Problem You want to track all intrusion attempts that have been made against your PC. Solution Using a graphical user interface From the Control Panel, choose Windows Firewall, click the Advanced tab, and click the Settings button in the Security Logging section. The dialog box shown in Figure 13-8 appears. Figure 13-8. Creating a Windows Firewall log 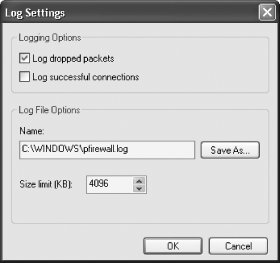
Choose whether to log dropped packets, successful connections, or both. A dropped packet is a packet that the Windows Firewall has blocked. A successful connection doesn't mean an intruder has successfully connected to your PC; it refers to any connection you have made over the Internet, such as to web sites. Because of this, there's usually no reason for you to log successful connections. If you do log them, your log will become large quickly, and it will be more difficult to track only potentially dangerous activity. So, your best bet is to log only dropped packets. After you've made your choices, choose a location for the log, set its maximum size, and click OK. I don't let my log get larger than 1 MB, but depending on how much you care about disk space and how much you plan to use the log, you might want yours larger or smaller. The log will be created in a W3C Extended Log format (.log) that you can examine with Notepad or another text editor or by using a log analysis program such as the free AWStats (http://awstats.sourceforge.net). Each log entry has a total of up to 16 pieces of information associated with each event, but the most important columns for each entry are the first eight.
 | In a text editor, the names of the columns don't align over the data, but they will align in a log analyzer. |
|
Discussion When examining the logs, you need to keep in mind that the source IP address is the source of the attack. Keep in mind that most probes are automated and not targeted at your specific computer. The probes are sent out to thousands of IP addresses. You might notice the same source IP address continually cropping up; if so, you might be targeted by an intruder. It's also possible that the intruder is sending out automated probes to thousands of PCs across the Internet and your PC is not under direct attack. In either case, you can send the log information to your ISP and ask them to follow up by tracking down the source of the attempts. Either forward the entire log or cut and paste the relevant sections to a new file. To help you better understand the logs, Table 13-4 describes the most important columns. Table 13-4. The columns in the Windows Firewall log| Name | Description |
|---|
| Date | Date of occurrence, in year-month-date format | | Time | Time of occurrence, in hour:minute:second format | | Action | The operation that was logged by the firewall, such as DROP for dropping a connection, OPEN for opening a connection, and CLOSE for closing a connection | | Protocol | The protocol used, such as TCP, UDP, or ICMP | | Source IP (src-ip) | The IP address of the computer that started the connection | | Destination IP (dst-ip) | The IP address of the computer to which the connection was attempted | | Source Port (src-port) | The port number on the sending computer from which the connection was attempted | | Destination Port (dst-port) | The port to which the sending computer was trying to make a connection | | size | The packet size | | tcpflags | Information about TCP control flags in TCP headers | | tcpsyn | The TCP sequence of a packet | | tcpack | The TCP acknowledgment number in the packet | | tcpwin | The TCP window size of the packet | | icmtype | Information about the ICMP messages | | icmcode | Information about the ICMP messages | | Info | Information about an entry in the log |
See Also Recipe 13.12 setting up the Windows Firewall; Recipe Recipe 13.14 on using the ZoneAlarm firewall; MS KB 875356, "How to configure the Windows Firewall feature in Windows XP Service Pack 2," and MS KB 875357, "Troubleshooting Windows Firewall settings in Windows XP Service Pack 2" |

