4.11 Deciphering the security descriptor components
4.11 Deciphering the security descriptor components
Retrieving the security descriptor components, such as the Access Control List and the Access Control Entries of the Discretionary ACL and the System ACL, is the very first step of the security descriptor deciphering. As shown in the two previous WMI and ADSI output representations, some properties contain numeric values. A closer look at these values shows that every bit composing the values has a specific meaning for the property. The interpretation of the properties represents the second step of the deciphering. In this section, we will decipher each value available from a security descriptor.
4.11.1 Deciphering the Owner and Group properties
The Owner and Group properties in the WMI object model are represented by a Win32_Trustee instance in an SWBemObject object. Therefore, Sample 4.28 ("Deciphering a WMI security descriptor representation"), by its recursive logic, naturally detects that the Group and Owner properties of the Win32_SecurityDescriptor class contain a Win32_Trustee instance. No particular deciphering technique is necessary. The Win32_Trustee instance is deciphered inside the DecipherWMISecurityDescriptor() in Sample 4.28. The following output sample shows the Win32_Trustee instances contained in a WMI Owner security descriptor representation coming from a folder (lines 69 through 76).
1: C:\>WMIManageSD.Wsf /FileSystem:C:\MyDirectory /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via WMI from 'C:\MyDirectory'. 6: 7: +- Win32_SecurityDescriptor ---------------------------------------------------------------- 8: | ControlFlags: .......................... &hB414 ..: 68: | +----------------------------------------------------------------------------------------- 69: | Owner: ................................. (Win32_Trustee) 70: | +- Win32_Trustee ------------------------------------------------------------------------- 71: | | Domain: .............................. BUILTIN 72: | | Name: ................................ Administrators 73: | | SID: ................................. 1,2,0,0,0,0,0,5,32,0,0,0,32,2,0,0 74: | | SidLength: ........................... 16 75: | | SIDString: ........................... S-1-5-32-544 76: | +----------------------------------------------------------------------------------------- ..: ..: ..:
When the security descriptor is represented in the ADSI object model, things are easier. The Group and the Owner properties of a security descriptor contain a literal string representing the trustee (i.e., Domain\User), which is displayed by the DecipherADSISecurityDescriptor() function in Sample 4.29 ("Deciphering an ADSI security descriptor representation"). If some SID resolution problems occur, the property could return a SID instead of a literal string representing the trustee. The following output sample shows the trustees contained in an ADSI security descriptor representation coming from a folder (line 8 for the trustee contained in the Owner property and line 9 for the trustee contained in the Group property).
1: C:\>WMIManageSD.Wsf /FileSystem:C:\MyDirectory /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via ADSI from 'C:\MyDirectory'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. LISSWARENET\Domain Users 10: | Revision: .............................. 1 11: | Control: ............................... &h9404 ..: ..: ..:
4.11.2 Deciphering the security descriptor Control Flags
The security descriptor Control Flags property (called ControlFlags with WMI and Control with ADSI; see Table 4.3, "The WMI and ADSI Security Descriptor Exposed Methods and Properties") is helpful in determining the presence of the various security descriptor subcomponents, such as the DACL and SACL. With the introduction of Windows 2000, the security descriptor inheritance is also determined by this property. Each bit in the value has a specific meaning, summarized in Table 4.8.
| SE_GROUP_DEFAULTED | 0x2 | A default mechanism, rather than the original provider of the security descriptor, provided the security descriptor's group SID. To set this flag, use the SetSecurityDescriptorGroup function. |
| SE_OWNER_DEFAULTED | 0x1 | A default mechanism, rather than the original provider of the security descriptor, provided the security descriptor's owner security identifier (SID). To set this flag, use the SetSecurityDescriptorOwner function. |
| SE_DACL_DEFAULTED | 0x8 | Indicates a security descriptor with a default DACL. For example, if an object's creator does not specify a DACL, the object receives the default DACL from the creator's access token. This flag can affect how the system treats the DACL, with respect to ACE inheritance. The system ignores this flag if the SE_DACL_PRESENT flag is not set. This flag is used to determine how the final DACL on the object is to be computed and is not stored physically in the security descriptor control of the securable object. To set this flag, use the SetSecurityDescriptorDacl function. |
| SE_SACL_DEFAULTED | 0x20 | A default mechanism, rather than the original provider of the security descriptor, provided the SACL. This flag can affect how the system treats the SACL, with respect to ACE inheritance. The system ignores this flag if the SE_SACL_PRESENT flag is not set. To set this flag, use the SetSecurityDescriptorSacI function. |
| SE_DACL_PRESENT | 0x4 | Indicates a security descriptor that has a DACL. If this flag is not set, or if this flag is set and the DACL is NULL, the security descriptor allows full access to everyone. This flag is used to hold the security information specified by a caller until the security descriptor is associated with a securable object. Once the security descriptor is associated with a securable object, the SE_DACL_PRESENT flag is always set in the security descriptor control. To set this flag, use SetsecurityDescriptorDacl. |
| SE_SACL_PRESENT | 0x10 | Indicates a security descriptor that has a SACL. To set this flag, use the SetSecurityDescriptorSacI function. |
| SE_DACL_PROTECTED | 0x1000 | Windows 2000/XP: Prevents the DACL of the security descriptor from being modified by inheritable ACEs. To set this flag, use the SetSecurityDescriptorControl function. |
| SE_SACL_PROTECTED | 0x2000 | Windows 2000/XP: Prevents the SACL of the security descriptor from being modified by inheritable ACEs. To set this flag, use the SetSecurityDescriptorControl function. |
| SE_DACL_AUTO_INHERIT_REQ | 0x0100 | Requests that the provider for the object protected by the security descriptor automatically propagate the DACL to existing child objects. If the provider supports automatic inheritance, it propagates the DACL to any existing child objects, and sets the SE_DACL_AUTO_INHERITED bit in the security descriptors of the object and its child objects. |
| SE_SACL_AUTO_INHERIT_REQ | 0x0200 | Requests that the provider for the object protected by the security descriptor automatically propagates the SACL to existing child objects. If the provider supports automatic inheritance, it propagates the SACL to any existing child objects, and sets the SE_SACL_AUTO_INHERITED bit in the security descriptors of the object and its child objects. |
| SE_DACL_AUTO_INHERITED | 0x0400 | Windows 2000/XP: Indicates a security descriptor in which the DACL is set up to support automatic propagation of inheritable ACEs to existing child objects. For Windows 2000 ACLs that support auto inheritance, this bit is always set. It is used to distinguish these ACLs from Windows NT 4.0 ACLs that do not support auto-inheritance. Protected servers can call the ConvertToAutoInheritPrivateObjectSecurity function to convert a security descriptor and set this flag. This bit is not set in security descriptors for Windows NT versions 4.0 and earlier, which do not support automatic propagation of inheritable ACEs. |
| SE_SACL_AUTO_INHERITED | 0x0800 | Windows 2000/XP: Indicates a security descriptor in which the SACL is set up to support automatic propagation of inheritable ACEs to existing child objects. The system sets this bit when it performs the automatic inheritance algorithm for the object and its existing child objects. Protected servers can call the ConvertToAutoInheritPrivateObjectSecurity function to convert a security descriptor and set this flag. This bit is not set in security descriptors for Windows NT versions 4.0 and earlier, which do not support automatic propagation of inheritable ACEs. |
| SE_SELF_RELATIVE | 0x8000 | Indicates a security descriptor in self-relative format with all the security information in a contiguous block of memory. If this flag is not set, the security descriptor is in absolute format. For more information, see Absolute and Self-Relative Security Descriptors. |
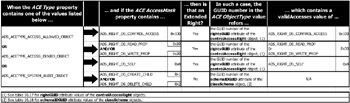
Based on these values, the Control Flags bits must be deciphered with a bitwise operation, since each label in Table 4.8 corresponds to a specific bit setting in the value. For instance, Figure 4.18 shows flags that are turned ON or OFF when the Control Flags value equals 0xB814 (flags turned ON are in bold).
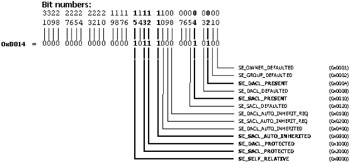
Figure 4.18: The Control Flags bitwise values.
Based on the flag values, Sample 4.30 deciphers the various bits of the property.
Sample 4.30: Deciphering the security descriptor Control Flags property
.: .: .: 8:' ---------------------------------------------------------------------------------------- 9:Function DecipherSDControlFlags (intControlFlags) ..: 15: strTemp = "&h" & Hex (intControlFlags) 16: 17: If (intControlFlags And SE_OWNER_DEFAULTED) Then 18: strTemp = strTemp & "," & "SE_OWNER_DEFAULTED" 19: End If 20: If (intControlFlags And SE_GROUP_DEFAULTED) Then 21: strTemp = strTemp & "," & "SE_GROUP_DEFAULTED" 22: End If 23: If (intControlFlags And SE_DACL_PRESENT) Then 24: strTemp = strTemp & "," & "SE_DACL_PRESENT" 25: End If 26: If (intControlFlags And SE_DACL_DEFAULTED) Then 27: strTemp = strTemp & "," & "SE_DACL_DEFAULTED" 28: End If 29: If (intControlFlags And SE_SACL_PRESENT) Then 30: strTemp = strTemp & "," & "SE_SACL_PRESENT" 31: End If 32: If (intControlFlags And SE_SACL_DEFAULTED) Then 33: strTemp = strTemp & "," & "SE_SACL_DEFAULTED" 34: End If 35: If (intControlFlags And SE_DACL_AUTO_INHERIT_REQ) Then 36: strTemp = strTemp & "," & "SE_DACL_AUTO_INHERIT_REQ" 37: End If 38: If (intControlFlags And SE_SACL_AUTO_INHERIT_REQ) Then 39: strTemp = strTemp & "," & "SE_SACL_AUTO_INHERIT_REQ" 40: End If 41: If (intControlFlags And SE_DACL_AUTO_INHERITED) Then 42: strTemp = strTemp & "," & "SE_DACL_AUTO_INHERITED" 43: End If 44: If (intControlFlags And SE_SACL_AUTO_INHERITED) Then 45: strTemp = strTemp & "," & "SE_SACL_AUTO_INHERITED" 46: End If 47: If (intControlFlags And SE_DACL_PROTECTED) Then 48: strTemp = strTemp & "," & "SE_DACL_PROTECTED" 49: End If 50: If (intControlFlags And SE_SACL_PROTECTED) Then 51: strTemp = strTemp & "," & "SE_SACL_PROTECTED" 52: End If 53: If (intControlFlags And SE_SELF_RELATIVE) Then 54: strTemp = strTemp & "," & "SE_SELF_RELATIVE" 55: End If 56: 57: DecipherSDControlFlags = ConvertStringInArray (strTemp, ",") 58: 59:End Function
Basically, the code performs a Boolean operation on the Control Flags value to determine the state of the bits corresponding to the flags listed in Table 4.8. If the bit is ON, the code constructs a comma-delimited string with the different bit labels from Table 4.8 (lines 15 through 55). Most values contained in a security descriptor or in one of its components use a similar deciphering technique. Only the flags used to decipher the value are different. Once completed, the comma-delimited string is converted to an array (line 57). The obtained output result would be as follows:
1: C:\>WMIManageSD.Wsf /FileSystem:C:\MyDirectory /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via WMI from 'C:\MyDirectory'. 6: 7: +- Win32_SecurityDescriptor ---------------------------------------------------------------- 8: | ControlFlags: .......................... &hB814 9: SE_DACL_PRESENT 10: SE_SACL_PRESENT 11: SE_SACL_AUTO_INHERITED 12: SE_DACL_PROTECTED 13: SE_SACL_PROTECTED 14: SE_SELF_RELATIVE ..: ..: ..:
The DecipherSDControlFlags() function is called by Sample 4.28 ("Deciphering a WMI security descriptor representation" at line 59) and Sample 4.29 ("Deciphering an ADSI security descriptor representation" at line 28). Note that both the WMI and ADSI deciphering functions call the DecipherSDControlFlags() function if the command-line parameter /Decipher+ is specified. Independent of the object model representing the security descriptor, it makes sense to have the same meaning for the values in the properties.
The Control Flags property determines two behaviors of the security descriptor in regard to the inherited ACE:
-
How the security descriptor behaves in regard to the ACE inherited from a parent object (i.e., Parent folder in the file system or Container in Active Directory). The SE_DACL_PROTECTED and SE_ SACL_PROTECTED flags determine this first behavior.
-
How the ACE defined in the security descriptor is inherited by the child objects (i.e., Subfolder in the file system or a child object in Active Directory). The SE_DACL_AUTO_INHERIT_REQ and the SE_SACL_AUTO_INHERIT_REQ flags determine this second behavior.
Since these flags are quite important for a security descriptor management, it could be useful to manage the SE_DACL_PROTECTED, SE_ SACL_PROTECTED, the SE_DACL_AUTO_INHERIT_REQ, and the SE_SACL_AUTO_INHERIT_REQ flags. In order to configure these flags from the command line, it is necessary to calculate the new Control Flags value from the labels given on the command line. Sample 4.31 makes this calculation. Other Control Flags bits, listed in Table 4.8, are set by the script itself when necessary and are not configurable from the command line. This is why the array defined between lines 20 and 23 only contains the four flags just mentioned.
Sample 4.31: Calculate the security descriptor controls value
.: .: .: 8:' ---------------------------------------------------------------------------------------- 9:Function CalculateSDControlFlags (arraySDControlFlags) ..: 20: arraySDControlFlagsData = Array ("SE_DACL_PROTECTED", SE_DACL_PROTECTED, _ 21: "SE_SACL_PROTECTED", SE_SACL_PROTECTED, _ 22: "SE_DACL_AUTO_INHERIT_REQ", SE_DACL_AUTO_INHERIT_REQ, _ 23: "SE_SACL_AUTO_INHERIT_REQ", SE_SACL_AUTO_INHERIT_REQ) 24: 25: For Each strSDControlFlags in arraySDControlFlags 26: boolFlagFound = False 27: For intIndice = 0 To UBound (arraySDControlFlagsData) Step 2 28: If Ucase (strSDControlFlags) = Ucase (arraySDControlFlagsData(intIndice)) Then 29: intSDControlFlags = intSDControlFlags + arraySDControlFlagsData(intIndice + 1) 30: boolFlagFound = True 31: Exit For 32: End If 33: Next 34: If boolFlagFound = False Then 35: WScript.Echo "Invalid SD control flags '" & strSDControlFlags & "'." 36: WScript.Quit (1) 37: End If 38: Next 39: 40: CalculateSDControlFlags = intSDControlFlags 41: 42:End Function The flag labels given on the command line are passed in the form of an array as a parameter of the CalculateSDControlFlags() function (line 9). Next, another array is created (lines 20 through 23), which contains the flags accepted on the command line. To validate the flags given on the command line and calculate the final value, two loops are enclosed together (lines 25 through 38 and 27 through 33). If there is a match between the flag label given on the command line and the authorized list (line 28), its corresponding value is calculated (line 29). In case of invalid flag syntax, the loop detects that no match occurred and the script execution terminates (lines 34 through 37). For all flag labels given on the command line, the routine will follow the exact same logic. This logic is not related to the security descriptor Control Flags property. This algorithm is also used with the /ACEType and the /ACEMask switches in the CalculateACEType() CalculateACEMask() functions, respectively.
The CalculateSDControlFlags() function is only used when the Control Flags property is updated in the security descriptor. We will see later in section 4.12.3 ("Updating the security descriptor Control Flags") how this new value is updated in the security descriptor and how it is saved back to the secured entity.
Note that some security descriptors do not support ACE inheritance. This is, for instance, the case for every security descriptor of the Windows NT platform and for the file system share security descriptor (any platform). However, an ACE of a security descriptor from a parent CIM repository namespace is always inherited. This setting is not modifiable from the user interface.
4.11.3 Deciphering the Access Control Lists
Based on the security descriptor object model, the ACL is represented differently. A WMI security descriptor representation has a very basic representation of an ACL, since it is implemented in the form of an array exposed by the DACL and the SACL properties. Each array element contains a Win32_ACE instance. If an ACE must be added or removed from an ACL, the array must be manipulated accordingly. There is no WMI class explicitly representing an ACL.
An ADSI security descriptor representation is slightly different, since the DiscretionaryACL and SystemACL properties retrieve an AccessControlList object exposed by the IADsAccessControlList interface. This interface exposes ACEs as a collection. The interface also exposes methods to add and remove ACEs from the collection, which makes the ACE management in an ADSI ACL easier.
In both cases, there is no specific function to decipher an ACL. ACLs are retrieved in Sample 4.28 ("Deciphering a WMI security descriptor representation," lines 29 through 39) and Sample 4.29 ("Deciphering an ADSI security descriptor representation," lines 36 and 110).
For both object models, we will see the scripting technique to use to manage an ACE in an ACL in sections 4.12.4 ("Adding an ACE") and 4.12.5 ("Removing an ACE").
4.11.4 Deciphering the Access Control Entries
At the beginning of this chapter (see section 4.4.1, "The security descriptor WMI representation"), we saw that a security descriptor ACE is made up of six properties:
-
The ACE Trustee property
-
The ACE Type property
-
The ACE Flags property
-
The ACE AccessMask property
-
The ACE ObjectType property
-
The ACE InheritedObjectType property
However, the ADSI object model shows an additional property: the ACE FlagType property. The ACE FlagType property is used to determine the presence of a GUID number in the ACE ObjectType and ACE InheritedObjectType properties. This property is not a security descriptor component, but it is a property exposed by the ADSI security descriptor structural representation to signify the presence of a GUID number in ObjectType and/or InheritedObjectType ADSI properties.
As we can see, ACE properties are the same for any security descriptor regardless of its origin. On the other hand, property values and meanings may vary with the origin of the security descriptor (i.e., file system, registry, Active Directory). The best example is the ACE AccessMask property. The flags used to decipher an ACE AccessMask part of a file security descriptor will be totally different from an ACE AccessMask part of an Active Directory security descriptor. In this section, we will discover how to decipher all ACE properties in relation to their origins. Some property deciphering techniques are common to all security descriptors (i.e., ACE Trustee, ACE Type); other property deciphering techniques will be unique to the origin of the security descriptor.
4.11.4.1 Deciphering the ACE Trustee property
As with the Owner and Group properties, the ACE Trustee property in the WMI object model is represented by a Win32_Trustee instance in an SWBemObject object. Therefore, Sample 4.28 ("Deciphering a WMI security descriptor representation"), by its recursive logic, naturally detects that the Trustee property of the Win32_ACE instance contains a Win32_Trustee instance. No particular bitwise deciphering technique is necessary. The Win32_Trustee instance is deciphered inside the DecipherWMISecurityDescriptor() in Sample 4.28.
When the security descriptor is represented in the ADSI object model, things are easier. The Trustee property contains a literal string representing the trustee (i.e., Domain\User). Therefore, Sample 4.29 ("Deciphering an ADSI security descriptor representation") makes a simple display of the string without further processing.
4.11.4.2 Deciphering the ACE Type property
The aim of the ACE Type property is to determine:
-
If the ACE trustee part of the same ACE is granted for the rights specified in the ACE AccessMask.
-
If the ACE trustee part of the same ACE is denied for the rights specified in the ACE AccessMask.
-
If the ACE trustee part of the same ACE is audited for the rights specified in the ACE AccessMask.
Note that an ACE can only be used for one purpose at a time: granting, denying, or auditing. So, the ACE Type property does not use any bitwise operation for the deciphering, since only one of the three values can be assigned for one single ACE.
Sample 4.32 shows the DecipherACEType() function, which is called by Sample 4.28 ("Deciphering a WMI security descriptor representation") at line 96 and Sample 4.29 ("Deciphering an ADSI security descriptor representation") at line 71. This demonstrates that the object model does not influence the interpretation of the value.
Sample 4.32: Deciphering the ACE Type property
.: .: .: 8:' --------------------------------------------------------------------------------------------- 9:Function DecipherACEType (intSDType, intACEType) ..: 15: strTemp = "&h" & Hex (intACEType) 16: 17: Select Case intSDType 18: Case cFileViaWMI, cFileViaADSI, _ 19: cShareViaWMI, _ 20: cShareViaADSI, _ 21: cRegistryViaADSI, _ 22: cWMINameSpaceViaWMI 23: Select Case intACEType 24: Case ACCESS_ALLOWED_ACE_TYPE 25: strTemp = strTemp & "," & "ACCESS_ALLOWED_ACE_TYPE" 26: Case ACCESS_DENIED_ACE_TYPE 27: strTemp = strTemp & "," & "ACCESS_DENIED_ACE_TYPE" 28: Case SYSTEM_AUDIT_ACE_TYPE 29: strTemp = strTemp & "," & "SYSTEM_AUDIT_ACE_TYPE" 30: Case SYSTEM_ALARM_ACE_TYPE 31: strTemp = strTemp & "," & "SYSTEM_ALARM_ACE_TYPE" 32: Case Else 33: 34: End Select 35: 36: Case cActiveDirectoryViaWMI, cActiveDirectoryViaADSI, _ 37: cExchange2000MailboxViaWMI, cExchange2000MailboxViaADSI, _ 38: cExchange2000MailboxViaCDOEXM 39: Select Case intACEType 40: Case ADS_ACETYPE_ACCESS_ALLOWED 41: strTemp = strTemp & "," & "ADS_ACETYPE_ACCESS_ALLOWED" 42: Case ADS_ACETYPE_ACCESS_DENIED 43: strTemp = strTemp & "," & "ADS_ACETYPE_ACCESS_DENIED" 44: Case ADS_ACETYPE_SYSTEM_AUDIT 45: strTemp = strTemp & "," & "ADS_ACETYPE_SYSTEM_AUDIT" 46: Case ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 47: strTemp = strTemp & "," & "ADS_ACETYPE_ACCESS_ALLOWED_OBJECT" 48: Case ADS_ACETYPE_ACCESS_DENIED_OBJECT 49: strTemp = strTemp & "," & "ADS_ACETYPE_ACCESS_DENIED_OBJECT" 50: Case ADS_ACETYPE_SYSTEM_AUDIT_OBJECT 51: strTemp = strTemp & "," & "ADS_ACETYPE_SYSTEM_AUDIT_OBJECT" 52: Case Else 53: 54: End Select 55: 56: Case cRegistryViaWMI, cWMINameSpaceViaADSI 57: 58: Case Else 59: 60: End Select 61: 62: DecipherACEType = ConvertStringInArray (strTemp, ",") 63: 64:End Function 65: ..: ..: ..:
Sample 4.32 deciphers the ACE Type property according to the origin of the security descriptor. If the security descriptor does not originate from Active Directory, the code between lines 23 and 34 is executed. If the security descriptor is from Active Directory, the code between lines 39 and 54 is executed. As examples, for a non-Active Directory security descriptor, we will have an ACE Type (lines 18 through 34):
-
Granting Access with the ACCESS_ALLOWED_ACE_TYPE flag.
-
Denying Access with the ACCESS_DENIED_ACE_TYPE flag.
-
Auditing Access with the SYSTEM_AUDIT_ACE_TYPE flag.
For instance, lines 38 and 54 show the ACE Type of a folder security descriptor.
1: C:\>WMIManageSD.Wsf /FileSystem:C:\MyDirectory /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via ADSI from 'C:\MyDirectory'. ..: 16: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 17: ||+- ADSI ACE ------------------------------------------------------------------------------ 18: ||| AccessMask: .......................... &h1F01FF ..: 37: ||| AceType: ............................. &h0 38: ACCESS_ALLOWED_ACE_TYPE 39: ||| AceFlagType: ......................... &h0 40: ||| Trustee: ............................. BUILTIN\Administrators 41: ||+----------------------------------------------------------------------------------------- 42: ||+- ADSI ACE ------------------------------------------------------------------------------ 43: ||| AccessMask: .......................... &h1200A9 ..: 51: ||| AceFlags: ............................ &h2 ..: 53: ||| AceType: ............................. &h0 54: ACCESS_ALLOWED_ACE_TYPE 55: ||| AceFlagType: ......................... &h0 56: ||| Trustee: ............................. LISSWARENET\MyGroup 57: ||+----------------------------------------------------------------------------------------- 58: |+------------------------------------------------------------------------------------------ 59: +-------------------------------------------------------------------------------------------
If the security descriptor originates from Active Directory, we will have an ACE Type (lines 36 through 54):
-
Granting Access with the ADS_ACETYPE_ACCESS_ALLOWED flag.
-
Denying Access with the ADS_ACETYPE_ACCESS_ALLOWED flag.
-
Auditing Access with the ADS_ACETYPE_SYSTEM_AUDIT flag.
For instance, lines 34 and 47 show the ACE Type of an Active Directory security descriptor.
1: C:\>WMIManageSD.Wsf /ADObject:"CN=MyUser,CN=Users,DC=LissWare,DC=Net" /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from LDAP://CN=MyUser,CN=Users,... 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. LISSWARENET\Alain.Lissoir 10: | Revision: .............................. 1 11: | Control: ............................... &h8C14 ..: 17: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 18: ||+- ADSI ACE ------------------------------------------------------------------------------ 19: ||| AccessMask: .......................... &hF01BD ..: 31: ||| AceFlags: ............................ &h2 ..: 33: ||| AceType: ............................. &h0 34: ADS_ACETYPE_ACCESS_ALLOWED 35: ||| AceFlagType: ......................... &h0 36: ||| Trustee: ............................. BUILTIN\Administrators 37: ||+----------------------------------------------------------------------------------------- 38: ||+- ADSI ACE ------------------------------------------------------------------------------ 39: ||| AccessMask: .......................... &h20014 ..: 43: ||| AceFlags: ............................ &h3 ..: 46: ||| AceType: ............................. &h0 47: ADS_ACETYPE_ACCESS_ALLOWED 48: ||| AceFlagType: ......................... &h0 49: ||| Trustee: ............................. LISSWARENET\MyUser ..: ..: ..:
If the security descriptor originates from the Active Directory and the ACE refers to Active Directory Extended Rights, we will have an ACE Type (lines 36 through 54):
-
Granting Access with the ADS_ACETYPE_ACCESS_ALLOWED_ OBJECT flag.
-
Denying Access with the ADS_ACETYPE_ACCESS_ALLOWED_OBJECT flag.
-
Auditing Access with the ADS_ACETYPE_SYSTEM_AUDIT_OBJECT flag.
For instance, lines 126 and 141 show the ACE Type of an Active Directory security descriptor for an Extended Right. Note the presence of a GUID for the ACE ObjectType property at lines 130 and 145.
1: C:\>WMIManageSD.Wsf /ADObject:"CN=MyUser,CN=Users,DC=LissWare,DC=Net" /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP://CN=MyUser,CN=Users,... 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. LISSWARENET\Alain.Lissoir 10: | Revision: .............................. 1 11: | Control: ............................... &h8C14 ..: 17: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 18: ||+- ADSI ACE ------------------------------------------------------------------------------ ...: 119: ||+- ADSI ACE ------------------------------------------------------------------------------ 120: ||| AccessMask: .......................... &h10 ...: 122: ||| AceFlags: ............................ &h12 ...: 125: ||| AceType: ............................. &h5 126: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 127: ||| AceFlagType: ......................... &h3 ...: 130: ||| ObjectType: .......................... {037088F8-0AE1-11D2-B422-00A0C968F939} 131: ||| InheritedObjectType: ................. {BF967ABA-0DE6-11D0-A285-00AA003049E2} 132: ||| Trustee: ............................. BUILTIN\Pre-Windows 2000 Compatible Access 133: ||+----------------------------------------------------------------------------------------- 134: ||+- ADSI ACE ------------------------------------------------------------------------------ 135: ||| AccessMask: .......................... &h10 ...: 137: ||| AceFlags: ............................ &h12 ...: 140: ||| AceType: ............................. &h5 141: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 142: ||| AceFlagType: ......................... &h3 ...: 145: ||| ObjectType: .......................... {59BA2F42-79A2-11D0-9020-00C04FC2D3CF} 146: ||| InheritedObjectType: ................. {BF967ABA-0DE6-11D0-A285-00AA003049E2} 147: ||| Trustee: ............................. BUILTIN\Pre-Windows 2000 Compatible Access 148: ||+----------------------------------------------------------------------------------------- ...: ...: ...: We will see in section 4.11.4.5.3 ("The Active Directory object ACE AccessMask property") how to manipulate the Active Directory ACE AccessMask property with Extended Rights.
4.11.4.3 Deciphering the ACE Flags property
The ACE Flags property determines the inheritance of an ACE. Do not confuse this property with the Control Flags property, which works at the security descriptor level, while the ACE Flags property works at the ACE level. The ACE Flags property determines how child objects inherit an ACE (i.e., Subfolder in the file system or a child object in Active Directory).
The DecipherACEFlags() function is called by Sample 4.28 ("Deciphering a WMI security descriptor representation") at line 84 and Sample 4.29 ("Deciphering an ADSI security descriptor representation") at line 62, which demonstrates once more that the object model does not influence the interpretation of the value.
As opposed to the ACE Type deciphering technique, the ACE Flags property is deciphered with a bitwise operation, because several bits determine how the ACE must be inherited. Even if the logic to decipher is always the same for any security descriptor, the origin determines the ACE Flags values to use to decipher. Table 4.9 lists the inheritance flags to use when the security has an origin other than Active Directory (i.e., files or folders, registry)
| OBJECT_INHERIT_ACE | 0x1 | Noncontainer objects contained by the primary object inherit the entry. |
| CONTAINER_INHERIT_ACE | 0x2 | Other containers that are contained by the primary object inherit the entry. |
| NO_PROPAGATE_INHERIT_ACE | 0x4 | The OBJECT_INHERIT_ACE and CONTAINER_INHERIT_ACE flags are not propagated to an inherited entry. |
| INHERIT_ONLY_ACE | 0x8 | The ACE does not apply to the primary object to which the ACL is attached, but objects contained by the primary object inherit the entry. |
| INHERITED_ACE | 0x10 | Only under Windows 2000, Windows XP, and Windows Server 2003, it indicates that the ACE was inherited. The system sets this bit when it propagates an inherited ACE to a child object. |
| SUCCESSFUL_ACCESS_ACE_FLAG | 0x40 | Used with system-audit ACEs in a SACL to generate audit messages for successful access attempts. |
| FAILED_ACCESS_ACE_FLAG | 0x80 | Used with system-audit ACEs in a SACL to generate audit messages for failed access attembts. |
| VALID_INHERIT_FLAGS | 0x1F | Indicates whether the inherit flags are valid. The system sets this bit. |
Table 4.10 lists the flags controlling ACE inheritance when the security descriptor comes from the Active Directory (i.e., Active Directory user object).
| ADS_ACEFLAG_INHERIT_ACE | 0x2 | Child objects will inherit this access-control entry (ACE). The inherited ACE is inheritable unless the ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE flag is set. |
| ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE | 0x4 | The system will clear the ADS_ACEFLAG_INHERIT_ACE flag for the inherited ACEs of child objects. This prevents the ACE from being inherited by subsequent generations of objects. |
| ADS_ACEFLAG_INHERIT_ONLY_ACE | 0x8 | Indicates an inherit-only ACE that does not exercise access control on the object to which it is attached. If this flag is not set, the ACE is an effective ACE that exerts access control on the object to which it is attached. |
| ADS_ACEFLAG_INHERITED_ACE | 0x10 | Indicates whether or not the ACE was inherited. The system sets this bit. |
| ADS_ACEFLAG_VALID_INHERIT_FLAGS | 0x1F | Indicates whether the inherit flags are valid. The system sets this bit. |
| ADS_ACEFLAG_SUCCESSFUL_ACCESS | 0x40 | Generates audit messages for successful access attempts, used with ACEs that audit the system in a system access-control list (SACL). |
| ADS_ACEFLAG_FAILED_ACCESS | 0x80 | Generates audit messages for failed access attempts, used with ACEs that audit the system in a SACL. |
Moreover, the ACE inheritance capabilities rely on the security descriptor origin. For instance, a File System share security descriptor doesn't implement the concept of inheritance, while an Active Directory security descriptor does. When we decipher the ACE AccessMask property, we will see how to set up the ACE inheritance, since it determines how ACE AccessMask is applied.
The DecipherACEFlags() function deciphering the ACE Flags is illustrated in Sample 4.33.
Sample 4.33: Deciphering the ACE Flags property
..: ..: ..: 65: 66:' --------------------------------------------------------------------------------------------- 67:Function DecipherACEFlags (intSDType, intACEFlags) ..: 73: strTemp = "&h" & Hex (intACEFlags) 74: 75: Select Case intSDType 76: Case cFileViaWMI, cFileViaADSI, _ 77: cShareViaWMI, _ 78: cShareViaADSI, _ 79: cRegistryViaADSI, _ 80: cWMINameSpaceViaWMI 81: If (intACEFlags And OBJECT_INHERIT_ACE) Then 82: strTemp = strTemp & "," & "OBJECT_INHERIT_ACE" 83: End If 84: If (intACEFlags And CONTAINER_INHERIT_ACE) Then 85: strTemp = strTemp & "," & "CONTAINER_INHERIT_ACE" 86: End If 87: If (intACEFlags And NO_PROPAGATE_INHERIT_ACE) Then 88: strTemp = strTemp & "," & "NO_PROPAGATE_INHERIT_ACE" 89: End If ..: 99: If (intACEFlags And SUCCESSFUL_ACCESS_ACE_FLAG) Then 100: strTemp = strTemp & "," & "SUCCESSFUL_ACCESS_ACE_FLAG" 101: End If 102: If (intACEFlags And FAILED_ACCESS_ACE_FLAG) Then 103: strTemp = strTemp & "," & "FAILED_ACCESS_ACE_FLAG" 104: End If 105: 106: Case cActiveDirectoryViaWMI, cActiveDirectoryViaADSI, _ 107: cExchange2000MailboxViaWMI, cExchange2000MailboxViaADSI, _ 108: cExchange2000MailboxViaCDOEXM 109: If (intACEFlags And ADS_ACEFLAG_OBJECT_INHERIT_ACE) Then 110: strTemp = strTemp & "," & "ADS_ACEFLAG_OBJECT_INHERIT_ACE" 111: End If 112: If (intACEFlags And ADS_ACEFLAG_CONTAINER_INHERIT_ACE) Then 113: strTemp = strTemp & "," & "ADS_ACEFLAG_CONTAINER_INHERIT_ACE" 114: End If 115: If (intACEFlags And ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE) Then 116: strTemp = strTemp & "," & "ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE" 117: End If ...: 127: If (intACEFlags And ADS_ACEFLAG_SUCCESSFUL_ACCESS) Then 128: strTemp = strTemp & "," & "ADS_ACEFLAG_SUCCESSFUL_ACCESS" 129: End If 130: If (intACEFlags And ADS_ACEFLAG_FAILED_ACCESS) Then 131: strTemp = strTemp & "," & "ADS_ACEFLAG_FAILED_ACCESS" 132: End If 133: 134: Case cRegistryViaWMI, cWMINameSpaceViaADSI 135: 136: Case Else 137: 138: End Select 139: 140: DecipherACEFlags = ConvertStringInArray (strTemp, ",") 141: 142:End Function 143: ...: ...: ...:
The following output shows the ACE Flags values from lines 34 through 36 and at lines 51 and 52.
1: C:\>WMIManageSD.Wsf /FileSystem:C:\MyDirectory /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via ADSI from 'C:\MyDirectory'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. LISSWARENET\Domain Users 10: | Revision: .............................. 1 11: | Control: ............................... &h9404 ..: 16: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 17: ||+- ADSI ACE ------------------------------------------------------------------------------ 18: ||| AccessMask: .......................... &h1F01FF ..: 34: ||| AceFlags: ............................ &h3 35: OBJECT_INHERIT_ACE 36: CONTAINER_INHERIT_ACE 37: ||| AceType: ............................. &h0 ..: 39: ||| AceFlagType: ......................... &h0 40: ||| Trustee: ............................. BUILTIN\Administrators 41: ||+----------------------------------------------------------------------------------------- 42: ||+- ADSI ACE ------------------------------------------------------------------------------ 43: ||| AccessMask: .......................... &h1200A9 ..: 51: ||| AceFlags: ............................ &h2 52: CONTAINER_INHERIT_ACE 53: ||| AceType: ............................. &h0 ..: 55: ||| AceFlagType: ......................... &h0 56: ||| Trustee: ............................. LISSWARENET\MyGroup 57: ||+----------------------------------------------------------------------------------------- 58: |+------------------------------------------------------------------------------------------ 59: +-------------------------------------------------------------------------------------------
4.11.4.4 Deciphering the ACE Flag Type property
The ACE FlagType is only used when the ACE ObjectType or ACE InheritedObjectType properties contain a GUID number. Only Sample 4.29 ("Deciphering an ADSI security descriptor representation") at line 80 calls the DecipherACEFlagType() function. The security descriptor WMI representation supports the display of a GUID number but does not use an ACE FlagType property. This property is a peculiarity of the ADSI object model representation. We will see in section 4.11.4.5.3 ("The Active Directory object ACE AccessMask property") how to interpret the GUID number. Except for these peculiarities, the ACE FlagType coding and deciphering technique are always the same (see Sample 4.34).
Sample 4.34: Deciphering the ACE FlagType property
...: ...: ...: 143: 144:' --------------------------------------------------------------------------------------------- 145:Function DecipherACEFlagType (intSDType, intACEFlagType) ...: 151: strTemp = "&h" & Hex (intACEFlagType) 152: 153: Select Case intSDType 154: Case cFileViaWMI, cFileViaADSI, _ 155: cShareViaWMI, _ 156: cShareViaADSI, _ 157: cActiveDirectoryViaWMI, cActiveDirectoryViaADSI, _ 158: cExchange2000MailboxViaWMI, cExchange2000MailboxViaADSI, _ 159: cExchange2000MailboxViaCDOEXM, _ 160: cRegistryViaADSI, _ 161: cWMINameSpaceViaWMI 162: If (intACEFlagType And ADS_FLAG_OBJECT_TYPE_PRESENT) Then 163: strTemp = strTemp & "," & "ADS_FLAG_OBJECT_TYPE_PRESENT" 164: End If 165: If (intACEFlagType And ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT) Then 166: strTemp = strTemp & "," & "ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT" 167: End If 168: 169: Case cRegistryViaWMI, cWMINameSpaceViaADSI 170: 171: Case Else 172: 173: End Select 174: 175: DecipherACEFlagType = ConvertStringInArray (strTemp, ",") 176: 177:End Function 178: ...: ...: ...:
The following output sample shows the ACE FlagType values from line 157 through 159 and 172 through 174.
1: C:\>WMIManageSD.Wsf /ADObject:"CN=MyUser,CN=Users,DC=LissWare,DC=Net" /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP://CN=MyUser,CN=Users,... 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. LISSWARENET\Alain.Lissoir 10: | Revision: .............................. 1 11: | Control: ............................... &h8C14 ..: 17: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 149: ||+- ADSI ACE ------------------------------------------------------------------------------ 150: ||| AccessMask: .......................... &h10 ...: 152: ||| AceFlags: ............................ &h12 ...: 155: ||| AceType: ............................. &h5 ...: 157: ||| AceFlagType: ......................... &h3 158: ADS_FLAG_OBJECT_TYPE_PRESENT 159: ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT 160: ||| ObjectType: .......................... {BC0AC240-79A9-11D0-9020-00C04FC2D4CF} 161: ||| InheritedObjectType: ................. {BF967ABA-0DE6-11D0-A285-00AA003049E2} 162: ||| Trustee: ............................. BUILTIN\Pre-Windows 2000 Compatible Access 163: ||+----------------------------------------------------------------------------------------- 164: ||+- ADSI ACE ------------------------------------------------------------------------------ 165: ||| AccessMask: .......................... &h10 ...: 167: ||| AceFlags: ............................ &h12 ...: 170: ||| AceType: ............................. &h5 ...: 172: ||| AceFlagType: ......................... &h3 173: ADS_FLAG_OBJECT_TYPE_PRESENT 174: ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT 175: ||| ObjectType: .......................... {4C164200-20C0-11D0-A768-00AA006E0529} 176: ||| InheritedObjectType: ................. {BF967ABA-0DE6-11D0-A285-00AA003049E2} 177: ||| Trustee: ............................. BUILTIN\Pre-Windows 2000 Compatible Access 178: ||+----------------------------------------------------------------------------------------- ...: ...: ...:
4.11.4.5 Deciphering the ACE AccessMask property
To decipher security descriptors, the script makes use of the DecipherACEMask() function. The DecipherACEMask() is divided into several samples due to the fact that there is always a specific set of flags to use for each security descriptor origin. The DecipherACEMask() function is illustrated in Samples 4.35 through 4.40 in the following sections.
This DecipherACEMask() function is called by Sample 4.28 ("Deciphering a WMI security descriptor representation") at line 72 and Sample 4.29 ("Deciphering an ADSI security descriptor representation") at line 53.
4.11.4.5.1 The files and folders ACE AccessMask property
To decipher a file or a folder ACE AccessMask, it is necessary to use the flag values listed in Table 4.11.
| Granted & denied rights | Standard View | Advanced View | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Full Control | Modify | Read & Execute | List Folder Contents | Read | Write | Traverse Folder / Execute File | List Folder / Execute Data | Read Attributes | Read Extended Attributes | Create Files / Write Data | Create Folders / Append Data | Write Attributes | Write Extended Attributes | Delete Subfolders and Files | Delete | Read Permissions | Change Permissions | Take Ownership | ||
| ACEType | ||||||||||||||||||||
| ACCESS_ALLOWED_ACE_TYPE (Allowed access ACE) | 0x0 | X [1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] |
| ACCESS_DENIED_ACE_TYPE (Denied access ACE) | 0x1 | |||||||||||||||||||
| SYSTEM_AUDIT_ACE_TYPE (System Audit ACE) | 0x2 | |||||||||||||||||||
| ACEMask | ||||||||||||||||||||
| FILE_GENERIC_EXECUTE | 0X1200A9 | X | ||||||||||||||||||
| FILE_GENERIC_READ | 0x120089 | X | ||||||||||||||||||
| FILE_GENERIC_WRITE | 0x100116 | X | ||||||||||||||||||
| FILE_ALL_ACCESS | 0x1F01FFOxlFOlFF | X | ||||||||||||||||||
| FILE_APPEND_DATA (FOLDER_ADD_SUBDIRECTORY) | 0x000004 | X | X | X | X | |||||||||||||||
| FILE_DELETE | 0x010000 | X | X | X | ||||||||||||||||
| FILE_DELETE_CHILD | 0x000040 | X | X | |||||||||||||||||
| FILE_EXECUTE (FOLDER_TRAVERSE) | 0x000020 | X | X | X | X | X | ||||||||||||||
| FILE_READ_ATTRIBUTES | 0x000080 | X | X | X | X | X | X | |||||||||||||
| FILE_READ_CONTROL | 0x020000 | X | X | X | X | X | X | |||||||||||||
| FILE_READ_DATA (FOLDER_LIST_DIRECTORY) | 0x000001 | X | X | X | X | X | X | |||||||||||||
| FILE_READ_EA | 0x000008 | X | X | X | X | X | X | |||||||||||||
| FILE_SYNCHRONIZE | 0x100000 | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X |
| FILE_WRITE_ATTRIBUTES | 0x000100 | X | X | X | X | |||||||||||||||
| FILE_WRITE_DAC | 0x040000 | X | X | |||||||||||||||||
| FILE_WRITE_DATA (FOLDER_ADD_FILE) | 0x000002 | X | X | X | X | |||||||||||||||
| FILE_WRITE_EA | 0x000010 | X | X | X | X | |||||||||||||||
| FILE_WRITE_OWNER | 0x080000 | X | X | |||||||||||||||||
|
[1]Windows NT 4.0/Windows 2000: The ADsSecurfty.DLL from the ADSI Resource Kit does not retrieve the SACLobject from the registry. Windows XP/Windows Server 2003: Unfortunately, a bug in the ADsSecurityUtility interface prevents the retrieval of the SystemACL Microsoft doesn't plan to fix this bug in the RTM code for timing issues. WMI offers an acceptable work-around for file and folders only. For the registry key, there is no work-around available unless you use the UserRight.Control developed to work around this problem. (See section 4.7.1.2, "Retrieving file and folder security descriptors with ADSL") | ||||||||||||||||||||
The column headings in this table represent the settings in the user interface. The left column lists the flags that must be used to decipher or set an ACE AccessMask value for a file or a folder, while the top row shows the user interface selection.
In Figure 4.19, the user interface shows a folder security descriptor. We see that the "Read & Execute" right is granted to "Everyone." In Table 4.11, in the column "Read & Execute," we see that each time there is a cross in the cell the corresponding flag is set. In such a case, we have the following flags:
-
FOLDER_LIST_DIRECTORY
-
FILE_READ_EA
-
FOLDER_TRAVERSE
-
FILE_READ_ATTRIBUTES
-
FILE_READ_CONTROL
-
FILE_SYNCHRONIZE
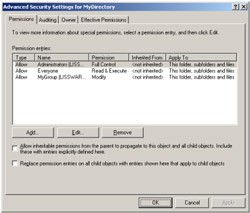
Figure 4.19: The files and folders security descriptor user interface.
To ease flag use, some flags are generic. They are made from a combination of several flags. So, instead of using all previously listed flags, the "Read & Execute" right can be summarized by the use of the FILE_GENERIC_EXECUTE flag. For the files and folders, there are three generic flags listed in Table 4.11 (FILE_GENERIC_EXECUTE, FILE_GENERIC_READ, and FILE_GENERIC_WRITE).
To decipher the ACE AccessMask property, the logic is always the same. Sample 4.35 shows the bitwise operations executed with the flags listed in Table 4.11. Again, we see that the deciphering technique applies for an ACE AccessMask coming from a WMI security descriptor or an ADSI security descriptor representation.
Sample 4.35: Deciphering the ACE AccessMask property for files and folders
...: ...: ...: 178: 179:' --------------------------------------------------------------------------------------------- 180:Function DecipherACEMask (intSDType, intACEMask) ...: 186: strTemp = "&h" & Hex (intACEMask) 187: 188: Select Case intSDType 189: Case cFileViaWMI, cFileViaADSI 190: If (intACEMask = FILE_ALL_ACCESS) Then 191: strTemp = strTemp & "," & "(FILE_ALL_ACCESS)" 192: End If 193: If (intACEMask = FILE_GENERIC_EXECUTE) Then 194: strTemp = strTemp & "," & "(FILE_GENERIC_EXECUTE)" 195: End If 196: If (intACEMask = FILE_GENERIC_READ) Then 197: strTemp = strTemp & "," & "(FILE_GENERIC_READ)" 198: End If 199: If (intACEMask = FILE_GENERIC_WRITE) Then 200: strTemp = strTemp & "," & "(FILE_GENERIC_WRITE)" 201: End If 202: If (intACEMask And FILE_READ_DATA) Then 203: strTemp = strTemp & "," & "FILE_READ_DATA " & _ 204: "(FOLDER_LIST_DIRECTORY for a Folder)" 205: End If 206: If (intACEMask And FILE_WRITE_DATA) Then 207: strTemp = strTemp & "," & "FILE_WRITE_DATA " & _ 208: "(FOLDER_ADD_FILE for a Folder)" 209: End If 210: If (intACEMask And FILE_APPEND_DATA) Then 211: strTemp = strTemp & "," & "FILE_APPEND_DATA " & _ 212: "(FOLDER_ADD_SUBDIRECTORY for a Folder)" 213: End If ...: 245: If (intACEMask And FILE_SYNCHRONIZE) Then 246: strTemp = strTemp & "," & "FILE_SYNCHRONIZE" 247: End If 248: ...: ...: ...:
To distinguish the security descriptor origin, the DecipherACEMask() function uses a Select Case statement, where each case corresponds to a deciphering of an ACE AccessMask value from a specific security descriptor origin.
The execution of the following command line will completely decipher the security descriptor shown in Figure 4.19.
1: C:\>WMIManageSD.wsf /FileSystem:C:\MyDirectory /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading File or Folder security descriptor via WMI from 'C:\MyDirectory'. 6: 7: +- Win32_SecurityDescriptor ---------------------------------------------------------------- 8: | ControlFlags: .......................... &hBC14 9: SE_DACL_PRESENT 10: SE_SACL_PRESENT 11: SE_DACL_AUTO_INHERITED 12: SE_SACL_AUTO_INHERITED 13: SE_DACL_PROTECTED 14: SE_SACL_PROTECTED 15: SE_SELF_RELATIVE 16: | DACL: .................................. (Win32_ACE) 17: | +- Win32_ACE ----------------------------------------------------------------------------- 18: | | AccessMask: .......................... &h1F01FF 19: (FILE_ALL_ACCESS) 20: FOLDER_LIST_DIRECTORY 21: FOLDER_ADD_FILE 22: FOLDER_ADD_SUBDIRECTORY 23: FILE_READ_EA 24: FILE_WRITE_EA 25: FOLDER_TRAVERSE 26: FILE_DELETE_CHILD 27: FILE_READ_ATTRIBUTES 28: FILE_WRITE_ATTRIBUTES 29: FILE_DELETE 30: FILE_READ_CONTROL 31: FILE_WRITE_DAC 32: FILE_WRITE_OWNER 33: FILE_SYNCHRONIZE 34: | | AceFlags: ............................ &h3 35: OBJECT_INHERIT_ACE 36: CONTAINER_INHERIT_ACE 37: | | AceType: ............................. &h0 38: ACCESS_ALLOWED_ACE_TYPE 39: | | Trustee: ............................. (Win32_Trustee) 40: | | +- Win32_Trustee ----------------------------------------------------------------------- 41: | | | Domain: ............................ BUILTIN 42: | | | Name: .............................. Administrators 43: | | | SID: ............................... 1,2,0,0,0,0,0,5,32,0,0,0,32,2,0,0 44: | | | SidLength: ......................... 16 45: | | | SIDString: ......................... S-1-5-32-544 46: | | +--------------------------------------------------------------------------------------- 47: | +----------------------------------------------------------------------------------------- 48: | +- Win32_ACE ----------------------------------------------------------------------------- 49: | | AccessMask: .......................... &h1200A9 50: (FILE_GENERIC_EXECUTE) 51: FOLDER_LIST_DIRECTORY 52: FILE_READ_EA 53: FOLDER_TRAVERSE 54: FILE_READ_ATTRIBUTES 55: FILE_READ_CONTROL 56: FILE_SYNCHRONIZE 57: | | AceFlags: ............................ &h3 58: OBJECT_INHERIT_ACE 59: CONTAINER_INHERIT_ACE 60: | | AceType: ............................. &h0 61: ACCESS_ALLOWED_ACE_TYPE 62: | | Trustee: ............................. (Win32_Trustee) 63: | | +- Win32_Trustee ----------------------------------------------------------------------- 64: | | | Name: .............................. Everyone 65: | | | SID: ............................... 1,1,0,0,0,0,0,1,0,0,0,0 66: | | | SidLength: ......................... 12 67: | | | SIDString: ......................... S-1-1-0 68: | | +--------------------------------------------------------------------------------------- 69: | +----------------------------------------------------------------------------------------- 70: | +- Win32_ACE ----------------------------------------------------------------------------- 71: | | AccessMask: .......................... &h1301BF 72: FOLDER_LIST_DIRECTORY 73: FOLDER_ADD_FILE 74: FOLDER_ADD_SUBDIRECTORY 75: FILE_READ_EA 76: FILE_WRITE_EA 77: FOLDER_TRAVERSE 78: FILE_READ_ATTRIBUTES 79: FILE_WRITE_ATTRIBUTES 80: FILE_DELETE 81: FILE_READ_CONTROL 82: FILE_SYNCHRONIZE 83: | | AceFlags: ............................ &h3 84: OBJECT_INHERIT_ACE 85: CONTAINER_INHERIT_ACE 86: | | AceType: ............................. &h0 87: ACCESS_ALLOWED_ACE_TYPE 88: | | Trustee: ............................. (Win32_Trustee) 89: | | +- Win32_Trustee ----------------------------------------------------------------------- 90: | | | Domain: ............................ LISSWARENET 91: | | | Name: .............................. MyGroup 92: | | | SID: ............................... 1,5,0,0,0,...,207,122,236,255,136,223,4,0,0 93: | | | SidLength: ......................... 28 94: | | | SIDString: ......................... S-1-5-21-3533506287-3489020660-2298473594-1247 95: | | +--------------------------------------------------------------------------------------- 96: | +----------------------------------------------------------------------------------------- 97: | Owner: ................................. (Win32_Trustee) 98: | +- Win32_Trustee ------------------------------------------------------------------------- 99: | | Domain: .............................. BUILTIN 100: | | Name: ................................ Administrators 101: | | SID: ................................. 1,2,0,0,0,0,0,5,32,0,0,0,32,2,0,0 102: | | SidLength: ........................... 16 103: | | SIDString: ........................... S-1-5-32-544 104: | +----------------------------------------------------------------------------------------- 105: +-------------------------------------------------------------------------------------------
As we have seen, the ACE AccessMask inheritance is defined by the ACE Flags property. Although the deciphering technique is the same for any security descriptor (see Sample 4.33, "Deciphering the ACE Flags property"), the flag values used and their combinations to decipher or set the ACE Flags property are dependent on the security descriptor origin, since the origin determines the inheritance capabilities.
Table 4.12 summarizes the flag values in regard to the inheritance settings that can be set from the user interface shown in Figure 4.20. The previous security descriptor deciphering output of Figure 4.19 shows the ACE Flags settings for the configured inheritance.
| Inheritance &Audit | (Folders only) | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| This folder only | This folder, subfolder, and files | This folder and subfolders | This folder and files | Subfolders and files only | Subfolders only | Files only | Audit Successful access | Audit Failed access | ||
| ACEFIags | ||||||||||
| NONE | 0x0 | X | ||||||||
| CONTAINER_INHERIT_ACE | 0x2 | X | X | X | X | |||||
| INHERIT_ONLY_ACE | 0x8 | X | X | X | ||||||
| INHERITED_ACE [1] | 0x10 | |||||||||
| NO_PROPAGATE_INHERIT_ACE | 0x4 | |||||||||
| OBJECT_INHERIT_ACE | 0x1 | X | X | X | X | |||||
| VALID_INHERIT_FLAG[1] | 0x1F | |||||||||
| SUCCESSFUL_ACCESS_ACE_FLAG | 0x40 | X | ||||||||
| FAILED_ACCESS_ACE_FLAG | 0x80 | |||||||||
|
[1]Set by the system. | ||||||||||
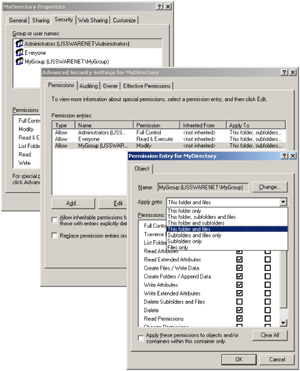
Figure 4.20: The files and folders inheritance user interface.
To set up a security descriptor in a folder similar to the one shown in Figure 4.19, the script must be executed several times, since it sets only one ACE at a time. Of course, Tables 4.11 ("The files and folders ACE AccessMask values") and 4.12 ("The files and folders ACE Flags values") can be used to determine these settings. In such a case, the following command lines will set up the settings in Figure 4.19:
1: WMIManageSD.wsf /FileSystem:C:\MyDirectory /Trustee:REMOVE_ALL_ACE /DelAce+ 2: 3: WMIManageSD.wsf /FileSystem:C:\MyDirectory /Trustee:BUILTIN\Administrators 4: /ACEType:ACCESS_ALLOWED_ACE_TYPE 5: /ACEMask:FILE_ALL_ACCESS 6: /ACEFlags:OBJECT_INHERIT_ACE,CONTAINER_INHERIT_ACE 7: /AddAce+ 8: 9: WMIManageSD.wsf /FileSystem:C:\MyDirectory /Trustee:Everyone /DelAce+ 10: 11: WMIManageSD.wsf /FileSystem:C:\MyDirectory /Trustee:LissWareNET\Everyone 12: /ACEType:ACCESS_ALLOWED_ACE_TYPE 13: /ACEMask:FILE_GENERIC_EXECUTE 14: /ACEFlags:OBJECT_INHERIT_ACE,CONTAINER_INHERIT_ACE 15: /AddAce+ 16: 17: WMIManageSD.wsf /FileSystem:C:\MyDirectory /Trustee:LissWareNET\MyGroup 18: /ACEType:ACCESS_ALLOWED_ACE_TYPE 19: /ACEMask:FOLDER_LIST_DIRECTORY, 20: FOLDER_ADD_FILE,FOLDER_ADD_SUBDIRECTORY,FILE_READ_EA,FILE_WRITE_EA, 21: FOLDER_TRAVERSE,FILE_READ_ATTRIBUTES,FILE_WRITE_ATTRIBUTES, 22: FILE_DELETE,FILE_READ_CONTROL,FILE_SYNCHRONIZE 23: /ACEFlags:OBJECT_INHERIT_ACE,CONTAINER_INHERIT_ACE /AddAce+
Please take a few minutes to compare the command-line settings with the previous output and the content of Tables 4.11 and 4.12.
At line 1, the script removes all available ACEs. We will see in section 4.12.5 ("Removing an ACE") that the end result of this operation sets a full access right to "Everyone" on the secured object. Although it is possible to remove all ACEs one by one to obtain the desired configuration, this makes the work more complicated, because it forces us to know which ACE has to be removed. By removing all ACE entries at once, we start the security descriptor configuration from a clear and known situation. From line 3 through 7, the script configures the "Administrators" group with a full access right. If the user configuring the security descriptor is part of the "Administrators" group (which is supposed to be in this example), then the "Everyone" group can be removed (line 9). Of course, as shown in Figure 4.19, the "Everyone" group has a "Read & Execute" access. This configuration is set up from line 11 through 15. Although it is technically possible to edit the ACE properties of the deleted ACE at line 9, this requires more granularity in terms of management capabilities to change existing ACE-specific properties. For the sake of simplicity, the script manages the ACE security descriptor at the ACE level for an existing ACE, not at the ACE property level. Finally, from line 17 through 23, the script grants the "Modify" right to the "MyGroup" group. Once completed, we obtain the security settings shown in Figure 4.19. We will see in section 4.13 ("Updating the security descriptor") how the security descriptor is saved back to the secured entity (which is a folder in this example).
The script accesses the security descriptor via WMI and therefore uses the WMI Security provider and its related class methods implementing the security descriptor access. In the case of a file or a folder, it is possible to use ADSI as the access method. Therefore, the switch /ADSI+ must be specified. Keep in mind the restrictions that apply to the SACL access when using ADSI (see Table 4.4).
Now, if you compare the results obtained when deciphering the Figure 4.19 configuration with the command-line switches used previously, you will see that the exact same settings are used. Basically, each time you need to configure a security descriptor, it is a good idea to configure the desired result via the user interface first. Next, run the script to decipher the desired result and reuse this output to customize the command-line switches to automate the security configuration settings. We will see other examples with other security descriptors later. The logic is always the same. Only some flags related to a specific security descriptor must be adapted (file, share, Active Directory objects, etc.).
4.11.4.5.2 The File System share ACE AccessMask property
To decipher a File System share ACE AccessMask, it is necessary to use the flag values listed in Table 4.13.
| Granted & denied rights | Standard View | |||
|---|---|---|---|---|
| Full Control | Change | Read | ||
| ACEType | ||||
| ACCESS_ALLOWED_ACE_TYPE | 0x0 | X | X | X |
| ACCESS_DENIED_ACE_TYPE | 0x1 | |||
| ACEMask | ||||
| FILE_SHARE_FULL_ACCESS | 0x0C0040 | X | ||
| FILE_SHARE_CHANGE_ACCESS | 0x010116 | X | X | |
| FILE_SHARE_READ_ACCESS | 0x1200A9 | X | X | X |
Deciphering the File System share ACE AccessMask is quite easy, since there are only three flags used. Sample 4.36 is the continuation of Sample 4.35 ("Deciphering the ACE AccessMask property for files and folders") and shows how to decipher a File System share ACE AccessMask with the values listed in Table 4.13.
Sample 4.36: Deciphering the ACE AccessMask property for File System shares
...: ...: ...: 248: 249: Case cShareViaWMI, cShareViaADSI 250: If (intACEMask And FILE_SHARE_FULL_ACCESS) Then 251: strTemp = strTemp & "," & "FILE_SHARE_FULL_ACCESS" 252: End If 253: If (intACEMask And FILE_SHARE_CHANGE_ACCESS) Then 254: strTemp = strTemp & "," & "FILE_SHARE_CHANGE_ACCESS" 255: End If 256: If (intACEMask And FILE_SHARE_READ_ACCESS) Then 257: strTemp = strTemp & "," & "FILE_SHARE_READ_ACCESS" 258: End If 259: ...: ...: ...:
Based on that code, an execution of the script from the command line produces the following output if a File System share security is configured, as shown in Figure 4.21.
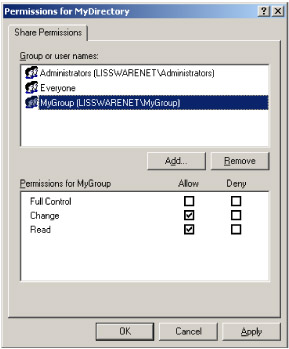
Figure 4.21: The File System share security descriptor user interface
1: C:\>WMIManageSD.wsf /Share:MyDirectory /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading Share security descriptor via WMI from 'MyDirectory'. 6: 7: +- Win32_SecurityDescriptor ---------------------------------------------------------------- 8: | ControlFlags: .......................... &h8004 9: SE_DACL_PRESENT 10: SE_SELF_RELATIVE 11: | DACL: .................................. (Win32_ACE) 12: | +- Win32_ACE ----------------------------------------------------------------------------- 13: | | AccessMask: .......................... &h1F01FF 14: FILE_SHARE_FULL_ACCESS 15: FILE_SHARE_CHANGE_ACCESS 16: FILE_SHARE_READ_ACCESS 17: | | AceFlags: ............................ &h0 18: | | AceType: ............................. &h0 19: ACCESS_ALLOWED_ACE_TYPE 20: | | Trustee: ............................. (Win32_Trustee) 21: | | +- Win32_Trustee ----------------------------------------------------------------------- 22: | | | Domain: ............................ BUILTIN 23: | | | Name: .............................. Administrators 24: | | | SID: ............................... 1,2,0,0,0,0,0,5,32,0,0,0,32,2,0,0 25: | | | SidLength: ......................... 16 26: | | | SIDString: ......................... S-1-5-32-544 27: | | +--------------------------------------------------------------------------------------- 28: | +----------------------------------------------------------------------------------------- 29: | +- Win32_ACE ----------------------------------------------------------------------------- 30: | | AccessMask: .......................... &h1200A9 31: FILE_SHARE_READ_ACCESS 32: | | AceFlags: ............................ &h0 33: | | AceType: ............................. &h0 34: ACCESS_ALLOWED_ACE_TYPE 35: | | Trustee: ............................. (Win32_Trustee) 36: | | +- Win32_Trustee ----------------------------------------------------------------------- 37: | | | Name: .............................. Everyone 38: | | | SID: ............................... 1,1,0,0,0,0,0,1,0,0,0,0 39: | | | SidLength: ......................... 12 40: | | | SIDString: ......................... S-1-1-0 41: | | +--------------------------------------------------------------------------------------- 42: | +----------------------------------------------------------------------------------------- 43: | +- Win32_ACE ----------------------------------------------------------------------------- 44: | | AccessMask: .......................... &h1301BF 45: FILE_SHARE_CHANGE_ACCESS 46: FILE_SHARE_READ_ACCESS 47: | | AceFlags: ............................ &h0 48: | | AceType: ............................. &h0 49: ACCESS_ALLOWED_ACE_TYPE 50: | | Trustee: ............................. (Win32_Trustee) 51: | | +- Win32_Trustee ----------------------------------------------------------------------- 52: | | | Domain: ............................ LISSWARENET 53: | | | Name: .............................. MyGroup 54: | | | SID: ............................... 1,5,0,0,0,...,207,122,236,255,136,223,4,0,0 55: | | | SidLength: ......................... 28 56: | | | SIDString: ......................... S-1-5-21-3533506287-3489020660-2298473594-1247 57: | | +--------------------------------------------------------------------------------------- 58: | +----------------------------------------------------------------------------------------- 59: +-------------------------------------------------------------------------------------------
The ACE Flags property, although exposed by the WMI and the ADSI object model, is not applicable to a File System share, since the concept of inheritance does not exist for such a security descriptor type. This is why the value is always set to zero (lines 17, 32, and 47).
To configure a security descriptor equivalent to the one shown in Figure 4.21, the following command lines must be used:
1: C:\>WMIManageSD.wsf /Share:MyDirectory /Trustee:REMOVE_ALL_ACE /DelAce+ 2: C:\>WMIManageSD.wsf /Share:MyDirectory /Trustee:BUILTIN\Administrators 3: /ACEType:ACCESS_ALLOWED_ACE_TYPE 4: /ACEMask:FILE_SHARE_FULL_ACCESS, 5: FILE_SHARE_CHANGE_ACCESS, 6: FILE_SHARE_READ_ACCESS 7: /ACEFlags:NONE /AddAce+ 8: C:\>WMIManageSD.wsf /Share:MyDirectory /Trustee:Everyone /DelAce+ 9: C:\>WMIManageSD.wsf /Share:MyDirectory /Trustee:LissWareNET\Everyone 10: /ACEType:ACCESS_ALLOWED_ACE_TYPE 11: /ACEMask:FILE_SHARE_READ_ACCESS 12: /ACEFlags:NONE /AddAce+ 13: C:\>WMIManageSD.wsf /Share:MyDirectory /Trustee:LissWareNET\MyGroup 14: /ACEType:ACCESS_ALLOWED_ACE_TYPE 15: /ACEType:ACCESS_ALLOWED_ACE_TYPE 16: /ACEMask:FILE_SHARE_CHANGE_ACCESS, 17: FILE_SHARE_READ_ACCESS 18: /ACEFlags:NONE /AddAce+ 19: C:\>WMIManageSD.wsf /Share:MyDirectory /Decipher+
As for a folder, setting up the security descriptor of a File System share requires one execution per ACE configuration. Even if flag values are taken from Table 4.13, the logic is exactly the same as before. Note the ACE Flags set to "NONE," since inheritance is not supported for a File System share. As with a file or a folder, the WMI security descriptor access method is used, since no /ADSI+ switch is specified.
4.11.4.5.3 The Active Directory object ACE AccessMask property
Managing the ACE AccessMask property of an Active Directory security descriptor is probably one of the most complex properties to handle. For Active Directory, we must first distinguish the standard rights from the Extended Rights. The standard rights are part of the system and cannot be modified.
However, because some directory-enabled applications may require the creation of some specific rights for the aim of the application, Active Directory offers a way to create new rights to protect Active Directory objects and attributes with more granularity. These rights are called the Active Directory Extended Rights and make use of the ACE ObjectType property. Of course, as we will see in section 4.11.4.5.3.2 ("Understanding the ACE InheritedObjectType property"), the use of an Extended Right is detected by also deciphering other ACE properties.
To decipher the standard Active Directory rights, the technique is still the same as before. A series of flags, defined in Tables 4.14 and 4.15, must be used to perform the deciphering bitwise operations.
| Granted & denied rights | Standard View | ||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Full Control | Read | Write | Create All Child Objects | Delete All Child Objects | Allowed to Authenticate | Change Password | Receive As | Reset Password | Send As | Read Account Restrictions | Write Account Restrictions | Read General Information | Write General Information | Read Group Membership | Write Group Membership | Read Logon Information | Write Logon Information | Read Personal Information | Write Personal Information | Read Phone and Mail Options | Write Phone and Mail Options | Read Public Information | Write Public Information | ||
| ACEType | Standard | Extended | |||||||||||||||||||||||
| ADS_ACETYPE_ACCESS_ALLOWED | 0x0 | X | X | X | X | X | |||||||||||||||||||
| ADS_ACETYPE_ACCESS_DENIED | 0x1 | ||||||||||||||||||||||||
| ADS_ACETYPE_SYSTEM_AUDIT | 0x2 | ||||||||||||||||||||||||
| ADS_ACETYPE_ACCESS_ALLOWED_OBJECT | 0x5 | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | |||||
| ADS_ACETYPE_ACCESS_DENIED_OBJECT | 0x6 | ||||||||||||||||||||||||
| ADS_ACETYPE_SYSTEM_AUDIT_OBJECT | 0x7 | ||||||||||||||||||||||||
| ACEMask | |||||||||||||||||||||||||
| ADS_RIGHT_GENERIC_ALL | 0x10000000 | X | |||||||||||||||||||||||
| ADS_RIGHT_GENERIC_EXECUTE | 0x20000000 | ||||||||||||||||||||||||
| ADS_RIGHT_GENERIC_READ | 0x80000000 | X | |||||||||||||||||||||||
| ADS_RIGHT_GENERIC_WRITE | 0x40000000 | X | |||||||||||||||||||||||
| ADS_RIGHT_ACCESS_SYSTEM_SECURITY | 0x1000000 | ||||||||||||||||||||||||
| ADS_RIGHT_ACTRL_DS_LIST | 0x4 | X | X | ||||||||||||||||||||||
| ADS_RIGHT_DELETE | 0x10000 | X | |||||||||||||||||||||||
| ADS_RIGHT_DS_CONTROL_ACCESS | 0x100 | X | X | X | X | X | X | ||||||||||||||||||
| ADS_RIGHT_DS_CREATE_CHILD | 0x1 | X | X | ||||||||||||||||||||||
| ADS_RIGHT_DS_DELETE_CHILD | 0x2 | X | X | ||||||||||||||||||||||
| ADS_RIGHT_DS_DELETE_TREE | 0x40 | X | |||||||||||||||||||||||
| ADS_RIGHT_DS_LIST_OBJECT | 0x80 | X | |||||||||||||||||||||||
| ADS_RIGHT_DS_READ_PROP | 0x10 | X | X | X | X | X | X | X | X | X | |||||||||||||||
| ADS_RIGHT_DS_SELF | 0x8 | X | X | ||||||||||||||||||||||
| ADS_RIGHT_DS_WRITE_PROP | 0x20 | X | X | X | X | X | X | X | X | X | |||||||||||||||
| ADS_RIGHT_READ_CONTROL | 0x20000 | X | X | X | X | X | |||||||||||||||||||
| ADS_RIGHT_SYNCHRONIZE | 0x100000 | ||||||||||||||||||||||||
| ADS_RIGHT_WRITE_DAC | 0x40000 | X | |||||||||||||||||||||||
| ADS_RIGHT_WRITE_OWNER | 0x80000 | X |
| ||||||||||||||||||||||
| ObjectType | Standard | Extended | |||||||||||||||||||||||
| {68B1D179-0D15-4D4f-AB71-46152E79A7BC} | X | ||||||||||||||||||||||||
| {AB721A53-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||||||||
| {AB721A56-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||||||||
| {00299570-246D-11D0-A768-00AA006E0529} | X | ||||||||||||||||||||||||
| {AB721A54-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||||||||
| {E45795B2-9455-11D1-AEBD-0000F80367C1} | X | ||||||||||||||||||||||||
| {E45795B2-9455-11D1-AEBD-0000F80367C1} | X | ||||||||||||||||||||||||
| {59BA2F42-79A2-11D0-9020-00C04FC2D3CF} | X | ||||||||||||||||||||||||
| {59BA2F42-79A2-11D0-9020-00C04FC2D3CF} | X | ||||||||||||||||||||||||
| {BC0AC240-79A9-11D0-9020-00C04FC2D4CF} | X | ||||||||||||||||||||||||
| {BC0AC240-79A9-11D0-9020-000C04FC2D4CF} | X | ||||||||||||||||||||||||
| {77B5B886-944A-11D1-AEBD-0000F80367C1} | X | ||||||||||||||||||||||||
| {77B5B886-944A-11D1-AEBD-0000F80367C1} | X | ||||||||||||||||||||||||
| {E48D0154-BCF8-11D1-8702-00C04FB96050} | X | ||||||||||||||||||||||||
| {E48D0154-BCF8-11D1-8702-00C04FB96050} | X | ||||||||||||||||||||||||
| {037088F8-0AE1-11D2-B422-00A0C968F939} | |||||||||||||||||||||||||
| {037088F8-0AE1-11D2-B422-00A0C968F939} | |||||||||||||||||||||||||
| {4C164200-20C0-11D0-A768-00AA006E0529} | X | ||||||||||||||||||||||||
| {4C164200-20C0-11D0-A768-00AA006E0529} | X | ||||||||||||||||||||||||
| {5F202010-79A5-11D0-9020-00C04FC2D4CF} | X | ||||||||||||||||||||||||
| {5F202010-79A5-11D0-9020-00C04FC2D4CF} | X | ||||||||||||||||||||||||
| {E45795B3-9455-11D1-AEBD-0000F80367C1} | |||||||||||||||||||||||||
| {E45795B3-9455-11D1-AEBD-0000F80367C1} | |||||||||||||||||||||||||
| ACEFIagType | |||||||||||||||||||||||||
| ADS_FLAG_OBJECT_TYPE_PRESENT[1] | 0x1 | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | |||||
| ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT[1] | 0x2 | ||||||||||||||||||||||||
|
[1]Only used when the ADSI object model is used to represent the security descriptor. | |||||||||||||||||||||||||
| Granted & denied rights | Advanced View | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Full Control | List Contents | Read All Properties | Write All Properties | Delete | Delete Subrange | Read Permissions | Modify Permissions | Modify Owner | All Validated Writes | All Extended Rights | Create All Child Objects | Delete All Child Objects | Allowed to authenticate | Change Password | Receive As | Reset Password | Send As | ||
| ACEType | Standard | Extended | |||||||||||||||||
| ADS_ACETYPE_ACCESS_ALLOWED | 0x0 | X | X | X | X | X | X | X | X | X | X | X | X | X | |||||
| ADS_ACETYPE_ACCESS_DENED | 0x1 | ||||||||||||||||||
| ADS_ACETYPE_SYSTEM_AUDIT | 0x2 | ||||||||||||||||||
| ADS_ACETYPE_ACCESS_ALLOWED_OBJECT | 0x5 | X | X | X | X | X | |||||||||||||
| ADS_ACETYPE_ACCESS_DENIED_OBJECT | 0x6 | ||||||||||||||||||
| ADS_ACETYPE_SYSTEM_AUDIT_OBJECT | 0x7 | ||||||||||||||||||
| ACEMask | |||||||||||||||||||
| ADS_RIGHT_GENERIC_ALL | 0x10000000 | X | |||||||||||||||||
| ADS_RIGHT_GENERIC_EXECUTE | 0x20000000 | ||||||||||||||||||
| ADS_RIGHT_GENERIC_READ | 0x80000000 | ||||||||||||||||||
| ADS_RIGHT_GENERIC_WRITE | 0x40000000 | ||||||||||||||||||
| ADS_RIGHT_ACCESS_SYSTEM_SECURITY | 0x1000000 | ||||||||||||||||||
| ADS_RIGHT_ACTRL_DS_LIST | 0x4 | X | X | X | X | X | X | X | |||||||||||
| ADS_RIGHT_DELETE | 0x10000 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_CONTROL_ACCESS | 0x100 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_CREATE_CHILD | 0x1 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_DELETE_CHILD | 0x2 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_DELETE_TREE | 0x40 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_LIST_OBJECT | 0x80 | X | |||||||||||||||||
| ADS_RIGHT_DS_READ_PROP | 0x10 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_SELF | 0x8 | X | X | ||||||||||||||||
| ADS_RIGHT_DS_WRITE_PROP | 0x20 | X | X | ||||||||||||||||
| ADS_RIGHT_READ_CONTROL | 0x20000 | X | X | ||||||||||||||||
| ADS_RIGHT_SYNCHRONIZE | 0x100000 | ||||||||||||||||||
| ADS_RIGHT_WRITE_DAC | 0x40000 | X | X | ||||||||||||||||
| ADS_RIGHT_WRITE_OWNER | 0x80000 | X | X | ||||||||||||||||
| ObjectType | |||||||||||||||||||
| {68BlD179-0D15-4D4f-AB71-46152E79A7BC} | X | ||||||||||||||||||
| {AB721A53-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||
| {AB72 1A56-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||
| {00299570-246D-11D0-A768-00AA006E0529} | X | ||||||||||||||||||
| {AB721A54-1E2F-11D0-9819-00AA0040529B} | X | ||||||||||||||||||
| ACEFIagType | |||||||||||||||||||
| ADS_FLAG_OBJECT_TYPE_PRESENT [1] | 0x1 | X | X | X | X | X | |||||||||||||
| ADS_FLAG_INHERITED_OB]ECT_TYPE_PRESENT[1] | 0x2 | ||||||||||||||||||
|
[1]Only used when the ADSI object model is used to represent the security descriptor. | |||||||||||||||||||
Sample 4.37, which is part of the DecipherACEType() function, implements this logic. Due to the large number of rights, only a portion of the code is represented.
Sample 4.37: Deciphering the ACE AccessMask property for Active Directory objects
...: ...: ...: 259: 260: Case cActiveDirectoryViaWMI, cActiveDirectoryViaADSI 261: If (intACEMask = ADS_RIGHT_GENERIC_READ) Then 262: strTemp = strTemp & "," & "(ADS_RIGHT_GENERIC_READ)" 263: End If 264: If (intACEMask = ADS_RIGHT_GENERIC_WRITE) Then 265: strTemp = strTemp & "," & "(ADS_RIGHT_GENERIC_WRITE)" 266: End If 267: If (intACEMask = ADS_RIGHT_GENERIC_EXECUTE) Then 268: strTemp = strTemp & "," & "(ADS_RIGHT_GENERIC_EXECUTE)" 269: End If 270: If (intACEMask = ADS_RIGHT_GENERIC_ALL) Then 271: strTemp = strTemp & "," & "(ADS_RIGHT_GENERIC_ALL)" 272: End If ...: 316: If (intACEMask And ADS_RIGHT_DS_CONTROL_ACCESS) Then 317: strTemp = strTemp & "," & "ADS_RIGHT_DS_CONTROL_ACCESS" 318: End If 319: ...: ...: ...:
Active Directory objects can inherit an ACE from parent objects. Therefore, some flags define how the ACE inheritance behaves. These flags are summarized in Table 4.16.
| Inheritance & Audit | ||||||
|---|---|---|---|---|---|---|
| This object only | This object and all child objects | Child objects only | Audit Successful access | Audit Failed access | ||
| ACEFIags | ||||||
| NONE | 0x0 | X | ||||
| ADS_ACEFLAG_INHERIT_ACE | 0x2 | X | X | |||
| ADS_ACEFLAG_INHERIT_ONLY_ACE | 0x8 | X | ||||
| ADS_ACEFLAG_INHERITED_ACE1 | 0x10 | |||||
| ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE | 0x4 | |||||
| ADS_ACEFLAG_VALID_INHERIT_FLAGS [1] | 0x1F | |||||
| ADS_ACEFLAG_SUCCESSFUL_ACCESS | 0x40 | X | ||||
| ADS_ACEFLAG_FAILED_ACCESS | 0x80 | X | ||||
|
[1]can only be set by the system. | ||||||
When configuring ACE inheritance, it is possible to specify that the ACE inheritance will only apply on a particular Active Directory object class. This inheritance makes use of the ACE InheritedObjectType property, which contains a GUID number. To understand how to set up the ACE InheritedObjectType property, it is best to understand how Active Directory Extended Rights work first. This will help us to discover the links that exist between Active Directory classes, Active Directory attributes, and Active Directory rights. It is important to note that Active Directory Extended Rights and ACE inheritance on specific object classes are two different things, but they use the same type of information for their configuration. This explains why it is easier to discover the Active Directory Extended Rights first.
4.11.4.5.3.1 Understanding the ACE ObjectType property
Having a good knowledge of the different Naming Contexts that Active Directory implements and how they are structured is important with respect to the origin of the GUID number contained in the ACE ObjectType property.
All Active Directory objects support a standard set of access rights, listed in Table 4.14. You can use these access rights in the ACE AccessMask of an object's security descriptor to control access at the object level. However, some objects' classes may require an access control not supported by the standard access rights. In such a case, Active Directory allows you to extend the standard access control mechanism to perform a more granular control on some Active Directory objects and attributes. An Active Directory Extended Right is an Active Directory object created from the controlAccessRight object class. All Active Directory Extended Rights are located in the "CN=Extended-Rights" container of the Active Directory Configuration naming context. To correctly decipher an ACE of an Active Directory Extended Right, we must distinguish between different Extended Rights types. The type is determined by the validAccesses attribute value defined in each controlAccessRight object created in the "CN=Extended-Rights" container. There are three Extended Rights types:
-
The Extended Rights enforced by Active Directory: These Extended Rights are enforced by Active Directory to grant (or deny) a read or write operation to an Active Directory property set. A validAccesses attribute value of 0x30 (ADS_RIGHT_DS_READ_ PROP or ADS_RIGHT_DS_WRITE_PROP) defines this type of Extended Rights. They have an ACE Type set to one of these three values: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT, ADS_ACETYPE_ACCESS_DENIED_OBJECT, or ADS_ACETYPE_SYSTEM_AUDIT_OBJECT. The ACE AccessMask value is equal to a logical combination of the ADS_RIGHT_DS_READ_PROP and ADS_RIGHT_DS_WRITE flags (see Table 4.14).
-
The Extended Rights enforced by applications: These rights are enforced by applications, which could be, for instance, Exchange 2000, Outlook 2000, or the system itself but not Active Directory. A validAccesses attribute value of 0x100 (ADS_RIGHT_DS_CONTROL_ACCESS) defines this type of Extended Rights. They have an ACE Type set to one of these three values: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT, ADS_ACETYPE_ACCESS_DENIED_OBJECT, or ADS_ACETYPE_SYSTEM_AUDIT_OBJECT They have an ACE AccessMask value equal to the ADS_RIGHT_DS_CONTROL_ACCESS flag value (see Table 4.14).
-
The Extended Rights enforced by the system to perform extra checking: These Extended Rights are called the "Validated Writes." These rights are used by the system to perform a value check or validation before writing a value to a property on an object. The value checking or validation goes beyond what is required by the Active Directory schema. This type of right uses a value of 0x8 (ADS_RIGHT_DS_SELF) in the validAccesses attribute. They have an ACE Type set to one of these three values: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT, ADS_ACETYPE_ACCESS_DENIED_OBJECT, or ADS_ACETYPE_SYSTEM_AUDIT_OBJECT They have an ACE AccessMask value equal to the ADS_RIGHT_DS_SELF flag value.
Figure 4.22 shows an example of the three Extended Rights types. On the left, we have the "Personal Information" right, which is enforced by Active Directory (validAccesses = 0x30). In the center, we have the "Send As" right, which is enforced by an application (validAccesses = 0x100). On the right, we have the "Add/Remove self as member" right, which is only enforced by the system itself (validAccesses = 0x08).
Figure 4.22: The Extended Rights enforced by Active Directory (left), enforced by applications (center), and enforced by the system (right).
To continue, we will use the three rights in Figure 4.22 as examples. Because rights are always related to an Active Directory object, Extended Rights have a link with the Active Directory object classes they apply to. For instance, the Extended Rights in Figure 4.22 ("Personal Information" and "Send As") are linked with the Active Directory user class defined in the Active Directory schema, because they apply to objects created from the user class. The same rule applies for the "Add/Remove self as member" right, but it is linked with the group class. The link between the Extended right and the user class or the group class is made with an attribute available from the controlAccessRight object, called the appliesTo attribute. The appliesTo attribute may contain one or more GUID numbers, where each GUID number is the value contained in the schemaIDGUID attribute of the class that the Extended Rights relates to. For instance, the "Personal Information" Extended Right has several GUID numbers in the appliesTo attribute (Figure 4.23, left pane), where each of them is coming from the schemaIDGUID attribute of the corresponding classes (Figure 4.23, right pane) for the user class.
Figure 4.23: The appliesTo GUID numbers of the "Personal Information" Extended Right in liaison with the schemaIDGUID attribute of the classSchema object.
Although the format of the GUID number in the schemaIDGUID attribute is in binary, it is the same GUID number. Figure 4.24 illustrates the logic to use to convert a binary GUID number to a string GUID number and vice versa.
Figure 4.24: Converting a GUID string to a GUID number and vice versa.
If we look for the same information for the "Send As" Extended Right, we find the same type of relationship (see Figure 4.25). The same rule will apply if you look at the GUID number stored in the schemaIDGUID attribute of the group class.
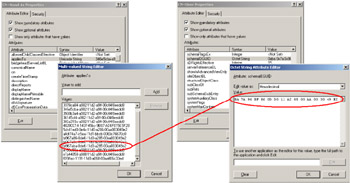
Figure 4.25: The appliesTo GUID numbers of the "Send As" Extended Right in liaison with the schemaIDGUID attribute of the classSchema object.
The aim of the "Personal Information" Extended Right (and of all Extended Rights using a validAccesses attribute value equal to 0x30) is to protect some Active Directory attributes associated with the class that the Extended Right refers to. This means that a relationship between Extended Rights and some Active Directory attributes also exists. To establish the link between an Extended Right and the set of attributes it protects, an Extended Right of this type (validAccesses = 0x30) uses another GUID number, which is stored in the rightsGUID attribute of the controlAccessRight object. Any attributes that can be protected by the Extended Right refer to the Extended Right GUID number by storing the value in its attributeSecurityGUID attribute (see Figure 4.26). The attributeSecurityGUID attribute is part of the attributeSchema object defining the attribute in the Active Directory Schema.
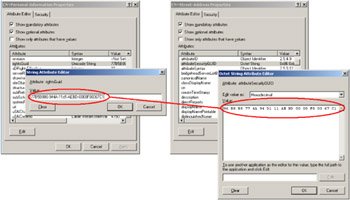
Figure 4.26: The attributeSecurityGUID attribute of the attributeSchema object contains the rights-GUID GUID number of the "Personal Information" Extended Right.
Finally, Figure 4.27 summarizes the links between Extended Rights (controlAccessRight), Active Directory object classes (classSchema), and attribute definitions (attributeSchema). Figure 4.27 also shows that the ACE ObjectType property of a security descriptor using an Extended Right refers to the GUID number value stored in the rightsGUID attribute of the controlAccessRight object. However, we will see later in this section that the GUID number could come from the schemaIDGUID attribute of a classSchema object. This is why we have a dashed line in Figure 4.27.
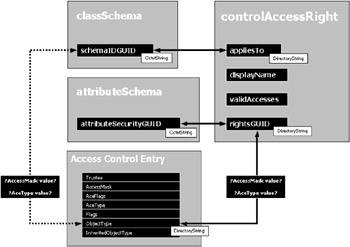
Figure 4.27: The Extended Rights attributes links.
When Extended Rights use a validAccesses attribute value of 0x100, they do not refer to any particular attribute, since this type of right is enforced at the application level, which means that it is the responsibility of the application to validate the right (i.e., Exchange 2000 and Outlook 2000 validate the "Send As" Extended Right). The last type (validAccesses = 0x8) is enforced by the system and is used to lock write operations to some Active Directory attributes (i.e., "Validated write to DNS host name" right applying to the computer class). Table 4.17 summarizes the Extended Rights names and GUID numbers available under Windows Server 2003 and Exchange 2000 SP3 with the classes and attributes they apply to.
| Extended Right Display Name | GUID number (rightsGUID) | Type | Related classes | Protected attributes |
|---|---|---|---|---|
| Account Restrictions | {4c164200-20c0-11d0-a768-00aa006e0529} | 0x30 | inetOrgPerson computer user | accountExpires msDS-User-Account-Control-Computed pwdLastSet userAccountControl userParameters |
| Add GUID | {440820ad-65b4-11d1-a3da-0000f875ae0d} | 0x100 | domainDNS | |
| Add PF to admin group | {ce4c81a8-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Add/Remove Replica In Domain | {9923a32a-3607-11d2-b9be-0000f87a36b2} | 0x100 | domainDNS | |
| Add/Remove self as member | {bf9679c0-0de6-11d0-a285-00aa003049e2} | 0x8 | group | |
| Administer information store | {d74a8762-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchStorageGroup msExchServersContainer msExchPublicMDB msExchPseudoPFAdmin msExchPrivateMDB msExchPFTree msExchOrganizationContainer msExchExchangeServer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Allocate Rids | {1abd7cf8-0a99-11d1-adbb-00c04fd8d5cd} | 0x100 | nTDSDSA | |
| Allowed to Authenticate | {68b1d179-0d15-4d4f-ab71-46152e79a7bc} | 0x100 | inetOrgPerson user computer | |
| Apply Group Policy | {edacfd8f-ffb3-11d1-b41d-00a0c968f939} | 0x100 | groupPolicyContainer | |
| Change Domain Master | {014bf69c-7b3b-11d1-85f6-08002be74fab} | 0x100 | crossRefContainer | |
| Change Infrastructure Master | {cc17b1fb-33d9-11d2-97d4-00c04fd8d5cd} | 0x100 | infrastructureUpdate | |
| Change Password | {ab721a53-1e2f-11d0-9819-00aa0040529b} | 0x100 | inetOrgPerson computer user | |
| Change PDC | {bae50096-4752-11d1-9052-00c04fc2d4cf} | 0x100 | domainDNS | |
| Change Rid Master | {d58d5f36-0a98-11d1-adbb-00c04fd8d5cd} | 0x100 | rIDManager | |
| Change Schema Master | {e12b56b6-0a95-11d1-adbb-00c04fd8d5cd} | 0x100 | dMD | |
| Check Stale Phantoms | {69ae6200-7f46-11d2-b9ad-00c04f79f805} | 0x100 | nTDSDSA | |
| Create Inbound Forest Trust | {e2a36dc9-ae17-47c3-b58b-be34c55ba633} | 0x100 | domainDNS | |
| Create named properties in the information store | {d74a8766-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchStorageGroup msExchServersContainer msExchPublicMDB msExchPrivateMDB msExchPFTree msExchOrganizationContainer msExchExchangeServer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup |
|
| Create public folder | {cf0b3dc8-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPFTree msExchOrganizationContainer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Create top level public folder | {cf4b9d46-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPFTree msExchOrganizationContainer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| DNS Host Name Attributes | {72e39547-7b18-11d1-adef-00c04fd8d5cd} | 0x30 | computer | dNSHostName msDS-AdditionalDnsHostName |
| Do Garbage Collection | {fec364e0-0a98-11d1-adbb-00c04fd8d5cd} | 0x100 | nTDSDSA | |
| Domain Administer Server | {ab721a52-1e2f-11d0-9819-00aa0040529b} | 0x100 | samServer | |
| Domain Password & Lockout Policies | {c7407360-20bf-11d0-a768-00aa006e0529} | 0x30 | domainDNS domain | lockOutObservationWindow loctoutDuration loctoutThreshold maxPwdAge minPwdAge minPwdLength pwdHistoryLength pwdProperties |
| Enable Per User Reversibly Encrypted Password | {05c74c5e-4deb-43b4-bd9f-86664c2a7fd5} | 0x100 | domainDNS | |
| Enroll | {0e10c968-78fb-11d2-90d4-00c04f79dc55} | 0x100 | pKICertificateTemplate | |
| Enumerate Entire SAM Domain | {91d67418-0135-4acc-8d79-c08e857cfbec} | 0x100 | samServer | |
| Exchange administrator | {f8e48d5a8-b09e-11d2-aa0fr00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Exchange full administrator | {f8e6571e0-b09e-11d2-aa0fr00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Exchange public folder read-only administrator | {8ff1383c-b09e-11d2-aa0fr00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Exchange public folder service | {90280e52-b09e-11d2-aa06-00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Execute Forest Update Script | {2f16c4a5-b98e-432c-952a-cb388ba33f2e} | 0x100 | crossRefContainer | |
| General Information | {59ba2f42-79a2-11d0-9020-00c04fc2d3cf} | 0x30 | inetOrgPerson user | adminDescription codePage countryCode displayName objectSid primaryGroupID sAMAccountName sAMAccountType sDRightsEffective showInAdvancedViewOnly sIDHistory uid comment |
| Generate Resultant Set of Policy (Logging) | {b7b1b3de-ab09-4242-9e30-9980e5d322f7} | 0x100 | domainDNS organizationalUnit | |
| Generate Resultant Set of Policy (Planning) | {b7b1b3dd-ab09-4242-9e30-9980e5d322f7} | 0x100 | domainDNS organizationalUnit | |
| Group Membership | {bc0ac240-79a9-11d0-9020-00c04fc2d4cf} | 0x30 | inetOrgPerson user | memberOf member |
| Logon Information | {5f202010-79a5-11d0-9020-00c04fc2d4cf} | 0x30 | inetOrgPerson user | badPwdCount homeDirectory homeDrive lastLogoff lastLogon lastLogonTimestamp logonCount logonHours logonWorkstation profilePath scriptPath userWorkstations |
| Mail-enable public folder | {cf899a6a-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPFTree msExchOrganizationContainer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Manage Replication Topology | {1131f6ac-9c07-11d1-f79f-00c04fc2dcd2} | 0x100 | dMD configuration domainDNS | |
| Migrate SID History | {ba33815a-4f93-4c7fr87f3-57574bff8109} | 0x100 | domainDNS | |
| Modify public folder ACL | {d74a8769-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchPseudoPFAdmin msExchPFTree | |
| Modify public folder admin ACL | {d74a876f-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchPseudoPFAdmin msExchPFTree msExchOrganizationContainer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Modify public folder deleted item retention | {cffe6da4-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPseudoPFAdmin msExchPFTree msExchAdminGroup | |
| Modify public folder expiry | {cfc7978e-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPseudoPFAdmin msExchPFTree msExchAdminGroup | |
| Modify public folder quotas | {d03a086e-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchPseudoPFAdmin msExchPFTree msExchAdminGroup |
|
| Modify public folder replica list | {d0780592-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchStorageGroup msExchServersContainer msExchPublicMDB msExchPseudoPFAdmin msExchPFTree msExchOrganizationContainer msExchExchangeServer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Monitor Active Directory Replication | {f98340fb-7c5b-4cdb-a00b-2ebdfa115a96} | 0x100 | dMD configuration domainDNS | |
| Open Address List | {a1990816-4298-11d1-ade2-00c04fd8d5cd} | 0x100 | addressBookContainer | |
| Open Connector Queue | {b4e60130-df3f-11d1-9c86-006008764d0e} | 0x100 | site | |
| Open mail send queue | {d74a8774-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchStorageGroup msExchServersContainer msExchPublicMDB msExchPrivateMDB msExchOrganizationContainer msExchExchangeServer msExchAdminGroupContainer msExchAdminGroup | |
| Other Domain Parameters (for use by SAM) | {b8119fd0-04f6-4762-ab7a-4986c76b3f9a} | 0x30 | domainDNS | domainReplica forceLogoff modifiedCount oEMInformation serverRole serverState uASCompat |
| Peek Computer Journal | {4b6e08c3-df3c-11d1!-9c8fr006008764d0e} | 0x100 | mSMQConfiguration | |
| Peek Dead Letter | {4b6e08c1-df3c-11d1-9c86-006008764d0e} | 0x100 | mSMQConfiguration | |
| Peek Message | {06bd3201-df3e-11d1-9c86-006008764d0e} | 0x100 | mSMQQueue |
|
| Personal Information | {77b5b886-944a-11d1-aebd-0000f80367c1} | 0x30 | inetOrgPerson computer contact user | streetAddress homePostalAddress assistant info c facsimileTelephoneNumber internationalISDNNumber I publicDelegates mSMQDigests mSMQSignCertificates personalTitle otherFacsimileTelephoneNumber otherHomePhone homePhone otherIpPhone ipPhone primaryInternationalISDNNumber otherMobile mobile otherTelephone otherPager pager physicalDeliveryOfficeName thumbnailPhoto postOfficeBox postalAddress postalCode preferredDeliveryMethod registeredAddress st street telephoneNumber teletexTerminalIdentifier telexNumber primaryTelexNumber userCert userSharedFolder userSharedFolderOther userSMIMECertificate x121Address userCertificate |
| Phone and Mail Options | {e45795b2-9455-11d1-aebd-0000f80367c1} | 0x30 | inetOrgPerson group user |
|
| Public Information | {e48d0154-bcf8-11d1-8702-00c04fb96050} | 0x30 | inetOrgPerson computer user | notes allowedAttributes allowedAttributesEffective allowedChildClasses allowedChildClassesEffective altSecurityIdentities cn company department d escription displayNamePrintable division givenName initials legacyExchangeDN manager msDS-AllowedToDelega |
| Read metabase properties | {be013017-13a1-41ad-a058-f156504cb617} | 0x100 | msExchServersContainer protocolCfgSharedServer msExchOrganizationContainer msExchExchangeServer msExchAdminGroupContainer msExchAdminGroup | |
| Reanimate Tombstones | {45ec5156-db7e-47bb-b53f-dbeb2d03c40f} | 0x100 | dMD configuration domainDNS | |
| Recalculate Hierarchy | {f0bc1554e-0a99-11d1-adbb-00c04fd8d5cd} | 0x100 | nTDSDSA | |
| Recalculate Security Inheritance | {f62dd28a8-7f46-11d2-b9ad-00c04f79f805} | 0x100 | nTDSDSA | |
| Receive As | {ab721a56-1e2f-11d0-9819-00aa0040529b} | 0x100 | msExchServersContainer msExchPublicMDB protocolCfgSMTPServer msExchPrivateMDB msExchOrganizationContainer mTA msExchExchangeServer msExchAdminGroupContainer msExchAdminGroup inetOrgPerson computer user | |
| Receive Computer Journal | {4b6e08c2-df3c-11d1-9c86-006008764d0e} | 0x100 | mSMQConfiguration | |
| Receive Dead Letter | {4b6e08c0-df3c-11d1-9c86-006008764d0e} | 0x100 | mSMQConfiguration | |
| Receive Journal | {06bd3203-df3e-11d1-9c86-006008764d0e} {06bd3200-df3e-11d1-9c86-006008764d0e} | 0x100 | mSMQQueue | |
| Receive Message | {06bd3200-df3e-11d1-9c86-006008764d0e} | 0x100 | mSMQQueue | |
| Refresh Group Cache for Logons | {9432c620-033c-4db7-8b58-14ef6d0bf477} | 0x100 | nTDSDSA |
|
| Remote Access Information | {037088f8-0ae1-11d2-b422-00a0c968f939} | 0x30 | inetOrgPerson user | msNPAllowDialin msNPCallingStationID msRADIUSCallbackNumber msRADIUSFramedIPAddress msRADIUSFramedRoute msRADIUSServiceType tokenGroups tokenGroupsGlobalAndUniversal tokenGroupsNoGCAcceptable |
| Remove PF from admin group | {d0b86510-afe6-11d2-aa04-00c04f8eedd8} | 0x100 | msExchAdminGroup | |
| Replicating Directory Changes | {1131f6aa-9c07-11d1-f79f-00c04fc2dcd2} | 0x100 | dMD configuration domainDNS | |
| Replicating Directory Changes All | {1131f6ad-9c07-11d1-f79f-00c04fc2dcd2} | 0x100 | dMD configuration domainDNS | |
| Replication Synchronization | {1131f6ab-9c07-11d1-f79f-00c04fc2dcd2} | 0x100 | dMD configuration domainDNS | |
| Reset Password | {00299570-246d-11d0-a768-00aa006e0529} | 0x100 | inetOrgPerson computer user | |
| Send As | {ab721a54-1e2f-11d0-9819-00aa0040529b} | 0x100 | msExchServersContainer msExchPublicMDB publicFolder protocolCfgSMTPServer msExchPrivateMDB msExchOrganizationContainer mTA msExchExchangeServer msExchAdminGroupContainer msExchAdminGroup group contact inetOrgPerson computer user |
|
| Send Message | {06bd3202-df3e-11d1-9c86-006008764d0e} | 0x100 | msMQ-Group mSMQQueue | |
| Send To | {ab721a55-1e2f-11d0-9819-00aa0040529b} | 0x100 | Group | |
| Unexpire Password | {ccc2dc7d-a6ad-4a7a-8846-c04e3cc53501} | 0x100 | domainDNS | |
| Update Password Not Required Bit | {280f369c-67c7-438e-ae98-1d46f3c6f541} | 0x100 | domainDNS | |
| Update Schema Cache | {be2bb760-7f46-11d2-b9ad-00c04f79f805} | 0x100 | dMD | |
| Validated write to DNS host name | {72e39547-7b18-11d1-adef-00c04fd8d5cd} | 0x8 | computer | dNSHostName msDS-AdditionalDnsHostName |
| Validated write to service principal name | {f3a64788-5306-11d1-a9c5-0000f80367c1} | 0x8 | computer | |
| View information store status | {d74a875e-22b9-11d3-aa62-00c04f8eedd8} | 0x100 | msExchStorageGroup msExchServersContainer msExchPublicMDB msExchPseudoPFAdmin msExchPrivateMDB msExchPFTree msExchOrganizationContainer msExchExchangeServer msExchConfigurationContainer msExchAdminGroupContainer msExchAdminGroup | |
| Web Information | {e45795b3-9455-11d1-aebd-0000f80367c1} | 0x30 | inetOrgPerson contact user | wWWHomePage url |
Each time, an "ACE" refers to an Extended Right, the ACE ObjectType GUID number must be searched in this table to find the corresponding Extended Rights name. Table 4.17 can also be used to determine which Extended Right protects a specific attribute of a specific Active Directory object. This should ease the process of determining which right must be set to secure a specific attribute. For instance, based on Table 4.17, we know that the "Personal Information" Extended Right protects the street and telephoneNumber attributes, among others.
To understand how to decipher this type of ACE, let's take examples from Figure 4.22. We see that a user called "LISSOIR Alain" is granted to read and change his personal information (left). At the same time, he is also granted the "Send As" right (center), and he can add or remove himself from the "Enterprise Admins" group.
By using the WMIManageSD.Wsf script with the following command line, deciphering this Active Directory security descriptor produces the following output:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=LISSOIR Alain,CN=Users,DC=..." /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP://CN=LISSOIR Alain,CN=Users,DC=... 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. LISSWARENET\Domain Admins 9: | Group: ................................. LISSWARENET\Domain Admins 10: | Revision: .............................. 1 11: | Control: ............................... &h9C14 ..: 18: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 19: ||+- ADSI ACE ------------------------------------------------------------------------------ ..: 38: ||+----------------------------------------------------------------------------------------- ...: 186: ||+- ADSI ACE ------------------------------------------------------------------------------ 187: ||| AccessMask: .......................... &h100 188: ADS_RIGHT_DS_CONTROL_ACCESS 189: ||| AceFlags: ............................ &h0 190: ||| AceType: ............................. &h5 191: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 192: ||| AceFlagType: ......................... &h1 193: ADS_FLAG_OBJECT_TYPE_PRESENT 194: ||| ObjectType: .......................... {AB721A54-1E2F-11D0-9819-00AA0040529B} 195: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 196: ||+----------------------------------------------------------------------------------------- 197: ||+- ADSI ACE ------------------------------------------------------------------------------ 198: ||| AccessMask: .......................... &h30 199: ADS_RIGHT_DS_READ_PROP 200: ADS_RIGHT_DS_WRITE_PROP 201: ||| AceFlags: ............................ &h0 202: ||| AceType: ............................. &h5 203: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 204: ||| AceFlagType: ......................... &h1 205: ADS_FLAG_OBJECT_TYPE_PRESENT 206: ||| ObjectType: .......................... {77B5B886-944A-11D1-AEBD-0000F80367C1} 207: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 208: ||+----------------------------------------------------------------------------------------- ...: 232: |+------------------------------------------------------------------------------------------ 233: +------------------------------------------------------------------------------------------- ...: ...: ...: From line 186 through 196, the "Send As" Extended Right is granted to trustee "Alain.Lissoir" as:
-
The ACE Type has a value equal to ADS_ACETYPE_ACCESS_ALLOWED_OBJECT (line 191).
-
The ACE AccessMask has a value equal to ADS_RIGHT_DS_CONTROL_ACCESS ACE (line 188).
-
The ACE ObjectType property has a GUID number corresponding to the "Send As" Extended Right (line 194). Check Table 4.17 to find the Extended Right GUID number with its corresponding display name.
In the same way, from line 197 through 208, the "Personal Information" Extended Right is granted to trustee "Alain.Lissoir" to read and write the personal information as:
-
The ACE Type has a value equal to ADS_ACETYPE_ACCESS_ALLOWED_OBJECT (line 203).
-
The ACE AccessMask has a value equal to ADS_RIGHT_DS_READ_PROP + ADS_RIGHT_DS_WRITE_PROP (lines 199 and 200).
-
The ACE ObjectType property has a GUID number corresponding to the "Personal Information" Extended Right (line 206). Check Table 4.17 to find the Extended Right GUID number with its corresponding display name.
For the "Add/Remove self as member" Extended Right, the same logic applies with different values.
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Enterprise Admins,CN=Users,DC=..." /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP://CN=Enterprise Admins,CN=...'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. LISSWARENET\Domain Admins 9: | Group: ................................. LISSWARENET\Domain Admins 10: | Revision: .............................. 1 11: | Control: ............................... &h9C14 ..: 18: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 19: ||+- ADSI ACE ------------------------------------------------------------------------------ ..: 38: ||+----------------------------------------------------------------------------------------- ...: 174: ||+- ADSI ACE ------------------------------------------------------------------------------ 175: ||| AccessMask: .......................... &h8 176: ADS_RIGHT_DS_SELF 177: ||| AceFlags: ............................ &h2 178: ADS_ACEFLAG_CONTAINER_INHERIT_ACE 179: ADS_ACEFLAG_VALID_INHERIT_FLAGS 180: ||| AceType: ............................. &h5 181: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 182: ||| AceFlagType: ......................... &h1 183: ADS_FLAG_OBJECT_TYPE_PRESENT 184: ||| ObjectType: .......................... {BF9679C0-0DE6-11D0-A285-00AA003049E2} 185: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 186: ||+----------------------------------------------------------------------------------------- ...: 224: |+------------------------------------------------------------------------------------------ 225: +------------------------------------------------------------------------------------------- From line 174 through 186, the right "Add/Remove self as member" is granted to trustee "Alain.Lissoir" as:
-
The ACE Type has a value equal to ADS_ACETYPE_ACCESS_ALLOWED_OBJECT (line 181).
-
The ACE AccessMask has a value equal to ADS_RIGHT_DS_SELF (line 176).
-
The ACE ObjectType property has a GUID number corresponding to the "Add/Remove self as member" Extended Right (line 184). Check Table 4.17 to find the Extended Right GUID number with its corresponding display name.
When the ACE AccessMask property has a value coming from a combination of the ADS_RIGHT_DS_CREATE_CHILD and ADS_RIGHT_DS_DELETE_CHILD flags, the ACE ObjectType property contains a GUID number, but it does not refer to an Extended Right. In this case, the GUID number refers to the schemaIDGUID of an Active Directory class-Schema object and defines a permission that grants or denies a trustee the right to create or delete objects of the referred class type. The dashed line in Figure 4.27 represents this link. Figure 4.28 shows an example of such a right on the "CN=Users" container.
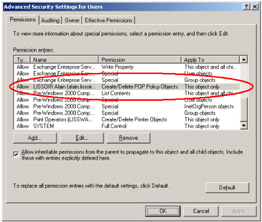
Figure 4.28: The ACE ObjectType property used to grant or deny the creation or deletion of objects from a particular class.
If we decipher the ACE, we obtain the following result:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Users,DC=LissWare,DC=Net" /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP://CN=Users,DC=LissWare,DC=Net'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. LISSWARENET\Domain Admins 9: | Group: ................................. LISSWARENET\Domain Admins 10: | Revision: .............................. 1 11: | Control: ............................... &h8C14 ..: 17: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 18: ||+- ADSI ACE ------------------------------------------------------------------------------ ..: 29: ||+----------------------------------------------------------------------------------------- ...: 105: ||+- ADSI ACE ------------------------------------------------------------------------------ 106: ||| AccessMask: .......................... &h3 107: ADS_RIGHT_DS_CREATE_CHILD 108: ADS_RIGHT_DS_DELETE_CHILD 109: ||| AceFlags: ............................ &h2 110: ADS_ACEFLAG_CONTAINER_INHERIT_ACE 111: ADS_ACEFLAG_VALID_INHERIT_FLAGS 112: ||| AceType: ............................. &h5 113: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 114: ||| AceFlagType: ......................... &h1 115: ADS_FLAG_OBJECT_TYPE_PRESENT 116: ||| ObjectType: .......................... {35BE884C-A982-11D2-A9FF-00C04F8EEDD8} 117: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 118: ||+----------------------------------------------------------------------------------------- ...: 437: |+------------------------------------------------------------------------------------------ 438: +------------------------------------------------------------------------------------------- From line 105 through 118, the right "Create/Delete POP Policy Objects" is granted to trustee "Alain.Lissoir" as:
-
The ACE Type has a value equal to ADS_ACETYPE_ACCESS_ALLOWED_OBJECT (line 113).
-
The ACE AccessMask has a value equal to ADS_RIGHT_DS_CREATE_CHILD + ADS_RIGHT_DS_DELETE_CHILD (lines 107 and 108).
-
The ACE ObjectType property has a GUID number corresponding to the schemaIDGUID of a classSchema object, which is the msExchProtocolCfgPOPPolicy object class (line 116). Check Table 4.18 to find the schemaIDGUID GUID number and determine the corresponding Active Directory class.
Table 4.18: The schemaIDGUID GUID Number with iTs Class Names Display Name
Object Class
schemaIDGUID
* objects
msExchDomainContentConfig
{ab3a1ad1-1df5-11d3-aa5e-00c04f8eedd8}
account objects
account
{2628a46a-a6ad-4ae0-b854-2b12d9fe6f9e}
aCSPolicy objects
aCSPolicy
{7f561288-5301-11d1-a9c5-0000f80367c1}
aCSResourceLimits objects
aCSResourceLimits
{2e899b04-2834-11d3-91d4-0000f87a57d4}
aCSSubnet objects
aCSSubnet
{7f561289-5301-11d1-a9c5-0000f80367c1}
Active Directory Service objects
nTDSService
{19195a5f-6da0-11d0-afd3-00c04fd930c9}
ADC Connection Agreement objects
msExchConnectionAgreement
{ee64c33a-a980-11d2-a9ff-00c04f8eedd8}
ADC Schema Map Policy objects
msExchSchemaMapPolicy
[348af8f2-a98-11d2-a9ff-00c04f8eedd8}
ADC Service objects
msExchActiveDirectoryConnector
{e605672c-a980-11d2-a9ff-00c04f8eedd8}
Address List objects
addressBookContainer
{3e74f60f-3e73-11d1-a9c0-0000f80367c1}
Address Template objects
addressTemplate
{5fd4250a-1262-11d0-a060-00aa006c33ed}
Address Type objects
addrType
{a8df74ab-c5ea-11d1-bbcb-0080c76670c0}
Addressing Policy objects
msExchAddressingPolicy
{e7211f02-a980-lld2-a9ff-00c04f8eedd8>
Administrative Group objects
msExchAdminGroup
{e768a58e-a980-11d2-a9ff-00c04f8eedd8}
Administrative Groups objects
msExchAdminGroupContainer
(e7a44058-a980-11d2-a9ff-00c04f8eedd8}
Administrative Role objects
msExchAdminRole
{e7f2edf2-a980-11d2-a9ff-00c04f8eedd8}
Advanced Security objects
msExchAdvancedSecurityContainer
(8cc8fb0e-b09e-11d2-aa06-00c04f8eedd8}
applicationEntity objects
applicationEntity
{3fdfee4f-47f4-11d1-a9c3-0000f80367c1}
applicationProcess objects
applicationProcess
{5fd4250b-1262-11d0-a060-00aa006c33ed}
applicationSettings objects
applicationSettings
{f780acc1-56f0-11d1-a9c6-0000f80367c1}
applicationSiteSettings objects
applicationSiteSettings
(19195a5c-6da0-11d0-afd3-00c04fd930c9}
applicationVersion objects
applicationVersion
{ddc790aoaf4d-442a-8f0f-a1d4caa7dd92}
builtinDomain objects
builtinDomain
{bf967a81-0de6-11d0-a285-00aa003049e2}
categoryRegistration objects
categoryRegistration
{7d6c0e9d-7e20-11d0-afd6-00c04fd930c9}
cc:Mail Connector objects
msExchocMailConnector
{e85710b6-a980-11d2-a9ff-00c04f8eedd8}
Certificate Template objects
pKICertificateTemplate
{e5209ta2-3bba-11d2-90cc-00c04fd91ab1}
Certification Authority objects
certificationAuthority
{3fdfee50-47f4-11d1-a9c3-0000f8a367c1}
Chat Network objects
msExchChatNetwork
{e934cb68-a980-11d2-a9ff-00c04f8eedd8}
Chat Protocol objects
msExchChatProtocol
{e9621816-a980-11d2-a9ff-00c04f8eedd8}
classRegistration objects
classRegistration
{bf967a82-0de6-11d0-a285-00aa003049e2}
classStore objects
classStore
{bf967a84-0de6-11d0-a285-00aa003049e2}
comConnectionPoint objects
comConnectionPoint
{bf967a85-0de6-11d0-a285-00aa003049e2}
Computer objects
computer
{bf967a86-0de6-11d0-a285-00aa003049e2}
Computer Policy objects
msExchComputerPolicy
{ed2c752c-a980-11d2-a9ff-00c04f8eedd8}
Conference Site objects
msExchConferenceSite
{eddce330-a980-11d2-a9ff-00c04f8eedd8}
Conference Sites objects
msExchConferenceContainer
(ed7fe77a-a980-11d2-a9ff-00c04f8eedd8}
configuration objects
configuration
{bf967a87-0de6-11d0-a285-00aa003049e2}
Connection objects
nTDSConnection
{19195a60-6da0-11d0-afd3-00c04fd930c9}
connectionPoint objects
connectionPoint
{5cb41ecf-0e4c-11d0-a286-00aa003049e2}
Connections objects
msExchConnectors
{eee325dc-a980-11d2-a9ff-00c04f8eedd8}
Contact objects
contact
{5cb41ed0-0e4c-11d0-a286-00aa003049e2}
Container objects
container
{bf967a8b-0de6-11d0-a285-00aa003049e2}
country objects
country
{bf967a8c-0de6-11d0-a285-00aa003049e2}
cRLDistributionPoint objects
cRLDistributionPoint
{167758ca-47f3-11d1-a9c3-0000f80367c1}
crossRef objects
crossRef
{bf967a8d-0de6-11d0-a285-00aa003049e2}
crossRefContainer objects
crossRefContainer
{ef9e60e0-56f7-11d1-a9c6-0000f80367c1}
Data Conference Server (T.120 MCU) objects
msExchMCU
{038680ec-a981-11d2-a9ff-00c04f8eedd8}
Data Conference Technology Provider (T.120 MCU) objects
msExchMCUContainer
{03aa4432-a981-11d2-a9ff-00c04f8eedd8}
device objects
device
{bf967a8e-0de6-11d0-a285-00aa003049e2}
dfsConfiguration objects
dfsCcnfiguration
{8447f9f2-1027-11d0-a05f-00aa006c33ed}
dHCPClass object
dHCPCIass
{963d2756-48be-11d1-a9c3-0000f80367c1}
Directory objects
dSA
{3fdfee52-47f4-11d1-a9c3-0000f80367c1}
Directory Replication Connector objects
msExchReplicationConnector
{99f58682-12e8-11d3-aa58-00c04f8eedd8}
Diectory Synchronization objects
IocalDXA
{a8df74b5-c5ea-11d1-bbcb-0080c76670c0}
Directory Synchronization Requestor objects
dXRequestor
{a8df74ae-c5ea-11d1-bbcb-0080c76670c0}
Directory Synchronization Server Connector objects
dXServerConn
(a8df74af-c5ea-11d1-bbcb-0080c76670c0}
Directory Synchronization Site Server objects
dXASiteServer
(a8df74b0-c5ea-11d1-bbcb-0080c76670c0}
Display Template objects
displayTemplate
{5fd4250c-1262-11d0-a060-00aa006c33ed}
displaySpecifier objects
displaySpecifier
{e0fa1e8a-9b45-11d0-afdd-00c04fd930c9}
dnsNode objects
dnsNode
{e0fa1e8c-9b45-11d0-afdd-00c04fd930c9}
dnsZone objects
dnsZone
{e0fa1e8b-9b45-11d0-afdd-00c04fd930c9}
document objects
document
{39bad96d-c2d6-4baf-88ab-7e4207600117}
documentSeries objects
documentSeries
{7a2be07c-302f-4b96-bc90-0795d66885f8}
Domain Controller Settings objects
nTDSDSA
{f0f8ffab-1191-11d0-a060-00aa006c33ed}
domain objects
domain
{19195a5a-6da0-11d0-afd3-00c04fd930c9}
Domain objects
domainDNS
{19195a5b-6da0-11d0-afd3-00c04fd930c9}
Domain Policy objects
domainPolicy
{bf967a99-0de6-11d0-a285-00aa003049e2}
domainRelatedObject objects
domainRelatedObject
{8bfd2d3d-efda-4549-852c-f85e137aedc6}
dSUISettings objects
dSUISettings
{09b10f14-6f93-11d2-9905-0000f87a57d4}
Dynamic RAS Connector objects
rASX400Link
{a8df74d4-c5ea-11d1-bbcb-0080c76670c0}
dynamicObject objects
dynamicObject
{66d51249-3355-4c1f-b24e-81f252aca23b}
Encryption Configuration objects
encryptionCfg
{a8df74b1-c5ea-11d1-bbcb-0080c76670c0}
Exchange Add-In objects
addln
{a8df74aa-c5ea-11d1-bbct-0080c76670c0}
Exchange Admin Extension objects
adminExtension
{a8df74ac-c5ea-11d1-bbcb-0080c76670c0}
Exchange Configuration Container objects
msExchConfigurationContainer
{d03d5858-06f4-11d2-aa53-00c04fd7d63a}
Exchange Container objects
msExchContainer
{006c91da-a981-11d2-a9ff-00c04f8eedd8}
Exchange Organization objects
msExchOrganizationContainer
{366a319c-a982-11d2-a9ff-00c04f8eedd8}
Exchange Policies objects
msExchPoliciesContainer
{3630f92c-a982-11d2-a9ff-00c04f8eedd8}
Exchange, Protocols objects
msExchProtocolCfgProtocolContainer
{90f2b634-b09e-11d2-aa06-00c04f8eedd8}
Exchange Server objects
msExchExcriangeServer
{01a9aa9c-a981-11d2-a9ff-00c04f8eedd8}
Exchange Server Policy objects
msExchExchangeServerPolicy
{e497942f-1d42-11d3-aa5e-00c04f8eedd8}
Exchange Servers objects
msExchServersContainer
{346e5cba-a982-11d2-a9ff-00c04f8eedd8}
Extended Right objects
controlAccessRight
{8297931e-86d3-11d0-afda-00c0fd930c9}
fileLinkTracking objects
fileLinkTracking
{dd712229-10e4-11d0-a05f-00aa006c33ed}
fileLinkTrackingEntry objects
filelinkTrackingEntry
{8e4eb2ed-4712-11d0-a1a0-00c04fd930c9}
Foreign Security Principal objects
foreignSecurityPrincipal
{89e31c12-8530-11d0-afda-00c04fd930c9}
friendlyCountry objects
friendlyCountry
{c498f152-dc6b-474a-9f52-7cdba3d7d351}
FRS Member objects
nTFRSMember
{2a132586-9373-11d1-aebc-0000f80367c1}
FRS Replica Set objects
nTFRSReplicaSet
{5245803a-ca6a-11d0-afff-0000f80367c1}
FRS Settings objects
nTFRSSettingss
{f780acc2-56f0-11d1-a9c6-0000f80367c1}
FRS Subscriber objects
nTFRSSubscriber
{2a132588-9373-11d1-aebc-0000f80367c1}
FRS Subscriptions objects
nTFRSSubscriptions
{2a132587-9373-11d1-aebc-0000f80367c1}
fTDfs objects
fFDfs
{8447f9f3-1027-11d0-a05f-00aa006c33ed}
Gateway objects
mailGateway
{a8df74b7-c5ea-11d1-bbcb-0080c76670c0}
Group objects
group
{bf967a9c-0de6-11d0-a285-00aa003049e2}
groupOfNames objects
groupOfNames
{bf967a9d-0de6-11d0-a285-00aa003049e2}
groupOfUniqueNames objects
groupOfUniqueNames
{0310a911-93a3-4e21-a7a3-55d85ab2c48b}
groupPolicyContainer objects
groupPolicyContainer
{f30e3bc2-9ff0-11d1-b603-0000f80367c1}
GroupWise Connector objects
msExchGroupWiseConnector
{91eaaac4-b09e-11d2-aa06-00c04f8eedd8}
HTTP Protocol objects
msExchProtocolCfgHTTPContainer
{9432cae6-b09e-11d2-aa06-00c04f8eedd8}
HTTP Virtual Directory objects
msExchProtocolCfgHTTPVirtualDirectory
{8c3c5050-b09e-11d2-aa06-00c04f8eedd8}
HTTP Virtual Server objects
protocolCfgHTTPServer
{a8df74c2-c5ea-11d1-bbcb-0080c76670c0}
IMAP Policy objects
msExchProtocolCfgIMAPPolicy
{35f7c0bc-a982-11d2-a9ff-00c04f8eedd8}
IMAP Protocol objects
msExchProtocolCfgIMAPContainer
{93da93e4-b09e-11d2-aa06-00c04f8eedd8}
IMAP Sessions objects
msExchProtocolCfgIMAPSessions
{99f58672-12e8-11d3-aa58-00c04f8eedd8}
IMAP Virtual Server objects
protocolCfgIMAPServer
{a8df74c5-c5ea-11d1-bbcb-0080c76670c0}
indexServerCatalog objects
indexServerCatalog
{7bfdcb8a-4807-11d1-a9c3-0000f80367c1}
InetOrgPerson objects
inetorgPerson
{4828cc14-1437-45bc-9b07-ad6f015e5f28}
Information Store objects
msExchInformationStore
{031b371a-a981-11d2-a9ff-00c04f8eedd8}
infrastructureUpdate objects
infrastructureUpdate
{2df90d89-009f-11d2-aa4c-00c04fd7d83a}
Instant Messaging Global Settings objects
msExchIMGlobalSettingsContainer
[9f116eb8-284e-11d3-aa68-00c04f8eedd8}
Instant Messaging Protocol objects
msExchProtocolCfgIMContainer
{9f116ea3-284e-11d3-aa68-00c04f8eedd8}
Instant Messaging Virtual Server objects
msExchProtocolCfgIMVirtuaIServer
{9f116eb4-284e-11d3-aa68-00c04f8eedd8}
IntelliMirror Group objects
intellimirrorGroup
{07383086-91df-11d1-aebc-000080367c1}
IntelliMirror Service objects
intellimirrorSCP
{07383085-91df-11d1-aebc-0000f80367c1}
Internet Message Formats objects
msExchContentConfigContainer
{ab3a1acc-1df5-11d3-aa5e-00c04f8eedd8}
Inter-Site Transport objects
interSiteTransport
{26d97376-6070-11d1-a9c6-0000f80367c1}
Inter-Site Transports Container objects
interSiteTransportContainer
{26d97375-6070-11d1-a9c6-0000f80367c1}
ipsecBase objects
ipsecBase
{b40ff825-427a-11d1-a9c2-0000f80367c1}
ipsecFilter objects
ipsecFilter
{b40ff826-427a-11d1-a9c2-0000f80367c1}
ipsecISAKMPPoliy objects
ipsecISAKMPPolicy
{b40ff828-427a-11d1-a9c2-0000f80367c1}
ipsecNegotiationPolicy objects
ipsecNegotiationPolicy
{b40ff827-427a-11d1-a9c2-0000f80367c1}
ipsecNFA objects
ipsecNFA
{b40ff829-427a-11d1-a9c2-0000f80367c1}
ipsecPolicy objects
ipsecPolicy
{b7b13121-b82e-11d0-afee-0000f80367c1}
Key Management Server objects
msExchKeyManagementServer
{8ce334ec-b09e-11d2-aa06-00c04f8eedd8}
leaf objects
leaf
{bf967a9e-0de6-11d0-a285-00aa003049e2}
Licensing Site Settings obiects
licensingSiteSettings
{1be8f7d-a9ff-11d0-afe2-00c04fd930c9}
linkTrackObjectMoveTable objects
linkTrackObjectMoveTable
{ddac0cf5-af8f-11d0-afeb-00c04fd930c9}
linkTrackOMTEntry objects
linkTrackOMTEntry
{ddac0cf7-af8f-11d0-afeb-00c04fd930c9}
linkTrackVolEntry objects
linkTrackVolEntry
{ddac0cf6-af8f-11d0-afeb-00c04fd930c9}
linkTrackVolumeTable objects
linkTrackVolumeTable
{ddac0cf4-af8f-11d0-afeb-00c04fd930c9}
locality objects
Locality
{bf967aa0-0de6-11d0-a285-00aa003049e2}
lostAndFound objects
lostAndFound
{52ab8671-5709-11d1-a9c6-0000f80367c1}
Mail Recipient objects
mailRecipient
{bf967aa1-0de6-11d0-a285-00aa003049e2}
meeting objects
Meeting
{11b6cc94-48c4-11d1-a9c3-0000f80367c1}
Message Delivery Configuration objects
msExchMessageDeliveryConfig
{ab3a1ad7-1df5-11d3-aa5e-00c04f8eedd8}
Message Gateway for cc:Mail objects
mailConnector
{a8df74b6-c5ea-11d1-bbcb-0080c76670c0}
Message Transfer Agent objects
mTA
{a8df74a7-c5ea-11d1-bbcb-0080c76670c0}
mHSMonitoringConfig objects
mHSMonitoringConfig
{a8df74bb-c5ea-11d1-bbcb-0080c76670c0}
Microsoft Exchange System Objects objects
msExchSystemObjectsContainer
{0bffa04c-7d8e-44cd-968a-b2cac11d17e1}
Monitoring Link Configuration objects
mHSLinkMonitoringConfig
{a8df74b9-c5ea-11d1-bbcb-0080c76670c0}
Monitoring Server Configuration objects
mHSServerMonitoringConfig
{a8df74bd-c5ea-11d1-bbcb-0080c76670c0}
msCOM-Partition objects
msCOM-Partition
{c90:0e74-4e58-9f7-8a89-5e3e2340fcf8}
msCOM-PartitionSet objects
msCOM-PartitionSet
{250464ab-c417-497a-975a-9e0d459a7ca1}
msDS-App-Configuration objects
msDS-App-Configuration
{90df3c3e-1854-4455-a5d7-cad40d56657a}
msDS-AppData objects
msDS-AppData
{9e67d761-e327-4d55-bc95-682f875e2f8e}
msDS-AzAdminManager objects
msDS-AzAdminManager
{cfee1051-5f28-4bae-a863-5d0cc18a8ed1}
msDS-AzApplication objects
msDS-AzApplication
{ddf8de9b-cba5-4e12-842e-28d8b66f75ec}
msDS-AzOperation objects
msDS-AzOperation
{860abe37-9a9b-4fa4-b3d2-b8ace5df9ec5}
msDS-AzRole objects
msDS-AzRole
{8213eac9-9d55-44dc-925c-e9a52b927644}
msDS-AzScope objects
msDS-AzScope
{4feae054-ce55-47bb-860e-5b12063a51de}
msDS-AzTask objects
msDS-AzTask
{1ed3a473-9b1b-418a-bfa0-3a37b95a5306}
msExchAddressListServiceContainer objects
msExchAddressListServiceContainer
{b1fce95a-1d44-11d3-aa5e-00c04f8eedd8}
msExchBaseClass objects
msExchBaseClass
{d8782c34-46ca-11d3-aa72-00c04f8eedd8}
msExchCalendarConnector objects
msExchCalendarConnector
{922180da-b09e-11d2-aa06-00c4f8eedd8}
msExchCertificatelnformation objects
msExchCertificatelnformation
{e8977034-a980-11d2-a9ff-00c04f8eedd8}
msExchChatBan objects
msExchChatBan
{e8d0a8a4-a980-11d2-a9ff-00c04f8eedd8}
msExchChatChannel objects
msExchChatChannel
{e902ba06-a980-11d2-a9ff-00c04f8eedd8}
msExchChatUserClass objects
msExchChatUserClass
{e9a0153a-a980-11d2-a9ff-00c04f8eedd8}
msExchConnector objects
msExchConnector
{89652316-b09e-11d2-aa06-00c04f8eedd8}
msExchCTP objects
msExchCTP
{00aa8efe-a981-11d2-a9ff-00c04f8eedd8}
msExchCustomAttributes objects
msExchCustomAttributes
{00e629c8-a981-11d2-a9ff-00c04f8eedd8}
msExchDynamicDistributionList objects
msExchDynamicDistributionList
{018849b0-a981-11d2-a9ff-00c04f8eedd8}
msExchGenericPolicy objects
msExchGenericPolicy
{e32977cd-1d31-11d3-aa5e-00c04f8eedd8}
msExchGenericPolicyContainer objects
msExchGenericPolicyContainer
{e32977c3-1d31-11d3-aa5e-00c04f8eedd8}
msExchIMFirewall objects
MsExchIMFirewall
{9f116ebe-284e-11d3-aa68-00c04f8eedd8}
msExchIMRecipient objects
msExchIMRecipient
{028502f4-a981-11d2-a9ff-00c04f8eedd8}
msExchMailboxManagerPolicy objects
msExchMailboxManagerPolicy
{36f94fcc-ebbb-4a32-b721-1cae42b2dbab}
msExchMailStorage objects
msExchMailStorage
{03652000-a981-11d2-a9ff-00c04f8eedd8}
msExchMDB objects
msExchMDB
{03d069d2-a981-11d2-a9ff-00c04f8eedd8}
msExchMonitorsContainer objects
msExchMonitorsContainer
{03f68f72-a981-11d2-a9ff-00c04f8eedd8}
msExchMultiMediaUser objects
msExchMultiMediaUser
{1529cf7a-2fdb-11d3-aa6d-00c04f8eedd8}
msExchOWMConnector objects
msExchOWMConnector
{91ce0e8c-b09e-11d2-aa06-00c04f8eedd8}
msExchPrivateMDBProxy objects
msExchPrivateMDBProxy
{b8d47e54-4b78-11d3-aa75-00c04f8eedd8}
msExchProtocolCfgHTTPFilter objects
msExchProtocolCfgHTTPFilter
{8c7588c0-b09e-11d2-aa06-00c04f8eedd8}
msExchProtocolCfgHTTPFilters objects
msExchProtocolCfgHTTPFilters
{8c58ec88-b09e-11d2-aa06-00c04f8eedd8}
msExchProtocolCfgIM objects
msExchProtocolCfgIM
{9f116ea7-284e-11d3-aa68-00c04f8eedd8}
msExchProtocolCfgSharedContainer objects
msExchProtocolCfgSharedContainer
{939ef91a-b09e-11d2-aa06-00c04f8eedd8}
msExchProtocolCfgSMTPIPAddress objects
msExchProtocolCfg SMTPIPAddress
{8b7b31d6-b09e-11d2-aa06-00c04f8eedd8}
msExchProtocolCfgSMTPIPAddressContainer objects
msExchProtocolCfgSMTPIPAddressContainer
{8b2c843c-b09e-11d2-aa06-00c04f8eedd8}
msExchPseudoPF objects
msExchPseudoPF
{oec4472b-22ae-11d3-aa62-00c04f8eedd8}
msExchPseudoPFAdmin objects
msExchPseudoPFAdmin
{9ae2fa1b-22b0-11d3-aa62-00c04f8eedd8}
msExchPublicFolderTreeContainer objects
msExchPublicFolderTreeContainer
{3582ed82-a982-11d2-a9ff-00c04f8eedd8}
msExchSNADSConnector objects
msExchSNADSConnector
{91b17254-b09e-11d2-aa06-00c04f8eedd8}
msieee80211-Policy objects
msieee80211-Policy
{7b9a2d92-b7eb-4382-9772-c3e0f9baaf94}
MSMail Connector objects
mSMailConnector
{a8df74be-c5ea-11d1-bbcb-0080c76670c0}
MSMQ Configuration objects
mSMQConfiguration
{9a0dc344-c100-11d1-bbc5-0080c76670c0}
MSMQ Enterprise objects
mSMQEntErpriseSettings
{9a0dc345-c100-11d1-bbc5-0080c-76670c0}
MSMQ Group objects
msMQ-Group
{46b27aac-aafa-4ffb-b773-e5bf621ee87b}
MSMQ Queue Alias objects
msMQ-Custom-Recipient
{876d5817-35cc-436c-acea-5ef7174dd9be}
MSMQ Queue objects
mSMQQueue
{9a0dc343-c100-11d1-bbc5-0080c76670c0}
MSMQ Routing Link objects
mSMQSiteLink
{9a0dc346-c100-11d1-bbc5-0080c76670c0}
MSMQ Settings objects
mSMQSettings
{9a0dc347-c100-11d1-bbc5-0080c76670c0}
MSMQ Upgraded User objects
mSMQMigratedUser
{50776997-3c3d-11d2-90cc-00c04fd91ab1}
msPKI-Enterprise-Oid objects
msPKI-Enterprise-Oid
{37cfd85c-6719-4ad8-8f9e-8678ba627563}
msPKI-Key-Recovery-Agent objects
msPKI-Key-Recovery-Agent
{26ccf238-a08e-4b86-9a82-a8c9ac7ee5cb}
msPKI-PrivateKeyRecoveryAgent objects
msPKI-PrivateKeyRecoveryAgent
{1562a632-44b9-4a7e-a2d3-e426c96a3acc}
mS-SQL-OLAPCube objects
mS-SQL-OLAPCube
{09f0506a-cd28-11d2-9993-0000f87a57d4}
mS-SQL-OLAPDatabase objects
mS-SQL-OLAPDatabase
{20afa31a-cef-11d2-9993-0000f87a57d4}
mS-SQL-OLAPServer objects
mS-SQL-OLAPServer
{0c7e18ea-ccef-11d2-9993-0000f87a57d4}
mS-SQL-SQLDatabase objects
mS-SQL-SQLDatabase
{1d08694a-ccef-11d2-9993-0000f87a57d4}
mS-SQL-SQLPublication objects
mS-SQL-SQLPublication
{17c2f64e-ccef-11d2-9993-0000f87a57d4}
mS-SQL-SQLRepository objects
mS-SQL-SQLRepository
{11d43c5c-ccef-11d2-9993-0000f87a57d4}
mS-SQL-SQLServer objects
mS-SQL-SQLServer
{05f6c878-ccef-11d2-9993-0000f87a57d4}
msTAPI-RtConference objects
msTAPI-RtConference
{ca7b9735-4b2a-4e49-89c3-99025334dc94}
msTAPI-RtPerson objects
msTAPI-RtPerson
{53ea1cb5-b704-4df9-818f-5cb4ec86cac1}
msWMI-IntRangeParam objects
msWMI-IntRangeParam
{50ca5d7d-5c8b-4ef3-b9df-5b66d491e526}
msWMI-IntSetParam objects
msWMI-IntSetParam
{292f0d9a-cf76-42b0-841f-b650f331df62}
msWMI-MergeablePolicyTemplate objects
msWMI-MergeablePolicyTemplate
{07502414-fdca-4851-b04a-13645b11d226}
msWMI-ObjectEncoding objects
msWMI-ObjectEncoding
{55dd81c9-c312-41f9-a84d-c6adbdf1e8e1}
msWMI-PolicyTemplate objects
msWMI-PolicyTemplate
{e2bc80f1-244a-4d59-acc6-ca5c4f82e6e1}
msWMI-PolicyType objects
msWMI-PolicyType
{595b2613-4109-4e77-9013-a3bb4ef277c7}
msWMI-RangeParam objects
msWMI-RangeParam
{45fb5a57-5018-4d0f-9056-997c8c9122d9}
msWMI-RealRangeParam objects
msWMI-RealRangeParam
{6afe8fe2-70bc-4cce-b166-a96f7359c514}
msWMI-Rule objects
msWMI-Rule
{3c7e6f83-dd0e-481b-a0c2-74cd96ef2a66}
msWMI-ShadowObject objects
msWMI-ShadowObject
{f1e44bdf-8dd3-4235-9c86-f91f31f5b569}
msWMI-SimplePolicyTemplate objects
msWMI-SimplePolicyTemplate
{6cc8b2b5-12df-44f6-8307-e74f5cdee369}
msWMI-Som objects
msWMI-Som
{ab857078-0142-4406-945b-34c9b6b13372}
msWMI-StringSetParam objects
msWMI-StringSetParam
{0bc579a2-1da7-4cea-b699-807f3b9d63a4}
msWMI-UintRangeParam objects
msWMI-UintRangeParam
{d9a799b2-cef3-48b3-b5ad-fb85f8dd3214}
msWMI-UintSetParam objects
msWMI-UintSetParam
{8f4beb31-4e19-46f5-932e-5fa03c339b1d}
msWMI-UnknownRangeParam objects
msWMI-UnknownRangeParam
{b82ac26b-c6db-4098-92c6-49c18a3336e1}
msWMI-WMIGPO objects
msWMI-WMIGPO
{05630000-3927-4ede-bf27-ca91f275c26f}
NNTP Protocol objects
msExchProtocolCfgNNTPContainer
{94162eae-b09e-11d2-aa06-00c04f8eedd8}
NNTP Virtual Server objects
protocolCfgNNTPServer
{a8df74cb-c5ea-11d1-bbcb-0080c76670c0}
Notes Connector objects
msExchNotesConnector
{04c85e62-a981-11d2-a9ff-00c04f8eedd8}
Offline Address List objects
msExchOAB
{3686cdd4-a982-11d2-a9ff-00c04f8eedd8}
organization objects
organization
{bf967aa3-0de6-11d0-a285-00aa003049e2}
Organizational Unit objects
organizationalUnit
{bf967aa5-0de6-11d0-a285-00aa003049e2}
organizationalPerson objects
organizationalPerson
{bf967aa4-0de6-11d0-a285-00aa003049e2}
organizationalRole objects
organizationalRole
{a8df74bf-c5ea-11d1-bbcb-0080c76670c0}
packageRegistration objects
packageRegistration
{bf967aa6-0de6-11d0-a285-00aa003049e2}
person objects
person
{bf967aa7-0de6-11d0-a285-00aa003049e2}
physicalLocation objects
physicalLocation
{b7b13122-b82e-11d0-afee-0000f80367c1}
pKIEnrollmentService objects
pKIEnrollmentService
{ee4aa692-3bba-11d2-90cc-00c04fd91ab1}
POP Policy objects
msExchProtocolCfgPOPPolicy
{35be884c-a982-11d2-a9ff-00c04f8eedd8}
POP Protocol objects
msExchProtocolCfgPOPContainer
{93f99276-b09e-11d2-aa06-00c04f8eedd8}
POP Sessions objects
msExchProtocolCfgPOPSessions
{99f58676-12e8-11d3-aa58-00c04f8eedd8}
POP Virtual Server objects
protocolCfgPOPServer
{a8df74ce-c5ea-11d1-bbcb-0080c76670c0}
Printer objects
printQueue
{bf967aa8-0de6-11d0-a285-00aa003049e2}
Private Information Store objects
msExchPrivateMDB
{36145cf4-a982-11d2-a9ff-00c04f8eedd8}
Private Information Store Policy objects
msExchPrivateMDBPolicy
{35db2484-a982-11d2-a9ff-00c04f8eedd8}
protocolCfg objects
protocolCfg
{a8df74c0-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgHTTP objects
protocolCfgHTTP
{a8df74c1-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgIMAP objects
protocolCfgIMAP
{a8df74c4-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgLDAP objects
protocolCfgLDAP
{a8df74c7-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgNNTP objects
protocolCfgNNTP
{a8df74ca-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgPOP objects
protocolCfgPOP
{a8df74cd-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgShared objects
protocolCfgShared
{a8df74d0-c5ea-11d1-bbcb-0080c76670c0}
protocolCfgSMTP objects
protocolCfgSMTP
{33f98980-a982-11d2-a9ff-00c04f8eedd8}
Public Folder objects
publicFolder
{f0f8ffac-1191-11d0-a060-00aa006c33ed}
Public Folder Top Level Hierarchy objects
msExchPFTree
{364d9564-a982-11d2-a9ff-00c04f8eedd8}
Public Information Store objects
msExchPublicMDB
{3568b3a4-a982-11d2-a9ff-00c04f8eedd8}
Public Information Store Policy objects
msExchPublicMDBPolicy
{354c176c-a982-11d2-a9ff-00c04f8eedd8}
Query Policy objects
queryPolicy
{83cc7075-cca7-11d0-afff-0000f80367c1}
RAS MTA Transport Stack objects
rASStack
{a8df74d3-c5ea-11d1-bbcb-0080c76670c0}
Recipient Policies objects
msExchRecipientPolicyContainer
{e32977d2-1d31-11d3-aa5e-00c04f8eedd8}
Recipient Policy objects
msExchRecipientPolicy
{e32977d8-1d31-11d3-aa5e-00c04f8eedd8}
Recipient Update Service objects
msExchAddressListService
{e6a2c260-a980-11d2-a9ff-00c04f8eedd8}
Remote Storage Service objects
remoteStorageServicePoint
{2a39c5bd-8960-11d1-aebc-0000f80367c1}
remoteDXA objects
remoteDXA
{a8df74d5-c5ea-11d1-bbcb-0080c76670c0}
remoteMailRecipient objects
remoteMailRecipient
{bf967aa9-0de6-11d0-a285-00aa003049e2}
Replication Connectors objects
msExchReplicationConnectorContainer
{99f5867e-12e8-11d3-aa58-00c04f8eedd8}
residentialPerson objects
residentialPerson
{a8df74d6-c5ea-11d1-bbcb-0080c76670c0}
rFC822LocalPart objects
rFC822LocalPart
{b93e3a78-cbae-485e-a07b-5ef4ae505686}
rIDManager objects
rIDManager
{6617188d-8f3c-11d0-afda-00c04fd930c9}
rIDSet objects
rIDSet
{7bfdcb89-4807-11d1-a9c3-0000f80367c1}
room objects
room
{7860e5d2-c8b0-4cbb-bd45-d9455beb9206}
Routing Group Connector objects
msExchRoutingGroupConnector
{899e5b86-b09e-11d2-aa06-00c04f8eedd8}
Routing Group objects
msExchRoutingGroup
{35154156-a982-11d2-a9ff-00c04f8eedd8}
Routing Groups objects
msExchRoutingGroupContainer
{34de6b40-a982-11d2-a9ff-00c04f8eedd8}
RPC Services objects
rpcContainer
{80212842-4bdc-11d1-a9c4-0000f80367c1}
rpcEntry objects
rpcEntry
{bf967aac-0de6-11d0-a285-00aa003049e2}
rpcGroup objects
rpcGroup
{88611bdf-8cf4-11d0-afda-00c04fd930c9}
rpcProfile objects
rpcProfile
{88611be1-8cf4-11d0-afda-00c04fd930c9}
rpcProfileElement objects
rpcProfileElement
{f29653cf-7ad0-11d0-afd6-00c04fd930c9}
rpcServer objects
rpcServer
{88611be0-8cf4-11d0-afda-00c04fd930c9}
rpcServerElement objects
rpcServerElement
{f29653d0-7ad0-11d0-afd6-00c04fd930c9}
rRASAdministrationConnectionPoint objects
rRASAdministrationConnectionPoint
{2a39c5be-8960-11d1-aebc-0000f80367c1}
rRASAdministrationDictionary objects
rRASAdministrationDictionary
{f39b98ae-938d-11d1-aebd-0000f80367c1}
samDomain objects
samDomain
{bf967a90-0de6-11d0-a285-00aa003049e2}
samDomainBase objects
samDomainBase
{bf967a91-0de6-11d0-a285-00aa003049e2>
samServer objects
samServer
{bf967aad-0de6-11d0-a285-00aa003049e2}
Schedule+ Free/Busy Connector objects
msExchSchedulePlusConnector
{b1fce946-1d44-11d3-aa5e-00c04f8eedd8}
Schema Attribute objects
attributeSchema
{bf967a80-0de6-11d0-a285-00aa003049e2}
Schema Container objects
dMD
{bf967a8f-0de6-11d0-a285-00aa003049e2}
Schema Object objects
classSchema
{bf967a83-0de6-11d0-a285-00aa003049e2}
secret objects
secret
{bf967aae-0de6-11d0-a285-00aa003049e2}
securityObject objects
securityObject
{bf967aaf-0de6-11d0-a285-00aa003049e2}
securityPrincipal objects
securityPrincipal
{bf967ab0-0de6-11d0-a285-00aa003049e2}
Server LDAP Protocol objects
protocolCfgLDAPServer
{a8df74c8-c5ea-11d1-bbcb-0080c76670c0}
Server objects
server
{bf967a92-0de6-11d0-a285-00aa003049e2}
Server Protocols objects
protocolCfgSharedServer
{a8df74d1-c5ea-11d1-bbcb-0080c76670c0}
Servers Container objects
serversContainer
{f780acc0-56f0-11d1-a9c6-0000f80367c1}
Service objects
serviceAdministrationPoint
{b7b13123-b82e-11d0-afee-0000f80367c1}
serviceClass objects
serviceClass
{bf967ab1-0de6-11d0-a285-00aa003049e2}
serviceConnectionPoint objects
serviceConnectionPoint
{28630ec1-41d5-11d1-a9c1-0000f80367c1}
serviceInstance objects
serviceInstance
{bf967ab2-0de6-11d0-a285-00aa003049e2}
Shared Folder objects
volume
{bf967abb-0de6-11d0-a285-00aa003049e2}
simpleSecurityObject objects
simpleSecurityObject
{5fe69b0b-e146-4f15-b0ab-c1e5d488e094}
Site Addressing objects
siteAddressing
{a8df74d9-c5ea-11d1-bbcb-0080c76670c0}
Site Connector objects
siteConnector
{a8df74da-c5ea-11d1-bbcb-0080c76670c0}
Site HTTP Protocol objects
protocolCfgHTTPSite
{a8df74c3-c5ea-11d1-bbcb-0080c76670c0}
Site IMAP Protocol objects
protocolCfgIMAPSite
{a8df74c6-c5ea-11d1-bbcb-0080c76670c0}
Site LDAP Protocol objects
protocolCfgLDAPSite
{a8df74c9-c5ea-11d1-bbcb-0080c76670c0}
Site Link Bridge objects
siteLinkBridge
{d50c2cdf-8951-11d1-aebc-0000f80367c1}
Site Link objects
siteLink
{d50c2cde-8951-11d1-aebc-0000f80367c1}
Site MTA Configuration objects
mTACfg
{a8df74a8-c5ea-11d1-bbcb-0080c76670c0}
Site NNTP Protocol objects
protocolCfgNNTPSite
{a8df74cc-c5ea-11d1-bbcb-0080c76670c0}
Site objects
site
{bf967ab3-0de6-11d0-a285-00aa003049e2}
Site POP Protocol objects
protocolCfgPOPSite
{a8df74cf-c5ea-11d1-bbcb-0080c76670c0}
Site Protocols objects
protocolCfgSharedSite
{a8df74d2-c5ea-11d1-bbcb-0080c76670c0}
Site Replication Service objects
msExchSiteReplicationService
{99f5867b-12e8-11d3-aa58-00c04f8eedd8}
Site Settings objects
nTDSSiteSettings
{19195a5d-6da0-11d0-afd3-00c04fd930c9}
Site SMTP Protocol objects
protocolCfgSMTPSite
{32f0e47a-a982-11d2-a9ff-00c04f8eedd8}
Sites Container objects
sitesContainer
{7a4117da-cd67-11d0-afff-0000f80367c1}
SMTP Connector objects
msExchRoutingSMTPConnector
{89baf7be-b09e-11d2-aa06-00c04f8eedd8}
SMTP Domain objects
protocolCfgSMTPDomain
{33d82894-a982-11d2-a9ff-00c04f8eedd8}
SMTP Domains objects
protocolCfgSMTPDomainContainer
{33bb85c-a982-11d2-a9ff-00c04f8eedd8}
SMTP Policy objects
msExchProtccolCfgSMTPPolicy
{359f89ba-a982-11d2-a9ff-00c04f8eedd8}
SMTP Protocol objects
msExchProtocolCfgSMTPContainer
{93bb9552-b09e-11d2-aa06-00c04f8eedd8}
SMTP Routing Sources objects
protocolCfgSMTPRoutingSources
{3397c916-a982-11d2-a9ff-00c04f8eedd8}
SMTP Sessions objects
protocolCfgSMTPSessions
{8ef628c6-b093-11d2-aa06-00c04f8eedd8}
SMTP Turf List objects
msExchSMTPTurfList
{0b836da5-3b20-11d3-aa6f-00c04f8eedd8}
SMTP Virtual Server objects
protocolCfgSMTPServer
{3378ca84-a982-11d2-a9ff-00c04f8eedd8}
Storage Group objects
msExchStorageGroup
{3435244a-a982-11d2-a9ff-00c04f8eedd8}
storage objects
storage
{bf967ab5-0de6-11d0-a285-00aa003049e2}
Subnet objects
subnet
{b7b13124-b82e-11d0-afee-0000f80367c1}
Subnets Container objects
subnetContainer
{b7b13125-b82e-11d0-afee-0000f80367c1}
subSchema objects
subSchema
{5a8b3261-c38d-11d1-bbc9-0080c76670c0}
System Attendant objects
exchangeAdminService
{a8df74b2-c5ea-11d1-bbcb-0080c76670c0}
System Policies objects
msExchSystemPolicyContainer
{32412a7a-22af-479c-a444-624c0137122e}
System Policy objects
msExchSystemPolicy
{ba085a33-8807-4c6c-9522-2cf5a2a5e9c2}
TCP (RFC1006) MTA Transport Stack objects
rFC1006Stack
{a8df74d7-c5ea-11d1-bbcb-0080c76670c0}
TCP (RFC1006) X.400 Connector objects
rFC1006X400Link
{a8df74d8-c5ea-11d1-bbcb-0080c76670c0}
top objects
top
{bf967ab7-0de6-11d0-a285-00aa003049e2}
TP4 MTA Transport Stack objects
tP4Stack
{a8df74db-c5ea-11d1-bbcb-0080c76670c0}
TP4 X.400 Connector objects
tP4X400Link
{a8df74dc-c5ea-11d1-bbcb-0080c76670c0}
transportStack objects
transportStack
{a8df74dd-c5ea-11d1-bbcb-0080c76670c0}
Trusted Domain objects
trustedDomain
{bf967ab8-0de6-11d0-a285-00aa003049e2}
typeLibrary objects
typeLibrary
{281416e2-1968-11d0-a28f-00aa003049e2}
User objects
user
{bf967aba-0de6-11d0-a285-00aa003049e2}
Video Conference Technology Provider objects
msExchIpConfContainer
{99f5866d-12e8-11d3-aa58-00c04f8eedd8}
Virtual Chat Network objects
msExchChatVirtualNetwork
{ea5ed15a-a980-11d2-a9ff-00c04f8eedd8}
X.25 MTA Transport Stack objects
x25Stack
{a8df74de-c5ea-11d1-bbcb-0080c76670c0}
X.25 X.400 Connector objects
x25X400Link
{a8df74df-c5ea-11d1-bbcb-0080c76670c0}
x400Link objects
x-400Link
{a8df74e0-c5ea-11d1-bbcb-0080c76670c0}
Because ACE ObjectType deciphering logic could be confusing, Table 4.19 summarizes the logic to follow to decipher this property.
|
|
The table must be read from left to right, column by column. For instance, it should be read as follows:
When the ACE Type property contains one of the values listed below ... (column 1)
ADS_ACETYPE_ACCESS_ALLOWED_OBJECT ADS_ACETYPE_ACCESS_DENIED_OBJECT ADS_ACETYPE_SYSTEM_AUDIT_OBEJECT
. . . and if the "ACE AccessMask" property contains ... (column 2)
ADS_RIGHT_DS_READ_PROP (0x10)
... then is that an Extended Right? (column 3)
Yes!
In such a case, the GUID number in the ACE ObjectType value refers . . . (column 4)
-
the GUID number from the rightsGUID attribute of the controlAccessRight object,
-
... which contains a validAccesses value of. . . (column 5)
ADS_RIGHT_DS_READ_PROP Or ADS_RIGHT_DS_WRITE_PROP (0x30)
To customize the three Extended Rights samples shown in Figure 4.22, the following command lines must be used:
-
For the "Personal Information" Extended Right:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=LISSOIR Alain,CN=Users,DC=LissWare,DC=Net" 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 4: /ACEMask:ADS_RIGHT_DS_READ_PROP, 5: ADS_RIGHT_DS_WRITE_PROP 6: /ACEFlags:None 7: /ObjectType:{77B5B886-944A-11D1-AEBD-0000F80367C1} 8: /AddAce+ /ADSI+ -
For the "Send As" Extended Right:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=LISSOIR Alain,CN=Users,DC=LissWare,DC=Net" 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 4: /ACEMask:ADS_RIGHT_DS_CONTROL_ACCESS 5: /ACEFlags:None 6: /ObjectType:{AB721A54-1E2F-11D0-9819-00AA0040529B} 7: /AddAce+ /ADSI+ -
For the "Add/Remove self as member" Extended Right:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Enterprise Admins,CN=Users,DC=LissWare,DC=Net" 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 4: /ACEMask:ADS_RIGHT_DS_SELF 5: /ACEFlags:ADS_ACEFLAG_CONTAINER_INHERIT_ACE 6: /ObjectType:{BF9679C0-0DE6-11D0-A285-00AA003049E2} 7: /AddAce+ /ADSI+
To customize the ACE inheritance shown in Figure 4.28 ("The ACE ObjectType property used to grant or deny the creation or deletion of objects from a particular class"), the following command line must be used:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Users,DC=LissWare,DC=Net" 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 4: /ACEMask:ADS_RIGHT_DS_CREATE_CHILD, 5: ADS_RIGHT_DS_DELETE_CHILD 6: /ACEFlags:ADS_ACEFLAG_CONTAINER_INHERIT_ACE 7: /ObjectType:{35BE884C-A982-11D2-A9FF-00C04F8EEDD8} 8: /AddAce+ /ADSI+ Since we manipulate a security descriptor coming from Active Directory, the ADSI security descriptor access method is used. The /ADSI+ switch is specified for every command line. Note that the WMI access method can also be used for this example, since we manage the DACL of the security descriptor. However, as we have seen in section 4.4.4 ("Which access technique to use? Which security descriptor representation do we obtain?"), the SACL access of an Active Directory security descriptor via WMI is not supported.
The command-line input is always based on the various deciphering outputs previously seen and the content of:
-
Table 4.14, "The Active Directory Object ACE AccessMask Values—Standard View"
-
Table 4.15, "The Active Directory Object ACE AccessMask Values—Advanced View"
-
Table 4.16, "The Active Directory Objects ACE Flags Values"
-
Table 4.17, "Extended Rights Available in Active Directory under Windows Server 2003 (Exchange 2000 Extended Rights Included)"
-
Table 4.18, "The schemaIDGUID GUID Number with Its Class Names"
-
Table 4.19, "Summary of the GUID Number Origins for the ACE ObjectType Property"
4.11.4.5.3.2 Understanding the ACE InheritedObjectType property
As discussed when we examined the ACE Flags property (section 4.11.4.3), objects contained in subcontainers can inherit ACEs. However, with Active Directory, there are situations where only a specific class of object will inherit an ACE. Figure 4.29 shows an example of this configuration.
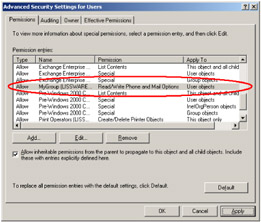
Figure 4.29: ACE Inheritance to a specific object class.
The group "MyGroup" is granted to read and write the phone and mail options on all user objects. If we decipher the ACE, we obtain the following result:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Users,DC=LissWare,DC=Net" /Decipher+ /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading AD object security descriptor via ADSI from 'LDAP:// CN=Users,DC=LissWareNET,...'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. LISSWARENET\Domain Admins 9: | Group: ................................. LISSWARENET\Domain Admins 10: | Revision: .............................. 1 11: | Control: ............................... &h8C14 ..: 17: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 18: ||+- ADSI ACE ------------------------------------------------------------------------------ ..: 33: ||+----------------------------------------------------------------------------------------- ...: 121: ||+- ADSI ACE ------------------------------------------------------------------------------ 122: ||| AccessMask: .......................... &h30 123: ADS_RIGHT_DS_READ_PROP 124: ADS_RIGHT_DS_WRITE_PROP 125: ||| AceFlags: ............................ &hA 126: ADS_ACEFLAG_CONTAINER_INHERIT_ACE 127: ADS_ACEFLAG_INHERIT_ONLY_ACE 128: ADS_ACEFLAG_VALID_INHERIT_FLAGS 129: ||| AceType: ............................. &h5 130: ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 131: ||| AceFlagType: ......................... &h3 132: ADS_FLAG_OBJECT_TYPE_PRESENT 133: ADS_FLAG_INHERITED_OBJECT_TYPE_PRESENT 134: ||| ObjectType: .......................... {E45795B2-9455-11D1-AEBD-0000F80367C1} 135: ||| InheritedObjectType: ................. {BF967ABA-0DE6-11D0-A285-00AA003049E2} 136: ||| Trustee: ............................. LISSWARENET\MyGroup 137: ||+----------------------------------------------------------------------------------------- ...: 456: |+------------------------------------------------------------------------------------------ 457: +------------------------------------------------------------------------------------------- From line 121 through 137, the "Phone and Mail options" Extended Right is granted to the trustee "MyGroup" for read and write operations as:
-
The ACE Type has a value equal to ADS_ACETYPE_ACCESS_ALLOWED_OBJECT (line 130).
-
The ACE AccessMask has a value equal to ADS_RIGHT_DS_READ_PROP + ADS_RIGHT_DS_WRITE_PROP (lines 123 and 124).
-
The ACE ObjectType property has a GUID number corresponding to the "Phone and Mail options" Extended Right (line 134). Table 4.17 lists the Extended Rights GUID numbers with their corresponding display names.
-
Because it applies to the user objects only, the ACE InheritedObjectType property is set with the GUID number stored in the schemaIDGUID of the user class (line 135). To find the name of the class with the GUID number, refer to Table 4.18.
To customize this inheritance with the script, as shown in Figure 4.29, the following command line must be used:
1: C:\>WMIManageSD.Wsf /ADObject:"CN=Users,DC=LissWare,DC=Net" 2: /Trustee:LissWareNET\MyGroup 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED_OBJECT 4: /ACEMask:ADS_RIGHT_DS_READ_PROP, 5: ADS_RIGHT_DS_WRITE_PROP 6: /ACEFlags:ADS_ACEFLAG_CONTAINER_INHERIT_ACE, 7: ADS_ACEFLAG_INHERIT_ONLY_ACE 8: /ObjectType:{E45795B2-9455-11D1-AEBD-0000F80367C1} 9: /InheritedObjectType:{BF967ABA-0DE6-11D0-A285-00AA003049E2} 10: /AddAce+ /ADSI+ As usual, the switch parameters can be taken from a deciphering output or from the various tables related to the Active Directory security descriptors (Tables 4.14 through 4.19).
Before moving to the next security descriptor type, it is interesting to note that the script offers limited support about the GUID numbers management. Actually, it is possible to extend the script in such a way that it accepts the Extended Rights and Active Directory classes display names instead of those ugly GUID numbers. Based on these names, it is always possible to retrieve their corresponding GUID numbers. This will certainly make the script easier to use. However, this logic must be implemented by performing some LDAP search operations on top of ADSI. Since we are focusing on the WMI scripting techniques, this ADSI scripting logic is beyond the scope of this book. However, this could represent a nice extension to have for a day-to-day use of the script.
4.11.4.5.4 The Exchange 2000 mailbox ACE AccessMask property
When an Exchange 2000 mailbox is created, the mailbox security descriptor is initially stored in the msExchMailboxSecurityDescriptor attribute of the Active Directory user object. The msExchMailboxSecurityDescriptor attribute can be accessed via ADSI or WMI, but, again, the ACE AccessMask deciphering technique is independent of the access method and the object model representing the security descriptor. Even if the mailbox security descriptor is stored in Active Directory, the deciphering technique is much simpler than the deciphering technique used for an Active Directory object security descriptor. Sample 4.38 uses the same logic as any other standard rights but with a different set of flags.
Sample 4.38: Deciphering the ACE AccessMask property for Exchange 2000 mailboxes
...: ...: ...: 319: 320: Case cExchange2000MailboxViaWMI, cExchange2000MailboxViaADSI, _ 321: cExchange2000MailboxViaCDOEXM 322: If (intACEMask And E2K_MB_FULL_MB_ACCESS) Then 323: strTemp = strTemp & "," & "E2K_MB_FULL_MB_ACCESS" 324: End If 325: If (intACEMask And E2K_MB_SEND_AS) Then 326: strTemp = strTemp & "," & "E2K_MB_SEND_AS" 327: End If 328: If (intACEMask And E2K_MB_EXTERNAL_ACCOUNT) Then 329: strTemp = strTemp & "," & "E2K_MB_EXTERNAL_ACCOUNT" 330: End If 331: If (intACEMask And E2K_MB_DELETE) Then 332: strTemp = strTemp & "," & "E2K_MB_DELETE" 333: End If 334: If (intACEMask And E2K_MB_READ_PERMISSIONS) Then 335: strTemp = strTemp & "," & "E2K_MB_READ_PERMISSIONS" 336: End If 337: If (intACEMask And E2K_MB_CHANGE_PERMISSIONS) Then 338: strTemp = strTemp & "," & "E2K_MB_CHANGE_PERMISSIONS" 339: End If 340: If (intACEMask And E2K_MB_TAKE_OWNERSHIP) Then 341: strTemp = strTemp & "," & "E2K_MB_TAKE_OWNERSHIP" 342: End If 343: ...: ...: ...:
The Exchange 2000 mailbox flags with their corresponding user interface settings are summarized in Table 4.20.
| Granted & denied rights | Standard View | ||||||
|---|---|---|---|---|---|---|---|
| Delete Mailbox storage | Read permissions | Change permissions | Take ownership | Full mailbox access | Associated external account | ||
| ACEType | |||||||
| ADS_ACETYPE_ACCESS_ALLOWED | 0x0 | X | X | X | X | X | X |
| ADS_ACETYPE_ACCESS_DENIED | 0x1 | ||||||
| ADS_ACETYPE_SYSTEM_AUDIT | 0x2 | ||||||
| ACEMask | |||||||
| E2K_MB_CHANGE_PERMISSIONS | 0x40000 | X | |||||
| E2K_MB_DELETE | 0x10000 | X | |||||
| E2K_MB_EXTERNAL_ACCOUNT | 0x4 | X | |||||
| E2K_MB_FULL_MB_ACCESS | 0x1 | X | X | ||||
| E2K_MB_READ_PERMISSIONS | 0x20000 | X | |||||
| E2K_MB_SEND_AS | 0x2 | ||||||
| E2K_MB_TAKE_OWNERSHIP | 0x80000 | X | |||||
Table 4.21 lists the ACE Flags to define ACE inheritance for an Exchange 2000 mailbox.
| Inheritance & Audit | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| This object only | Inherit only | This object and subcontainers | This object and children objects | Subcontainers only | Children objects only | This object, subcontainers, and children objects | Subcontainers and children objects | Audit Successful access | Audit Failed access | ||
| ACEFlags | |||||||||||
| NONE | 0x0 | X | |||||||||
| ADS_ACEFLAG_OBJECT_INHERIT_ACE [2] | 0x1 | X | X | X | X | ||||||
| ADS_ACEFLAG_CONTAINER_INHERIT_ACE[2] | 0x2 | X | X | X | X | ||||||
| ADS_ACEFLAG_INHERIT_ONLY_ACE | 0x8 | X | X | X | X | ||||||
| ADS_ACEFLAG_INHERITED_ACE [1] | 0x10 | ||||||||||
| ADS_ACEFLAG_NO_PROPAGATE_INHERIT_ACE | 0x4 | ||||||||||
| ADS_ACEFLAG_VALID_INHERIT_FLAGS[1] | 0x1F | X | X | X | X | X | X | X | |||
| ADS_ACEFLAG_SUCCESSFUL_ACCESS | 0x40 | X | |||||||||
| ADS_ACEFLAG_FAILED_ACCESS | 0x80 | X | |||||||||
|
[2]These two values are not defined in the ADS_ACEFLAG_ENUM. The ADS_ACEFLAG_CONTAINER_INHERIT_ACE is actually defined as the ADS_ACEFLAG_INHERIT_ACE value (0x2). The ADS_ACEFLAG_OBJECT_INHERIT_ACE value is not defined but the 0x1 value is required to correctly decipher the Exchange 2000 ACE inheritance.
[1]can only be set by the system. | |||||||||||
The mailbox security settings shown in Figure 4.30 can be deciphered with the following command line. The output would be as follows:
1: C:\>WMIManageSD.Wsf /E2KMailbox:"CN=LISSOIR Alain,CN=Users,..." /Decipher* /ADSI+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading Exchange 2000 mailbox security descriptor via ADSI from 'LDAP://CN=LISSOIR...'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. LISSWARENET\Alain.Lissoir 9: | Group: ................................. LISSWARENET\Alain.Lissoir 10: | Revision: .............................. 1 11: | Control: ............................... &h8004 12: SE_DACL_PRESENT 13: SE_SELF_RELATIVE 14: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 15: ||+- ADSI ACE ------------------------------------------------------------------------------ 16: ||| AccessMask: .......................... &h20003 17: E2K_MB_FULL_MB_ACCESS 18: E2K_MB_SEND_AS 19: E2K_MB_READ_PERMISSIONS 20: ||| AceFlags: ............................ &h2 21: ADS_ACEFLAG_CONTAINER_INHERIT_ACE 22: ADS_ACEFLAG_VALID_INHERIT_FLAGS 23: ||| AceType: ............................. &h0 24: ADS_ACETYPE_ACCESS_ALLOWED 25: ||| AceFlagType: ......................... &h0 26: ||| Trustee: ............................. NT AUTHORITY\SELF 27: ||+----------------------------------------------------------------------------------------- 28: |+------------------------------------------------------------------------------------------ 29: +-------------------------------------------------------------------------------------------
Figure 4.30: The default Exchange 2000 mailbox security just after creation from the MMC.
Lines 15 through 26 show the ACE configuration for the security settings shown in Figure 4.30. The ACE AccessMask is composed of the flags listed in Table 4.20, while the ACE Flags property is made up of the flags from Table 4.21.
To customize the Exchange 2000 security descriptor, as shown in Figure 4.30, the following command line can be used:
1: C:\>WMIManageSD.Wsf /E2KMailbox:"CN=LISSOIR Alain,CN=Users,DC=LissWare,DC=Net" 2: /Trustee:"NT AUTHORITY\SELF" 3: /ACEType:ADS_ACETYPE_ACCESS_ALLOWED 4: /ACEMask:E2K_MB_FULL_MB_ACCESS, 5: E2K_MB_SEND_AS, 6: E2K_MB_READ_PERMISSIONS 7: /ACEFlags:ADS_ACEFLAG_CONTAINER_INHERIT_ACE 8: /AddAce+ /ADSI+
It is important to note that the script sets the security on the mailbox. It doesn't create a mail-enabled or mailbox-enabled Active Directory object. In this example, we use the ADSI security descriptor access method. However, as we have seen in section 4.4.4 ("Which access technique to use? Which security descriptor representation do we obtain?"), the WMI and CDOEXM method can be used as well. The access method depends on certain conditions, which we will discuss in section 4.13.4 ("Updating Exchange 2000 mailbox").
4.11.4.5.5 The registry key ACE AccessMask property
The registry ACE AccessMask deciphering technique is no more complicated than any other ACE AccessMask. It follows the same coding and deciphering rules as seen previously. As usual, the set of flags to use to decipher the ACE AccessMask is dedicated to the registry. Table 4.22 summarizes the various user interface settings possible, with their corresponding values.
| Granted & denied rights | Standard View | Advanced View | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Read | Full Control | Query Value | Set Value | Create Subkey | Enumerate Subkeys | Notify | Create Link | Delete | Write DAC | Write Owner | Read Control | ||
| ACEType | |||||||||||||
| ADS_ACETYPE_ACCESS_ALLOWED | 0x0 0x1 | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] | X[1] |
| ADS_ACETYPE_ACCESS_DENIED | |||||||||||||
| ADS_ACETYPE_SYSTEM_AUDIT | 0x2 | ||||||||||||
| ACEMask | |||||||||||||
| REG_GENERIC_FULL_CONTROL | 0xF003F | X | |||||||||||
| REG_GENERIC_READ | 0x20019 | X | |||||||||||
| REG_CREATE_LINK | 0x20 | X | X | ||||||||||
| REG_CREATE_SUBKEYS | 0x4 | X | X | ||||||||||
| REG_DELETE | 0x10000 | X | X | ||||||||||
| REG_ENUMERATE_SUBKEYS | 0x8 | X | X | X | |||||||||
| REG_NOTIFY | 0x10 | X | X | X | |||||||||
| REG_QUERY_VALUE | 0x1 | X | X | X | |||||||||
| REG_READ_CONTROL | 0x20000 | X | X | X | |||||||||
| REG_SET_VALUE | 0x2 | X | X | ||||||||||
| REG_WRITE_DAC | 0x40000 | X | X | ||||||||||
| REG_WRITE_OWNER | 0x80000 | X | X | ||||||||||
|
[1]Windows NT 4.0/Windows 2000: The ADsSecurity.DLL from the ADSI Resource Kit does not retrieve the SACL object from the registry. Windows XP/Windows Server 2003: Unfortunately, a bug in the ADsSecurityUtility interface prevents the retrieval of the SystemACL. Microsoft doesn't plan to fix this bug in the RTM code for timing issues. WMI offers an acceptable work-around for file and folders only. For the registry key, there is no work-around available unless you use the UserRight.Control developed to work around this problem. (See section 4.7.1.2, "Retrieving file and folder security descriptors with ADSI.") | |||||||||||||
Table 4.23 shows the ACE Flags used to control the ACE inheritance in a registry hive.
| Inheritance | ||||
|---|---|---|---|---|
| This key only | This key and subkeys | Subkeys only | ||
| ACEFIags | ||||
| NONE | 0x0 | X | ||
| CONTAINER_INHERIT_ACE | 0x2 | X | X | |
| INHERIT_ONLY_ACE | 0x8 | X | ||
Based on the flags of Table 4.22, Sample 4.39 deciphers the ACE AccessMask property. There is nothing new to explain about the logic, since the coding technique remains the same.
Sample 4.39: Deciphering the ACE AccessMask property for registry keys
...: ...: ...: 343: 344: Case cRegistryViaADSI 345: If (intACEMask = REG_GENERIC_FULL_CONTROL) Then 346: strTemp = strTemp & "," & "(REG_GENERIC_FULL_CONTROL)" 347: End If 348: If (intACEMask = REG_GENERIC_READ) Then 349: strTemp = strTemp & "," & "(REG_GENERIC_READ)" 350: End If 351: 352: If (intACEMask And REG_QUERY_VALUE) Then 353: strTemp = strTemp & "," & "REG_QUERY_VALUE" 354: End If 355: If (intACEMask And REG_SET_VALUE) Then 356: strTemp = strTemp & "," & "REG_SET_VALUE" 357: End If 358: If (intACEMask And REG_CREATE_SUBKEYS) Then 359: strTemp = strTemp & "," & "REG_CREATE_SUBKEYS" 360: End If ...: 379: If (intACEMask And REG_WRITE_OWNER) Then 380: strTemp = strTemp & "," & "REG_WRITE_OWNER" 381: End If 382: ...: ...: ...:
If we take the configuration settings of Figure 4.31, the script output obtained is as follows:
1: C:\>WMIManageSD.Wsf /RegistryKey:HKLM\SYSTEM\CurrentControlSet\Services\SNMP /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading registry security descriptor via ADSI from 'HKLM\SYSTEM\CurrentContr...'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. NT AUTHORITY\SYSTEM 10: | Revision: .............................. 1 11: | Control: ............................... &h8404 12: SE_DACL_PRESENT 13: SE_DACL_AUTO_INHERITED 14: SE_SELF_RELATIVE 15: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 16: ||+- ADSI ACE ------------------------------------------------------------------------------ 17: ||| AccessMask: .......................... &h30019 18: REG_QUERY_VALUE 19: REG_ENUMERATE_SUBKEYS 20: REG_NOTIFY 21: REG_DELETE 22: REG_READ_CONTROL 23: ||| AceFlags: ............................ &h2 24: CONTAINER_INHERIT_ACE 25: ||| AceType: ............................. &h0 26: ACCESS_ALLOWED_ACE_TYPE 27: ||| AceFlagType: ......................... &h0 28: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 29: ||+----------------------------------------------------------------------------------------- ...: 153: |+------------------------------------------------------------------------------------------ 154: +-------------------------------------------------------------------------------------------
Figure 4.31: The registry hive security descriptor user interface.
The highlighted trustee in Figure 4.31 has a full read access to the registry hive. It is also able to delete registry keys below the selected hive. The ACE is deciphered from line 16 through 29 with the flag values of Tables 4.22 and 4.23. To configure the same ACE with the WMIManageSD.Wsf script, the following command line must be used:
1: C:\>WMIManageSD.Wsf /RegistryKey:HKLM\SYSTEM\CurrentControlSet\Services\SNMP 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ACCESS_ALLOWED_ACE_TYPE 4: /ACEMask:REG_QUERY_VALUE, 5: REG_ENUMERATE_SUBKEYS, 6: REG_NOTIFY, 7: REG_DELETE, 8: REG_READ_CONTROL 9: /ACEFlags:CONTAINER_INHERIT_ACE 10: /AddAce+ /ADSI+
The only access method available to read and update the security descriptor is exposed by ADSI. Therefore, the /ADSI+ switch must be specified in this example.
4.11.4.5.6 The CIM repository namespace ACE AccessMask property
Deciphering the ACE AccessMask of a CIM repository namespace is the same as deciphering any other ACE AccessMask. Only the flag values are different. Table 4.24 lists the possible configuration settings.
| Granted & denied rights | Advanced View | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Execute methods | Full Write | Partial Write | Provider Write | Enable Account | Remote Enable | Read Security | Edit Security | ||
| ACEType | |||||||||
| ADS_ACETYPE_ACCESS_ALLOWED | 0x0 0x1 | X | X | X | X | X | X | X | X |
| ADS_CETYPE_ACCESS_DENIED | |||||||||
| ADS_ACETYPE_SYSTEM_AUDIT | 0x2 | N/A [1] | |||||||
| ACEMask | |||||||||
| WBEM_ENABLE | 0x1 | X | |||||||
| WBEM_FULL_WRITE_REP | 0x4 | X | |||||||
| WBEM_METHOD_EXECUTE | 0x2 | X | |||||||
| WBEM_PARTIAL_WRITE_REP | 0x8 | X | X | ||||||
| WBEM_READ__CONTROL | 0x20000 | X | |||||||
| WBEM_REMOTE_ACCESS | 0x20 | X | |||||||
| WBEM_WRITE_DAC | 0x40000 | X | |||||||
| WBEM_WRITE_PROVIDER | 0x10 | X | X | ||||||
|
[1]SACL is not supported in the WMI CIM repository. | |||||||||
Regarding the ACE Flags to configure the ACE inheritance, you can refer to Table 4.25.
| Inheritance | ||||
|---|---|---|---|---|
| This namespace only | This namespace and subnamespaces | Subnamespaces only | ||
| ACEFIags | ||||
| NONE | 01x01 X | |||
| CONTAINER INHERIT ACE | 0x2 | X | X | |
| INHERIT ONLY ACE | 0x8 | X | ||
As an example, Figure 4.32 shows the default security settings of the Root\CIMv2 namespace.
Figure 4.32: The Root\CIMv2 namespace security descriptor user interface.
By using the script, the DecipherACEMask() function executes the code segment shown in Sample 4.40.
Sample 4.40: Deciphering the ACE AccessMask property for CIM repository namespaces
...: ...: ...: 382: 383: Case cWMINameSpaceViaWMI 384: If (intACEMask And WBEM_ENABLE) Then 385: strTemp = strTemp & "," & "WBEM_ENABLE" 386: End If 387: If (intACEMask And WBEM_METHOD_EXECUTE) Then 388: strTemp = strTemp & "," & "WBEM_METHOD_EXECUTE" 389: End If 390: If (intACEMask And WBEM_FULL_WRITE_REP) Then 391: strTemp = strTemp & "," & "WBEM_FULL_WRITE_REP" 392: End If 393: If (intACEMask And WBEM_PARTIAL_WRITE_REP) Then 394: strTemp = strTemp & "," & "WBEM_PARTIAL_WRITE_REP" 395: End If 396: If (intACEMask And WBEM_WRITE_PROVIDER) Then 397: strTemp = strTemp & "," & "WBEM_WRITE_PROVIDER" 398: End If 399: If (intACEMask And WBEM_REMOTE_ACCESS) Then 400: strTemp = strTemp & "," & "WBEM_REMOTE_ACCESS" 401: End If 402: If (intACEMask And WBEM_WRITE_DAC) Then 403: strTemp = strTemp & "," & "WBEM_WRITE_DAC" 404: End If 405: If (intACEMask And WBEM_READ_CONTROL) Then 406: strTemp = strTemp & "," & "WBEM_READ_CONTROL" 407: End If 408: 409: Case cRegistryViaWMI, cWMINameSpaceViaADSI 410: 411: Case Else 412: 413: End Select 414: 415: DecipherACEMask = ConvertStringInArray (strTemp, ",") 416: 417:End Function
As a result, the right settings in Figure 4.32 are deciphered as follows:
1: C:\>WMIManageSD.Wsf /WMINameSpace:Root\CIMv2 /Decipher+ 2: Microsoft (R) Windows Script Host Version 5.6 3: Copyright (C) Microsoft Corporation 1996-2001. All rights reserved. 4: 5: Reading CIM repository namespace security descriptor via WMI from 'Root\CIMv2'. 6: 7: +- ADSI Security Descriptor ---------------------------------------------------------------- 8: | Owner: ................................. BUILTIN\Administrators 9: | Group: ................................. BUILTIN\Administrators 10: | Revision: .............................. 1 11: | Control: ............................... &h8004 12: SE_DACL_PRESENT 13: SE_SELF_RELATIVE 14: |+- ADSI DiscretionaryAcl ------------------------------------------------------------------ 15: ||+- ADSI ACE ------------------------------------------------------------------------------ 16: ||| AccessMask: .......................... &h1F 17: WBEM_ENABLE 18: WBEM_METHOD_EXECUTE 19: WBEM_FULL_WRITE_REP 20: WBEM_PARTIAL_WRITE_REP 21: WBEM_WRITE_PROVIDER 22: ||| AceFlags: ............................ &hA 23: CONTAINER_INHERIT_ACE 24: INHERIT_ONLY_ACE 25: ||| AceType: ............................. &h0 26: ACCESS_ALLOWED_ACE_TYPE 27: ||| AceFlagType: ......................... &h0 28: ||| Trustee: ............................. LISSWARENET\Alain.Lissoir 29: ||+----------------------------------------------------------------------------------------- ..: 61: |+------------------------------------------------------------------------------------------ 62: +-------------------------------------------------------------------------------------------
From line 15 through 29, the ACE for the highlighted trustee in Figure 4.32 is deciphered with the flags coming from Tables 4.24 and 4.25. To configure the same ACE with the WMIManageSD.Wsf script, the following command line must be used:
1: C:\>WMIManageSD.Wsf /WMINameSpace:Root\CIMv2 2: /Trustee:LissWareNET\Alain.Lissoir 3: /ACEType:ACCESS_ALLOWED_ACE_TYPE 4: /ACEMask:WBEM_ENABLE, 5: WBEM_METHOD_EXECUTE, 6: WBEM_FULL_WRITE_REP, 7: WBEM_PARTIAL_WRITE_REP, 8: WBEM_WRITE_PROVIDER 9: /ACEFlags:CONTAINER_INHERIT_ACE,INHERIT_ONLY_ACE 10: /AddAce+
The only access method available to read and update the security descriptor is exposed by WMI via the GetSD and SetSD methods of the __SystemSecurity singleton system class (see sections 4.7.6 and 4.13.6). Therefore, no /ADSI+ switch is specified in this example.
EAN: 2147483647
Pages: 82