1.3 Challenging Aspects of Digital Evidence
1.3 Challenging Aspects of Digital Evidence
Digital evidence as a form of physical evidence creates several challenges for forensic examiners. First, it is a messy, slippery form of evidence that can be very difficult to handle. For instance, a hard drive platter contains a messy amalgam of data - pieces of information mixed together and layered on top of each other over time. Only a small portion of this amalgam might be relevant to a case, making it necessary to extract useful pieces, fit them together, and translate them into a form that can be interpreted.
Similarly, radio waves and microwaves traveling through the air contain a tangle of data, making it necessary to find the desired signal amongst the noise and translate it into the data that can be understood (Figure 1.1). This is conceptually similar to DNA analysis - the relevant information must be extracted from human fluid/tissue, processed, and translated into a form that we understand.
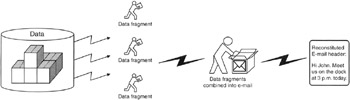
Figure 1.1: Conceptual depiction of data fragmants being extracted from a hard drive platter, combined, and translated into an e-mail message.
Second, digital evidence is generally an abstraction of some event or digital object. When a person instructs a computer to perform a task such as sending an e-mail, the resulting activities generate data remnants that give only a partial view of what occurred (Venema, Farmer 2000). Unless someone has installed surveillance equipment, individual mouse clicks, keystrokes, internal system commands, and other minutiae are not retained. Only certain results of the activity such as the e-mail message and server logs remain to give us a partial view of what occurred. Even when such minutiae are recorded, the electrical impulses of our mouse button clicks and keyboard depressions must be translated into data before they have any meaning. Similarly, an e-mail message and server log stored on a disk are the result of several layers of abstraction from magnetic fields on the disk to the letters and numbers that we see on the screen. Therefore, we never see the actual data but only a representation, and each layer of abstraction can introduce errors (Carrier 2003).
This situation is similar to that of the traditional crime scene investigation. In a homicide case, there may be clues that can be used to reconstruct events like putting a puzzle together. However, all of the puzzle pieces are never available, making it impossible to create a complete reconstruction of the crime. This book describes various sources of digital evidence and how these multiple, independent sources of corroborating information can be used to develop a more complete picture of the associated crime.
Third, the fact that digital evidence can be manipulated so easily raises new challenges for digital investigators. Digital evidence can be altered either maliciously by offenders or accidentally during collection without leaving any obvious signs of distortion. Fortunately, digital evidence has several features that mitigate this problem.
-
Digital evidence can be duplicated exactly and a copy can be examined as if it were the original. It is common practice when dealing with digital evidence to examine a copy, thus avoiding the risk of damaging the original.
-
With the right tools it is very easy to determine if digital evidence has been modified or tampered with by comparing it with an original copy.
-
Digital evidence is difficult to destroy. Even when a file is "deleted" or a hard drive is formatted, digital evidence can be recovered.
-
When criminals attempt to destroy digital evidence, copies and associated remnants can remain in places that they were not aware of.
CASE EXAMPLE (BLANTON 1995):
When Colonel Oliver North was under investigation during the Iran Contra affair in 1986, he was careful to shred documents and delete incriminating e-mails from his computer. However, unbeknown to him, electronic messages sent using the IBM Professional Office System (PROFS) were being regularly backed up and were later retrieved from backup tapes.
Fourth, digital evidence is usually circumstantial making it difficult to attribute computer activity to an individual. Therefore, digital evidence can only be one component of a solid investigation. If a case hinges upon a single form or source of digital evidence such as date-time stamps on computer files, then the case is unacceptably weak. Without additional information, it could be reasonably argued that someone else used the computer at the time. For instance, authentication mechanisms on more secure computers can be bypassed and many computers do not require a password, allowing anyone to use them. Similarly, if a defendant argues that some exonerating digital evidence was not collected from one system, this would only impact a weak case that does not have supporting evidence of guilt from other sources.
CASE EXAMPLE (UNITED STATES v. GRANT 2000):
In an investigation into the notorious online Wonderland Club, Grant argued that all evidence found in his home should be suppressed because investigators had failed to prove that he was the person associated with the illegal online activities in question. However, the prosecution presented enough corroborating evidence to prove their case.
EAN: 2147483647
Pages: 279