VPN Peer Model (MPLS)
|
| < Day Day Up > |
|
Because of the cost of ownership and complexity of implementation, many firms choose to trust their carrier with maintaining data integrity. These networks become known as 'trusted VPNs;' networks with encryption are known as 'secure VPNs.' In trusted VPNs, the sites are linked to the provider edge equipment (PE) via dedicated links or leased lines and tunnels are built from PE to PE (see Figure 7.15). The peer model is also called router adjacency.
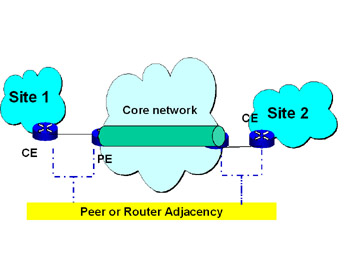
Figure 7.15: Peer Model
In the datacom marketplace, IP traffic is the primary network transport. Carriers wishing to provide IP VPNs offered Frame Relay (FR) and ATM. These solutions are good, but often are not scaleable or cost effective enough to provide viable solutions for many businesses.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 138
- Challenging the Unpredictable: Changeable Order Management Systems
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- The Second Wave ERP Market: An Australian Viewpoint
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Data Mining for Business Process Reengineering