14.3 Network Technologies
14.3 Network Technologies
Beneath the apparently consistent facade of TCP/IP is a collection of dissimilar network technologies. It is these network technologies that enable multiple hosts to share a single transmission medium such as a wire or the air. When hosts are sharing a transmission medium only one host can use the medium at any given time. This is analogous to a polite conversation between people in which one person talks and the other listens. If two hosts were allowed to use the transmission medium at the same time, they would interfere with each other.
The easiest way to understand network basics is to imagine someone setting up a network. For instance, suppose "Barbara the Bookie" wants to create an online betting site like World Sports Exchange[6] or World Gaming.[7] Once Barbara the Bookie has decided where to incorporate (e.g. England), where to establish operations (e.g. Antigua), and purchased computer equipment, she must select a network technology to connect the Antiguan servers physically. Seven network technologies: ARCNET, Ethernet, FDDI, ATM, IEEE 802.11 (wireless), cellular, and satellite are briefly described here.
14.3.1 Attached Resource Computer Network (ARCNET)
ARCNET was one of the earliest network technologies and the latest version (ARCNET Plus) can transmit data at twenty megabytes per second (20 Mbps).[8] ARCNET uses coaxial cables, similar to the ones used for cable television, to connect the Network Interface Card (NIC) in each host to a central hub. If a single host is damaged or turned off, others on the network can still communicate with each other through the hub. However, if the hub is damaged or turned off, none of the hosts will be able to communicate with each other.
ARCNET uses a method called "token passing" to coordinate communication between each of the hosts connected to the central hub (Figure 14.4). Basically, a token is sent around on the network and when a host wants to send data it waits for the token, takes the token, and starts to transmit. When that host has finished transmitting, it relinquishes the token, passing it on to the other hosts on the network thus allowing other hosts to communicate.
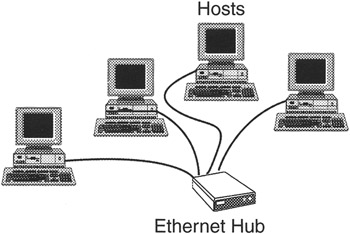
Figure 14.4: Hosts connected to a central hub (star typology).
14.3.2 Ethernet
Ethernet has gone through several stage of development and has become one of the most widely used network technologies because it is relatively fast and inexpensive. One of the most recent forms of Ethernet uses wires similar to regular telephone cords. These wires are used to connect the NIC in each host to a central hub or switch that essentially makes the hosts think that they are connected by a single wire.
Instead of token passing, Ethernet uses Carrier Sense Multiple Access with Collision Detection (CSMA/CD) to coordinate communication. Although CSMA/CD is a mouthful, the concept is straightforward. Hosts using Ethernet are like people making polite conversation at a dinner party. At a polite dinner party, if two people start to speak at the same time, they both stop for a moment, one starts to talk again while the other waits. Similarly, when two hosts using Ethernet start to transmit data at the same time, they both sense that the other host is transmitting and they both stop for a random period of time before transmitting again. Ethernet is described in more detail in Chapter 16.
14.3.3 Fiber Distributed Data Interface (FDDI)
As the name suggests, FDDI uses fiber optic cables to transmit data by encoding it in pulses of light. This type of network is expensive but fast, transmitting data at 100 Mbps. Like ARCNET, FDDI uses the token passing technique but instead of using a central hub, hosts on an FDDI network are connected together to form a closed circuit (Figure 14.5). Data travel around this circuit through every host until it reaches its destination. Normally, data only travel in one direction around this circuit. However, if one of the hosts on an FDDI network detects that it cannot communicate with its neighbor, it uses a second, emergency ring to send data around the ring in the opposite direction. In this way, a temporary ring of communication is established until the faulty host can communicate again.
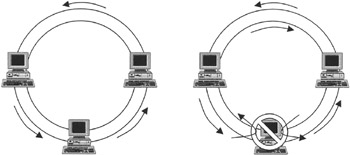
Figure 14.5: Normal FDDI communication versus backup communication when a host is down (double ring topology).
14.3.4 Asynchronous Transfer Mode (ATM)
ATM uses fiber optic cables and specialized equipment (ATM switches) to enable computers to communicate at very high rates (Gbits per second). Telecommunications companies developed this technology to accommodate concurrent transmission of video, voice, and data. Although it is very expensive, ATM is becoming more widely used.
ATM uses technology similar to telephone systems to establish a connection between two hosts. Computers are connected to a central ATM switch and these switches can be connected to form a larger network. One host contacts the central switch when it wants to communicate with another host. The switch contacts the other host and then establishes a connection between them.
In Chapter 16, ATM is briefly compared with Ethernet to highlight their similarities and differences and describe how they both can be useful as a source of digital evidence.
14.3.5 IEEE 802.11 (Wireless)
Unlike the previously summarized network technologies, computers connected using one of the IEEE 802.11 standards do not require wires; they transmit data through the air using radio signals (Figure 14.6). Currently, the two most widely used standards are 802.11a and 802.11b, which use the 2.4 and 5 GHz spectrums, respectively. The 802.11g standard is also becoming popular because of its increased speed and backwards compatibly with 802.11b. Access points containing a radio transmitter and receiver form the core of these wireless networks, enabling computers, personal digital assistants, and other devices with a compatible wireless NIC to communicate with each other. In addition to being a conduit for wireless devices, these access points are generally connected to a wired network like an Ethernet network to enable communication with wired devices and the Internet.
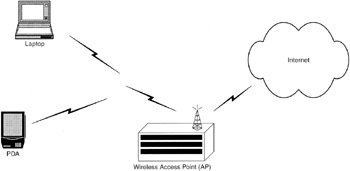
Figure 14.6: Wireless IEEE 802.11 network with a PDA and PC connected to an AP. Also shown is the AP connected to the Internet.
The main limitations of 802.11 networks are distance, speed, and interference. A computer must be within a certain distance of an access point to achieve reliable connectivity and even then, data are only transmitted at theoretical maximums of 11 and 54Mbps for 802.11b and 802.11a networks, respectively. Any obstacles between the computer and access point that block radio waves will degrade or prevent connectivity.[9]
Some businesses and hobbyists have intentionally created 802.11 networks for anyone to use. Passers-by can configure their computers to connect to these public wireless networks and access the Internet. Some organizations and home users have unintentionally configured their wireless network insecurely allowing anyone to access them. The emergence of these public and insecure wireless networks has led to a trend called war driving - people drive around neighborhoods and business districts with computers configured to locate 802.11 networks. Some individuals will use insecure networks to gain unauthorized access to an organization's network and can even monitor wireless network traffic. Others simply notify other war drivers of the wireless networks they have found either by marking a nearby surface with a symbol that describes the network (called war chalking) or by posting them on the Internet.
14.3.6 Cellular Networks
Cellular data networks are becoming widely available and increasingly popular. Organizations that depend on mobility (e.g. airlines, package delivery companies) have equipped their employees with hand-held devices that communicate over cellular networks. Cellular networks enable computers to connect to the Internet using a cellular telephone in much the same way as a modem is used to connect using telephone wires. Cellular networks are made up of cell sites that enable individuals within a certain geographical area to place and receive calls. Cell sites are connected to central computers (switches) that process and route calls and keep logs that can be used for billing, maintenance, and investigations. Although cellular networks are primarily used as circuit-switched networks (making direct connections between telephones) they can also function as packet-switched network (making virtual circuits between computers). To function as a packet-switched network, additional equipment is required that extracts packets of data from the wireless network and routes them to their destination.
Most digital cellular networks use Frequency Division Multiple Access (FDMA), Code Division Multiple Access (CDMA), Time Division Multiple Access (TDMA), or a combination of these technologies to transmit data via radio waves. These technologies enable several mobile telephones to share a single communications channel on a mobile telephone network (e.g. AMPS, GSM) by dividing the channel into several time slots, and assigning each telephone its own slot. To enable cellular devices to communicate with other hosts on the Internet, some cellular networks use a protocol Cellular Digital Packet Data (CDPD).[10] However, CDPD has been largely replaced with the higher speed General Packet Radio Service (GPRS) - part of GSM technology that uses a combination of TDMA and FDMA and has Internet Protocol capabilities.
Cellular technology is developing rapidly and the next evolution of GSM (called third generation or 3G) is emerging, providing higher data transmission rates and thus enabling more multimedia services such as music and video. The increasing functionality in cellular network technology is creating new opportunities for criminals and investigators. To understand the potential for investigators, a summary of mobile telephones is provided here. More information about digital evidence on wireless networks and devices is available in Chapter 10 of the Handbook of Computer Crime Investigation (Clarke and Gibbs 2001).
Mobile telephones have two numbers that uniquely identify them - an Electronic Serial Number (ESN), and a telephone number or Mobile Identification Number (MIN). When a mobile telephone is manufactured, its microchip is programmed with a unique ESN and when the telephone is given to a subscriber it is assigned a telephone number that people use to call the subscriber. These numbers are used by telephone companies to direct calls to the correct mobile telephone and are used by investigators to locate the phone. Special electronic tracking equipment enables investigators to lock onto an ESN/MIN pair and track it to a general geographical area. Within a given geographical area, triangulation can be used to pinpoint the cellular telephone. Investigators require the assistance of cellular telephone companies to perform this type of tracking.[11]
Most mobile telephone companies maintain communication with all of their mobile telephones at all times even when the telephone is not in use (the telephone must be turned on). This constant communication is used to notify subscribers of voice mail and can be used to track a cellular telephone even when it is not being used to make calls. For instance, the position data relating to a murder victim's mobile telephone can be compared with that of a suspect's to determine if they were in the same vicinity at the time of the crime. In one case, a kidnap victim's mobile telephone was used in real time to track and intercept the car she was being transported in. In several cases offenders have stolen the victim's mobile telephone and in one case the offender apparently called the victim's mother to taunt her. In another case, a victim saw the offender make calls from the crime scene using a mobile telephone. Although the offender was not apprehended in this case, digital evidence did exist on a telephone company's systems that could have been used to generate a short list of suspects. Some cellular telephones even have Global Positioning System (GPS) features that can be used to locate the device quite precisely.
In addition to tracking, cellular telephone companies can provide investigators with call details, toll records, and wiretaps. This information can be used to determine the calling patterns and even the specific activities of a criminal.
14.3.7 Satellite Networks
Satellites are becoming more widely used to convey Internet traffic around the globe. Some networks simply use satellite dishes, called Very Small Aperture Terminals (VSATs), to beam communications from the ground to a satellite overhead, which transmits the data to a central location on the ground. As with cellular networks, these VSATs use TDMA, CDMA, and similar technologies to transmit data using radio waves. These networks can support a range of network technologies, including ATM for high speed Internet access. Although some VSATs are portable, they usually only function within a given region or country and they are not as convenient to transport as a cellular telephone.
The Teledesic network is not designed with mobility in mind but aims to provide Internet-in-the-Sky access to anywhere in the world such as telecommuters in remote regions or businesses and homes in developing countries that do not have reliable telecommunications infrastructures. Conversely, Mobile Satellite Systems (MMS) like Iridium and Globalstar are designed with mobility in mind, providing global connectivity using mobile telephones. The Iridium Satellite System uses GSM-based technology to transmit data between wireless devices and low earth satellites and can be used to make telephone calls as well as connect to the Internet.
[6]WSEX (http://www.wsex.com) founder Jay Cohen was convicted of violating the US Wire Communications Act by illegally using interstate telephone lines to take online wagers. More specifically, Cohen had accepted sports bets from New Yorkers via the WSEX gambling site in Antigua. In 2001, Starnet Communications International, a subsidiary of World Gaming, Inc., pled guilty to violating Section 202 (1) b of the Canadian criminal code by having a machine in Canada for gambling or betting (http://laws.justice.gc.ca/en/c-46/39421.html). World Gaming has since moved their systems to Antigua and is incorporated in England.
[7]http://www.worldgaming.com
[8]ARCNET Plus is an enhanced version of ARCNET that has the ability to use TCP/IP.
[9]IEEE 802.11a networks interfere with other devices in Europe, making them ineffective. For this reason, the European HiperLAN2 standard was developed for higher speed wireless access.
[10]A CDPD network uses a network technology called Digital Sense Multiple Access with Collision Detection (DSMA/CD) that works just like CSMA/CD. Although it is possible to eavesdrop on a cellular network, CDPD uses encryption to conceal data in transit.
[11]If criminals can obtain an ESN and MIN, they can reprogram a cellular telephone to mimic someone else's telephone. Any calls made from the criminal's telephone will be billed to the valid subscriber. Additionally, it becomes harder to capture criminals when they change the ESN/MIN in their phones. This became such a problem in the late 1990's that most cellular telephones companies use encryption to protect the ESN and MIN of their telephones.
EAN: 2147483647
Pages: 279