16.5 Analysis Tools and Techniques
16.5 Analysis Tools and Techniques
It is useful to understand what the network traffic looks like in its most basic form. An actual Ethernet frame (encapsulating an IP packet) looks like this in hexadecimal:
08 00 5a 47 43 58 08 00 20 21 fb 7d 08 00 45 00 00 1d c0 fa 00 00 3c 11 00 a2 0a 17 2d 43 0a 17 2d 4414 0e 0f d4 00 0d 3c bc 72 6f 6f 74 00 00 00 00 00 00 00 00 00 00 00 00 00 00
As noted in Table 16.2 showing the general Ethernet frame structure, the bytes represent the following.
| 08 00 5a 47 43 58 | Source Ethernet address (OUI IBM Corporation) |
| 08 00 20 21 fb 7d | Destination Ethernet address (OUI Sun Microsystems) |
| 08 00 | denotes the fact that this frame contains an IP packet |
| 45 00 00 1d c0 fa 00 00 3c | part of the IP header (version, length, etc.) |
| 11 | indicates that the packet contains UDP data (11; 17 decimal) not TCP data (06), etc. |
| 00 a2 | checksum used to verify that the packet was not damaged in transit |
| 0a 17 2d 43 | source IP address (10.23.45.67) |
| 0a 17 2d 44 | destination IP address (10.23.45.68) |
| 14 0e 0f d4 00 0d 3c bc | UDP source port (5134), destination port (4052), header length and checksum |
| 72 6f 6f 74 | The word "root" in hexadecimal |
| 00 00 00 00 00 00 00 … | The rest is padding |
When analyzing network traffic, it is generally desirable to know what time events occurred. The tcpdump format includes date-time stamps for each frame that was captured but some tools, including tcpdump itself, only display the time and not the date.[8] For instance, using tcpdump to view the file named hotmail-02242003.dmp - available on the Web site associated with this book - does not display the date, only the time.
examiner1% tcpdump -r hotmail-02242003.dmp 15:59:15.501154 192.168.0.5.32769 > 192.168.0.1.53: 6342+ A? www.hotmail.com. (33) (DF)
Looking at the beginning of the same tcpdump file shows a date-time value of A3875A3E, which equates to Monday, February 24, 2003 15:59:15 GMT-0500:

Because this file was created on an Intel system, the date-time values are in little-endian format (e.g. A3875A3E) whereas a tcpdump file created on a Solaris machine has date-time values in big-endian format (e.g. 3E5A87A3).
16.5.1 Keyword Searches
In some cases, it may be sufficient during an examination to search a tcpdump file for a specific keyword. For instance, usernames and passwords for file transfer, e-mail, and other services can be found by searching the keywords "USER," "PASS," and "login" as shown here using a simple UNIX utility called ngrep:[9]
examiner1% ngrep -w 'USER|PASS|login' -t -x -s 65535 -I case02-04032003.dmp input: case02-04032003.dmp match: ((^USER|PASS\W) | (\WUSER|PASS$) | (\WUSER|PASS\W) ) #################################### T 2003/04/03 10:07:39.066816 192.168.0.5:32788 → 172.16.1.10:21 [AP] 55 53 45 52 20 61 72 67 6f 6e 69 6d 6f 6e 0d 0a USER argonimon.. ########## T 2003/04/03 10:08:01.956350 192.168.0.5:32788 → 172.16.1.10:21 [AP] 50 41 53 53 20 70 61 73 73 77 6f 72 64 2d 72 65 PASS password-re 76 65 61 6c 65 64 0d 0a vealed.. ########## T 2003/04/03 10:24:59.182353 192.168.0.5:32869 → 172.16.1.23:143 [AP] 32 20 6c 6f 67 69 6e 20 22 6e 61 6d 65 22 20 22 2 login "name" " 70 61 73 73 77 6f 72 64 2d 72 65 76 65 61 00 00 password-revea.. 09 01 00 00 ... ...############################################exit
Similarly, when looking for connections to IRC, searching for nicknames and channel names may provide all of the information that a digital investigator requires. In the aforementioned "hotmail-02242003.dmp" file, searching for packets containing the keyword "POST" can reveal the act of the suspect sending a message (Figure 16.7). The "HTTP POST" command corresponds to the act of sending a Hotmail message.
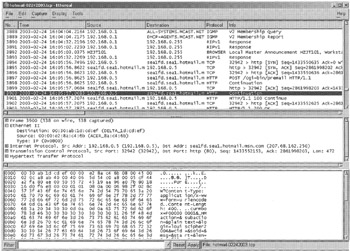
Figure 16.7: Ethereal showing packet in "hotmail-02242003.dmp" file containing the keyword "POST," corresponding to the act of sending the message through Hotmail.
Although tcpdump and Argus do not have a keyword search feature, they can be used in combination with grep to find items of interest.
16.5.2 Filtering and Classification
When dealing with large amounts of data involving many hosts, it is often necessary to focus the examination on certain protocols or traffic to and from specific hosts. The tcpdump program enables filtering based on certain criteria but uses the libpcap filter syntax, which is complex. For instance, the following tcpdump arguments can be used to examine traffic from a single host (192.168.0.5) to a given network (any IP address starting with 172.16.), excluding traffic to ports 21, 53, and 80:
# /usr/sbin/tcpdump -nex -s 65535 -r case001-04032003-02.dmp src host 192.168.0.5 and dst net 172.16.0.0/16 and dst port not (21 or 53 or 80)
Additionally, tcpdump can only recognize and extract a limited number of protocols, including TCP and UDP. To extract only Web traffic, for instance, one might look for traffic to port 80 but this would miss relevant Web traffic if the server was using a different port, such as 8080. Argus can be used to examine tcpdump files and uses a similar filter syntax as tcpdump but has more options and keeps track of session state information. Ethereal provides more filtering functionality using a slightly less complex syntax and supports more protocols. For instance, the above filter can be implemented in Ethereal using the following syntax:
ip.src = = 192.168.0.5 and ip.dst == 131.243.0.0/16 and not (ftp or dns or http)
Although Ethereal supports more protocols than tcpdump, it makes some assumptions about the expected behavior of protocols that prevent it from automatically classifying traffic that does not meet these basic assumptions. For instance, Ethereal does not automatically recognize and classify FTP traffic when a port other than the default port (21) is used. However, once the digital evidence examiner correctly classifies the FTP traffic, Ethereal can be instructed to interpret the data using the "Decode As" feature on the Tools menu.
Some commercial products have more features than these free tools that facilitate traffic filtering and classification. For instance, Figure 16.8(a) and (b) shows NetIntercept being used to locate and view the same information shown in Figure 16.7.
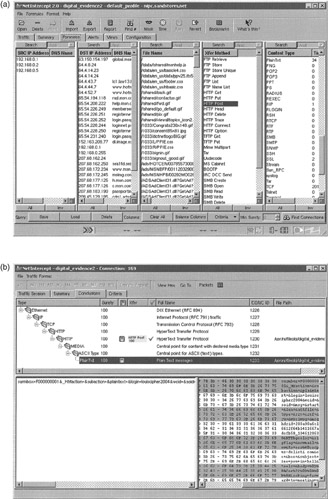
Figure 16.8: (a) Using the NetIntercept forensics view to examine network traffic and locate important items such as an "HTTP POST." (b) Using NetIntercept to view the same packet as Figure 16.7 containing the "POST" keyword.
NetIntercept's graphical user interface allows the examiner select criteria for filtering such as source and destination IP addresses within a certain time period. Also, NetIntercept interprets protocols rather than simply making assumptions based on default ports. By interpreting protocols, this tool can extract noteworthy elements (e.g. usernames, passwords, files, credit card numbers) and store them in a database to facilitate examination and analysis. This protocol analysis feature is also useful for finding traffic that violates expected behavior such as an FTP server running at a non-standard port. NetIntercept lists all such anomalies in the Alerts section and can generate a printable report of this information. This protocol anomaly detection feature is conceptually similar to the file signature mismatch detection provided by most media examination tools like FTK and EnCase. NetIntercept can generate other useful reports from network traffic, including traffic statistics and an inventory of components in Web traffic that is conceptually similar to an inventory of files on a disk.
16.5.3 Reconstruction
It is often desirable to reconstruct related packets into complete messages or sessions. For example, data contained in captured frames might be reassembled to form an e-mail message or Web page. Ethereal can be used to reconstruct streams in a rudimentary way (recall Figure 15.4), but can be cumbersome for large amounts of data and has some limitations from a digital evidence examination standpoint. For instance, Figure 16.9 shows the Hotmail Inbox recovered from the "hotmail-02242003.dmp" file using Ethereal. The banner advertisement at the top of the Web page was not present in the original traffic - it was automatically updated from the Internet when the reconstructed page was opened in a Web browser. At the very least, this spoliation of the evidence should be avoided by performing the examination on a computer that is not connected to the Internet. This also demonstrates the importance of understanding the limitations and quirles of tools being used to examine digital evidence.
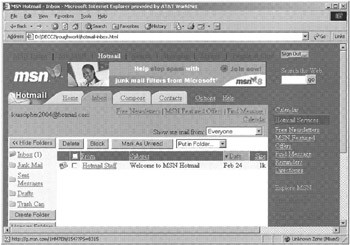
Figure 16.9: Hotmail Inbox recovered using Ethereal.
Some commercial tools are specifically designed for digital evidence examination and provide more visualization features that make it more efficient to examine large amounts of network traffic. For example, NetIntercept can also reconstruct and extract content from network traffic, such as Web pages, files transferred using FTP, and Word documents contained in MIME encoded e-mail attachments. Figure 16.10 shows the Hotmail Inbox shown in Figure 16.9 but reconstructed and displayed using NetIntercept. Notably, the banner advertisement at the top of the Web page is the original one from the "hotmail-02242003.dmp" file. Also, to protect the examiner's machine from malicious code, NetIntercept displays reconstructed Web pages in a protective viewer that does not execute scripts but does display them in raw form to facilitate analysis. Figure 16.11 shows NetIntercept displaying the content of several word documents and other files stored in a Zip file that was attached to an e-mail message. By decoding attachments and compressed archives in the way, NetIntercept can perform keyword searches on their content.
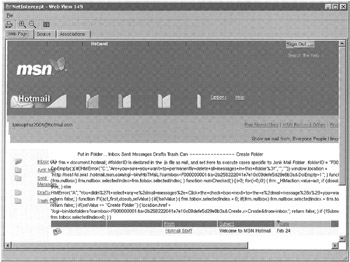
Figure 16.10: Hotmail Inbox extracted from a tcpdump file and displayed using NetIntercept.
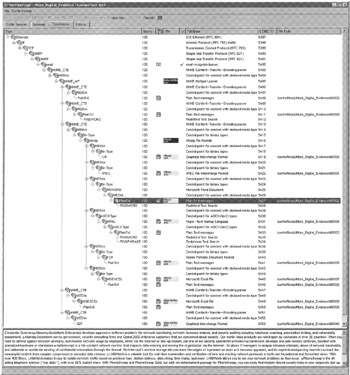
Figure 16.11: MIME encoded e-mail attachments containing data in a ZIP file extracted from a tcpdump file and displayed using NetIntercept.
[8]The date-time stamps in tcpdump files are stored in UNIX epoch time - a 32-bit hex value representing the number of seconds since January 1, 1970.
[9]http://ngrep.sourceforge.net
EAN: 2147483647
Pages: 279