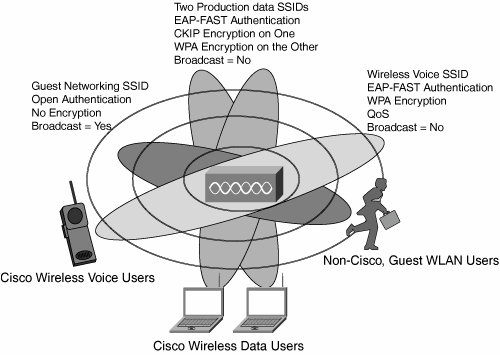
Enhanced Services
| Several enhanced services are available today, including support for wireless voice services and global guest networking. The enhanced services are facilitated by the use of several SSIDs and wireless VLANs, with differing security settings based upon the target devices. Figure 9-4 displays the various SSIDs used by Cisco to provide enhanced services, such as wireless voice and guest WLAN networking. Two production SSIDs are also used with different encryption methods: one with WPA and one with Cisco TKIP. This ensures that older devices that cannot support WPA are still provided with an SSID that they can use. Figure 9-4. SSID Architecture Wireless Voice ServicesWireless voice services are provided to Cisco employees by the use of the Cisco Wireless IP Phone 7920, a key component of the Cisco AVVID Wireless Solution and Cisco IP Communicator, a Windows-based Softphone application. The Cisco Wireless IP Phone 7920 is a WiFi-based (802.11b) phone that offers employees the ability to carry their extension with them as they move about Cisco premises. Many highly mobile users have adopted this device because it allows them to keep abreast of their voice communication services, even when away from their desk. Cisco IP Communicator is similar in concept to the Cisco Wireless IP Phone 7920, but it uses a virtual software-based IP phone that is set up and configured on the user's laptop. This allows users to access their extension, regardless of location and even when outside of Cisco sites by the use of VPN technology. Wireless voice services are provided by a dedicated SSID and wireless VLAN, configured with support for QoS (802.11e and WMM, or Wireless MultiMedia, protocols) and fast secure Layer 2 roaming (provided by Cisco Centralized Key Management [CCKM]). Wireless Guest NetworkingWireless Guest Networking services are provided by Cisco IT to enable visitors to access the Internet while at Cisco sites. The solution is based upon a combination of the existing WLAN infrastructure, the Cisco Building Broadband Services Manager (BBSM), and an internally developed web portal for employee self-service access code generation. All access points within the Cisco global network broadcast a guest networking SSID, which is configured with open authentication and no encryption to ensure that any client device can associate. When a visitor associates to the guest networking SSID and launches his browser, his HTTP session is automatically routed to a welcome page and portal. The visitor must read and accept the Cisco acceptable use policy and enter a preprovisioned access code. Upon validation, the visitor is then rerouted the Cisco demilitarized zone (DMZ) via a GRE tunnel to protect the production network. Effectively, from the guest's point of view, he is immediately provided with seamless Internet access, and he has no awareness of the intervening and transporting network between his location and the DMZ. Note DMZ is originally a military term denoting a semi-safe area around a base or border where military (and therefore enemy) activity is controlled. In the networking world, this term was adopted to describe the area of an enterprise network that lies between the Internet and the internal enterprise network. It is where the enterprise typically places its security apparatus and gateways to the Internet. A firewall or a router usually protects this zone. GRE is a tunneling protocol developed by Cisco Systems that can encapsulate a wide variety of protocol packet types inside IP tunnels. Access codes are required to satisfy the Cisco requirement for auditing and IT forensics. Were a visitor to undertake illegal or unfriendly activity, the behavior could be tracked back to a particular IP address, which in turn is associated with a particular access code. Because each access code is generated on an as-needed basis and associated with a particular visitor, Cisco security and legal departments can ascertain who was using a particular IP address at any particular time. Access control, and the use of access codes, is provided by the BBSM. However, to avoid unnecessary administrative overhead, Cisco IT developed an internal tool to allow Cisco users and staff to generate access codes for their own visitors. Effectively, Cisco has empowered its own staff with the ability to create access codes when they expect visitors. This removes unnecessary support burden from IT and administrative staff. Access codes are therefore available for creation at the internal intranet page hotspot.cisco.com. Any Cisco employee can access this page and, after authenticating oneself as a Cisco employee, generate one or more access codes. Figure 9-5 illustrates how a Cisco staff member can generate the access codes, which are in turn provisioned on the BBSM, which in turn acts as an access portal to the Internet for the guest. Figure 9-5. Cisco Guest Wireless Networking Solution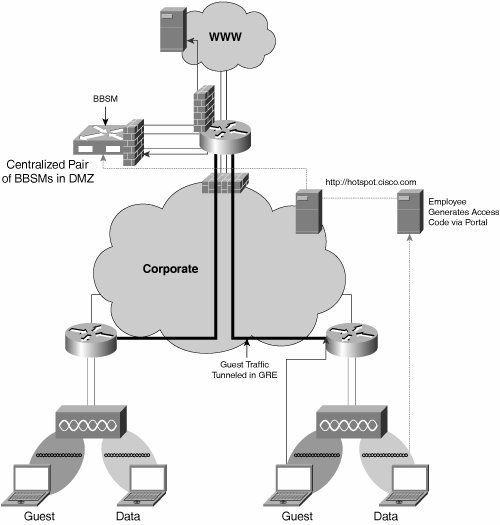 |
EAN: 2147483647
Pages: 163