Building a Secure WLAN
| This section provides guidelines for building a secure WLAN. These recommended practices are offered as tried and tested methodologies for addressing this challenging topic. Every enterprise comes with its own unique environment, infrastructure, and security challenges, but by following these suggestions and tailoring them to your specific needs, you can be sure that you have addressed the most common security issues encountered today. Trusted Versus Untrusted Wireless NetworksOne of your first decisions is whether your wireless network will be trusted or untrusted. This is an architectural issue, but it has a fundamental impact upon the security model you adopt. In the trusted model, you consider your WLAN to be an integral part of your intranet. The WLAN lies inside your secured fortress. In the untrusted model, you regard your WLAN as an extranet. The WLAN lies outside the secured perimeter of the organization. As such, you should make this decision very early in the planning or design phase of the PPDIOO lifecycle. Trusted WLANsTrusted wireless networks are fully integrated into the existing enterprise network. It is assumed that the integrity of the network is implicitly protected. WLAN security is placed at the network edge, where the clients or devices authenticate and the traffic is encrypted. From a security perspective, trusted wireless networks are the preferred type of deployment today. The advantages of a trusted WLAN include
Untrusted WLANsIn an untrusted wireless network, the assumption is that the network integrity is easily compromised. This assumption indicates that security does not exist or is incapable of providing necessary protection. Data in an untrusted WLAN is therefore considered "open," and hence there is the need to be explicit about security. The advantages of an untrusted WLAN include:
Define a Clear Security PostureA security posture is a framework of terms, protocols, standards, and policies that relate to protecting your wireless environment. It should at a minimum provide guidelines for
The critical steps of selecting an authentication mechanism and encryption strategy for your WLAN are discussed next. Note A common mistake when developing a security plan is to confuse authentication with encryption. Authentication is the process of validating an end user or device, whereas encryption is the function of hiding the original text in a cipher. Define Your Authentication MechanismEarlier in this chapter, you learned about the two authentication types: user-based and machine-based. The most commonly adopted and recommended authentication mechanism is EAP. An added advantage of EAP is that it supports both types of authentication. Your choice of EAP type is impacted by many factors, including the following:
Some EAP mechanisms make it extremely difficult to compromise a WLAN; however, they are correspondingly difficult to set up and maintain in large deployments. If security is of the utmost importance, this additional operational overhead is probably acceptable. On the other hand, some EAP mechanisms offer less protection and should not be seriously considered for an enterprise-class deployment. Carefully consider the tradeoffs between robustness of the authentication scheme, ease of management, and computational requirements on the client's end. Unavailability of appropriate software on clients typically limit the type of EAP you can practically use. Supporting a wide range of devices adds more analysis of the EAP type selection process. Refer to the section "EAP Types" for more information. The impact that clients have on your EAP selection are directly related to the following questions:
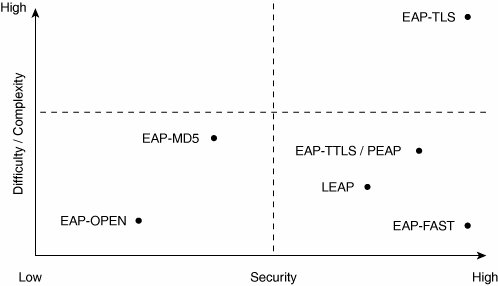
Different EAP types strike a different balance between complexity and security. Figure 7-4 depicts the trade-off for common EAP types. Figure 7-4. The Difficulty, Complexity, and Level of Security for EAP Types Select Your Encryption/Data Integrity TypeAnother significant decision for wireless security is choosing an appropriate encryption type for your environment. Although you might be inclined to choose the most secure option available, this choice might not be practical for your environment. Complexity, computational power, and user convenience are also key considerations. Yet again, a balance is required. Currently, the most popular standard is 802.11i using the Advanced Encryption Standard (AES). AES's benefit of robustness comes at the expense of increased computational overhead. Devices that intend to use AES should be foreseen of sufficient computing power so that they can process encryption transparently without negatively impacting other tasks of the device. Therefore, the more practical issue you need to consider is determining the most secure method that all your approved devices can handle given their existing compulational horsepower. An alternative strategy is to deploy multiple security types in function of the capabilities of the devices you support. Establish a Password PolicyIn any networked enterprise, it is important to have a password policy, and it is highly likely that you have already defined yours. In some enterprise deployments, a completely separate set of user credentials is used to provide access to the wireless network. One-time passwords (OTPs) are a good example. Users do not enter their "native" credentials to access the WLAN; instead, they use a randomly generated OTP provided by a smart card or by software on the client device. Just like any of the other security decisions you make, the password policy must take into account conflicting goals such as ease of use, deployment, and support (for users and devices). Here are some considerations:
Note There is an added risk concerning the protection of authentication credentials when they are cached on a device. Sometimes, however, this does not outweigh the benefits of caching credentials. For example, hospitals often store user IDs and passwords on devices so that doctors are not troubled with entering them. Define a Clear WLAN Security PolicyDefining a clear and consistent security policy is an essential part of securing your WLAN. This WLAN security policy should provide quidelines for
Note A security policy is a collection of practices and guidelines that set a standard for behavior and use on the network. A security policy is different from a security posture in that a security posture represents a collection of actions that are used to provide a level of protection for the network. Secure Your APsPolicies and procedures only set guidelines. As such, specific measures must be in place to reduce risk. Configuring your access points correctly is a critical step in securing your WLAN. We recommend that you specifically address the following parameters of access points. SSIDAs described in Chapter 1, "Introduction to Wireless LAN Technologies," the Service Set Identifier (SSID) is analogous to a network name. It is used only to identify your network to client devices. Hence, it is not a true security measure. SSIDs are part of operational recommended practices. They are the first step toward compromising your network. Any default setting is an open invitation for malicious attack and therefore should be changed. An added security measure is not allowing your SSID to be broadcast openly. This measure helps to eliminate any accidental discovery of the SSID. If broadcasting the SSID is necessary (such as guest networks), it should be put into a separate network space, such as VLANs. Implement a Secure Management Policy for APsTo secure your WLAN, you must also implement a policy to manage your APs so that standards can be updated and enforced. The following list outlines the essential steps:
Prevent Layer 2 MAC Address SpoofingMany access points and network devices allow you to configure Layer 2 MAC address spoofing prevention. This step prevents devices from using a MAC address other than their own. Many attacks are based upon spoofing a different MAC address, and this step will help mitigate that risk. Note Publicly Secure Packet Forwarding (PSPF) is a Cisco feature that allows you to prevent inter-client communication on WLANs. This means that two stations cannot consciously or, more importantly, inadvertently share files with others that use the same AP. PSPF allows network access to client devices without providing other capabilities of a LAN, such as peer-to-peer. This feature is especially useful for public wireless networks like those installed in airports or on college campuses. Reduce Transmit Power to Only That Required for CoverageAccess points can transmit at various signal strengths. The higher the signal strength, the greater the distance that RF propagates, and therefore the greater the covered area. To avoid the risk of unauthorized users connecting to your WLAN, it is important not to let your radio signal "bleed" uncontrolably into the surrounding area. By reducing the transmit power, you can more carefully manage your cell size and design, controlling the degree to which your WLAN extends outside of your physical building or office space. Managing the power and range improves security by reducing the potential threats to your WLAN. Although this technique reduces the footprint that an attacker can use to exploit the network, it only prevents casual discovery. DoS attacks are still a possibility as an attacker can still transmit into your network causing radio interference. Consider Directional AntennasDirectional antennas allow you to shape the coverage area of your WLAN. Although not a security setting per se, directional antennas can, like reducing transmit power, help ensure that wireless coverage does not bleed into areas that you do not want to cover. Even when physical and logical security are tight, there is no reason to extend your footprint into uncontrolled areas. Note Directional antennas can also be used to provide more accurate coverage in problematic deployment spaces, such as large factory floors, hallways, and operating rooms. Physically Secure APsYou should physically secure the access points. Many manufacturers provide mounting brackets that allow you to physically lock down access points. This is important because access points can contain information on the configuration of your network. Ensuring physical security of the device not only protects your capital assets but also removes one more potential area where attackers can target your deployment. Use AAAThe authentication, authorization, and accounting (AAA) architecture you use is important for all network security, and WLANs are no different. WLANs require a method to authenticate users and to manage an encryption key exchange. AAA systems provide the industrial strength authentication management system needed to support this in a scalable and resilient fashion. As a backbone service, the AAA systems need to have a breadth of support for EAP types and must be scalable. AAA and EAPRemembering that EAP is the recommended method for securing the radio transmissions of your WLAN, you should ensure that your AAA service can support an EAP type. The EAP family of protocols is "extensible," meaning many varieties are available, including several proprietary versions. Some AAA servers do not support all EAP mechanisms. If you already have an existing AAA server in your infrastructure, it is crucial that you ensure that it supports the EAP mechanism you choose for your WLAN. Alternatively, you could install a dedicated AAA server or servers for WLAN use only. However, this is likely to be cost-prohibitive because more devices need to not be acquired but also managed on an ongoing basis. AAA Scalability and AvailabilityLike all centralized services on a network, it is important that your AAA infrastructure is scalable and stable. Because AAA servers are fundamental to a secure network, their availability and reliability are essential for a secure network. If you are deploying a large-scale or global network, it's important to plan your AAA architecture accordingly. Centralizing all authentication on a single system is not good practice; it's better to use a distributed system with several AAA servers to avoid a single point of failure. A distributed AAA architecture not only has better resilience and disaster recovery capabilities but also provides the added benefit of load-balancing among available AAA servers. In global deployments, for example, it's common to have AAA servers regionally dispersed. Not only does this ensure that you have a resilient system, but it also keeps authentication traffic regional. Some solutions allow AAA services to reside locally, which means that the authentication is performed on the AP or switch servicing that WLAN. This solution can be attractive for very large-scale deployments where you might have hundreds or thousands of local WLANs (for example, small retail stores or bank branches). Remember that losing connectivity to your AAA server means that users cannot authenticate; therefore, the WLANas a transport medium to the network as a wholeis unavailable. As such, a robust AAA architecture is essential. Physically Secure the Office SpaceA necessity of any network is ensuring physical security of the environment. Your wireless network is no different and in some cases can be considered more susceptible to attacks by intruders because APs are typically not placed in secured wiring closets, but rather in open areas. It is therefore essential, for many reasons, that you have good physical security in your office space and adjacent areas. Note Many large corporations have sizeable parking lots or public areas that surround their office buildings. It is prudent to make your security staff aware that uninvited or "suspicious" visitors might be attempting to eavesdrop on your WLAN. Educate them to be aware of potential war walkers and war drivers. Communicate with Your UsersA robust wireless security posture, a strong wireless security policy, and comprehensive security procedures are all devalued if your user population is unaware of them or ignorant of the risks of poor behavior. As such, communication with your users about security is a fundamental aspect of securing your WLAN. The vast majority of your users will be welcome partners in your ongoing security efforts if they are engaged successfully and educated on how to help. Consider using multiple communications methods to provide your user community with a comprehensive source for information about the wireless network. Include FAQs, user education documents, WLAN news bulletins, deployment updates, and even links to software and external resources. We recommend that, at the very minimum, you engage in communications with your WLAN users regarding the following three topics:
Secure Wireless at HomeIf your company provides remote access services to your users, then a home wireless networking policies and guidelines are recommended. Many large enterprises allow their users to connect to the corporate network from home. In many circumstances, these remote access services are provided not only by standard analog modems but also by "always on" high-speed connections, such as cable modems, xDSL, ISDN, and even dedicated Frame Relay or WAN links. In all cases, it is very important to publish strict guidelines on the acceptable use of wireless devices at the home. Consider that these services effectively extend the corporate network to your users' homes. The WLAN access point that is installed at the home is no different than a rogue AP and hence brings along the same risks. The different strategies for mitigating these threats are discussed next. Note that not all the solutions enable the full extension of the corporate network to the WLAN-enabled home. Ban Home Wireless on Corporate Remote-Access EquipmentA policy decision could be made simply to ban the use of wireless access points on corporate equipment at users' homes. This is in some ways the easiest solution but the one that has the most negative impact on the user. However, any such ban needs to be preceded with education on the merits of such a position. Provide Corporate Support for Home Access PointsA list of recommended or supported WLAN devices can be created, with specific configuration guidelines for each. Your users can then configure their access points using the instructions provided to conform with corporate security requirements. Provide Home Wireless Recommended PracticesA list of recommended practices specifically for home wireless networking can be provided for your users. These best practices might not provide detailed configuration guidelines for every make and model of access point, but they should provide the users with advice on the "high-level" concepts of configuring their devices securely. Provide a simple step-by-step guide such as the sample presented here. A dual approach consisting of a "quick setup" as well as a more comprehensive and detailed version is ideal:
Determine How to Support and Secure Mobile DevicesMobile devices such as PDAs and "smart phones" present their own security challenges. A policy and support plan for these devices is recommended for every corporation. If you choose to support these devices on the wireless network, you should ensure that they, like the rest of your client devices, are detailed in your security posture statement. Many issues will need to be addressed including, but not limited to, the following:
Determine How to Support and Secure ClientsOne of the most difficult aspects of an effective and successful WLAN deployment is client management. This ability to controlboth physically and logicallythe expectations and capabilities of client devices is paramount. The threat of a client performing actions that mimic an AP is serious because this is sometimes the cause of DoS attacks. To mitigate any possibility of the client device being the weak link in the security of the WLAN, there also must be active control as to which clients are supported and what their abilities are. Manage Clients and Client AttributesBeyond developing a policy and list of supported client devices, the policy needs to outline attributes of the devices. Controlling these attributes helps to ensure that devices not supported in your security policy are not permitted on the network, thereby strengthening your overall security posture. You should consider the following three aspects of a client device:
Anti-VirusAlthough not specifically a wireless issue, user laptops and desktops should be provided with regularly updated anti-virus software. WLANs, just like any network, can propagate viruses if the client devices are not configured with appropriate software. Soft APSome wireless software is available that allows a laptop or desktop computer to act as an access point. This software-enabled access point or soft AP is considered a major threat because it is usually a trusted device. The soft AP creates the same security threat as the unauthorized installation of rogue access points. In some ways the soft AP can be a more dangerous threat because many hackers will use them to stage attacks. As the successful hacker can turn any computer in an AP, he is not tied down anymore by the physical placement of regular APs. In essence, the soft AP could enable a hacker to place an AP wherever there is a computer. As such, we recommend that you disallow the use of this software capability and make it very clear in your wireless security policy that such software is unacceptable. Actively detecting soft APs is very difficult and this is another reason why radio-based rogue access point detection is of critical importance. Disable Ad-Hoc Mode NetworkingAlthough this is primarily a policy decision, depending upon the wireless client software you use, it may be possible to disable ad-hoc networking. Some client software allows you to disable certain functions using centralized administration tools. Detect Rogue APsRogue access points are access points that are located within your enterprise and that were not installed by your IT department or approved vendors. They present a very serious security threat when connected to your network as they are improperly configured with little or no security settings. A robust rogue AP detection system is critical for any secure wireless network. Indeed, rogue AP detection is critical because there is no such thing as a "non-wireless" network anymore; if you haven't deployed a WLAN, you can only assume that there is no WLAN as staff are purchasing cheap access points and installing them themselves, often without realizing the security implications. It should be noted that the vast majority of rogue access points come from your own users, and only a small minority are from malicious hackers. Most user-installed rogue APs are not intended to compromise security but are attempts at benefiting from wireless networking without realizing the risks of poorly configured devices. If you have a comprehensive entitlement policy and wide coverage area, you will reduce the likelihood of rogue APs being installed in the first place. Detecting rogue access points can be challenging. A combined approach of client-based reporting, radio-based detection, and network scanning is the best method. Client-Based ReportingClient-based reporting can be as simple as asking your users to report suspicious access points to the IT department. These can be nonstandard (enterprise) AP models, APs in unusual locations such as hidden under desks, and consumer-grade access points on desks or in cubicles. This reporting will allow your IT team to investigate and address the threat if it turns out to be real. Additionally, some solutions now available on the market allow for wireless clients, such as laptops, to actively and automatically report a list of access points they have encountered to back-end management system. This reporting is entirely transparent to the user, but it allows your wireless management framework to construct a picture of all the access points in your enterprise. If an access point is reported but is not listed or managed by your network management system, there is a chance that it is a rogue. Radio-Based DetectionRadio-based detection uses your own access points, or dedicated scanners, to actively monitor the RF spectrum and report all radio devices they detect. Effectively, your access points are "auditing the airwaves" and drawing up a picture of the radio frequency use in your enterprise. Most of the leading manufacturers provide radio-based rogue access point detection services with their products. These often have the advantage of providing you with a graphical representation of what your radio network looks like, using floor plans and colored cells or clouds to represent each 802.11 cell. Radio-based detection can also be carried out manually by IT staff using handheld wireless network analyzers or laptops with software designed specifically for this purpose. These include popular tools such as AirMagnet, Kismet, and AirSnort. Network-Based DetectionNetwork-based detection is the third essential pillar of a robust rogue access point detection system. Network-based detection uses internally developed or publicly available tools to scan the wired network for devices that match a particular signature or "fingerprint." These devices scan for familiar MAC addresses, specific open TCP ports, and particular protocols and processes that might be running on a device. These tools can even attempt to log on to the device and note its response. By combining several criteria and automating the process into regular scripted jobs, network-based reporting can quickly produce a list of suspicious devices. Your IT department can then use this list to investigate the devices and act accordingly. One of the most popular publicly available pieces of software that can be used for this purpose is WinFingerPrint (http://winfingerprint.sourceforge.net/). Respond to Detected Rogue APsAfter you have identified a rogue access point, you need to act. The potential responses can be categorized under three headings: remove, reclassify, and remediate. RemoveYou can remove the rogue access point from the network. You can achieve this by disabling the network switch port to which it is attached (if applicable), or you can confiscate the device or instruct the owner to comply with your IT polices and power-off or remove the rogue access point. If the device is not physically within the confines of your enterprise, you might need to "work around" the problem and reconfigure some of your access points to remove the interference and contention. ReclassifyYou can reclassify many rogue access points, especially those identified during the initial discovery phase, as friendly and therefore no longer a security risk. Friendly APs can be those that are internal to your network, such as those in labs. Conversely, friendly APs can be external, such as those in shared office spaces where another company manages and controls the APs. Keep the knowledge of the function or ownership of these friendly APs for reference later when you audit rogues. RemediateFinally, you simply might want to remediate some rogue access points and ensure that they are supported by your IT department and have the correct configuration. This choice can be due to a valid requirement for WLAN coverage in a particular area, or it simply can be due to a bad configuration in an access point that was officially supported. Consider Using Intrusion Detection SystemsMany corporations opt for dedicated wireless intrusion detection systems (wireless IDSs). Many leading wireless equipment manufacturers also provide this service with their solutions. Wireless IDSs are a more advanced and dedicated approach to radio-based rogue access point detection. They often use dedicated "scanners" (often access points themselves, but sometimes cheaper scan-only devices) and specialized software. They can also be used to detect client behavior that you might want to prevent, such as the creation of ad-hoc wireless networks and client-to-client file-sharing networks. Wireless IDSs provide a very good level of security and are often used by corporations that want to restrict or ban the use of wireless networks entirely. However, every large-scale enterprise-class network can benefit from the added security they provide. |
EAN: 2147483647
Pages: 163