14.2 Technical Overview of Networks
14.2 Technical Overview of Networks
A computer connected to a network is generally referred to as a host, and uses a modem or network interface card (NIC) to send and receive information over wires or through the air.[3] When more than two hosts are being connected, it is not feasible to link each host directly to every other host - this would result in a ludicrous number of wires terminating at each host. Each time a new host was added to the network, it would have to be wired directly with every other computer. In the past, to avoid this situation, a single network cable was used and devices called a tap punctured the plastic sheath of the thick cable physically to connect a host to the network. Because this approach was inflexible and difficult to maintain, devices called hubs (a.k.a. concentrators) were developed to simulate this single network cable configuration - instead of using taps each host is connected to the hub using a thin cable. To increase network security and efficiency, hubs are being replaced by switches that perform a similar function but direct data to their intended destination rather than broadcasting them to all hosts on the network, thus inhibiting one host from eavesdropping on the network traffic of all neighboring hosts. Techniques have been developed to enable eavesdropping on switched networks, undermining the security provided by these devices (Snipe 2000; Convery 2002).
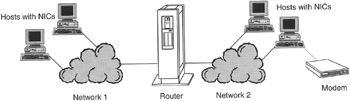
Figure 14.3: Depiction of hosts with NICs connected to a router to form a network.
Computers connected to the global Internet communicate using a set of protocols collectively called TCP/IP (Transport Control Protocol/Internet Protocol). As detailed in the next section, the Internet comprises many individual networks. TCP/IP is essentially the common language that enables hosts on these individual, often dissimilar networks to communicate. Each TCP connection (a.k.a. TCP stream) is bi-directional: one flow for receiving data and a second flow for sending data. A tool like Argus[4] can monitor network traffic and maintain logs for later analysis such as the two NetBIOS connections shown here:
Date Time Proto Source Destination 20 May 03 07:11:18 tcp 192.168.0.5.1029 → 192.168.0.2.netbios-ssn 20 May 03 07:12:24 tcp 192.168.0.5.1030 → 192.168.0.3.netbios-ssn
Hosts that are connected to two or more of these networks and direct traffic between them are called routers. Routers are a crucial component of computer networks, essentially directing data to the correct place. Although almost any host can be used as a router, most networks use custom-made routers like those produced by Cisco and Juniper. Routers can direct data from one network to another, filter unwanted traffic, and keep logs that can be an excellent source of digital evidence. In addition to system logs, some routers can generate more detailed NetFlow logs, similar to Argus logs, discussed in later chapters. Notably, NetFlow displays individual, unidirectional flows as shown here, whereas Argus displays bi-directional streams:
Start End SrcIPaddress SrcP DstIPaddress DstP Proto 0520.07:11 0520.07:12 192.168.0.5 1029 192.168.0.2 139 6 0520.07:11 0520.07:12 192.168.0.2 139 192.168.0.5 1029 6 0520.07:12 0520.07:13 192.168.0.5 1030 192.168.0.3 139 6 0520.07:12 0520.07:13 192.168.0.3 139 192.168.0.5 1030 6
Because of their importance, routers are at high risk of attack and computer intruders target routers to eavesdrop on traffic and disrupt or gain access to networks.
Preview (Chapter 17): For the most part, every host on the Internet is assigned a unique number, called an Internet Protocol (IP) address, to distinguish it from other hosts. Before information is sent through the Internet, it is addressed using the IP address of the destination host, much like an envelope is addressed before it is submitted to a postal system. Routers use these IP addresses to direct information through the Internet to its destination. If the sender requires confirmation that the destination host has received a transmission, the Transport Control Protocol (TCP) will perform this task, resending information when necessary. Be aware that TCP performs other functions, such as breaking information into packets and that there are other protocols in the TCP/IP family such as the User Datagram Protocol (UDP), the Internet Control Message Protocol (ICMP), and the Address Resolution Protocol (ARP). It is also worth noting that TCP/IP enables other protocols like Simple Mail Transfer Protocol (SMTP) and Hypertext Transfer Protocol (HTTP) to transmit e-mail and Web pages, respectively.
Firewalls are similar to routers in that they direct traffic from one network to another. However, these security devices are designed to block traffic by default and must be configured to permit traffic that meets certain criteria. Firewalls can keep detailed logs of successful and unsuccessful attempts to reach the hosts that it protects and can be a useful source of digital evidence.
The services that networks enable, such as sending and receiving e-mails, rely on the client-server model. Telnet provides a clear example of client-server communication, enabling remote users to log into a server and execute commands. For example, the following shows a telnet connection from a Windows client to a UNIX server (192.168.0.9) and some resulting log file entries:
C:\> telnet 192.168.0.101
Standard telnet does not encrypt traffic, exposing your password and data to network sniffers. A more secure alternative to telnet is Secure Shell (SSH), available at www.ssh.org.
login: eoc3
Password: ********
Last login: Thu Apr 3 15:50:33 from 192.168.0.5
| Warning | To protect the system from unauthorized use and to ensure that the system is functioning properly, activities on this system are monitored and recorded and subject to audit. Use of this system is expressed consent to such monitoring and recording. Any unauthorized access or use of this Automated Information System is prohibited and could be subject to criminal and civil penalties. |
oisin% grep telnet /var/log/messages Apr 3 15:50:33 oisin inetd[178]: [ID 317013 daemon.notice] telnet[373] from 192.168.0.5 2523 Apr 4 15:59:23 oisin inetd[178]: [ID 317013 daemon.notice] telnet[432] from 192.168.0.5 2531 oisin% last eoc3 pts/6 192.168.0.5 Fri Apr 4 15:59 still logged in eoc3 pts/2 192.168.0.5 Thu Apr 3 15:50 - 16:06 (00:16) ftp ftp ACBC4DOB.ipt.aol Tue Apr 1 14:41 - 13:04 (8+22:22)
This example also demonstrates the need to correlate log files to obtain a more complete picture of what occurred on a system. The associated syslog entry on the server shows the time of the connection and the IP address of the client. However, the syslog entries in this example do not indicate which account was used to make the connection and how long the connection lasted. This information is stored in the wtmp log, accessed here using the last command, showing which user account was used to connect at the time but does not indicate that telnet was used as the connection method.[5]
In the past, a server was viewed as a powerful computer that could provide a service to many smaller computers called clients, much like a law firm provides services to its clients. Some servers allow anyone to access their resources without restrictions (e.g. Web servers) while others (e.g. e-mail servers) only allow access to authorized individuals, usually requiring a user identifier and password. With the increased power and capacity of personal computers, the distinction between clients and servers has blurred. Today, any host can be made into a server by installing software that allows other hosts to access it over a network. This approach is commonly called peer-to-peer networking (P2P) to differentiate between this type of file sharing and the traditional client-server model, and was popularized by programs like Napster and Kazaa.
Peer-to-peer networking has been taken one step further by wireless technology that uses radio frequency, infrared, lasers, and microwaves to carry data. For instance, Bluetooth enables computers, personal digital assistants, mobile phones, and household appliances like televisions to communicate with each other. In essence, when a Bluetooth-enabled device is turned on, it attempts to communicate with other devices in its vicinity to create what is commonly called an ad hoc network or piconet.
Many components of networked systems contain information about the activities of the people who use them. Table 14.1 summarizes some of the information that different network components may have.
| INTERNET ACTIVITY | LOGS | ACTIVE STATE DATA |
|---|---|---|
| PPP dial-up | TACACS/RADIUS | Terminal server memory |
| Firewall/router | syslog/NetFlow | show cons |
| Host logon | Wtmp/NT Event Log | utmp/nbtstat -c |
| Web server | Access log | netstat -an |
| E-mail server | messages/syslog | Mail spool |
| FTP server | xferlog | netstat -an |
| IRC server | Server/boot logs | netstat -an |
| Wireless LAN | Device logs | Device memory query |
| Mobile phone | Call records | Location/conversations |
[3]Individuals who are learning about networks for the first time will find that the convenience of using abbreviations and acronyms creates its own difficulties. For instance, the acronym for Media Access Control addresses (MACs) can easily be confused with the abbreviation for Macintosh computers (Macs). The Glossary organizes the terms, abbreviations, and acronyms that are used in this text to assist the reader.
[4]http://www.qosient.com/argus/
[5]Some systems record the username and logout time in syslog. However, neither syslogs nor wtmp indicate what activities occurred on the system during the login session - this would require an analysis of MAC times on the file system and process accounting logs or BSM audit records if they exist. Additionally, routers, firewalls, intrusion detection systems, and other network monitoring devices could provide corroborating data.
EAN: 2147483647
Pages: 279