Lesson 4: Introducing and Enabling IPSec
Using Internet Protocol Security (IPSec) is the long-term solution for secure networking. More and more corporations are starting to use IPSec. It provides a key line of defense against private network and Internet attacks, balancing ease of use with security. This lesson discusses the technologies collectively referred to as IPSec.
After this lesson, you will be able to
- Explain the benefits of IPSec
- Describe the architecture of IPSec
Estimated lesson time: 15 minutes
Internet Protocol Security
As the Internet and intranets have evolved, the need for security has increased. Users are mainly concerned that that network traffic is safe from the following:
- Data modification while en route
- Interception
- Viewing or copying when intercepted
- Being accessed by unauthenticated parties
IPSec is a framework of open standards for ensuring private, secure communications over IP networks through the use of cryptographic security services. The Microsoft Windows 2000 implementation of IPSec is based on standards developed by the Internet Engineering Task Force (IETF) IPSec working group. IPSec has two goals:
- To protect IP packets
- To provide a defense against network attacks
Both goals are met through the use of cryptography-based protection services, security protocols, and dynamic key management. Starting with these two goals provides both the strength and flexibility to protect communications among computers on a private network, in remote sites connected by the Internet, and by dial-up clients. It can even be used to filter data packets on a network.
IPSec is based on an end-to-end security model, meaning that the only computers that must know about IPSec are the sending and receiving computers. Each handles security at its respective end, with the assumption that the medium over which the communication takes place is not secure. Routers that forward packets between the source and destination are not required to support IPSec. This model allows IPSec to be successfully deployed for these enterprise scenarios:
- Local area network (LAN)— client/server, peer-to-peer networks
- Wide area network (WAN) — router-to-router networks
- Remote access — access by dial-up clients, Internet access from private networks
IPSec Architecture
IPSec implementation in Windows 2000 consists of several components:
- IPSec policy agent
- ISAKMP/Oakley Key Management Service (IKE)
- IPSec driver
- IPSec model
IPSec Policy Agent Service
The policy agent is an IPSec mechanism residing on each Windows 2000 computer. The policy agent starts automatically when the computer is started. The policy agent performs the following tasks at the interval specified in the IPSec policy, as illustrated in Figure 9.15:
Figure 9.15 Specifying the IP security policy change interval
- The policy agent retrieves the computer's assigned IPSec policy from Windows 2000 Active Directory directory services.
- If there are no IPSec policies in the directory service or if the policy agent cannot connect to the directory service, it attempts to read the policy from the computer's registry. The policy agent service stops if there are no IPSec policies in the directory service or registry.
- If there are policies in the directory service, the data transfer of policy information from the directory service to the computer is protected with data integrity and encryption services.
- The policy agent sends the policy information to the IPSec driver, the IKE, and the computer's registry.
ISAKMP/Oakley Key Management Service (IKE)
This service is an IPSec mechanism residing on each computer running Windows 2000. Before IP datagrams can be transmitted from one computer to another, a security association must be established between the two computers. A security association is a set of parameters that defines the common security services and mechanisms used to protect the communication, such as keys and security properties.
The IKE centralizes security association management, reducing connection time. The Oakley protocol generates the actual keys that will be used to encrypt and decrypt the transferred data. IKE performs a two-phase operation:
- It establishes a secure channel between the two computers for the communication. To achieve this, it authenticates computer identities and exchanges keying data to establish the shared, secret key the computers will use to encrypt and decrypt the data.
- It establishes a security association between the two computers, which is passed to the IPSec driver, along with the shared key, on both the sending and receiving computers.
The policy agent automatically starts the IKE. This service does not start automatically or manually unless the policy agent service is running. If a security association cannot be established, the IPSec policy can be configured to either block communication or accept unsecured communication.
IPSec Driver
The IPSec driver (IPSEC.SYS) resides on each computer running Windows 2000. The driver watches all IP datagrams for a match with a filter list in the computer's security policy. The filter list defines which computers and networks require secure communications. If a filter match is found, the IPSec driver on the sending computer uses the SA and shared key to encrypt the data and sends it to the receiving computer. The IPSec driver on the receiving computer decrypts the transferred data and passes it to the receiving application.
NOTE
The policy agent automatically starts the IPSec driver.
The IPSec Model
Figure 9.16 shows two users on intranet computers running Windows 2000 Server. Both Computer A and Computer B have an active IPSec policy. Alice is using Computer A and needs to send some information to Bob, who is using Computer B.
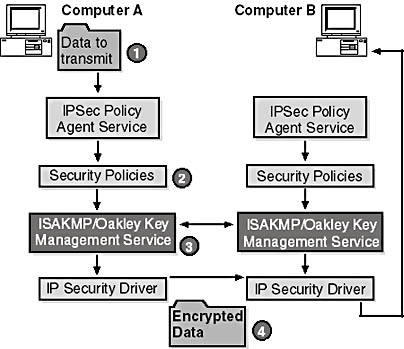
Figure 9.16 IPSec policy flow to encrypt data between two computers
- Alice launches the File Transfer Protocol (FTP) application from Host A and sends data to Bob.
- The IPSec driver on Host A notifies the IKE service that IPSec is needed for this communication by using the policies in the registry written by the policy agent.
- The IKE services on Host A and Host B establish a shared key and SA.
- The IPSec drivers on Host A and Host B each receive the key and SA.
- The IPSec driver on Host A uses the key to encrypt the data and sends the data to Host B.
- Host B's IPSec driver decrypts the data and passes it to the receiving application, where Bob retrieves the data.
NOTE
Any routers or switches that are in the path between the communicating computers should only participate in forwarding the encrypted IP datagrams to their destination. However, if a firewall or other security gateway is between the communicating computers, IP forwarding must be enabled or special filtering must be created to permit forwarding of encrypted IP datagrams.
Considerations for IPSec
IPSec provides encryption of outgoing packets, but at a cost in performance. IPSec implements symmetric encryption of network data that is very efficient. However, for servers supporting many simultaneous network connections, the additional cost of encryption is significant, so you need to test IPSec using simulated network traffic before deploying it. Testing is also important if you are using a third-party hardware or software product to provide IP security. You can define IPSec policies for each domain. You can configure IPSec policies to do the following:
- Specify the types of authentication and the levels of confidentiality required between IPSec clients
- Specify the lowest security level at which communications are allowed to occur between IPSec-aware clients
- Allow or prevent communications with non-IPSec-aware clients
- Require all communications to be encrypted for confidentiality, or allow communications to be carried out in plaintext
Consider using IPSec to provide security for the following applications:
- Peer-to-peer communications over your organization's intranet, such as legal-department or executive-committee communications
- Client/server communications to protect sensitive (confidential) information stored on servers
- Remote access (dial-up or virtual private network [VPN]) communications (For VPNs using IPSec with Layer Two Tunneling Protocol [L2TP], remember to set up Group Policy to permit auto enrollment for IPSec certificates. For detailed information about machine certificates for L2TP over IPSec VPN connections, see Windows 2000 Help.)
- Secure router-to-router WAN communications
Consider the following strategies for IPSec in your network security deployment plan:
- Identify clients and servers to use IPSec communications
- Identify whether client authentication is based on Kerberos trust or digital certificates
- Describe each IPSec policy, including rules and filter lists
- Describe certificate services needed to support client authentication by digital certificates
- Describe enrollment processes and strategies to enroll users for IPSec certificates
Lesson Summary
IPSec is a framework of open standards for ensuring private, secure communications over IP networks through the use of cryptographic security services. IPSec is transparent to the user and provides a high level of secure communications with a low cost of use.
The architecture of IPSec is comprised of four major components: IPSec policy agent, IKE Service, IPSec driver, and IPSec model.
EAN: N/A
Pages: 244