Securing TCPIP
Securing TCP/IPIn recent years, vendors have been busy extending and expanding their TCP/IP implementations to incorporate the security and encryption techniques discussed earlier in this hour. The following sections describe how encryption techniques are integrated into two Internet security protocol systems:
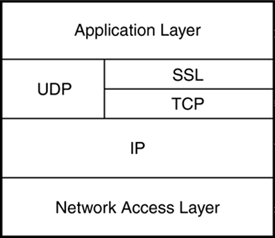
Other public security protocols are also in development, and some security software vendors have developed their own systems. The following sections are intended to give you an idea of the kind of solutions necessary to incorporate the promise of encryption into the business of a real network. SSLSecure Sockets Layer (SSL) is a collection of TCP/IP security protocols introduced by Netscape that is now on the path for ratification as an Internet standard. The purpose of SSL is to provide a layer of security between the sockets at the Transport layer (see Hour 6, "The Transport Layer") and the application accessing the network through the sockets. Figure 20.6 shows the position of SSL in the TCP/IP protocol stack. The idea is that, when SSL is active, network services such as FTP and HTTP are protected from attack by the secure SSL protocols. Figure 20.6. The TCP/IP stack with SSL.
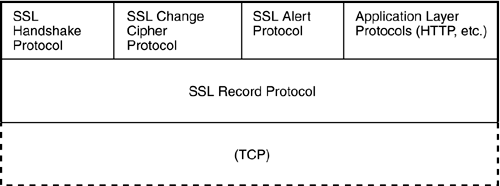
A closer look at the SSL layer reveals two sublayers (see Figure 20.7). The SSL Record Protocol is a standard base for accessing TCP. Above the Record Protocol is as a group of SSL-related protocols that perform specific services:
Figure 20.7. SSL sublayers.
SSL-enabled services such as HTTP operate directly through the SSL Record Protocol. After the connection is established, the SSL Record Protocol provides the encryption and verification necessary to ensure the confidentiality and integrity of the session. As with other protocol security techniques, the trick is to verify the identity of the participants and securely exchange the keys that will be used for encrypting and decrypting transmissions. SSL uses public key encryption and provides support for digital certificates (described earlier in this hour). The SSL Handshake Protocol establishes the connection and negotiates any connection settings (including encryption settings). SSL is used on many Web sites to establish a secure connection for the exchange of financial information and other sensitive data. Most mainstream browsers are capable of establishing SSL connections with little or no input from the user. One problem with SSL is that, because SSL operates above the Transport layer, the applications using the connection must be SSL-aware. The next section describes an alternative TCP/IP security system (IP Security) that operates at a lower layer and therefore hides the details of the security system from the application. IPSecIP Security (IPSec) is an alternative security protocol system used on TCP/IP networks. IPSec operates inside the TCP/IP protocol stack, beneath the Transport layer. Because the security system is implemented beneath the Transport layer, the applications operating above the Transport layer do not have to have knowledge of the security system. IPSec is designed to provide support for confidentiality, access control, authentication, and data integrity. IPSec also protects against replay attacks, in which a packet is extracted from the data stream and reused later by the attacker. IPSec, which is essentially a set of extensions to the IP protocol, is described in several RFCs, including RFCs 2401, 2402, 2406, and 2408. The RFCs describe IP security extensions for both IP version 4 (see Hour 4, "The Internet Layer") and IP version 6 (see Hour 22, "The New Internet"). IPSec provides the benefit of encryption-based security to any network application, regardless of whether the application is security-aware. However, the protocol stacks of both computers must support IPSec. Because the security is invisible to high-level applications, IPSec is ideal for providing security for network devices such as routers and firewalls. IPSec can operate in either of two modes:
Tunnel mode is used to build a secure communication tunnel in which all details of the network are hidden. An eavesdropper cannot even read the header to obtain the source IP address. IPSec tunnel mode is often used for virtual private network (VPN) products, which are intended to create a totally private communication tunnel across a public network. IPSec uses a number of encryption algorithms and key distribution techniques. Data is encrypted using conventional encryption algorithms such as DES, RC5, or Blowfish. Authentication and key distribution might employ public key techniques. |
EAN: 2147483647
Pages: 259