VPN Architecture
Several VPN network architectures are deployed by enterprise organizations for VPN services. The following list of remote access VPN network architectures is discussed in the following sections:
Firewall based
Black-box based
Router based
Remote-access based
Firewall-Based VPNs
With firewall-based VPNs, it is considered a safe presumption that a firewall will be used and placed at the network perimeter, as illustrated in Figure 16-3.
Figure 16-3. Firewall-Based VPN
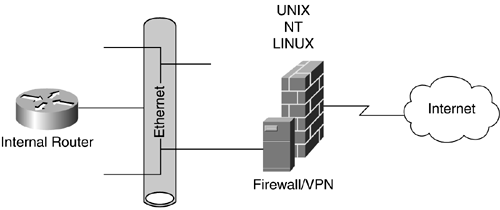
This presumption leads to a natural extension that this device also can support the VPN connections, providing a central point of management of both the firewall and network access security policies. A drawback to this combined firewall/VPN-access method is performance. On a single "box," a busy Internet circuit with multiple VPNs could overload the system.
Black-Box-Based VPNs
In the black-box scenario, a vendor offers just that, a black box; a device loaded with encryption software to create a VPN tunnel. Black-box VPN vendors should be supporting all three tunneling protocols PPTP, L2TP, and IPSec. Specific vendors need to be thoroughly researched, however, because they don't all provide the same level of tunneling protocol support.
The black-box VPN sits behind or with the firewall, as illustrated in Figure 16-4.
Figure 16-4. Black-Box-Based VPN
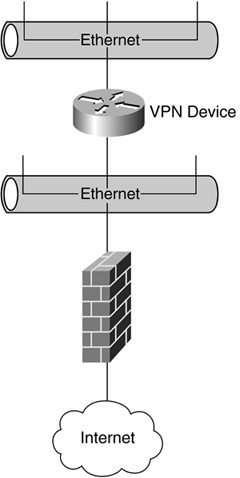
The firewall provides security to the organization, not the data, whereas the VPN device provides security to the data, but not the organization. If the firewall is in front of the VPN device, a rule-based policy on that firewall will need to be implemented.
Router-Based VPNs
Router-based VPNs are for an organization that has a large capital investment in routers and an experienced IT staff. Many router vendors support router-based VPN configurations. There are two ways to go about implementing router-based VPNs:
Software is added to the router to allow an encryption process to occur.
An external card from a third-party vendor is inserted into the router chassis. This method is designed to off-load the encryption process from the router CPU to the additional card.
Some vendors support hot swapping (replacing hardware) and redundancy (backup solutions), which are built into their router-based VPN products. Performance can be an issue with router-based VPNs because of the addition of an encryption process to the routing process; a heavier burden may be added to the router CPU, more than ever if the router is handling a large number of routes or implementing an intensive routing algorithm. Figure 16-5 illustrates a router-based VPN, where packets are encrypted from source to destination.
Figure 16-5. Router-Based VPN
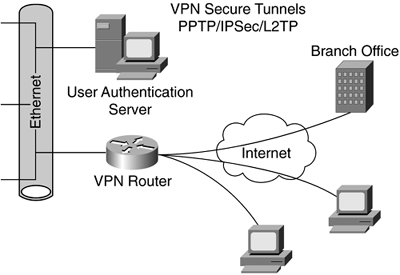
The drawback to a router-based VPN is security. Routers are considered to be poor at providing network security compared to a firewall. It is possible that an attacker will spoof traffic past the router, in turn fooling the firewall because the firewall will interpret these packets as originating from the other side of the VPN tunnel. This spoofing allows the attacker to gain access to services that are not visible from other locations on the Internet.
EAN: 2147483647
Pages: 269