Encryption
| It is very easy to intercept and read an unprotected packet of data traveling over a public network. In some cases, that data might contain user or password information. In other cases, the data might contain other sensitive information you don't want anyone else to see, such as credit card numbers or company secrets. The fact is that even if the data isn't particularly secret, many users are justifiably uncomfortable with the prospect of eavesdroppers listening in on their electronic communication. The security methods discussed later in this hour are designed to make the network more secret. Many of these methods use a concept known as encryption. Encryption is the process of systematically altering data to make it unreadable to unauthorized users. Data is encrypted by the sender. The data then travels over the network in coded, unreadable form. The receiving computer then decrypts the data in order to read it. In fact, encryption does not require a computer at all. Encryption methods have been around for centuries. As long as people have written secret messages, they have looked for codes or tricks to keep those messages secret. In the computer age, however, encryption has gotten much more sophisticated because of the ease with which computers can manipulate huge, messy numbers. Most computer encryption algorithms result from the manipulation of large prime numbers. The algorithms themselves are intensely mathematical, and I do not exaggerate to say that most of the experts who create and deploy encryption algorithms have graduate degrees in computer science or mathematics. Encryption is an important foundation of almost all TCP/IP security. The following sections discuss some important encryption concepts. As you read the rest of this hour, it is important to keep in mind that the security infrastructure actually has multiple goals, and security methods must address multiple needs. The beginning of this section discussed the goal of confidentiality (keeping data secret). The security system must also address such needs as
Encryption techniques are used to help ensure authentication and integrity as well as confidentiality. Algorithms and KeysAs you learned in the previous section, encryption is a process for rendering data unreadable to everything and everyone who doesn't have the secret for unlocking the encryption code. For encryption to work, the two communicating entities must have the following:
When programmers first began to write encryption software, they realized they must contend with the following problems:
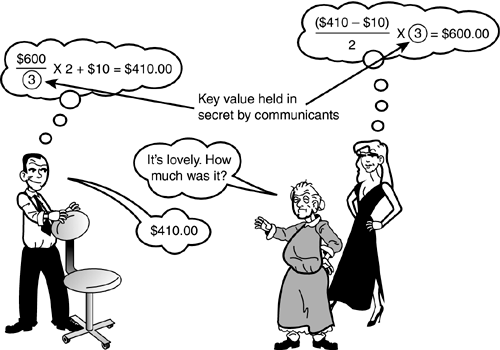
Intractable as these problems might seem, the large minds who develop encryption techniques quickly saw a solution. The solution is that the process for encrypting or decrypting the data must be divided into a standard, reproducible part (which is always the same) and a unique part (which forces a secret relationship between the communicating parties). The standard part of the encryption process is called the encryption algorithm. The encryption algorithm is essentially a set of mathematical steps used to transform the data into its unreadable form. The unique and secret part of the process is called the key. The science of encryption is extremely complex, but for purposes of discussion, you can think of the key as a large number that is used within the algorithm as a variable. The result of the encryption process depends on the value of the key. Therefore, as long as the value of the key is kept secret, unauthorized users will not be able to read the data even if they have the necessary decryption software. The strangeness and obscurity of good encryption algorithms cannot be overstated. However, the following example illustrates the key and algorithm concepts. A man does not want his mother to know how much he pays for furniture. He knows his mother is mathematically inclined, and he does not want to risk using a simple factor or multiplier to obscure the true value for fear that she will uncover the pattern. He has arranged with his lover that, if his mother is visiting and asks the cost, he will divide the real cost by a new, spontaneous number, multiply the result by two, and then add 10 dollars. In other words, the man arranges to use the following algorithm:
The new, spontaneous number (n) is the key. This same algorithm can be used every time the mother visits. The mother will have no way of determining a pattern for obscuring the real cost of the item as long as she does not know the key used in the calculation. If the man comes home with a chair or table and sees his mother in the yard, he secretly signals a number to his lover (see Figure 20.1). When his mother asks the cost of the piece, he processes the algorithm and uses the number he signaled to his lover as the key. For instance, if the key is 3 and the chair cost is $600, he would report Figure 20.1. An extremely primitive algorithm for disguising communication.
The lover, who is aware of the shared secret, knows that she must process the algorithm in reverse to obtain the true cost:
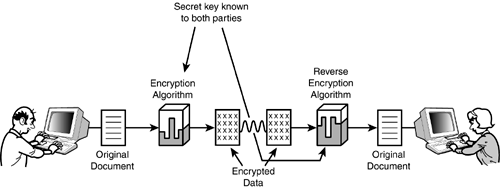
This simple example does not reveal the real complexity of computer encryption methods. It is also important to remember that the goal of changing a value is not exactly the same as the goal of making data unreadable. However, in the binary world of computers, this distinction is less pronounced than it might seem. This example is intended only as an illustration of the important difference between an algorithm and a key. Symmetric (Conventional) EncryptionSymmetric encryption is sometimes called conventional encryption because it preceded the development of newer, asymmetric techniques. Symmetric encryption is still the most common form, although public key asymmetric encryption (discussed later in this hour) has recently received considerable attention. Symmetric encryption is called symmetric because the decryption process is exactly the reverse of the encryption process. Figure 20.2 describes a symmetric encryption/decryption process. The steps are as follows:
Figure 20.2. The symmetric encryption process.
The furniture man and his lover (see the example in the preceding section) use a symmetric algorithm to hide the true value of the chair. The receiver works backward through the original algorithm, using the same secret key originally used to encrypt the data. By the Way You might be wondering how one could ever have an encryption method that doesn't use the original key with the reversed algorithm to decrypt the data. This question is understandable, considering that, after centuries of encryption dating back to the Greeks and Romans, no one thought about doing it any other way until the 1970s. You'll learn more about asymmetric encryption later in this hour. Symmetric encryption can be extremely secure if it is performed carefully. The most important considerations for the security of any encryption scheme (symmetric or asymmetric) are as follows:
Breaking through an encryption algorithm that uses a 128-bit key might seem completely impossible, but it can happen if the algorithm and key are not sufficiently secure. Still, the easiest way to steal encrypted data usually is to steal the key. The software must provide some secure means for delivering the key to the receiving computer. Various key delivery systems exist, and you'll learn about some of these systems later in this hour. In the case of symmetric encryption, the secret key is the whole secret. If you capture the key, you have everything. Most systems therefore call for a periodic renewal of the key. The unique key used by a pair of communicating computers might be re-created with every session or after a given time interval. Key renewal increases the number of keys crossing the network, which compounds the need for effective key protection. Several common encryption algorithms make use of symmetric encryption. The most famous symmetric algorithm might be the Data Encryption Standard (DES). DES is used with several common encryption techniques, including Kerberos 4.0. DES uses a 56-bit key, which many experts say is too short. In fact, the DES algorithm was actually cracked through brute-force techniques in a test lab in 1998. Other symmetric encryption algorithms include the 128-bit key IDEA algorithm. The Blowfish symmetric algorithm typically uses a 128-bit key, although key length may vary to up to 448 bits. The Kerberos authentication system (described later in this hour) provides a good example of the kind of procedures necessary to protect the keys in symmetric encryption. In general, the key distribution methods include the following:
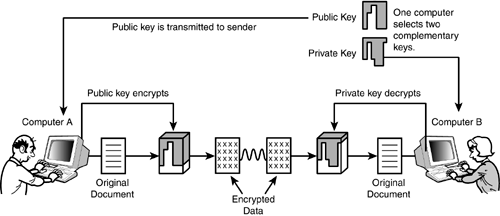
Another method that could be added to this list is the option of physically delivering the key offline, on a floppy disk or some other transportable medium. Asymmetric (Public Key) EncryptionAn alternative encryption method that has emerged over the last 25 years provides an answer to some of the key distribution problems implicit with symmetric encryption. Asymmetric encryption is called asymmetric because the key used to encrypt the data is different from the key used to decrypt the data. This process is shown in Figure 20.3. Figure 20.3. The asymmetric encryption process.
Asymmetric encryption is commonly associated with an encryption method known as public key encryption. In public key encryption, one of the two keys (called the private key) is held securely on a single computer. The other key (the public key) is made available to computers that want to send data to the holder of the private key. This process is depicted in Figure 20.3. The steps are as follows:
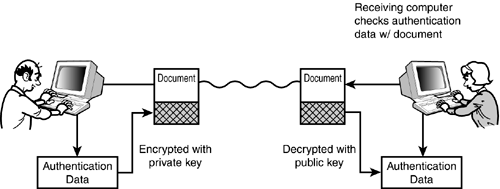
An important aspect of public key methods is that the encryption performed through the public key is a one-way function. The public key can be used to encrypt the data, but only the private key can decrypt the data after it is encrypted. An eavesdropper who intercepts the public key will still not be able to read messages encrypted using the public key. By the Way It can be argued that, although an eavesdropper who intercepts the public key cannot read data sent from Computer A, the eavesdropper can still pretend to be Computer A by encrypting new data and sending it on to Computer B. Thus, although public key encryption provides confidentiality, it does not necessarily provide authenticity. However, several methods exist for enclosing authentication information within the encrypted data, so that when the data is decrypted, Computer B will have some assurance that the data actually came from Computer A. See the sections "Digital Signatures" and "Certificates," later in this hour. Public key encryption methods are commonly used for protected Internet transactions. You'll learn later in this hour about public key certificates, which are used for TCP/IP security protocols such as Secure Sockets Layer and IP Security. Digital SignaturesIt is sometimes important to ensure the authenticity of a message even if you don't care whether the content of the message is confidential. For instance, a stock broker might receive an email message that says Sell 20 shares of my Microsoft stock. -Bennie Selling 20 shares might be an entirely routine event for this investor. The investor and the broker might not care if the transaction is totally immune from eaves dropping. However, they might consider it extremely important to ensure that this sell notice came from Bennie and not from someone pretending to be Bennie. A digital signature is a method for ensuring that the data came from the source to which it is attributed and that the data has not been altered along its delivery path. A digital signature is a block of encrypted data included with a message. The block of encrypted data is sometimes called an authenticator. A digital signature typically uses the public key encryption process in reverse (see Figure 20.4):
Figure 20.4. The digital signature process.
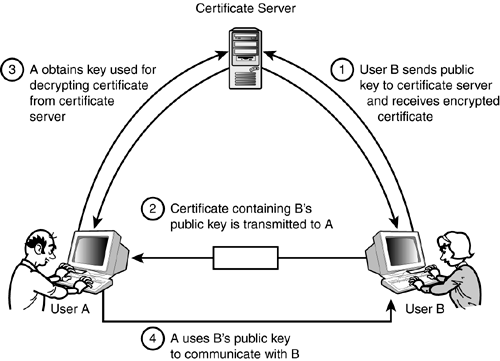
The digital signature thus ensures that the data was not altered and that it came from its presumptive source. As a rudimentary security measure, the entire message could be encrypted with Computer B's private key rather than just the authenticator. However, encrypting with a private key and decrypting with a public key does not really offer confidentiality, as the public key, which is used for decryption, is sent over the Internet and therefore might not be secret. An eavesdropper who has the public key can decrypt the encrypted authenticator. However, the eavesdropper will not be able to encrypt a new authenticator and therefore cannot pretend to be Computer B. Digital CertificatesThe grand design of making the public key available to anyone who requests it is an interesting solution, but it still has some limitations. The fact is, an attacker can still make mischief with the public key. The attacker might be able to decrypt digital signatures (see the preceding section) or even read passwords encrypted with the user's private key. It is safer to provide some kind of security system for ensuring who gets access to a public key. One answer to this problem is what is called a digital certificate. A digital certificate is essentially an encrypted copy of the public key. The certificate process is shown in Figure 20.5. This process requires a third-party certificate server that has a secure relationship with both the parties that want to communicate. The certificate server is also called a certificate authority (CA). Figure 20.5. Authentication using digital certificates.
Several companies provide certificate services for the Internet. One major certificate authority is VeriSign Corp. Some large organizations provide their own certificate services. The certificate process varies among the various vendors. A rough schematic description of the process is as follows:
The best known standard for the certification process is the X.509 standard, which is described in several RFCs. X.509 version 3 is described in RFC 2459. The digital certificate process is designed to serve a community of users. As you might guess, the security of the process depends on the safe distribution of any keys necessary for communicating with the certificate server. This might seem like simply transferring the problem. (You guarantee safe communication with the remote host by presupposing safe communication with the certificate server.) However, the fact that the protected communication channel is limited to a single certificate server (as opposed to any possible host within the community) makes it much more feasible to impose the overhead of additional safeguards necessary for ensuring a secure exchange. The certificate process described earlier in this hour conveniently assumes the certificate server assigned to Computer A is the same server that provides certificates for User B. The certificate process might actually require a number of certificate servers spread across a large network. In that case, the process might require a series of communications and certificate exchanges with other certificate servers to reach the server that provided the User B certificate. As RFC 2459 states, "In general, a chain of multiple certificates might be needed, comprising a certificate of the public key owner (the end entity) signed by one CA, and zero or more additional certificates of CAs signed by other CAs. Such chains, called certification paths, are required because a public key user is only initialized with a limited number of assured CA public keys." Luckily, like most of the details related to encryption, this process is built into the software and doesn't require direct oversight from the user. The X.509 certificate process is used in some of the TCP/IP security protocols discussed later in this hour, such as Secure Sockets Layer and IP Security. |
EAN: 2147483647
Pages: 259