Preparation
| The preparation phase of your deployment is a critical initial step. Careful consideration of the issues at this early stage will greatly increase the probability of a smooth and successful deployment. The primary task associated with the preparation phase of the PPDIOO solution lifecycle is identifying and validating the business case. This was covered in detail in Chapter 2. Additional factors that require attention when you prepare your WLAN deployment include defining the breadth and scope of the WLAN and deciding how you will fund the project. Generic solutions typically produce average results. By considering the topics defined in this section, you can proceed in a prepared manner with your goals and constraints clearly defined and understood. After you have defined your goal, you can carefully prepare your deployment plans. In Chapter 2, you effectively considered why a WLAN might be a good investment for your enterprise network. This chapter focuses on what you need to consider when planning a WLAN and how you will deploy it. It is all about understanding and addressing the larger context in which the project takes place. As such, the key factors that need to be considered include but are not limited to the following:
By clearly identifying and defining your position on these issues, you will provide a more targeted solution, avoid scope creep, achieve swifter deployment, and preempt many potential problems. Indeed, many technology deployments fail because the planner or business decision maker failed to identify and subsequently preemptively address these fundamental challenges. The next sections examine each of these key factors in turn. Breadth and Scope of DeploymentOne of the first sets of decisions you should make when preparing to deploy an enterprise-class wireless LAN relates to the breadth and scope of the deployment. You need to decide where you are going to deploy, whether your existing infrastructure is ready to support the WLAN, and what local and environmental regulations you must address. Deployment ScopeYou need to determine how large a footprint you want your WLAN to have. The business rationale you identify (as described in Chapter 2) will certainly assist you in this process. However, it is strongly recommended that you document as accurately as possible the breadth and scope of your deployment. Doing so ensures that you avoid installing the WLAN in areas where it is unnecessary or would provide limited benefits, and conversely ensures that you cover all areas in which WLAN connectivity is both required and beneficial to your organization. You may wish to identify early on whether there are specific business considerations with regards to where you will deploy. Options for deployment include the following:
Draw up a list of all buildings/sites/floors where you want to deploy independently of the business driver (secondary network, complimentary network, and so on). This will also assist you in your budget and project planning, help you to create a prioritized deployment list, and help you to identify possible pilot sites. Infrastructure ReadinessA key focal point should be the infrastructure requirements that a WLAN deployment presents. To assist you in this endeavor, you must consider typical network architecture models. Most large-scale networks are built on a hierarchical model. Typically, there are three "layers" to these networks, as shown in Table 3-1.
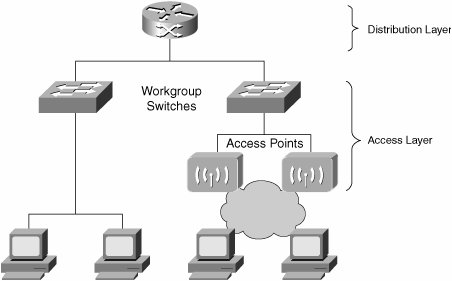
Figure 3-2 illustrates the network layers. Figure 3-2. Hierarchical Network Model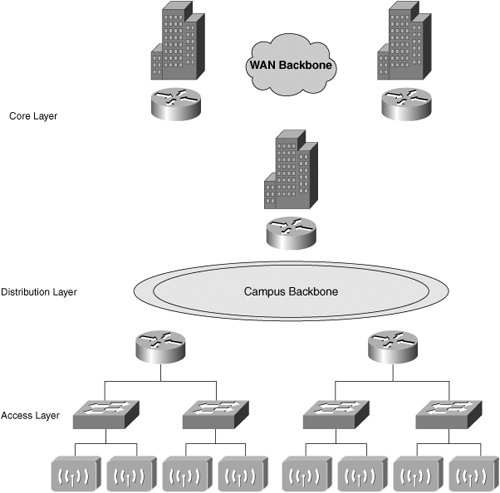 In a typical wired network, your users connect via the access layer switches, which are sometimes known as workgroup switches. In a WLAN, however, your users connect to the network via the wireless access points. Access points are considered edge devices, and they lie within the access layer, as you can see in Figure 3-3. Figure 3-3. Access Layer Note Don't confuse the terms "access layer" and "access points." The access layer is a conceptual term used to describe the edge devices that provide connectivity to your end users and workstations. Access points are the physical devices that provide wireless connectivity. They are analogous to workgroup switches. Access points and workgroup switches are considered to lie within the access layer, because they are "edge devices" that provide entry into the network. These concepts are important because when you deploy a WLAN, you are adding devices into your access layer and connecting them directly to your workgroup switches. Therefore, you must ensure that your workgroup switches have sufficient capacity for these access points. Typically they require a network port, power, and console access. ConnectivityBecause each access point requires an Ethernet port for connectivity, you must ensure that your network switches have sufficient port capacity to attach the AP to the rest of the network. Typically, this does not pose a problem in greenfield deployments. Deploying your WLAN in an established or mature networking environment, this becomes a significant consideration to address. Otherwise, you would have to budget accordingly for additional equipment. In addition, you should ensure that your Ethernet switches support at least 100BASE-T, as all the current WLAN standards (802.11a, 802.11b, and 802.11g) provide an aggregate nominal throughput of between 11 Mbps and 54 Mbps. Finally, you will have to ensure that the access point locations are within the cabling distance limit for the employed LAN technology. For example, the maximum transmission distance for 100BASE-T is 100 meters. In summary, to ensure that your access points can establish connectivity, answer the following questions:
PowerElectronic equipment requires electrical power. Generally speaking, you can power access points in two ways:
Powering the access points via AC is straightforward but requires that you provide AC outlets in the vicinity of the access point. This is often an expensive exercise that requires the use of certified electrical engineers, which can add significant cost and delays to your projects. Powering the access points via the Ethernet cables is achieved via Power over Ethernet (PoE). This technology has been standardized as IEEE 802.1af and employs a previously unused pair of wires in category 5 (or better) cables to provide power to a device. PoE is popular because it avoids the need to install expensive additional power cables at each location and helps reduce costs. When determining your power requirements, answer the following questions:
Console AccessMany enterprises provide console access, also known as out of band management, to their network equipment for support and management purposes. You should account for providing console-port access if required or desired. Note that not all access points support console access. If this is a requirement or standard for your organization, you should ensure that the access point make and model under consideration supports console access, and that your wired infrastructure has sufficient capacity to provide it. When planning your WLAN, answer the following questions:
Environmental ConsiderationsMany enterprises decide to physically locate the access points in the interstitial space between the ceiling tiles and roof. This plenum area has strict fire regulations associated with it in most countries. In the United States, for example, all equipment and cabling installed in the plenum space must be "plenum-rated," a term denoting that it is fire-resistant. Certain environments have stringent controls on what electrical equipment can be deployed in other areas. Examples include government or military installations, hazardous environments (mining, petroleum, gas, mineral exploitation, and so on), certain manufacturing locations (munitions, "clean-room" environments, and so on), and many healthcare-related buildings or campuses. In these circumstances, the electrical equipment must be deemed "intrinsically safe," a term denoting that the equipment does not create electrical interference or even very small electromagnetic discharges. Most electrical equipment, including access points, is not "intrinsically safe" and can therefore create very small electromagnetic discharges or interference. To address these stringent environmental controls, access points can be installed in special shielding containers. In the United States, these are called National Electrical Manufacturers Association (NEMA) enclosures. (Further information on NEMA and NEMA enclosures can be found at http://www.nema.org/prod/be/enclosures/.) In the United States, there are also national health and safety regulations to be considered, and local and national building standards. It is important for you to follow due diligence on potential environment or safety standard issues that are specific to your organization's context. Be sure to investigate and understand your obligations and ensure that your equipment complies with all relevant standards. The use of an experienced or professional deployment team will help in this area. Enterprises that work in such environments or that have equipment sensitive to environmental factors often have a safety or standards officer who can approve any wireless LAN installations or at least provide guidance. Ensure that they are represented in the project. Safety and standards compliance are not the only environmental topics that can impact your planning phase. Simple issues such as ruggedness or waterproofing might also need to be considered. This is especially the case when you might be deploying wireless access points outdoors (in a university campus, for example). Regulatory Restrictions or RequirementsAs mentioned in Chapter 1, the regulations that apply to the use of 2.4-GHz and 5-GHz frequency ranges are not the same all over the world. At this stage, it is sufficient to note that you must take local and national regulations into account and plan accordingly. This is especially important if you are considering a large, transnational or global deployment because you might need to purchase different models for different countries. Deployment Funding StrategiesThere are many funding strategies for deploying wireless in an organization, including the following:
This section describes these common strategies along with their advantages and disadvantages. You learn more about funding strategies in Chapter 6, "Wireless LAN Deployment Considerations." Centrally Funded DeploymentCentrally funded is perhaps the most common funding strategy. The entire cost is absorbed by a single entity; this can be the IT department, Finance, or the group responsible for business operations. In most small to medium deployments, this is the only model used. Advantages of centrally funded deployment include
Disadvantages of centrally funded deployment include
Group-Funded DeploymentGroup-funded deployment strategies are those where a division, department, or sometimes regional section of an enterprise funds the deployment from its own budget. It either engages external professional consultants to design and deploy the solution or uses the organization's existing IT department in a "professional services" model. Advantages of group-funded deployment include the following:
Disadvantages of group-funded deployment include the following:
Client-Funded DeploymentA client-funded strategy is simply one whereby the IT department of the enterprise is responsible for installing and managing the deployment but utilizes a charge-back mechanism to the clients (usually other departments or divisions) to fund the installation. This strategy is usually adopted with a clear policy direction that ensures your IT department is the only group approved for deploying wireless networks. This ensures that you maintain a consistent architecture, a standard design and scope of work (equipment, manufacturer and model), wireless security standards, and a common support plan. Furthermore, it prevents several different departments from proceeding with their own installations that might not be compliant with your internal security and procurement policies. Client-funded deployments are usually based upon an installation charge per AP or user, followed by an ongoing support cost. Advantages of client-funded deployment include
Disadvantages of client-funded deployment include
Subscription-Funded DeploymentThe subscription-based deployment strategy is also known as "pay as you go." In this model, the users or user groups pay a service fee for wireless network access. The subscription model ensures that you not only recover the costs associated with the service deployment but also recuperate ongoing support and maintenance costs. This model is less common in most standard enterprise deployments but popular in environments where you have many different user types. Universities are a good example. The provision of wireless network access can be considered an added value service that the student body pays for on a per-user or per-class basis. Advantages of subscription-funded deployment include the following:
Disadvantages of subscription-funded deployment include the following:
|
EAN: 2147483647
Pages: 163