Network Intrusion Prevention Capabilities
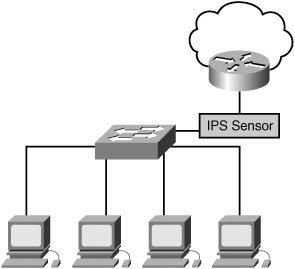
| Intrusion Prevention technology enables you to stop intrusion traffic before it enters your network by placing the sensor as a Layer 2 (Ethernet layer) forwarding device in the network. This sensor has two interfaces connected to your network (see Figure 7-1). Any traffic that passes through the sensor can then be examined by the sensor's Intrusion Prevention software.[click here] Figure 7-1. Intrusion Prevention Sensor Deployment
The main differentiator between an IDS and an IPS is the ability of an IPS to drop ( or modify) traffic it receives on one of its interfaces, preventing the original traffic from reaching its destination. For efficiency, dropping traffic is usually divided into the following categories:
Dropping a Single PacketThe simplest form of Intrusion Prevention involves identifying a suspicious packet and dropping it. The bad packet does not reach the target system, so your network is protected; however, the attacker can repeatedly send the bad packets. For each packet, the IPS needs to analyze the network packets and determine whether to pass or drop the traffic, consuming resources on your IPS device. Dropping All Packets for a ConnectionInstead of dropping a single packet, your IPS can drop all traffic for a specific connection for a configured period of time. In this situation, when a suspicious packet is detected, it is dropped along with all subsequent packets that belong to the same connection. The connection is usually defined as traffic that matches the following parameters:
The advantage to the connection drop is that subsequent packets matching the connection can be dropped automatically without analysis. The drawback, however, is an attacker still has the ability to send traffic that does not match the connection being dropped ( for example, attacking another service or system on your network). Dropping All Traffic from a Source IPThe final dropping mechanism is to drop all the traffic originating from a specific source IP address. In this situation, when the suspicious packet is detected, it is dropped, along with all traffic from the corresponding source IP address for a configured period of time. Because all traffic from the attacking host can be dropped with minimal examination, your IPS device uses very few resources. The main drawbacks are if attackers can spoof the source address and pretend to be an important system, such as a business partner, or if the initial signature is a false positive and valid traffic is denied access to your network. |
EAN: 2147483647
Pages: 115