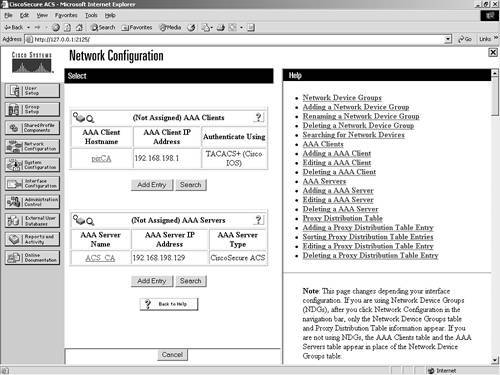
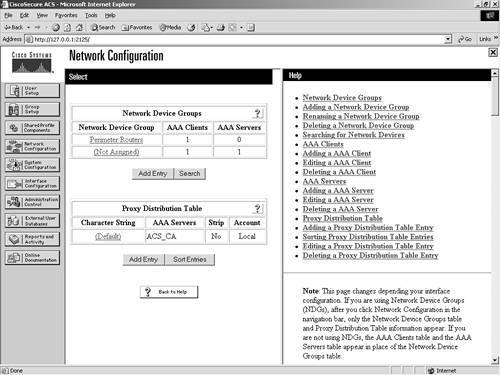
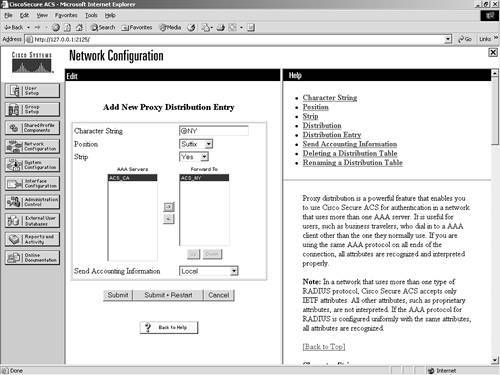
Configuring Proxy Distribution Tables
| A Proxy Distribution Table allows you to take a request for authentication and forward it to other ACS devices based on the string prefix or suffix that you define. In this manner, you can authenticate a user from a California ACS through a New York ACS using a Proxy Distribution Table. As mentioned in the previous section, this is enabled based on a suffix or a prefix that is added to the username and configured within the Proxy Distribution Table by you. When a local ACS sees a user request, the first place that ACS looks is into its database for that user. Assume that the ACS that is in New York sees an authentication request from an AAA client of the ACS in New York and the username and password is a user that is in the ACS California database. Because this user does not exist in the ACS New York database, the authentication would fail; however, with a Proxy Distribution Table configured, the ACS in New York could then forward the authentication request to the California ACS. Proxy authentication can affect authentication by performing a string match. Suppose the string you want to match is CA\. You would configure the Proxy Distribution Table in New York with the information necessary to forward the request to California. When a user enters a username preceded or followed by the string, the request is forwarded. In the Proxy Distribution Table, you define a prefix or a suffix. That prefix or suffix is then associated to another ACS server. For example, a New York ACS has an entry in the Proxy Distribution Table for a suffix of CA. When a California user authenticates and that request is sent to a New York ACS, the user then enters his or her username, username.CA. When the New York ACS database determines the string and looks to the Proxy Distribution Table that has an entry for .CA, the authentication request is forwarded. The user is then authenticated to the correct database. With proxy distribution, you also have the ability to configure ACS with multiple options in that Proxy Distribution Table. The character string that you find actually defines the suffix or the prefix. That suffix or prefix can be up to 32 characters long. The string contains a deliminating character, such as a dot (.) or a slash (/) to determine the breaking point, although this is not required. If you choose to use a prefix string, it would resemble the following: Irvine/bcarroll. In the preceding line of code, bcarroll is the username. Irvine/ defines an entry in the Proxy Distribution Table and, more specifically, the prefix that matches. Keep in mind that you don't need to use a / as the deliminating character. You can actually use just about any character you would like. The slash is just an example. You could just as well use the @ symbol. In that case, your string would resemble the following: IRVINE@bcarroll If you choose to use a suffix, it would resemble the following: bcarroll.IRVINE Again, bcarroll is the username, and .IRVINE is the entry in the Proxy Distribution Table. If the username in the ACS database in Irvine is bcarroll.IRVINE, you want to leave things as is. If the user name is simply bcarroll, you configure stripping so that when the request is forwarded to the ACS in Irvine, the suffix or the prefix is stripped from the message. When you configure stripping, you must take into account the username format on the destination ACS. When ACS proxies to another ACS, the second ACS responds to the first using only Internet Engineering Task Force (IETF) Remote Authentication Dial-In User Service (RADIUS) attributes if RADIUS is the protocol used. The ACS that receives the authentication request from the first ACS is unable to use any vendor-specific attributes. To create entries in the Proxy Distribution Table and enable the entire process, you need to follow three major steps:
We begin with the local AAA server in California. To demonstrate, refer to Figure 9-8. Here, you can see that a user from New York is on the network in California and would like to retrieve information from the Internet. Figure 9-8. Proxy Distribution Table Example Network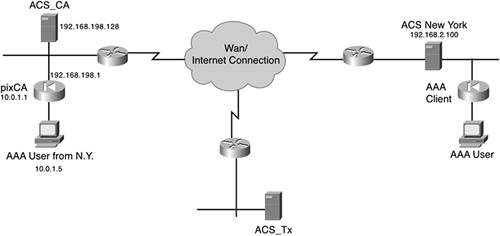 In the California network, the Internet use policy states that you must authenticate to ACS before you are allowed Internet access. Because the user from New York is not in the ACS_CA database, the user's authentication attempt would normally fail. To cause the attempt to be successful, execute the following steps:
At this point, you would assume that you are done; however, you still have not configured the ACS New York. If you look at this scenario from the perspective of the ACS in New York, when it receives an authentication request from California, it is coming from the ACS_CA and not the pixCA. Therefore, you need to add ACS_CA as an AAA client in the ACS New York. By now, you should be comfortable adding AAA clients to ACS. The configuration is no different than it is with any other AAA client, even though the AAA client, ACS_CA, is an AAA server. After it is added, you are able to authenticate, and you have just configured a Proxy Distribution Table. Now, you can add more than one server to the table, change the order that ACS proxies, and create a more distributed network. |
EAN: 2147483647
Pages: 173