup. Using safe mode, you can diagnose problems with drivers and other components that might be preventing normal startup. |
| Smart card infrastructure | Using Certificate Services and the certificate management tools in Windows 2000, you can deploy your own public key infrastructure. With a public key infrastructure, you can implement standards-based technologies such as smart card logon capabilities, client authentication (through Secure Sockets Layer and Transport Layer Security), secure e-mail, digital signatures, and secure connectivity (using Internet Protocol Security). |
| TAPI 3.0 | TAPI 3.0 unifies IP and traditional telephony to enable developers to create a new generation of powerful computer telephony applications that work as effectively over the Internet or an intranet as over the traditional telephone network. |
| Terminal Services | The Windows 2000 Server family offers the only server operating systems that integrate terminal emulation services. Using Terminal Services, a user can access programs running on the server from a variety of older devices. For example, a user could access a virtual Windows 2000 Professional desktop and 32-bit Windows-based applications from hardware that couldn't run the software locally. Terminal Services provides this capability for both Windows and non-Windows-based client devices. (Non-Windows devices require add-on software by Citrix Systems.) |
| Virtual Private Network (VPN) | You can allow users ready access to the network even when they're out of the office, and reduce the cost of this access, by implementing a VPN. Using VPNs, users can easily and securely connect to the corporate network. The connection is through a local Internet Service Provider (ISP), which reduces connect-time charges. With Windows 2000 Server, you can use several new, more secure protocols for creating Virtual Private Networks, including: L2TP, a more secure version of PPTP (L2TP is used for tunneling, address assignment, and authentication) and IPSec, a standard-based protocol that provides the highest levels of VPN security. Using IPSec, virtually everything above the networking layer can be encrypted. |
| Windows Media Services | Using Windows Media Services, you can deliver high-quality streaming multimedia to users on the Internet and intranets. |
| Windows Script Host (WSH) | Using WSH, you can automate actions such as creating a shortcut and connecting to and disconnecting from a network server. WSH is language-independent. You can write scripts in common scripting languages such as VBScript and JScript. |
Windows 2000 Network Environments
A Windows 2000-based network environment can be set up using either a workgroup model or a domain model. Both Windows 2000 Professional and Windows 2000 Server can participate in either of these two models. The administrative differences between the two products depend on the network environmental model.
Windows 2000 Workgroup Model
A Windows 2000 workgroup is a logical grouping of networked computers that share resources, such as files and printers. A workgroup is referred to as a peer-to-peer network because all computers in the workgroup can share resources as equals, or as peers, without a dedicated server. Each computer in the work-group, running either Windows 2000 Server or Windows 2000 Professional, maintains a local security database, as shown in the figure below. A local security database is a list of user accounts and resource security information for the computer on which it resides. Therefore, the administration of user accounts and resource security in a workgroup is decentralized.
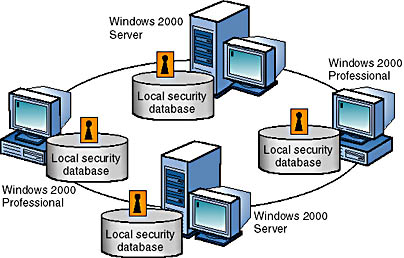
An example of a Windows 2000 workgroup
The following are disadvantages of using workgroup mode:
- A user must have a user account on each computer to which he or she wants to gain access.
- Any changes to user accounts, such as changing a user's password or adding a new user account, must be made on each computer in the workgroup. If you forget to add a new user account to a computer in your workgroup, the new user will not be able to log on to that computer and will be unable to access resources on it.
- Device and file sharing is handled by individual computers, and only for the users that have accounts on each individual computer.
A Windows 2000 workgroup provides the following advantages:
- A workgroup does not require a computer running Windows 2000 Server to hold centralized security information.
- A workgroup is simple to design and implement. A workgroup does not require the extensive planning and administration that a domain requires.
- A workgroup is convenient for a limited number of computers in close proximity. (A workgroup becomes impractical in environments with more than 10 computers.)
NOTE
In a workgroup, a computer running Windows 2000 Server that is not a member of a Windows 2000 domain is called a stand-alone server.
Windows 2000 Domain Model
A Windows 2000 domain is a logical grouping of network computers that share a central directory database. A directory database contains user accounts and security information for the domain. This directory database is known as the directory and is the database portion of Active Directory, which is the Windows 2000 directory service. Active Directory replaces all previous "domain" information storage containers, including multiple domains. Active Directory also contains information about services and other resources, organizations, and more.
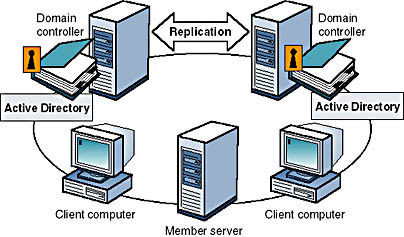
An example of a Windows 2000 domain
In a domain, the directory resides on computers that are configured as domain controllers. A domain controller is a server that manages all security-related aspects of user-domain interactions. Security and administration are centralized. Only computers running Windows 2000 Server may be designated as domain controllers.
A domain does not refer to a single location or specific type of network configuration. The computers in a domain can share physical proximity on a small LAN or can be located in different corners of the world, communicating over any number of physical connections, including dial-up lines, Integrated Services Digital Network (ISDN) lines, fiber lines, Ethernet lines, token ring connections, frame relay connections, satellite connections, and leased lines. The benefits of a Windows 2000 domain are as follows:
- A domain allows centralized administration because all user information is stored centrally. If a user changes his or her password, the change is automatically replicated throughout the domain.
- A domain provides a single logon process for users to gain access to network resources, such as file, print, and application resources for which they have permissions. In other words, a user can log on to one computer and use resources on another computer in the network as long as he or she has appropriate privileges to the resource.
- A domain provides scalability so that an administrator can create very large networks.
A typical Windows 2000 domain will have the following types of computers:
- Domain controllers running Windows 2000 Server. Each domain controller stores and maintains a copy of the directory. In a domain, you create a user account once, which Windows 2000 records in the directory. When a user logs on to a computer in the domain, a domain controller checks the directory for the user name, password, and logon restrictions to authenticate the user. When there are multiple domain controllers, they periodically replicate their directory information.
- Member servers running Windows 2000 Server. A member server is a server that is not configured as a domain controller. A member server does not store directory information and cannot authenticate domain users. Member servers provide shared resources such as shared folders or printers.
- Client computers running Windows 2000 Professional. Client computers run a user's desktop environment and allow the user to gain access to resources in the domain.
Lesson Summary
In this lesson you learned that Windows 2000 is a multipurpose operating system with integrated support for client/server and peer-to-peer networks. Windows 2000 consists of a family of four products: Windows 2000 Professional, Windows 2000 Server, Windows 2000 Advanced Server, and Windows 2000 Datacenter Server. Windows 2000 Professional is optimized for use alone as a desktop operating system, as a networked computer in a peer-to-peer workgroup environment, or as a workstation in a Windows 2000 Server domain environment. Windows 2000 Server is optimized for use as a file, print, and application server, as well as a Web-server platform.
A Windows 2000 workgroup is a logical grouping of networked computers that share resources, such as files and printers. A workgroup does not have a Windows 2000 Server domain controller. Security and administration for Windows 2000 Professional and Windows 2000 Server member servers are not centralized in a workgroup because each computer maintains a list of user accounts and resource security information for that computer.
A Windows 2000 domain is a logical grouping of networked computers that share a central directory database containing security and user account information. This directory database is known as the directory and is the database portion of Active Directory, the Windows 2000 directory service. In a domain, security and administration are centralized because the directory resides on domain controllers, which manage all security-related aspects of user-domain interactions.
EAN: N/A
Pages: 244
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XV Customer Trust in Online Commerce