Chapter3.DB2 Access and Security
Chapter 3. DB2 Access and Security
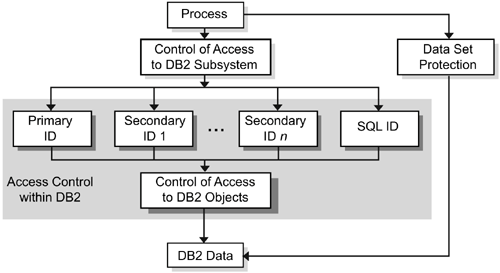
Security is an important consideration whenever data is stored in a relational database management system. This chapter discusses various methods of controlling data access. Access to data within DB2 is controlled at many levels, including subsystem, database objects, and application plan/packages. Authentication of user IDs and passwords is discussed. Groups of typical database users, such as database administrators, system administrators, transactional processing personnel, and decision support users are configured. Each of these database user types may require different access privileges. Another topic discussed is how to perform auditing, which allows you to monitor access and manipulation of data. Figure 3-1 shows several routes from a process to DB2 data, with controls on every route. Figure 3-1. DB2 data access control
|
EAN: 2147483647
Pages: 175