Systems Searching for Design Vulnerabilities
As was mentioned in Chapter 2, these vulnerabilities are especially dangerous, since they are hard to detect and eliminate. In this case, the vulnerability is characteristic of an information-system project or a program algorithm and, consequently, even perfect implementation (which is virtually impossible) can not eliminate the inherent vulnerability. Depending on the subject to be analyzed, it is possible to use various tools for detecting design vulnerabilities. As a rule, when searching for design vulnerabilities in the information system, we have the following two aims:
-
Analysis of the algorithm of the software and hardware complex
-
Analysis of the corporate system project
The first aim is achieved relatively easily, since it is possible to use the existing techniques in the field of software verification during detection of the software-algorithm vulnerabilities. The second aim is much more difficult to implement but, even in this case, there are special tools that enable the analysis of design vulnerabilities.
Project Analysis
Table 6.1 outlines advantages and drawbacks of such systems.
| Advantages | Drawbacks |
|---|---|
| | |
| Automation of problems that are difficult to formalize | The quality of the results depends on expert information built into the system |
| Expense | |
| Limited area of application | |
The CRAMM system (CCTA Risk Analysis and Management Technology) is one of the best-known systems in this class. It was developed in 1985 by BIS Applied Systems Ltd., as a result of a research project initiated by the British government. The product, based on the CCTA methodology, was modified several times according to the security requirements of the systems it was being used to analyze. Currently, there are different versions of this product intended for government organizations, military organizations, private companies and financial institutions.
Besides the above-mentioned systems, there are other solutions intended for undertaking risk analysis, including design-vulnerability analysis. These systems include the following: RANK-IT, @RISK, ALRAM, ARES, LAVA etc. These systems are covered in detail in [Stang1-93] and [Nist1-91].
Algorithm Analysis
The PVS (Prototype Verification System) developed in the Computer Science Laboratory at the Stanford Research Institute (SRI), which is famous for creating intrusion detection systems like NIDES and EMERALD, is the most common among the systems of this class. The PVS system has the built-in language of formal software descriptions, along with a subsystem intended for proving theorems.
Systems Detecting Implementation Vulnerabilities
Quite a large number of attacks, such as buffer overflow, are based on hardware and software implementation errors. Because of this, the detection of such vulnerabilities is very important. Initially, security analysis (or, to be more precise, a search for software implementation errors) was conducted using standard methods, which implied software verification (i.e., finding proof of its accuracy). Using special methods and demonstrating that the initial and final conditions were satisfied, the investigators proved the software's health. However, despite their ability to detect specific errors, these methods can not be used for finding a number of vulnerabilities, particularly backdoors intentionally introduced into the software code. This is mainly due to the fact that, currently, there is no formal vulnerability description. The scientists suggested several different approaches to solving this problem, which can be classified into the following two main classes: analytical and experimental (Fig. 6.4). Systems of the first type are used to prove the existence of vulnerabilities by mathematical methods or analytical methods. This method is reliable and efficient, since it enables the investigator to determine specifically if any vulnerabilities are present in the system under consideration. However, the common drawback of these systems is the fact that they are hard to implement. Experimental methods enable the researcher to detect vulnerabilities present during the testing, which can be conducted in a virtual test environment (the sandbox in Java technology can be though of as an analog of this technology) using test generators, syntax and semantic analysis, etc.
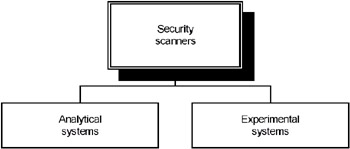
Fig. 6.4. Classification of the methods for searching for implementation vulnerabilities
Searching for vulnerabilities at the stage of software development allows the avoidance of many future security problems. Not only software developers can use the systems described in this section to provide information security, but also various organizations certifying hardware and software tools. Since my intent is to describe the most popular systems - those that can be employed by most users - I will briefly describe those used in certification laboratories.
Testing and controlling tools, in turn, can be classified depending on the availability of the source code of the program being analyzed (Fig. 6.5).
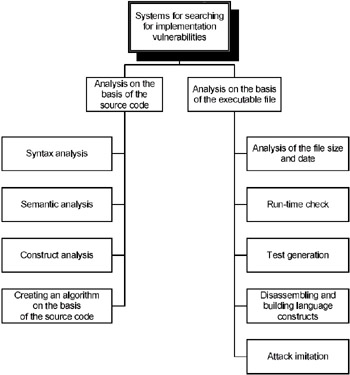
Fig. 6.5. Classification of the tools for searching for implementation vulnerabilities
Analysis of the Source Code
To create error-free software and hardware, it is necessary to organize the design and development process of the product correctly. This requirement, however, is not always met, due to the desire to release the product as soon as possible (or to accomplish obligations undertaken according to a contract). In this case, one generally uses various formal methods of describing the algorithm implemented by the product, the accordance of which is checked during the entire development process. Furthermore, one can check for vulnerabilities in the release version of the product. Examples of such systems are SLINT, RATS, and flawfinder. Quite often, if the source code of the software to be analyzed is not available, the product is disassembled. The resulting listing is then analyzed using standard source-code analysis methods.
The main drawback of source code analysis is the possibility of introducing various distortions into the software code when compiling and building programs. Even software that can be considered perfect from the point of view of the software code can have vulnerabilities introduced at the stage of compilation and building. Table 6.2 outlines the advantages and drawbacks of systems based on source-code analysis.
| Advantages | Drawbacks |
|---|---|
| | |
| Automation of the vulnerabilities search | The quality of the system functioning depends on the methods that it implements |
| Each programming language requires its own analyzer | |
| Limited area of application | |
| Not practical for analyzing large amounts of the source code | |
| Such systems require qualified skilled personnel | |
| When compiling and building the software project, various deviations can be introduced, which are virtually unnoticeable at the stage of the source code analysis | |
Analysis of the Executable Code
In most cases, software is provided without the source code. Furthermore, source-code analysis requires qualified personnel. As well as this, the lack of efficient analyzers prevents investigators from performing their research at a high-quality level. Because of the above-mentioned factors, systems intended for detecting vulnerabilities in the source code are highly popular. As already mentioned, executable-code analyzers can be classified in the following categories:
-
Analysis of file size, date and other attributes
-
Run-time check
-
Test generation
-
Disassembling
-
Attack imitation
File-Attribute Analysis
This method is very simple to implement. It simply compares the size and date of the file being analyzed with the data stored in the file database of existing vulnerable files. If these values match, the system decides that a vulnerability is present. For example, System Scanner performs a range of checks using this method.
Run-Time Check
Systems utilizing this approach (for example, BoundsChecker Pro, HeapAgent, and Purify NT) detect various errors (including vulnerabilities) that are hard to detect during source-code analysis. Although syntax and semantics analysis enables the detection of most errors with a high level of probability, some errors are still missed by these analyzers and can only be detected at runtime.
Test-Generation Systems
Test-generation systems apply a range of external actions to the software under analysis and investigate the system's response to these tests. Quite often, these tools analyze the system's reaction to various boundary values of the input data, including the following:
-
Buffer overflow
-
Array indexes exceeding array boundaries
-
Lack of argument check
-
Incorrect memory access
-
Invalid arguments passed to critical procedures
The need for such tests is clear, since, according to statistics, most implementation vulnerabilities relate to the above-mentioned errors (for example, buffer overflow).
Table 6.3 lists the main advantages and drawbacks of this method.
| Advantages | Drawbacks |
|---|---|
| | |
| Able to test software without needing the source code | Detects only specific classes of vulnerabilities and errors |
| Relative simplicity of implementation | The presence of some errors is not always an indication of vulnerability |
Disassembling
The process of disassembling itself is not very helpful when detecting vulnerabilities, since, in this case, the amount of code to be analyzed will significantly exceed the amount of the source code written using higher-level programming language. However, the disassembled code can be used as a source of information for higher-level analyzers.
Exploit Checking
Attack simulators are intended for modeling various unauthorized activities directed at the components of the information system. These systems are the most popular all over the world, since they are relatively simple and not very expensive. Using such simulators, it is possible to detect most vulnerabilities before they can be exploited to implement an attack. Systems in this class include SATAN, Internet Scanner, etc.
Attack simulators are equally successful in detecting both implementation vulnerabilities and configuration vulnerabilities. Consequently, the information provided in the next section (which is entirely dedicated to searching for configuration vulnerabilities) is also applicable to attack simulators. These products are the most popular with users.
EAN: 2147483647
Pages: 152
- ERP Systems Impact on Organizations
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- Distributed Data Warehouse for Geo-spatial Services
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations