Data Flow in MPLS Networks
|
| < Day Day Up > |
|
The simplest form of data “flow” occurs when IP packets are presented to the ingress router, which is acting as the LER (see Figure 1.7).
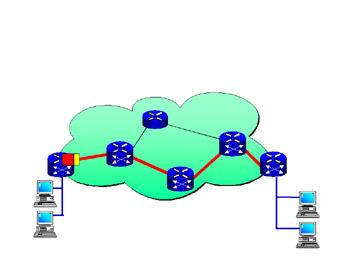
Figure 1.7: Ingress LER Attaches a Shim Header
Much like the sorting room at your postal service’s branch location that classifies mail into service grades of first-class, priority, or express, the LER classifies incoming IP traffic, relating it to the appropriate label. As we’ve seen, in MPLS this classification process is called forward equivalence class (FEC).
LERs use several different modes to label traffic. In the simplest example, the IP packets are “nailed up” to both a label and an FEC using preprogrammed tables, such as the example shown in Table 1.2.
| Destination/IP | Port Number | FEC | Next Hop | Label | Instruction |
|---|---|---|---|---|---|
| 199.50.5.1 | 80 | B | 47.5.10.100 | 80 | Push |
| 199.50.5.1 | 443 | A | 120.8.4.100 | 17 | Push |
| 199.50.5.1 | 25 | IP | 100.5.1.100 | (Do nothing; native IP) |
When the MPLS packets leave the LER, they are destined for the LSR, where they are examined for the presence of labels. The LSR looks to its forwarding table—called a label information base (LIB) or connectivity table—for instructions. The LSR will swap labels according to LIB instructions. Table 1.3 shows an example of a LIB.
| Label/In | Port In | Label/Out | Port/Out | FEC | Instruction Next Hop |
|---|---|---|---|---|---|
| 80 | B | 40 | B | B | Swap |
| 17 | A | 18 | C | A | Swap |
Figure 1.8 demonstrates the LSR performing its label-swapping functions.
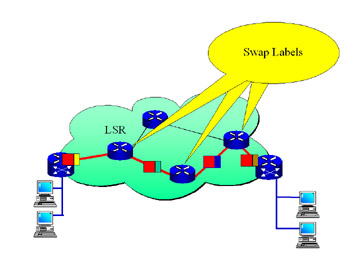
Figure 1.8: Label Swapping
At the egress of the network, the LER removes the MPLS header and forwards the packet to an IP network. Label swapping greatly simplifies MPLS packet flow.
The LER performs many packet-analysis functions: mapping Layer 2 to MPLS, mapping MPLS to Layer 3, and classifying traffic with great granularity. In addition, the LER decides which packets of the traffic become MPLS packets.
One decision-making method is called triggered mode. Using this method, a router will determine that there is a “traffic stream” when a predetermined number of packets are addressed to a single location and are scheduled to arrive within a specified timeframe. Once the router has made this determination, it will then reroute the stream of traffic for MPLS processing.
Even further enhancements and flexibility are available to MPLS using the label-stacking method, as shown in Figure 1.9.
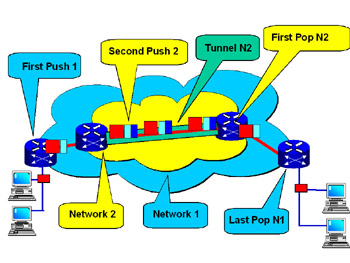
Figure 1.9: Stacked Labels with Tunneled Network
Consider the following scenario. You own Network 1; however, your traffic must proceed across Network 2, a network that is not owned by your company. You must ensure that Network 2 handles your traffic according to your service-level agreement (SLA), but Network 2’s owners are not using the same label criteria as your company.
In this case, you would stack labels and build a tunnel across Network 2. This configuration would preserve the integrity of your network’s labels while allowing the other network to operate independently.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 138