Voice
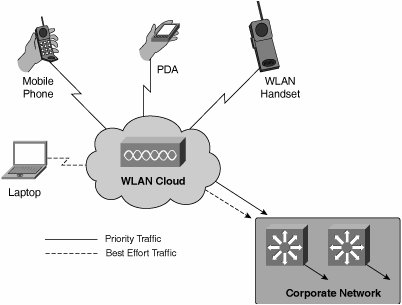
| Voice over IP (VoIP), which enables telephony over an IP infrastructure, is a complex topic in its own right. Given the importance of VoIP technology, this section explains the basic considerations for enabling VoIP on your WLAN. Refer to the "Additional Resources" section at the end of this chapter for books that cover VoIP, which is a communication protocol, and IP telephony, which is a communication application, in more detail. Many of the benefits that are found in wired VoIP are directly applicable to wireless VoIP. Strategic benefits include the enabling of rich-media content integration and distribution. Operational advantages consist of ease of maintenance and support through consolidation of the PBX infrastructure and avoiding the need to support an additional technology. Lastly, financial gains can consist of reduced toll-charges by routing internal calls across the organization's network instead of the public network. The challenges of enabling telephony over IP are in the IP protocol itself. Basic IP is by design a best-effort protocol. No distinction is made between the types of communication sessions and no guarantees are made regarding timely delivery of packets. E-mails, web traffic, voice, and video are by default all treated as equal. IP will only try to deliver the packets, and the handling of dropped packets is left up to the applications. Therefore, some higher-order mechanism is required to enable more deterministic behavior of the best-effort protocol. This is the domain of quality of service (QoS). QoS refers to a collection of tools and techniques for classifying, marking, and providing priority handling of traffic. Classification of traffic is done based on parameters such as protocols, network addresses, devices, application types, or even time of day. Marking of Layer 2 frames and Layer 3 packets is then performed to enable different priority processing of traffic. QoS mechanisms thus effectively engineer the traffic so that it exhibits a more deterministic behavior. WLANs employ 802.11e, a standard that was ratified by the IEEE in 2005, to provide Layer 2 QoS enhancements for WLAN applications by augmenting the IEEE 802.11 Media Access Control (MAC) layer. 802.11e provides two different types of enhancements. Both types enable the creation of traffic classes. However, the granularity with which these classes can be manipulated is slightly different. Enhanced Distributed Coordination Function (EDCF) is the simpler version of 802.11e and only provides a best-effort QoS. The more complex version, named Hybrid Coordination Function (HCF), offers more granular configuration possibilities, but has not been widely deployed. Note that Wireless Multimedia (WMM) is an alternative WLAN QoS standard defined by the WLAN Alliance. WMM can be considered to be a subset of 802.11e. It was developed while the industry waited for the IEEE to ratify 802.11e. Now that this ratification has occurred, WMM is less of a consideration for new deployments. However, it is still a supported technology by many vendors. Even though many of the VoIP benefits and challenges are shared between wired and wireless LANs, some challenges are either unique to WLANs or compounded by the nondeterministic behavior of wireless networks. The following sections focus on these unique challenges by taking a closer look at WLAN voice devices as well as specific hurdles that must be overcome to enable VoIP on WLANs. WLAN Voice DevicesTelephony is traditionally associated with dedicated devices. These devices are the handset that you encounter on desks or mobile telephony handsets. However, the advent of VoIP has made it possible to convert any general purpose computing device into a telephone. Today, telephones not only come in hardware, but they also come as software applications. These software versions of phones are colloquially known as SoftPhones. A SoftPhone application can effectively turn a desktop, laptop, or PDA into a fully featured telephone. Hence, you should not consider dedicated WLAN telephony handsets as the only viable alternative for WLAN VoIP. Various vendors manufacture and sell these WLAN VoIP handsets, and they look and feel like traditional mobile handsets. The difference is that they use 802.11 instead of analog radio as the transport mechanism. This is similar to the IP phones that you find on desks which use 802.3 instead of analog TDM. To enable consolidation of mobile telephones, several vendors are currently working on dual-mode handsets. These handsets are capable of interfacing with both WLANs and cellular networks giving users the option to select the most cost-effective connection. Cellular phones are likely to soon form an integral part of voice devices that your WLAN needs to support. Figure 4-1 summarizes the many different types of WLAN voice devices that you can encounter. Figure 4-1. WLAN Voice Devices Figure 4-1 shows that WLANs can mobilize voice on devices that traditionally are not considered as mobile telephony devices. Remain sensitive to this fact and include your strategy for supporting these devices and telephony in your architecture and design. Chapter 5, "Guidelines for a Successful Architecture and Design," covers this topic in greater detail. WLAN Voice Implementation ChallengesThe nondeterministic behavior of an IP network can plague the deployment of telephony in the IP environment. Specifically, latency caused by the nondiscriminating network as well as dropped IP voice packets can have a significant detrimental impact on voice quality. WLANs compound these challenges in three ways. The first two are caused by the shared nature of the medium. Not only is available throughput shared among users, but access to the medium is also granted on a first-come, first-serve basis. The third challenge relates to the speed with which wireless voice devices can roam from cell to cell. Bandwidth and LatencyWhereas bandwidth and latency considerations are important in wired networks, they are critical in wireless environments. The focus in this case is edge connectivity because backhaul connectivity is assumed the same irrespective of the wired or wireless connectivity provided to the end user. The contention that occurs in wired VoIP environments for network access is between different applications on a client that require network access. The client is connected via a dedicated connection to an access switch, and applications compete for access to the network. QoS mechanisms can be used to classify, mark, and provide priority queuing. This alleviates many of the bandwidth and latency challenges in wired networks. Unfortunately, this is not the case for WLANs because they share access to the transport medium among all connected stations. As such, contention for airspace access occurs not only inside of the client, but also between the clients. Even though a client could provide a higher priority queue for its time-sensitive applications such as voice (and video), the client must still compete with neighboring clients for airspace access. Quality of ServiceBecause of the aforementioned situation, it is difficult to guarantee timely access to the medium for voice traffic. 802.11e extends QoS mechanisms to the WLAN Media Access Control (MAC) layer to increase the probability of gaining access to the network. The simpler method, EDCF, is a "best effort" QoS method where high priority traffic is given a slightly higher transmission probability than lower priority traffic. The more complex type is HCF, which is the 802.11e version that provides features like bandwidth control, fairness between stations, classes of traffic, jitter management, and so on. As such, WLAN QoS can be configured with much greater precision with HCF. Even though this method provides more granularity, it has not been widely implemented yet due to its complexity. If voice is indeed a critical application for your environment, ensure that both QoS as well as sufficient bandwidth is provisioned. Avoid situations where many clients are part of the same cell because this will prevent excessive access contention. Chapter 5 provides strategies for determining the appropriate number of access points for your environment. Roaming ClientsA challenge that is unique to WLANs is that of roaming clients. Stations that are on the move transfer their association from one access point to another. When this transfer occurs, the device must re-authenticate with the authentication, authorization, and accounting (AAA) infrastructure, thereby introducing a possible momentary interruption in service. This is especially noticeable in voice applications where any interruption can result in lost packets and a corresponding impact on voice quality. WLAN vendors have addressed this by introducing fast Layer 2 roaming, which reduces the time to re-authenticate (usually to less than 100 ms or so) as the station moves its association from one access point to another. This fast roaming capability limits the disruption of the voice stream as packet loss is minimized. An additional challenge caused by roaming occurs when a station crosses an Extended Service Set (ESS) boundary. When a client transfers its association to an AP in a different ESS, it effectively moves into a different IP subnet. This is known as Layer 3 roaming, as the client device has moved from one IP subnet to another. Routing issues arise as the station's old IP address is invalid and VoIP sessions can terminate under these circumstances. If no additional measures are taken, the active call will be dropped. Figure 4-2 illustrates the effect of mobile VoIP handsets roaming across ESS boundaries and the resulting invalid IP address in the new ESS. Figure 4-2. Limitations in WLAN Layer 3 Roaming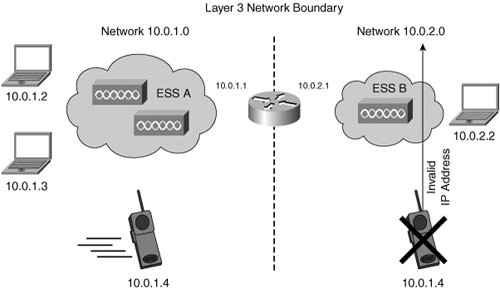 Given that most organizations have far more than a single ESS, roaming with mobile voice devices can become a significant challenge if not addressed in the architecture. Multisite or campus locations will have a hard time maintaining voice sessions throughout the campus. Various solutions do exist to address this roaming challenge, and each has its benefits and challenges. These include Mobile IP Protocol and "predictive" tunneling solutions. Almost all vendors have moved to some type of tunneling technology to solve the ESS roaming problem. The tunneling solutions are essentially the same as those discussed later in this chapter for constructing guest networking solutions. Mobile IP is typically deployed only in difficult environments such as moving vehicles. Physical Device AttributesVoice on WLANs brings along a number of considerations that are not necessarily related to the network, but rather to the physical attributes of the devices. These considerations include battery life and physical security of the clients. Battery life is important no matter what kind of mobile device you use. It is especially significant when contemplating voice because voice is a real-time form of communication. It is certainly more annoying to lose an active voice session due to battery power depletion than having your laptop warn you of an impending shutdown. As always, remain sensitive to security of the device. As opposed to a laptop or desktop, mobile voice-enabled devices are typically smaller and harder to physically control and secure. Security of mobile voice devices should not necessarily be thought of in terms of compromise of your network. Authentication information could indeed be extracted from the device facilitating other attacks. A greater liability is the information that is stored on the device such as phone books or the ability to make calls from an active phone, which can result in financial or legal burdens. Use security features such as PIN codes and policy administration tools to protect access to the devices. For a more in-depth treatise on security in wireless environments, refer to Chapter 7, "Security and Wireless LANs." |
EAN: 2147483647
Pages: 163